New ransomware sets unlock password on compromised Android handhelds
Real-time threat news | Hot news | All the news | Virus alerts
September 10, 2014
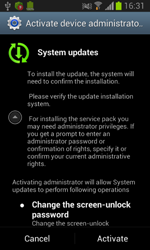
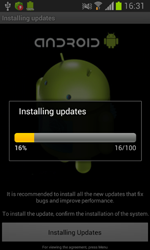
Dubbed by Dr.Web as Android.Locker.38.origin, the new malicious locker represents a growing family of ransomware that locks handhelds and demands a ransom to unlock them. This Android extortionist is spread in the guise of a system update. When launched, it requests access to the device's administrative features. After that the Trojan mimics update installation, removes its icon from the home screen, reports back to a remote server that the infection has been successful and awaits further instructions.
 |
 |
 |
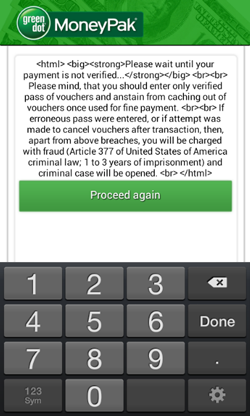
The command to lock the targeted device can be given via a JSON request from a web server as well as via an SMS message containing the directive set_lock. Similarly to other ransomware of the Android.Locker family, Android.Locker.38.origin locks the device's screen and shows a ransom demand that can't be closed.
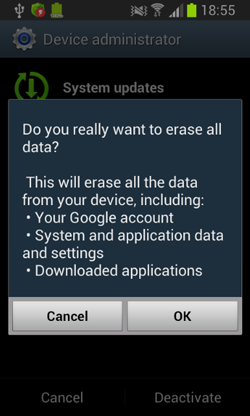
However, if the affected user still tries to delete the extortionist by depriving it of administrator privileges, Android.Locker.38.origin engages an additional lock. This ability distinguishes it from other similar threats for Android.
First, the Trojan switches an infected device into standby mode by using the standard phone feature to lock the screen. Once the lock screen is turned off, the malicious program displays a fake warning that all the data stored in the device's memory has been removed.
Once a selected action is confirmed, the ransomware brings up the lock screen again and activates a feature that requires the user to enter a password to toggle off the standby mode. Even if the feature hasn’t been used before, the malicious locker sets its own password: "12345". Thus, the infected smart phone or tablet is locked until the criminals involved get their ransom (the lock can be removed with the set_unlock command) or the user resets all the device's settings to default.
In addition to locking handhelds, Android.Locker.38.origin can also act as an SMS bot and send various messages when commanded to do so by criminals. This can result in additional financial losses for the user.
Devices running Dr.Web Anti-virus for Android are well protected from this malicious program.