Doctor Web’s February 2023 review of virus activity on mobile devices
April 6, 2023
Banking trojans and ransomware were detected less often on devices protected by Dr.Web—by 70.57% and 14.63%, respectively. Moreover, users were 33.93% less likely to encounter spyware trojans. The most widespread among these threats were different variants of a piece of malware that attacked users of some unofficial WhatsApp messenger mods.
During the past month, Doctor Web’s virus laboratory uncovered over 70 malicious apps on Google Play. Most of them represented fraudulent apps from the Android.FakeApp family. Trojans that subscribed victims to paid services were also among the discovered threats.
PRINCIPAL TRENDS IN FEBRUARY
- An increase in some adware trojan family activity
- A decrease in banking trojan and ransomware malware activity
- A decrease in spyware activity
- The discovery of multiple threats on Google Play
According to statistics collected by Dr.Web for Android
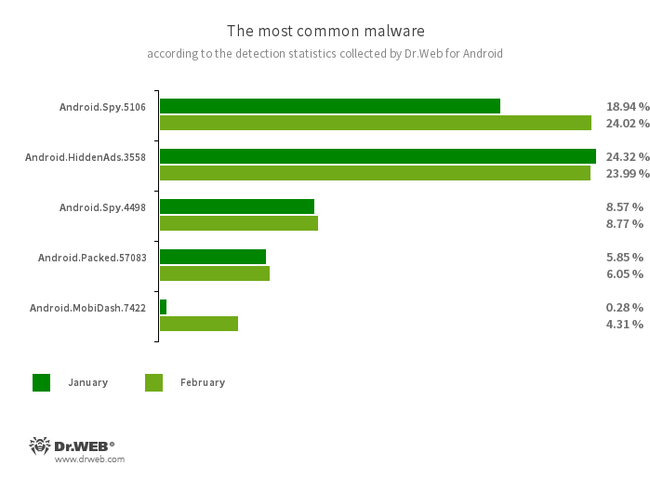
- Android.Spy.5106
- Android.Spy.4498
- The detection name for different variants of a trojan that represents modified versions of unofficial WhatsApp messenger mods. This malicious program can steal the contents of notifications and offer users other apps from unknown sources for installation. And when such a modified messenger is used, it can also display dialog boxes with remotely configurable content.
- Android.HiddenAds.3558
- A trojan designed to display intrusive ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.Packed.57083
- The detection name for malicious applications protected with an ApkProtector software packer. Among them are banking trojans, spyware, and other malicious software.
- Android.MobiDash.7422
- A trojan that displays obnoxious ads. It is a special software module that developers incorporate into applications.
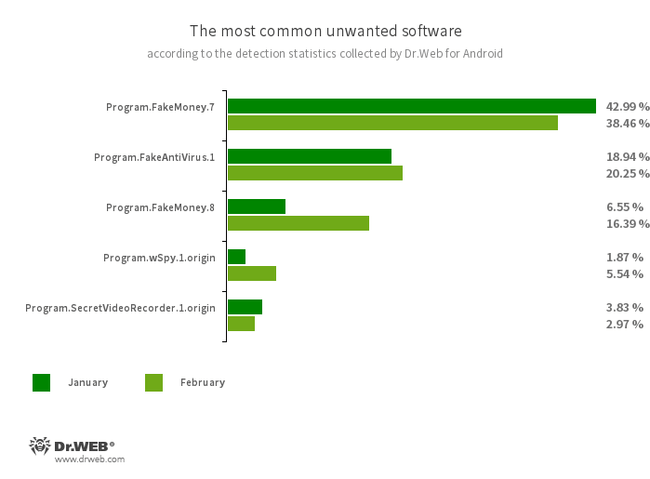
- Program.FakeMoney.7
- Program.FakeMoney.8
- The detection name for Android applications that allegedly allow users to earn money by watching video clips and ads. These apps make it look as if rewards are accruing for completed tasks. To withdraw their “earnings”, users allegedly have to collect a certain sum. But even if they succeed, in reality they cannot get any real payments.
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.wSpy.1.origin
- A commercial spyware app designed to covertly monitor Android device user activity. It allows intruders to read SMS and chats in popular messaging software, listen to the surroundings, track device location and browser history, gain access to a phonebook and contacts, photos and videos, and take screenshots and pictures through a device’s built-in camera. In addition, it has keylogger functionality.
- Program.SecretVideoRecorder.1.origin
- The detection name for various modifications of an application that is designed to record videos and take photos in the background using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
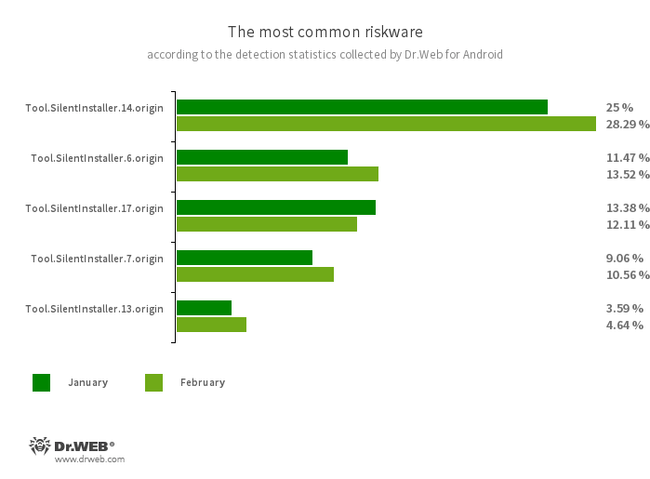
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.17.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.13.origin
- Riskware platforms that allow applications to launch APK files without installing them. They create a virtual runtime environment that does not affect the main operating system.
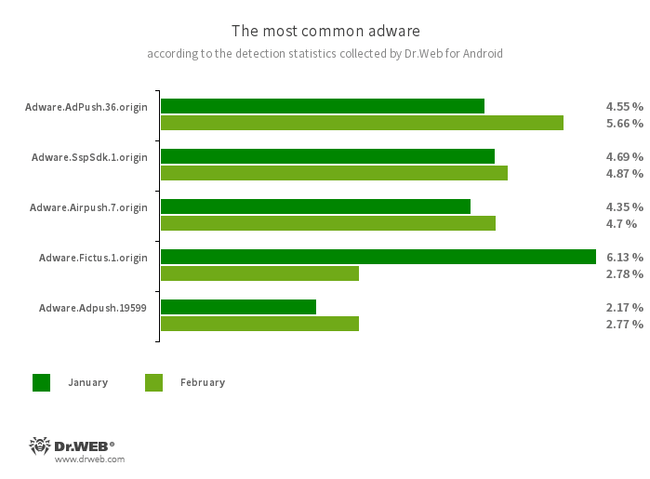
- Adware.AdPush.36.origin
- Adware.Adpush.19599
- Members of a family of adware modules that can be built into Android apps. They display notifications containing ads that mislead users. For example, such notifications can look like messages from the operating system. In addition, modules of this family collect a variety of confidential data and are able to download other apps and initiate their installation.
- Adware.SspSdk.1.origin
- A specialized advertizing software module which can be embedded into Android apps. It displays ads when host applications are not being used and their windows are closed. As a result, users have a hard time identifying the source of such intrusive behavior on their devices.
- Adware.Airpush.7.origin
- A member of adware modules that can be built into Android apps and display various ads. Depending on the modules’ version and modification, these can be notifications containing ads, pop-up windows or banners. Malicious actors often use these modules to distribute malware by offering their potential victims diverse software for installation. Moreover, such modules collect personal information and send it to a remote server.
- Adware.Fictus.1.origin
- An adware module that malicious actors embed into the cloned versions of popular Android games and applications. Its incorporation is performed through a specialized net2share packer. Copies of software created this way are then distributed through various software catalogs. When installed on Android devices, such apps and games display obnoxious ads.
Threats on Google Play
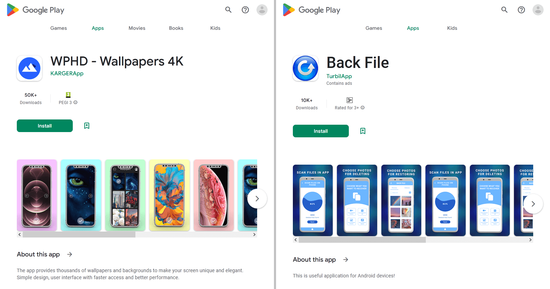
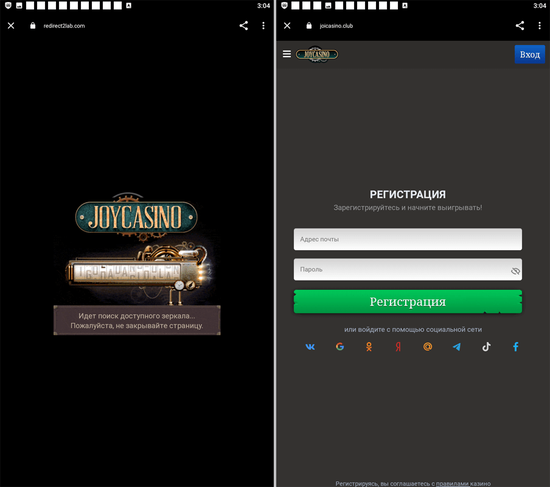
In February, Doctor Web’s virus analysts discovered other malicious apps on Google Play that subscribed Android device users to paid services. For example, trojans from the Android.Subscription family, added to the Dr.Web virus database as Android.Subscription.19 and Android.Subscription.20, were distributed as WPHD - Wallpapers 4K image collection software and a tool for recovering deleted files called Back File.
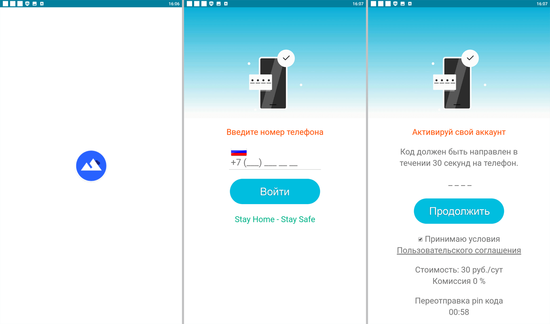
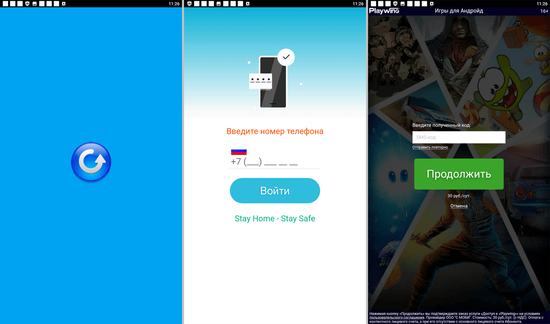
Upon launching, malicious apps of this type load sites of paid services and try subscribing users either automatically or by asking them to provide a mobile phone number. Below are examples of websites that the discovered trojans load to initiate the subscription process:
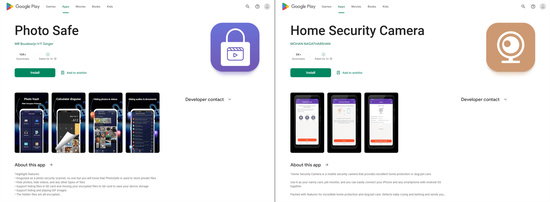
Dubbed Android.Joker.2038 and Android.Joker.2039, these new members of the Android.Joker trojan family were hidden in the Photo Safe and Home Security Camera apps. The former was an application designed to protect files from unauthorized access, while the latter allowed security cameras to be controlled via an Android smartphone or the device itself to be used in video-surveillance mode. These malicious programs covertly load the websites of the targeted services and then automatically subscribe victims to paid services.
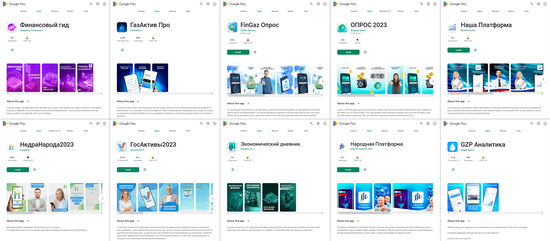
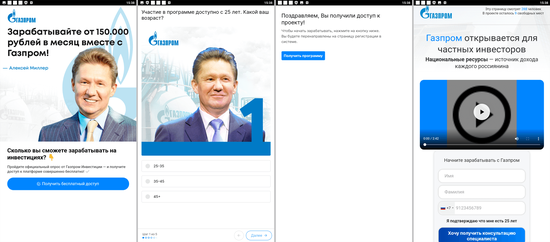
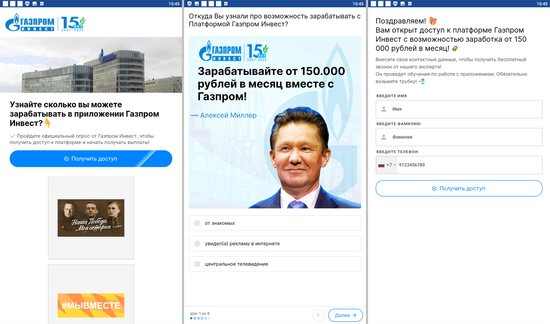
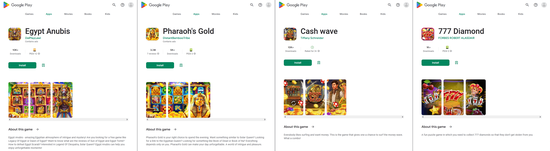
In addition, our specialists discovered dozens of bogus apps from the Android.FakeApp family that were distributed under the guise of all kinds of software. Malicious actors passed many of them off as different financial apps, like directories and teaching aids, programs for taking polls, trading tools, apps containing information on quotes, housekeeping instruments, and so on. Among them were Android.FakeApp.1219, Android.FakeApp.1220, Android.FakeApp.1221, Android.FakeApp.1226, Android.FakeApp.1228, Android.FakeApp.1229, Android.FakeApp.1231, Android.FakeApp.1232, Android.FakeApp.1241, and other trojans.
If users installed these by following a special link (for instance, from an advertisement), then these apps loaded fraudulent sites when launched. On such sites, potential victims were offered the chance to participate in a small poll and gain access to an “investing platform” by registering an account and providing personal information. However, if the installation was organic (i.e., users searched for and installed these fake apps on their own initiative), some of them provided the expected functionality instead of loading the fraudsters’ websites.
The next images depict examples of the bogus websites these trojans could load:
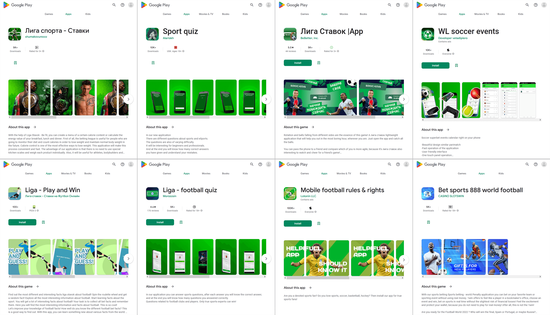
Cybercriminals passed off a number of fake apps as sports-related software or as bookmakers’ official apps.
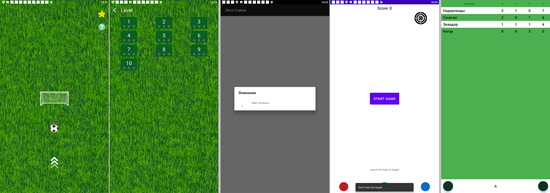
Some of them (like Android.FakeApp.1192, Android.FakeApp.1193, Android.FakeApp.1194, Android.FakeApp.22.origin, Android.FakeApp.1195, Android.FakeApp.1196, and others) performed a check on the device on which they were running. If they detected it was a testing device (for example, a device without a SIM card installed on it or a Nexus line device), they activated harmless functionality. For instance, they launched games and quizzes, loaded sports charts and information tables, loaded match information, etc. Otherwise, they loaded sites in WebView or in the browser whose addresses were obtained from a Firebase database. Other such fake apps (Android.FakeApp.1197, Android.FakeApp.1198, Android.FakeApp.1199, Android.FakeApp.1200, Android.FakeApp.1201, Android.FakeApp.1202, Android.FakeApp.1204, Android.FakeApp.1209, Android.FakeApp.1212, and others) connected to a remote server that made the decision to either execute the harmless functionality hidden in these apps or load a targeted site. And the Android.FakeApp.1203 trojan app received website links to load from the Firebase Remote Config cloud service. Below are examples of how these trojan apps operated.
Launching games and loading a table with information on football matches:
Some apps loading bookmakers’ sites:
The Android.FakeApp.1222, Android.FakeApp.1224, Android.FakeApp.1225, and Android.FakeApp.1235 trojans, which were disguised as games, could load online casinos’ websites in a Google Chrome browser instead of providing the actual gaming experience.
An example of how one of them operates in a gaming mode:
Examples of websites they could load:
Among the fake apps discovered was another program that was disguised as a job-search tool and loaded scammers’ websites with a list of forged vacancies. When users selected one of these, they were asked to either provide their contact details by filling out a special form or contact the “employer” directly through a messenger app. This fake software was a modification of a trojan known since late 2022. Dr.Web detects it as Android.FakeApp.1133.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products