Doctor Web virus activity overview: New Linux backdoor and other events of December 2014
Virus reviews | Hot news | All the news | Virus alerts
December 26, 2014
Viruses
Statistics collected by Dr.Web CureIt! demonstrate that the browser advertising plugins detected by Dr.Web as Trojan.BPlug.218 and Trojan.BPlug.341. are maintaining their leading position among the malicious programs detected on PCs in December. Trojan.Yontoo.115, another advertising Trojan program, ranks third in the December chart. Other malicious applications frequently identified during the past month by Dr.Web CureIt! include programs of the Trojan.Zadved and Trojan.LoadMoney families—they are all involved in downloading or displaying obtrusive advertisements.
According to the data gathered by Doctor Web statistics servers, BackDoor.Andromeda.404 was the malicious application most frequently detected in December; it accounted for 0.4% of the total number of malware programs identified. The malicious advertising program Trojan.LoadMoney.336 ranked second with 0.36%, while the installer of other malicious programs Trojan.InstallCore.16 (0.34%) ranked third.
The aforementioned BackDoor.Andromeda.404 was the malware most commonly found in email traffic— it constituted 2.28% of the total malware spread via email in December. Trojan.Hottrend.355 (0.87%) and Trojan.Fraudster.778 (0.67%) are also among the leaders. They noticeably crowded out the Trojan.Download programs that made the top ten a month ago.
The botnets that are being closely monitored by Doctor Web security researchers continue to engage in malicious activity. In particular, the botnet comprised of machines compromised by the file infector Win32.Sector experienced 50,500 connections from infected machines on a daily basis, 10% fewer than in the previous month. Yet the number of Macs infected with BackDoor.Flashback.39 hardly budged throughout the month. In December, the average was still about 13,500.
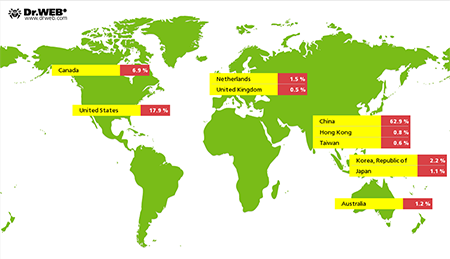
Linux.BackDoor.Gates.5 is still mounting DDoS attacks on various websites. As before, its main targets reside in China. In December, Doctor Web registered 5,624 IP addresses that came under attack (1,911 more than in November). It should also be noted that the geography of the attacks expanded significantly: server addresses registered in Australia, Taiwan, Netherlands, and the United Kingdom are being found more and more frequently among the targets. Information about the attacked hosts, arranged by country, is provided in the figure below:
Backdoor for Linux
In December, Doctor Web virus analysts examined a multi-component malware program for Linux. Dubbed Linux.BackDoor.Fysbis.1, it was presumably crafted by the cyber espionage group Sednit. The sample researched by Doctor Web incorporated two modules. One of them was used to perform various operations with the infected machine’s file system, while the second one facilitated the execution of commands issued by intruders.
This malicious program can operate using superuser privileges (root), as well as under an ordinary Linux account—in the latter case, the malware installs itself into a different directory and uses another name for its executable file.
Upon its initial launch, Linux.BackDoor.Fysbis.1 checks if its copy is already operating in the system and determines whether it is set to be launched automatically at startup. If that's not the case, the malware copies itself to the hard drive and ensures that it will be launched automatically.
The command and control (C&C) server address is hardcoded into the backdoor. The backdoor stores its encrypted configuration data and other information required for its operation in an SQLite3 database.
Linux.BackDoor.Fysbis.1 can receive various commands from the attackers’ C&C server and execute them on the infected machine.
Malware for Android
In the last month of 2014, handheld users were in to receive a large number of pre-holiday malicious gifts. Cybercriminals employed all kinds of Trojans to attack smart phones and tablets running Android. In particular, in December a number of malicious programs were found pre-installed on some low-cost Android-powered devices. One of these Trojans, which entered the virus database as Android.Backdoor.126.origin, could perform malicious tasks upon receiving the corresponding commands from the server; for example, it could plant a message composed by criminals among incoming SMS on the device. Since criminals could add any content they wanted into messages like these, users whose devices were compromised by Android.Backdoor.126.origin could be lured into all sorts of scams.Android.Backdoor.130.origin, was another malicious program lurking on some Android devices, but this one allowed its makers to accomplish a wider range of objectives. In particular, it could send short messages; make calls; display ads; download, install and launch applications without user consent; and transmit all kinds of information to its C&C server.
Also in December, a host of other Trojans that could be used to steal confidential information and money from bank accounts were discovered. For example, discovered in mid-month, Android.SmsBot.213.origin was distributed under the guise of a game and enabled attackers to intercept and send SMS messages. It could also upload confidential data found on infected mobile devices onto a server. Access to SMS capabilities allowed Android.SmsBot.213.origin to transmit a variety of sensitive data to cybercriminals, including information about credit and debit cards used in online banking. As a result, the guileful intruders gained control over user accounts and could carry out transactions as they saw fit.
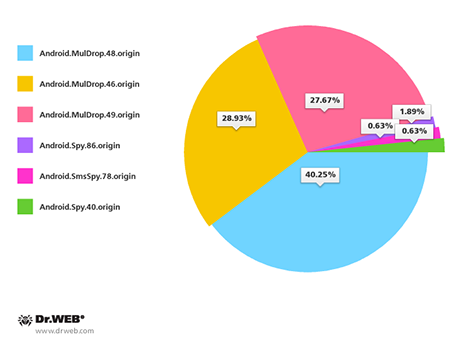
Malicious programs spread in South Korea were again found among the banking Trojans discovered in December. As before, to infect devices, criminals dispatched mass short messages containing download links. Throughout the month, Doctor Web registered about 160 such spam campaigns, most of them aimed at spreading malicious applications such as Android.MulDrop.48.origin, Android.MulDrop.46.origin, Android.MulDrop.49.origin and Android.Spy.86.origin.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live