Pandora's box is now open: the well-known Mirai trojan arrives in a new disguise to Android-based TV sets and TV boxes
Real-time threat news | Hot news | All the news | Virus alerts
September 6, 2023
Doctor Web received reports from several users about cases of files being modified in the /system directory. SpIDer Guard alerted them to the presence of the following objects in the file system:
- /system/bin/pandoraspearrk
- /system/bin/supervisord
- /system/bin/s.conf
- /system/xbin/busybox
- /system/bin/curl
The following files were also found to have been modified:
- /system/bin/rootsudaemon.sh
- /system/bin/preinstall.sh
File modification reports listed different files on different devices. As it turned out, the script that installs this malware looks for system services with executable code in .sh files and adds a line that launches the trojan:
- /system/bin/supervisord -c /system/bin/s.conf &
This is necessary to anchor the trojan in the system so that it will be launched when the device is rebooted.
Of particular interest is the obfuscated pandoraspearrk file. After undergoing analysis, this file was added to the virus database as the Android.Pandora.2 backdoor. Its main purpose is to use the infected device as part of a botnet to perform DDoS attacks. The supervisord file is a service that monitors the status of the pandoraspearrk executable and restarts the backdoor if it is terminated. Supervisord reads its settings from the s.conf file. The busybox and curl files are legitimate command-line utilities of the same name that are present to ensure networking capabilities and file system operations. The rootsudaemon.sh file starts the daemonsu service, which has root privileges, and the aforementioned supervisord which gets its configuration from s.conf. The preinstall.sh program performs various actions specified by the device vendor.
This malware targets users of Android TV-based devices, primarily those in the lower price bracket. In particular, users of Tanix TX6 TV Box, MX10 Pro 6K, H96 MAX X3 and others are at risk.
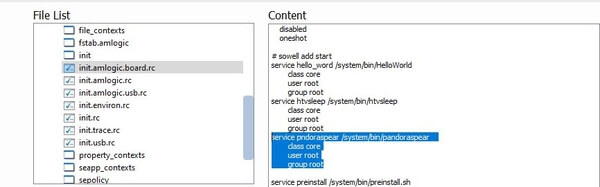
We have discovered that this trojan is a modification of the Android.Pandora.10 backdoor (formerly known as Android.BackDoor.334) that arrives as a malicious firmware update, released on December 3, 2015, for the MTX HTV BOX HTV3 Android box. It is likely that this update has been made available for download from a number of websites, as it is signed with publicly available Android Open Source Project test keys. The service that runs the backdoor is included in boot.img. The figure below shows how the malicious service is launched from the init.amlogic.board.rc file included in boot.img.
An alternative way for Android.Pandora backdoors to infect devices is for users to install applications for streaming pirated movies and TV shows. Examples of such resources include domains with names like youcine, magistv, latinatv, and unitv. These domains target Spanish-speaking users.
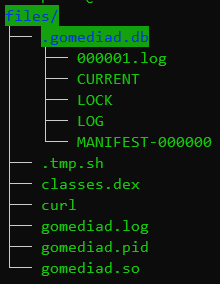
After the application is installed and launched on the device, the GoMediaService is started without the user noticing. After the application is launched for the first time, this service is automatically started when the device is booted; it then calls the gomediad.so program. This version of the program unpacks a number of files, including classes.dex, an executable file detected by Dr.Web antivirus as Tool.AppProcessShell.1, which is a command-line interpreter with elevated privileges. Malicious programs on the device can then interact with this shell through the open port 4521. The figure below shows the file structure created by the gomediad.so program, detected by Dr.Web as Android.Pandora.4, after it was launched.
Among the unpacked files is .tmp.sh, which is the installer for the Android.Pandora.2 backdoor we already know about. Once installed and launched, the backdoor obtains the address of the control server from command-line parameters or from a file encrypted with the Blowfish algorithm. After accessing the server, the backdoor downloads a hosts file to replace the original system file, starts the self-update process and becomes ready to receive commands.
By sending commands to an infected device, attackers can launch and stop DDoS attacks over the TCP and UDP protocols, perform SYN, ICMP and DNS flood, open a reverse shell, mount Android TV system partitions in read/write mode, and so on. All of these capabilities are available thanks to using the Linux.Mirai code, a trojan that has been used since 2016 to launch DDoS attacks against well-known sites such as GitHub, Twitter, Reddit, Netflix, Airbnb and many others.
Doctor Web recommends updating the operating systems on your devices to the latest available versions that fix existing vulnerabilities, and downloading software only from trusted sources: official websites or app stores.
Dr.Web Security Space for Android is able to remove Android.Pandora from the system as well as the applications in which it is embedded if root privileges are available. If root privileges are not available on the infected device, installing a clean OS image provided by the hardware manufacturer will help to remove the malware.
Read more about Android.Pandora.2 and Linux.Mirai.
Read more about Android.Pandora.4