Six month virus activity review from Doctor Web
Virus reviews | All the news | Virus alerts
Doctor Web presents the virus activity review for the first six months of 2009. ATM malware, new threats for Mac OS X and the first large botnet comprised of web-resources became the most significant events of the past half-year. On the other hand the expansion rate of the Shadow botnet (Conficker, Downdup) has decreased significantly.
Botnets
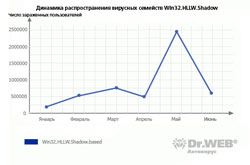
In the first months of 2009 many users and IT security experts focused their attention on the Win32.HLLW.Shadow worm.
Computers infected by the malicious program joined the botnet that ensnared millions of machines worldwide. Win32.HLLW.Shadow had several spreading techniques. It exploited Windows vulnerabilities, used brute force administrator password cracking (it turned out that passwords used by many administrators were rather weak) and travelled between computers on removable data-storage devices.
Authors of Win32.HLLW.Shadow released numerous modifications of the worm during the epidemics. All of them were promptly added to the Dr.Web virus databases. Now activity of this malicious program has declined and it left the virus top ten.
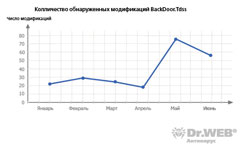
Virut was another botnet that came into the spotlight in the last six months. In case of this botnet computers were infected by a complex polymorphic virus. The Tdss botnet also became a stand-out among networks of zombie computers. A program that enslaved target machines used rootkit technologies to hide its presence in the system. BackDoor.Tdss has been spreading rather intensively in the last six months with its numerous modifications discovered in the wild every now and then. It should be noted that the backdoor can feature different sets of modules meaning that modules responsible for installation and disguise of BackDoor.Tdss are created and spread on commercial basis. The graph below shows how the number of discovered variations of the program changed through the first six months of 2009.
One of the last but by no means the least botnet that got into the news was created using the BackDoor.MaosBoot bootkit family. It is ought to be noted that these bootkits are among the hardest to cure. Two new versions of the bootkits have been discovered by Doctor Web virus analysts in 2009.
In April cyber-criminals included Twitter in their botnet control centre domain name generation algorithm. In May a lot of web-sites were found to spread the rootkit. The sites were capable of detecting location of a supposed victim. For example, BackDoor.MaosBoot wouldn’t attack a host unless it was located in Germany or the USA.
JS.Gumblar
While largest botnets were typically comprised of infected workstations, JS.Gumblar changed the situation. Malicious programs from this family contributed to creation of a botnet of more than 60000 web-pages.
The mid-May 2009 saw a wave of malicious scenarios implemented using Javascript. This was when JS.Gumblar came into action.
Malicious scenarios of JS.Gumblar were injected in the code of many web-resources. For most of them it was the first time when they were compromised.
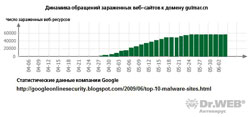
According to Google statistics showing the umber of requests to gumblar.cn (malicious scenarios used to carry out attacks from infected pages were downloaded from the web-site) looks as follows:
So instead of targeting user machines cyber-criminals created and still control this non-typical botnet of compromised web-resources with numbers of visitors reaching hundreds of thousands. Such web-resources enable malefactors to spread any piece of malware among users worldwide.
Malware and ATMs
Customers of Russian banks using ATMs were worried by the news about viruses that compromised ATMs of certain Russian banks.
Trojan.Skimer stored information found on bank cards and could also save account balance information if a victim obtained it using the ATM. This information can be used by cyber-criminals to manufacture fake cards to withdraw all funds available on accounts of their victims.
The ATM software vulnerability exploited by the Trojan has been closed.
Ransomware
SMS-fraud where a victim has to send a paid message is becoming even more popular. To force a user to send such a message cyber-criminals create ransomware that can block access to Windows (Trojan.Winlock) or display adult-content banners (Trojan.Blackmailer).
A message prompting a victim to send a paid SMS can also be sent via ICQ or over a social networking web-site.
Mac OS X
The growing interest to Mac OS X on the part of cyber criminals has been observed since the beginning of 2009. The first outcome of this interest was the Mac.Iservice Trojan that added compromised Macs to a botnet. It was the first case of a botnet consisting of machines running Mac OS X (the iBotnet).
The spring saw a wave of other malicious programs for Mac. Those were Mac.DnsChange trojans that were sperad as links to a malicious video clip. Twitter became one of the channels used to distribute the link.
Activation of the malicious video clip allowed detecting the target operating system using the User-Agent data. After detection of the platform a user was offered a corresponding file – a malicious program for Windows or for Mac OS X.
As popularity of Mac OS X grows among users, so it does among cyber-criminals. By now the number of threats for Mac OS X is not nearly large enough to be compared with the number of threats targetting Windows. However, the situation may change in the future.
Exploits
In the first two weeks of July a severe “zero day” vulnerability was found in a component of Microsoft DirectX used by Internet Explorer 6 and 7.
Vulnerable operating systems include 2000/2003/XP with all released updates installed (including x64 versions of the systems). incorreect procession of a video stream by the msVidCtl.dll component of ActiveX can be used to spread malicious programs from web-sites that cause stack overflow and launch a malicious program on the target machine.
All exploits of this vulnerability are members of the Exploit.DirectShow family.
Spam and mail viruses
Spammers never hesitate to exploit breaking news in their mailings. Ina few hours after death of Michael Jackson became known to the public it became one of the main subjects of spam e-mails replacing supposed news about events related to the latest Iran presidential election.
A number of phishing attacks also surged up .in June. The total amount of phishing e-mails increased as well as the target group that included customers of Bank of America, JPMorgan Chase Bank, Community State Bank, and St. George Bank as well as people that use PayPal, eBay and Amazon customers.
Mail viruses came into the spotlight in the first days of June. The last month became the leader in the number of messages with attached malware and message providing links to malware downloads. Trojan.PWS.Panda.122 was sent as an e-card between June 1 and 2. This malicious program scans Internet-traffic of the compromised machine and retrieves online banking and payment systems passwords.
Social networking web-sites
As in 2008, increased activity of cyber-criminals on social networking web-sites was registered in the spring of 2009.
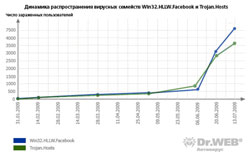
The number of instances of infections by Win32.HLLW.Facebook (aka Koobface) doubled in two summer months. At the beginning of June many modifications of Win32.HLLW.Facebook that targeted users of Facebook, МySpace and Twitter were added to the Dr.Web anti-virus database.
We believe it is necessary to speak about Twitter in more detail. It has already become a popular channel used to spread malicious programs with the number of messages containing links to bogus web-sites increasing.
It should be specially noted that link shortening services make it very hard to guess if a link points to an unwanted web-resource.
The JS.Twitter virus family appeared at the end of May. Now the family is represented by XSS-worms that were spreading using the social networking web-site at the end of the spring.
As for malicious programs spreading over Russian social networking web-sites, the family of Trojan.Hosts ransomware can serve as the most typicaly example.
Conclusions
By the summer 2009 the number of infections by Win32.HLLW.Shadow declined significantly. However, its appearance set the trend for the increasing number of large-scale viral threats that persisted in 2009. JS.Gumblar followed Win32.HLLW.Shadow and infected an unprecedented number of web-resources.
Cyber-criminals are clearly interested in Mac OS. Infection methods become more versatile allowing to deliver a malicious program for a detected platform. Popular social networking web-sites attract attention of the growing number of virus-makers. A number of modifications of Win32.HLLW.Facebook surged in the beginning of the summer. The particular interest of cyber-criminals in Twitter should also be taken intoo consideration.
The growing number of ransomware shows that cyber-extortioners strive for quick and easy illegal money.
The special trend of the past six months is the malicious program for ATMs.
Viruses detected in mail traffic in last six months
| 01.01.2009 00:00 - 01.07.2009 00:00 | ||
| 1 | Win32.HLLM.Netsky.35328 | 27763294 (34.82%) |
| 2 | Win32.HLLM.MyDoom.33808 | 7635271 (9.58%) |
| 3 | Win32.HLLM.Beagle | 7400948 (9.28%) |
| 4 | Trojan.DownLoad.36339 | 5816485 (7.29%) |
| 5 | Win32.HLLM.MyDoom.44 | 3053357 (3.83%) |
| 6 | Win32.HLLM.MyDoom.based | 2738829 (3.43%) |
| 7 | Win32.HLLM.Netsky.based | 2557757 (3.21%) |
| 8 | Win32.HLLM.Netsky.28672 | 2484754 (3.12%) |
| 9 | Win32.HLLM.Netsky | 2252999 (2.83%) |
| 10 | Win32.HLLM.Perf | 2012539 (2.52%) |
| 11 | Trojan.Botnetlog.9 | 1988614 (2.49%) |
| 12 | Trojan.MulDrop.19648 | 1705059 (2.14%) |
| 13 | Win32.HLLM.Beagle.32768 | 1500116 (1.88%) |
| 14 | Trojan.MulDrop.13408 | 1470765 (1.84%) |
| 15 | Win32.HLLM.MyDoom.49 | 1101971 (1.38%) |
| 16 | Trojan.PWS.Panda.114 | 1024091 (1.28%) |
| 17 | Win32.HLLM.Beagle.27136 | 999536 (1.25%) |
| 18 | Exploit.IFrame.43 | 917203 (1.15%) |
| 19 | Win32.HLLM.Beagle.pswzip | 629979 (0.79%) |
| 20 | Exploit.IframeBO | 573008 (0.72%) |
| Total scanned: | 353,878,451,872 |
| Infected: | 79,738,624 (0.0225%) |
Viruses detected on user machines in last six months
| 01.01.2009 00:00 - 01.07.2009 00:00 | ||
| 1 | Win32.HLLW.Gavir.ini | 7954841 (7.76%) |
| 2 | Win32.HLLW.Shadow.based | 4996557 (4.88%) |
| 3 | Trojan.DownLoad.36339 | 4610048 (4.50%) |
| 4 | DDoS.Kardraw | 3730909 (3.64%) |
| 5 | Win32.HLLM.Beagle | 3497040 (3.41%) |
| 6 | JS.Nimda | 3026751 (2.95%) |
| 7 | Trojan.Botnetlog.9 | 2836732 (2.77%) |
| 8 | Win32.Virut.5 | 2811911 (2.74%) |
| 9 | Trojan.Starter.516 | 2510767 (2.45%) |
| 10 | W97M.Thus | 2336936 (2.28%) |
| 11 | Win32.Virut.14 | 2162374 (2.11%) |
| 12 | Win32.HLLM.Netsky.35328 | 2141902 (2.09%) |
| 13 | Trojan.PWS.Panda.114 | 1988995 (1.94%) |
| 14 | Win32.Alman | 1895646 (1.85%) |
| 15 | Trojan.DownLoader.42350 | 1876554 (1.83%) |
| 16 | Win32.HLLW.Autoruner.5555 | 1802659 (1.76%) |
| 17 | Trojan.MulDrop.16727 | 1635885 (1.60%) |
| 18 | Trojan.Blackmailer.1094 | 1594609 (1.56%) |
| 19 | VBS.Generic.548 | 1540792 (1.50%) |
| 20 | Win32.Sector.17 | 1200103 (1.17%) |
| Total scanned: | 730,787,813,411 |
| Infected: | 102,456,427 (0.0140%) |