October 26, 2023
The number of user requests to decrypt files affected by encoder trojans decreased by 19.64%, compared to the previous month. The most common encoder in September was Trojan.Encoder.26996, which accounted for 24.64% of incidents recorded. The August leader, Trojan.Encoder.3953, ranked second; users encountered this trojan in 19.43% of cases. Third place was taken by Trojan.Encoder.35534, with a share of 5.21%.
Over the course of September, new threats were detected on Google Play. Among them were adware trojans, malware that subscribed users to paid services, and trojan apps that attackers use for fraud. Moreover, Doctor Web has published analytical materials covering the Android.Pandora.2 and Android.Spy.Lydia malicious programs. The former is a backdoor that infects Smart TVs and TV boxes based on the Android TV operating system and performs DDoS attacks at the command of threat actors. The latter is a spyware trojan targeting Iranian users.
Principal trends in September
- A decrease in the total number of detected threats
- A decrease in the number of user requests to decrypt files affected by encoder trojans
- The emergence of new malware on Google Play
According to Doctor Web’s statistics service
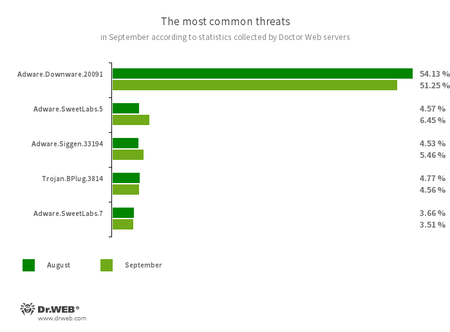
The most common threats in September:
- Adware.Downware.20091
- Adware that often serves as an intermediary installer of pirated software.
- Adware.SweetLabs.5
- Adware.SweetLabs.7
- An alternative app store and an add-on for Windows GUI (graphical user interface) from the creators of “OpenCandy” adware.
- Adware.Siggen.33194
- The detection name for a freeware browser that was created with an Electron framework and has a built-in adware component. This browser is distributed via various websites and loaded onto users’ computers when they try downloading torrent files.
- Trojan.BPlug.3814
- The detection name for a malicious component of the WinSafe browser extension. This component is a JavaScript file that displays intrusive ads in browsers.
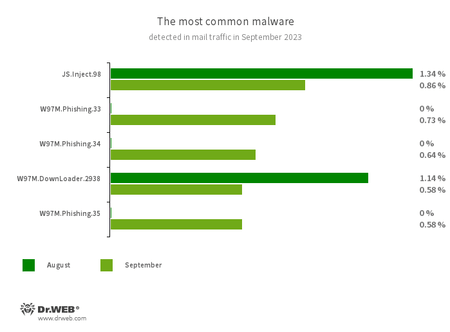
Statistics for malware discovered in email traffic
- JS.Inject
- A family of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- W97M.Phishing.33
- W97M.Phishing.34
- W97M.Phishing.35
- Microsoft Word phishing documents that target users who want to become investors. They contain links to fraudulent websites.
- W97M.DownLoader.2938
- A family of downloader trojans that exploit vulnerabilities in Microsoft Office documents. They can also download other malicious programs to a compromised computer.
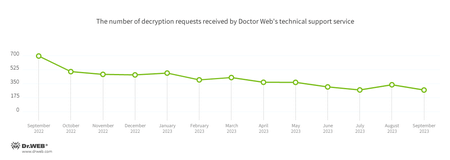
Encryption ransomware
In September, the number of requests to decrypt files affected by encoder trojans decreased by 19.64%, compared to August.
The most common encoders of September:
- Trojan.Encoder.26996 — 24.64%
- Trojan.Encoder.3953 — 19.43%
- Trojan.Encoder.35534 — 5.21%
- Trojan.Encoder.35067 — 3.32%
- Trojan.Encoder.24383 — 2.84%
Dr.Web Security Space for Windows protects against encryption ransomware
Dangerous websites
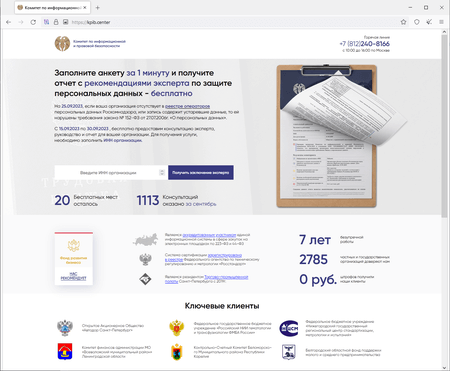
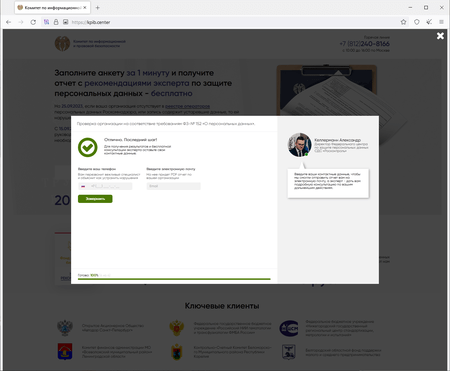
In September, Doctor Web’s Internet analysts noted the high activity of cyber fraudsters. For example, cases were detected of spam emails being distributed that were allegedly sent by tax authorities. Such emails contained a link to a website where visitors were offered the opportunity to verify whether organizations and companies were complying with the requirements of the Russian Federation’s law on personal data. For this, users had to take a short survey and then provide personal data “to receive the results and get a free expert consultation”.
The screenshot above shows how one such website asks visitors to “fill out the form in 1 minute and receive a report with an expert’s recommendations on personal-data protection – for free”.
After answering the preliminary survey questions, the user is asked to provide a phone number and an email:
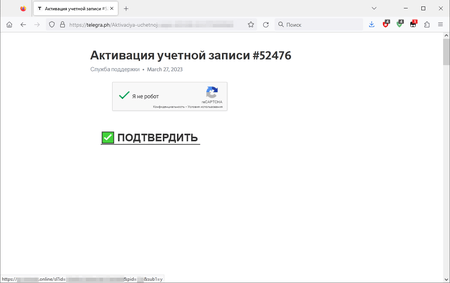
Our specialists also observed cases of malicious actors distributing web links to phishing sites via the Telegraph blog platform. The attackers publish posts on this platform, composing them in such a way that they look like confirmation forms for registering new accounts in various online services. When potential victims click on the element containing the text “CONFIRM”, they are redirected to phishing sites. Among them are fraudulent investment-themed sites.
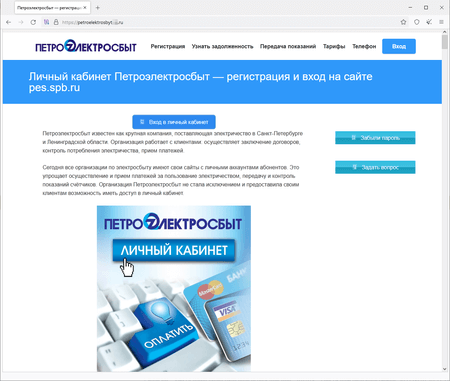
In addition, our specialists detected more fake sites where users allegedly could pay for public utilities. Cybercriminals use these to collect their victims’ personal data. The screenshot below depicts an example of one such site. It imitates the appearance of the web portal of one electricity supply organization. Visitors allegedly can use it to log into their account to pay their bills.
Malicious and unwanted programs for mobile devices
In September 2023, Doctor Web published research on the Android.Pandora.2 backdoor, which infects Smart TVs and TV boxes running the Android TV operating system. Cybercriminals use this malware to create a botnet of infected devices and perform DDoS attacks.
Moreover, our malware analysts informed users about the Android.Spy.Lydia trojan apps, which implement spyware functionality and target Iranian users.
According to detection statistics collected by Dr.Web for Android, in September, Android device owners encountered Android malware less often. At the same time, the number of adware detections increased. Over the course of last month, new threats were uncovered on Google Play. Among them were adware trojans from the Android.HiddenAds family, Android.Joker trojans, which subscribe users to paid services, and Android.FakeApp malicious apps used by fraudsters.
The following September events involving mobile malware are the most noteworthy:
- A decrease in the activity of Android malware,
- The detection of new trojan apps on Google Play.
To find out more about the security-threat landscape for mobile devices in September, read our special overview.