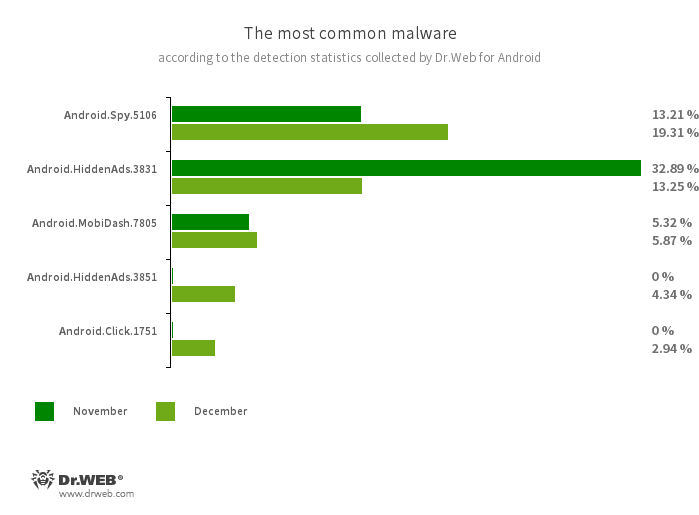
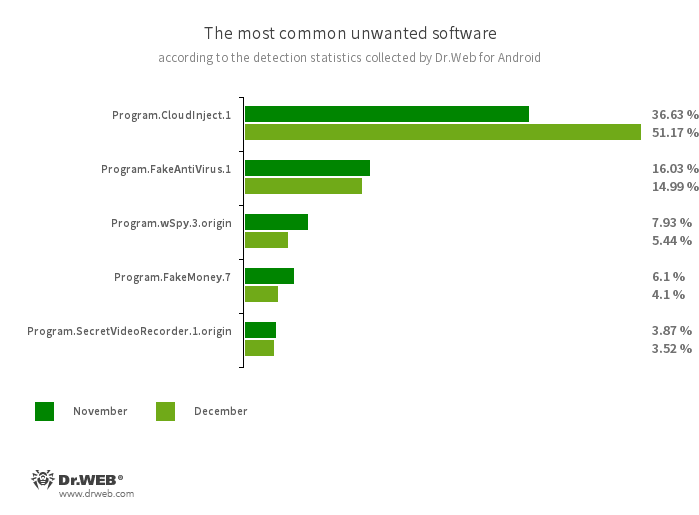
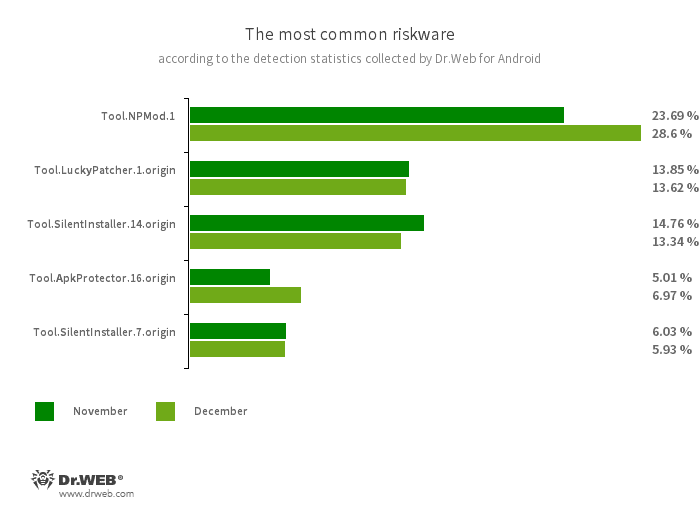
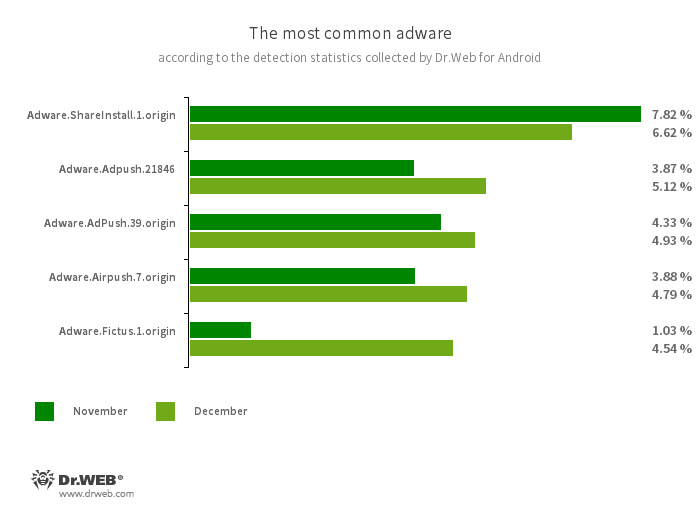
According to detection statistics collected by the Dr.Web for Android anti-virus, in December 2023, adware trojans from the Android.HiddenAds family were again the most active malicious programs. However, users encountered them 53.89% less often, compared to the previous month. In addition, the number of banking malware and spyware trojan attacks also decreased—by 0.88% and 10.83%, respectively.
Over the course of the final month of 2023, Doctor Web’s virus analysts discovered other malicious fake apps from the Android.FakeApp family on Google Pay. These were used in a variety of fraudulent schemes. Moreover, our specialists found more websites through which malicious actors were distributing fake crypto-wallet software.
PRINCIPAL TRENDS IN DECEMBER
- Adware trojans from the Android.HiddenAds family were detected most often on protected devices
- The activity of banking trojans and malicious spyware apps decreased
- New malicious programs were discovered on Google Play
- Our analysts identified more websites distributing fake crypto-wallet software for devices running the Android and iOS operating systems
Threats on Google Play
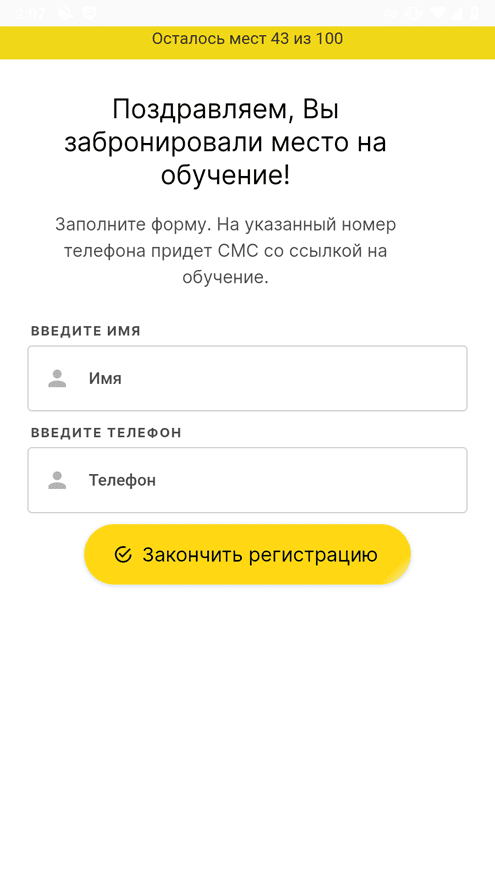
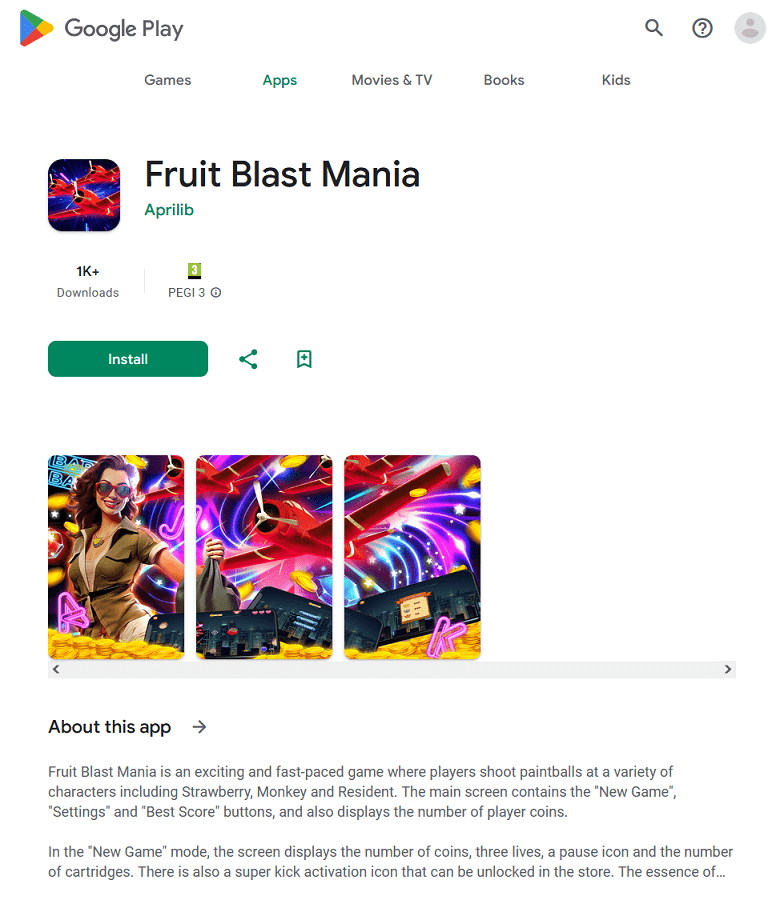
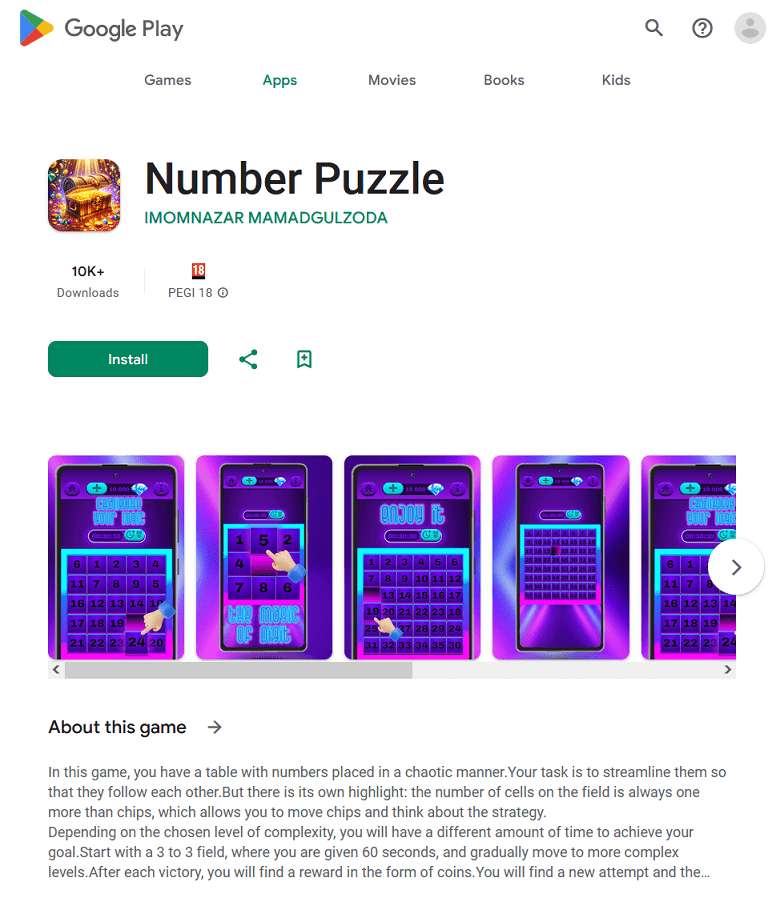
In December 2023, Doctor Web’s specialists discovered new trojan apps from the Android.FakeApp family on Google Play. For example, malicious actors disguised Android.FakeApp.1564 as a debt-tracking program. The Android.FakeApp.1563 trojan was hiding in survey software. And cybercriminals passed the Android.FakeApp.1569 trojan off as an instrument that could help users increase their productivity and develop good habits.
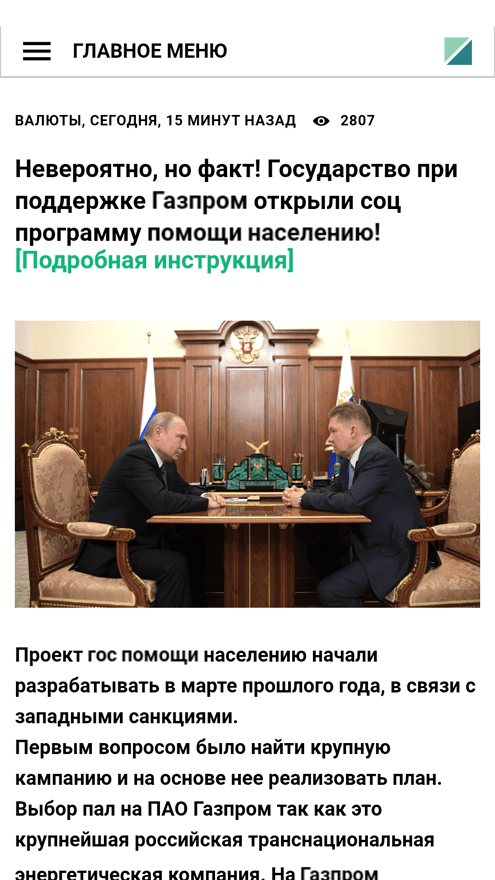
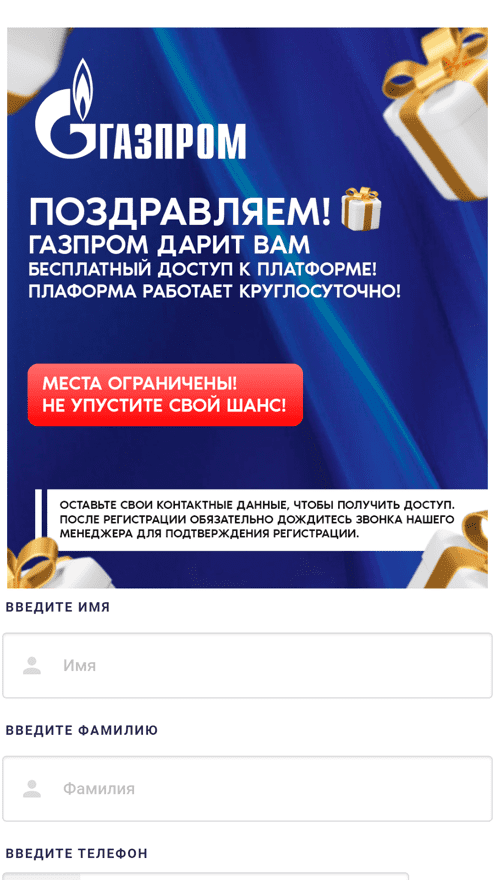
All these fake apps loaded fraudulent finance-related websites that copied the design of the genuine websites of banks, news agencies, and other well-known organizations. In addition, the corresponding companies’ names and logos were used in their design to further mislead potential victims. On such fraudulent websites, users were offered the chance to become investors, take financial literacy training, receive financial support, etc. At the same time, they were asked to provide personal data―allegedly to register an account and get access to the corresponding services.
Examples of websites loaded by these trojans:
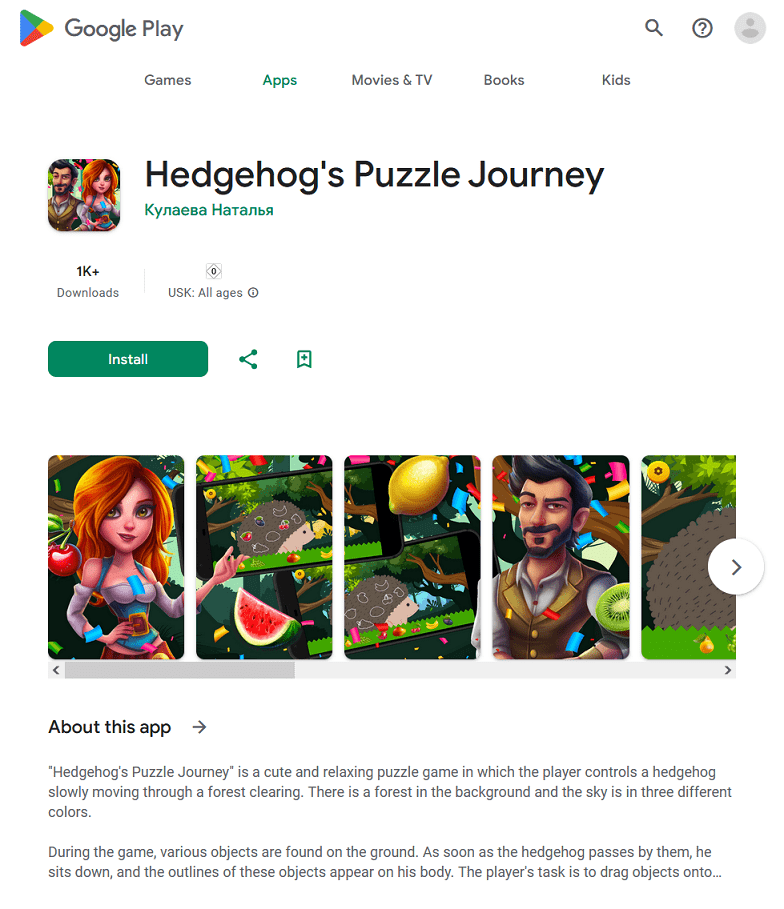
Other trojans, like Android.FakeApp.1566, Android.FakeApp.1567, and Android.FakeApp.1568, were distributed as games:
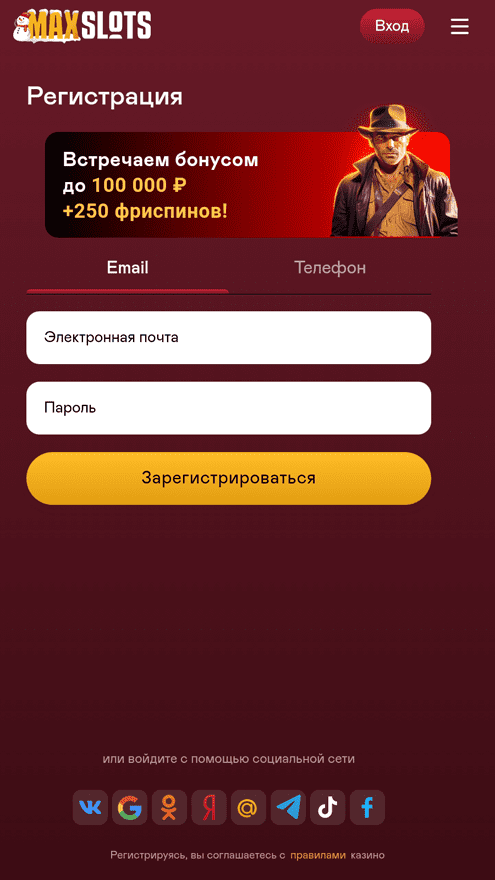
Instead of launching the actual games, they could load bookmaker and online casino websites, as shown in the example below.
One of these trojans operating in gaming mode:
One of the websites it loaded:
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.
Indicators of compromise
Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products
Free download