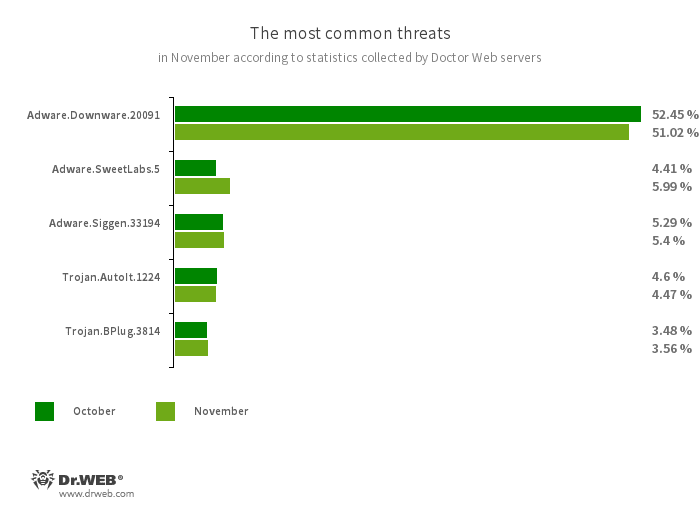
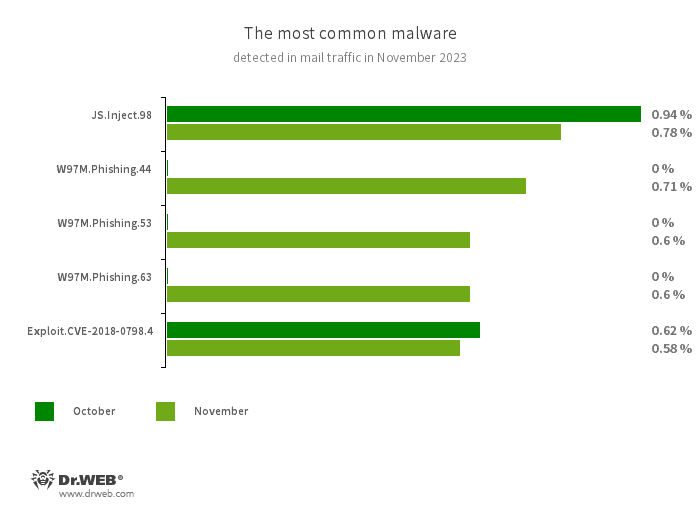
An analysis of Dr.Web anti-virus November detection statistics revealed an 18.09% decrease in the total number of threats detected, compared to October. At the same time, the number of unique threats also decreased by 13.79%. Among the most commonly detected threats were unwanted adware programs, adware trojans, and malicious apps that are distributed along with other threats to make the latter more difficult to detect. Email traffic was dominated by phishing documents. Also commonly encountered were malicious scripts, programs that exploit vulnerabilities in Microsoft Office documents, and various downloaders that download other malware onto target computers.
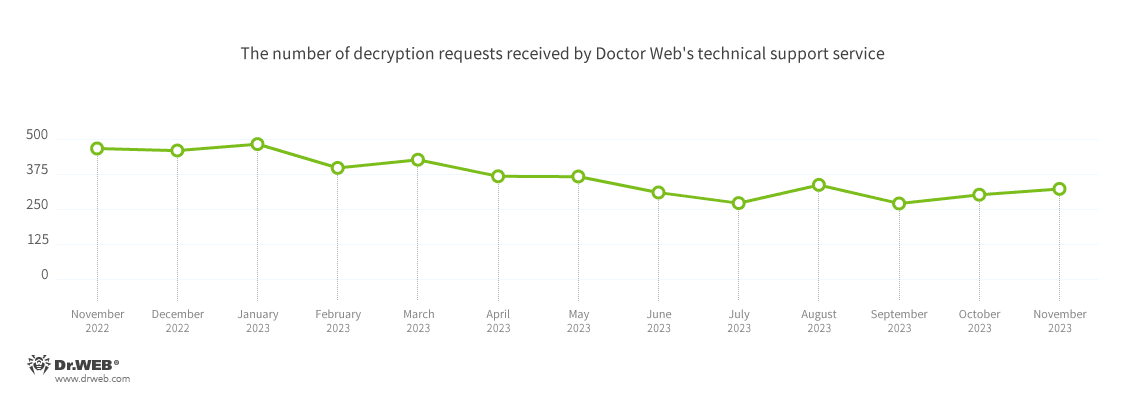
The number of user requests to decrypt files affected by encoder trojans increased by 6.98%, compared to October. Most often, users encountered Trojan.Encoder.3953, which accounted for 21.70% of all incidents recorded. In 21.20% of cases, users were attacked by Trojan.Encoder.26996. With a share of 8.94%, Trojan.Encoder.35534 again came in third.
In November, Doctor Web’s malware analysts discovered new malicious programs on Google Play. Among them were over 20 fake apps engaged in fraudulent schemes and a trojan that subscribed Android device owners to paid services.
Principal trends in November
- A decrease in the total number of threats detected
- A predominance of phishing documents in malicious email traffic
- An increase in the number of user requests to decrypt files affected by encoder trojans
- The emergence of new malicious programs on Google Play
Dangerous websites
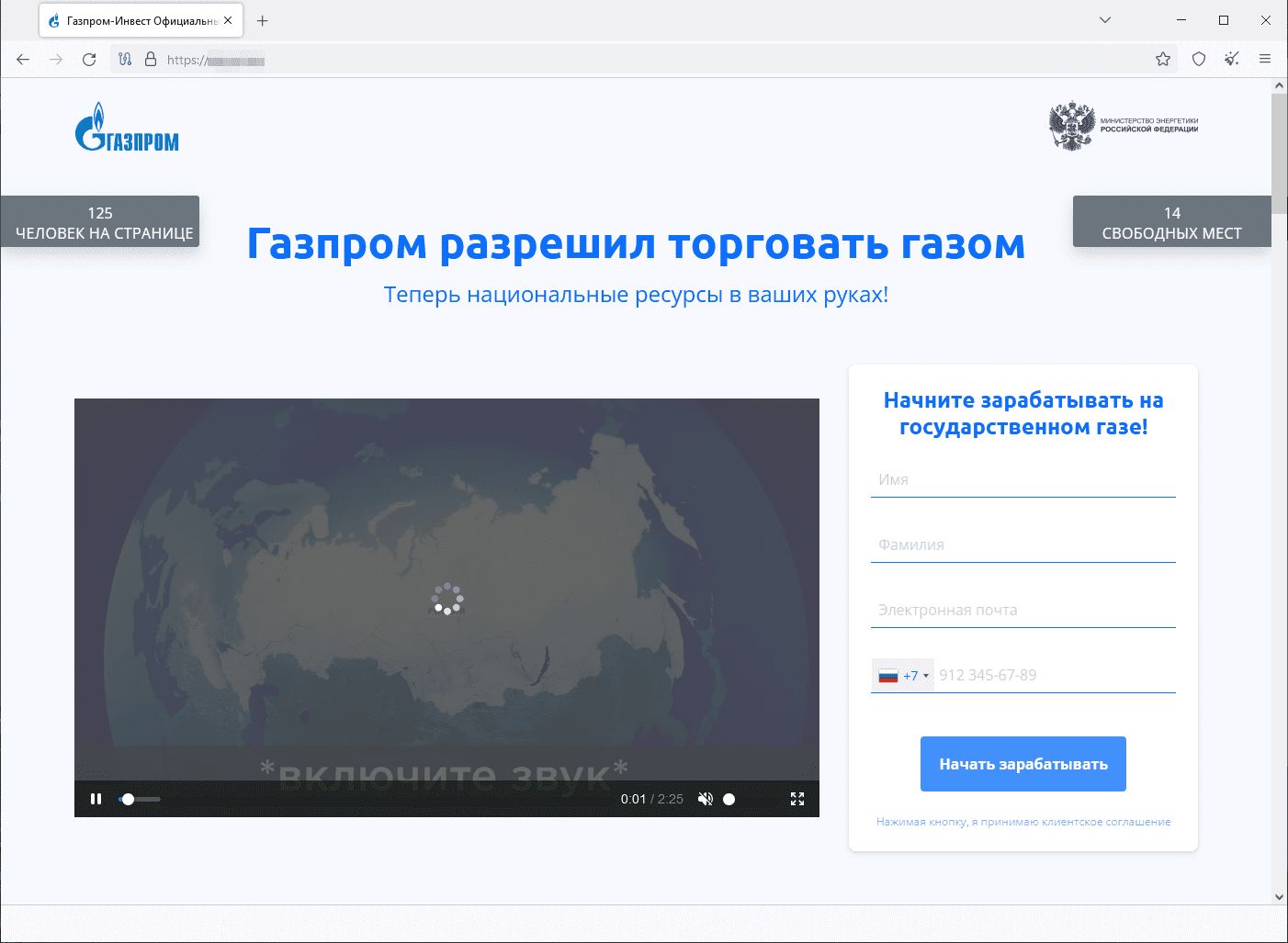
In November, Doctor Web’s Internet analysts detected no significant changes in cyberfraudster activity. Threat actors again tried luring potential victims to all sorts of fake websites, among which fraudulent investment sites and sites offering “free” lottery tickets and chances to participate in prize “draws” remained the most popular.
In the case of the former, users are encouraged to become investors, for which they need to provide their personal data. In the case of the latter, participating in so-called free lottery draws and online contests always ends in winnings. To get their prize, users allegedly need to pay a commission.
An example of a phishing site where a visitor is invited to become an investor:
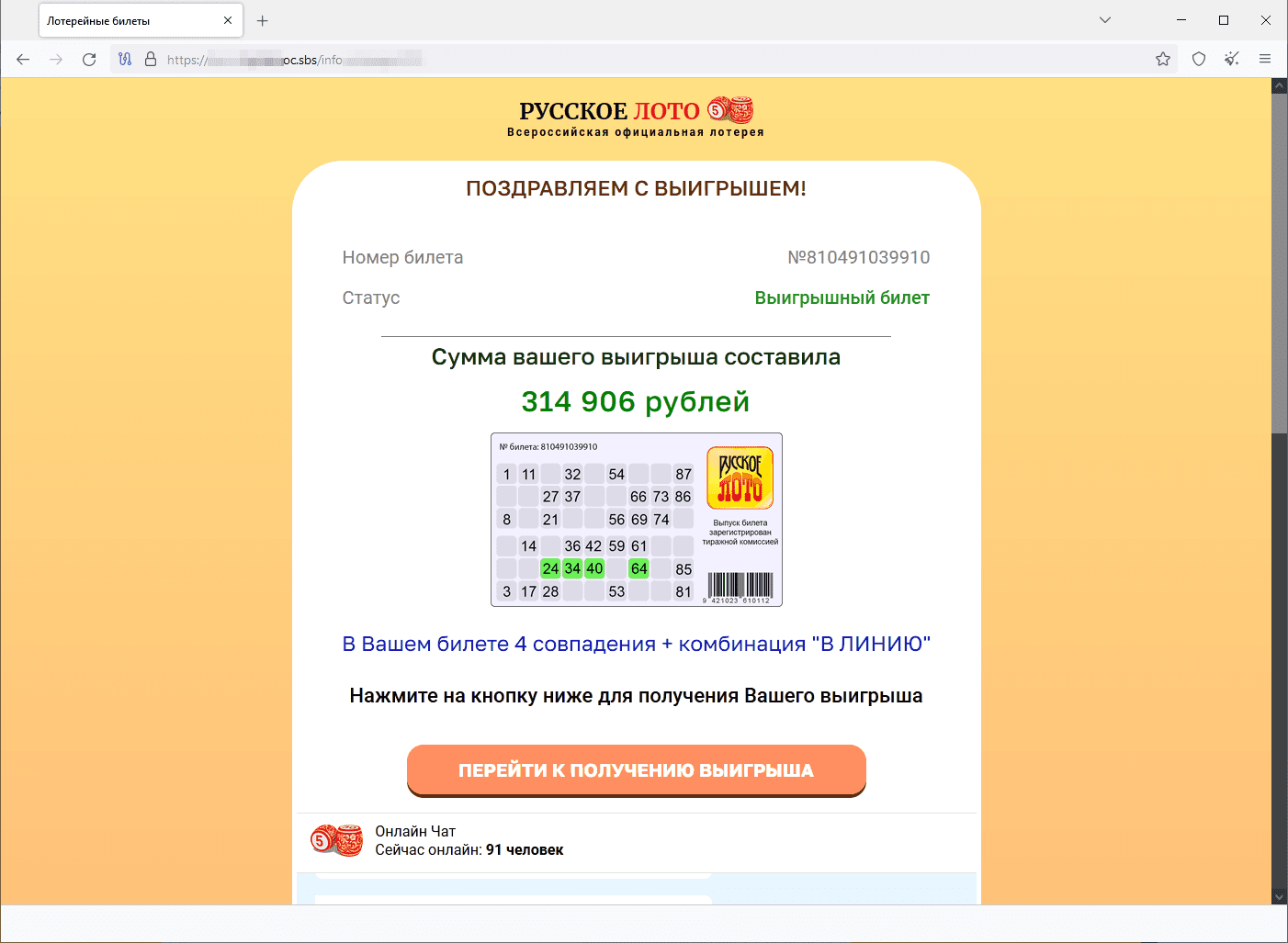
An example of a fraudulent website that simulates a lottery drawing:
The user allegedly won 314,906 rubles and can go on to receive their winnings: