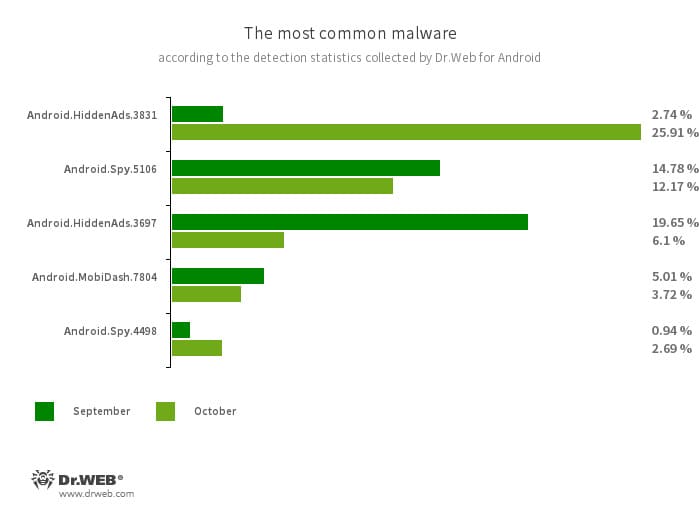
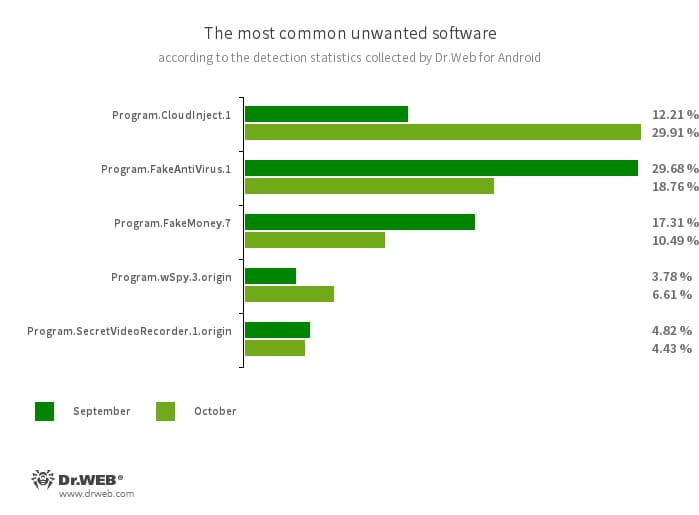
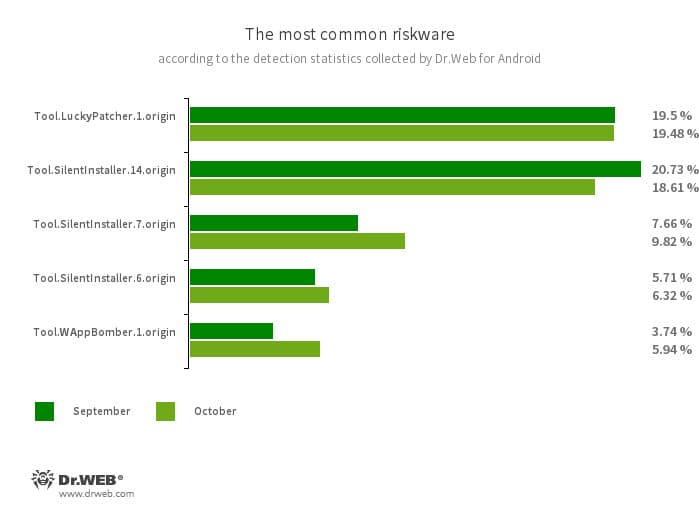
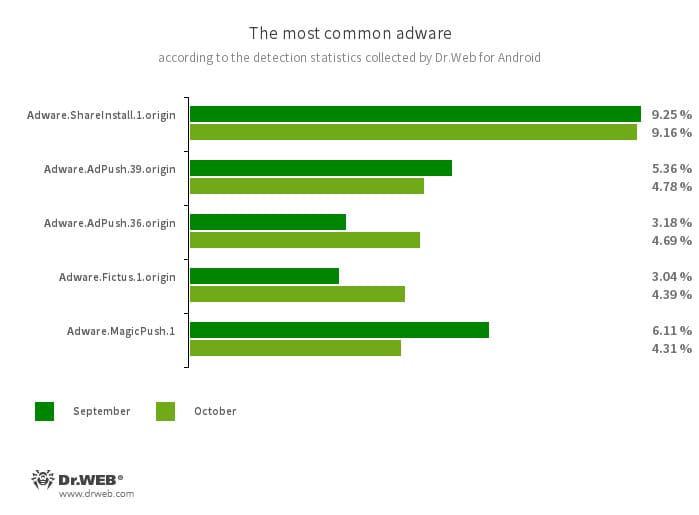
According to detection statistics collected by Dr.Web for Android, in October 2023, adware trojans from the Android.HiddenAds family were most often detected. Their activity increased by 46.16%, compared to the previous month. The second most widespread adware trojans, which belong to the Android.MobiDash family, also increased in number—by 7.07%. In addition, users encountered spyware trojans and banking malware more often—by 18.27% and 10.73%, respectively.
Over the course of October, Doctor Web’s specialists discovered more threats on Google Play. Among them were dozens of various fake apps from the Android.FakeApp family, which cybercriminals use for fraudulent purposes. Also uncovered were Android.Proxy.4gproxy trojans, which turn Android devices into proxy servers.
PRINCIPAL TRENDS IN OCTOBER
- An increase in adware trojan activity
- An increase in spyware trojan and banking malware activity
- The emergence of many new malicious apps on Google Play
Threats on Google Play
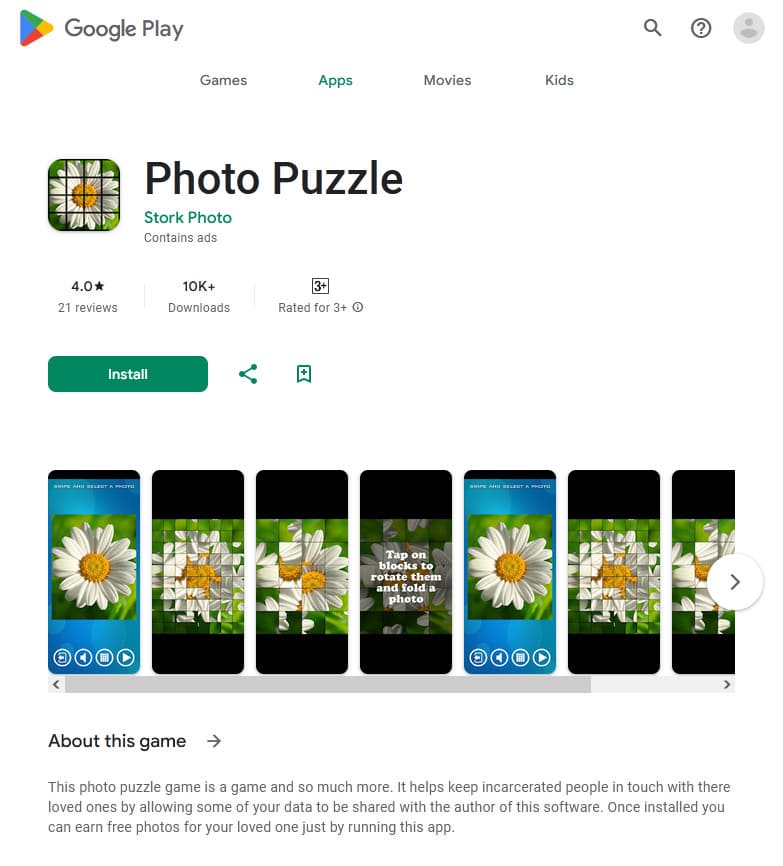
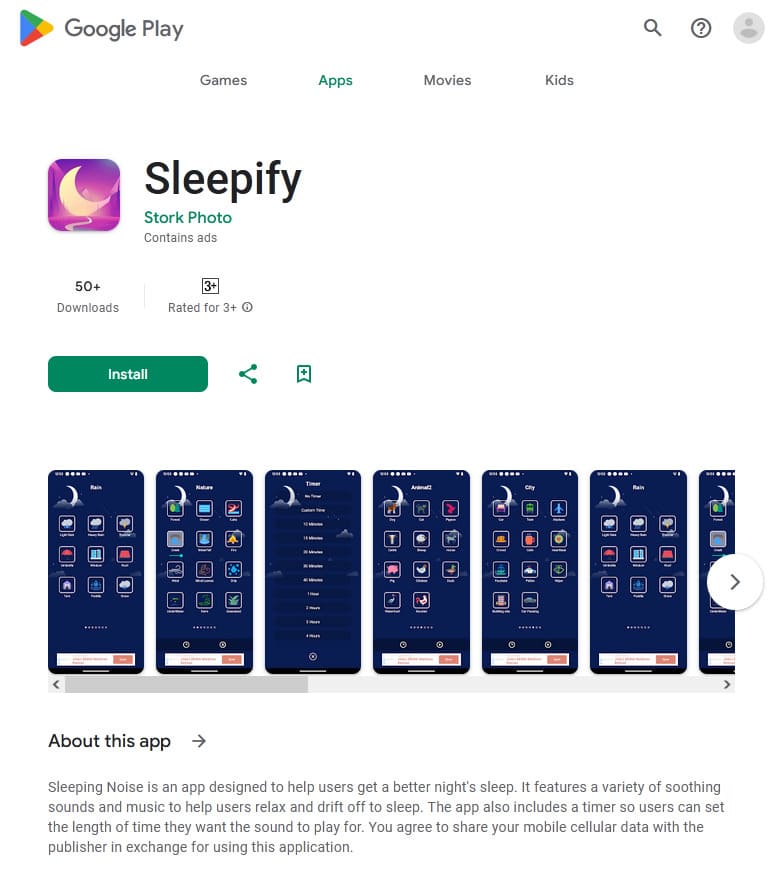
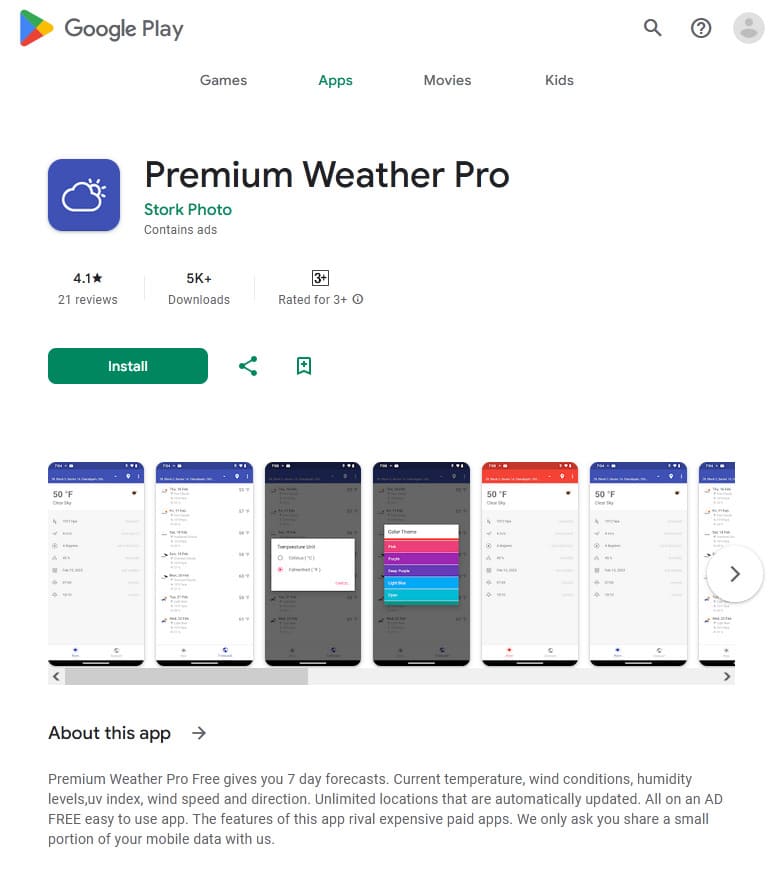
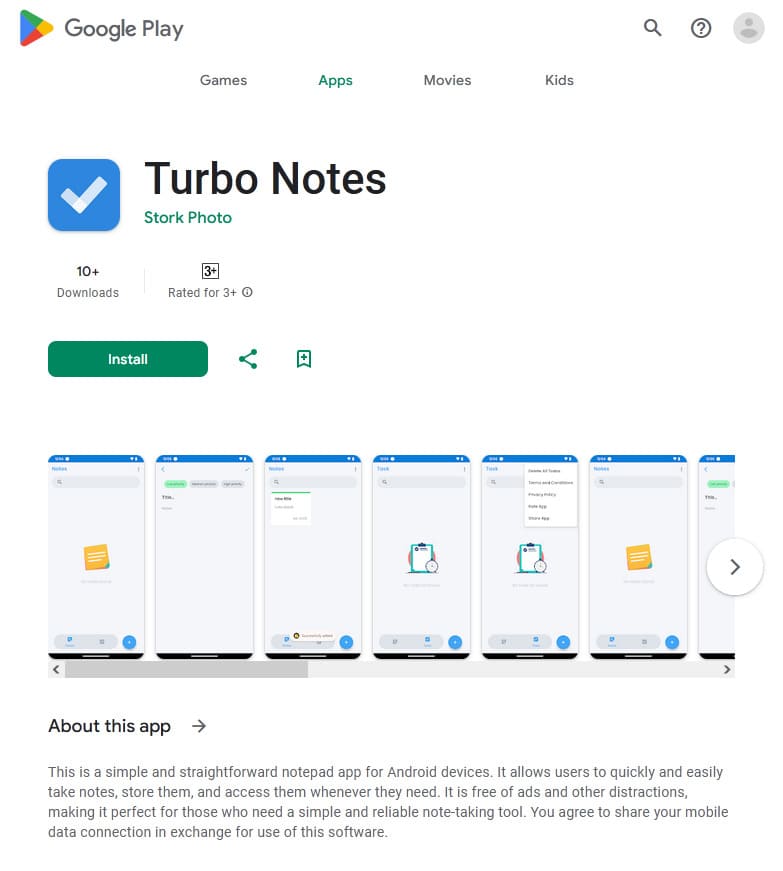
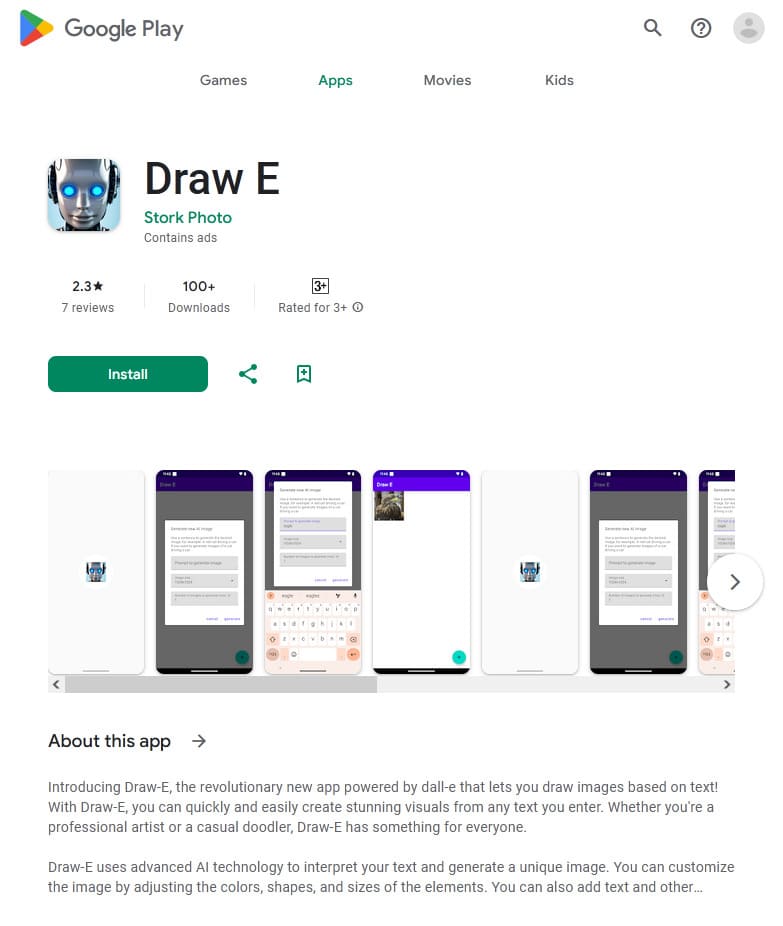
In October, Doctor Web’s virus analysts discovered over 50 malicious apps on Google Play. Among them were the Android.Proxy.4gproxy.1, Android.Proxy.4gproxy.2, Android.Proxy.4gproxy.3, and Android.Proxy.4gproxy.4 trojans, which turned infected devices into proxy servers and covertly transmitted third-party traffic through them. Various modifications of the first trojan were disguised as a Photo Puzzle game, a Sleepify program designed to help users with insomnia, and a tool called Rizzo The AI chatbot, which provided the functionality needed to work with a chat bot. The second trojan was hidden in the Premium Weather Pro weather forecast app. The third trojan was built into the Turbo Notes notepad app. And the last one was distributed by malicious actors as a Draw E program for creating images with the help of a neural network.
A special utility called 4gproxy (Dr.Web detects it as Tool.4gproxy) was built into these apps. This tool allows Android devices to be used as proxy servers. It is not malicious in itself and can be used for legitimate purposes. However, in the case of these newly discovered trojans, the proxy server functionality operates without users’ involvement and their explicit consent.
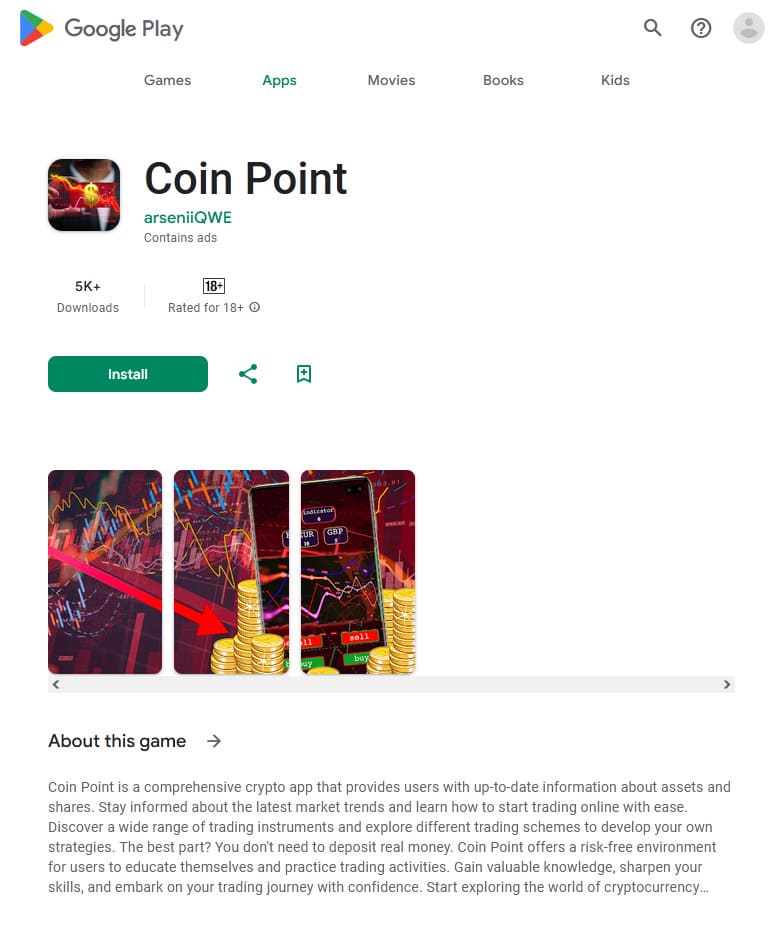
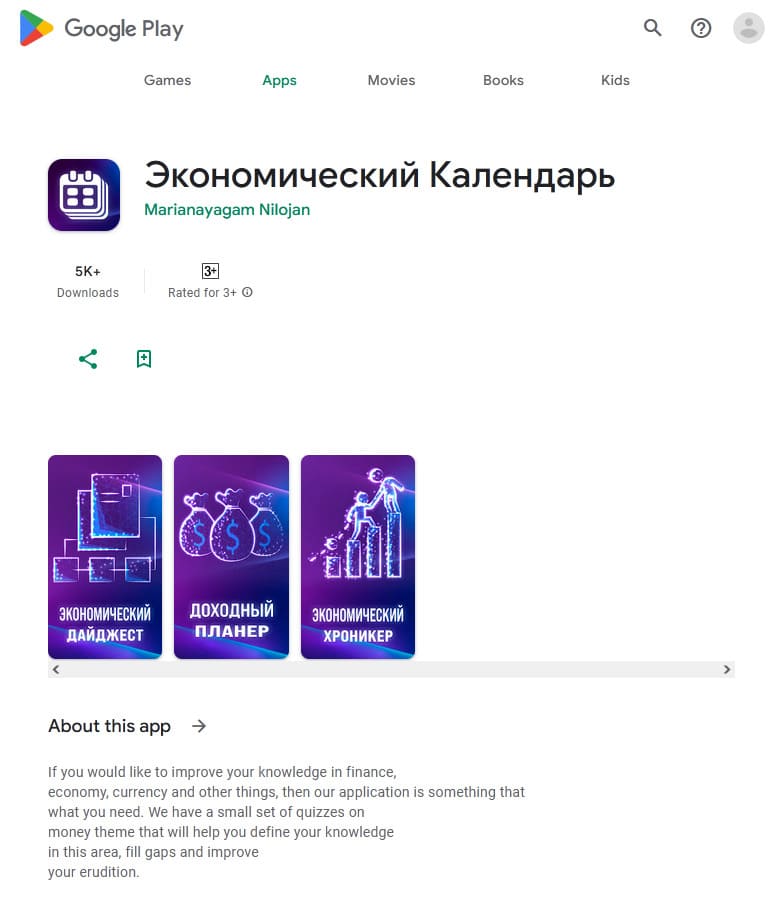
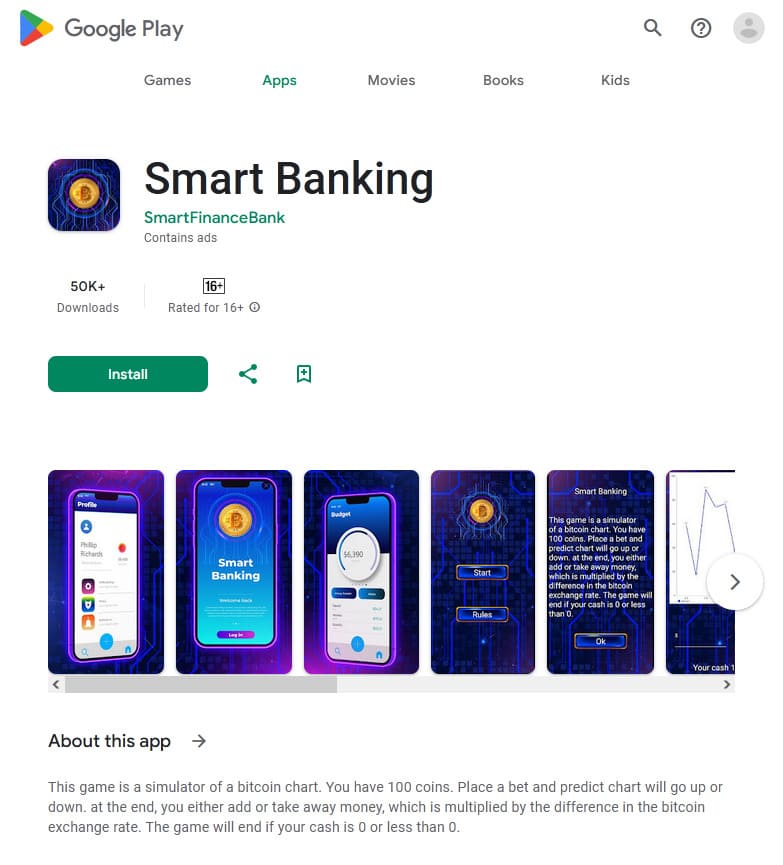
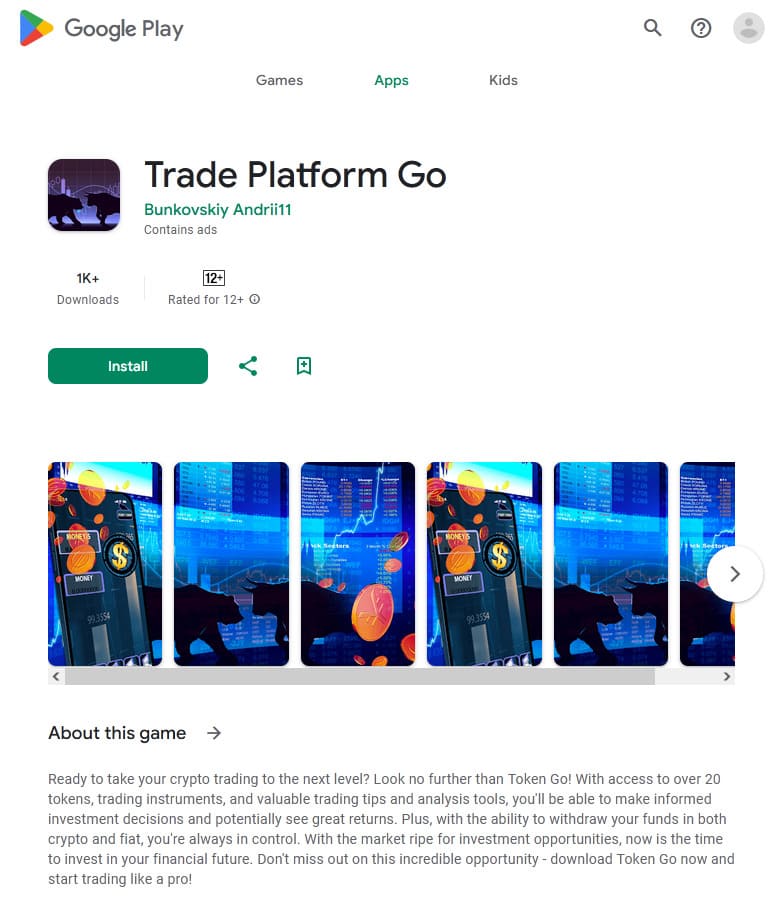
At the same time, our specialists uncovered dozens of new trojan apps from the Android.FakeApp family. Some of them again were distributed as financial apps (for example, trojans like Android.FakeApp.1459, Android.FakeApp.1460, Android.FakeApp.1461, Android.FakeApp.1462, Android.FakeApp.1472, Android.FakeApp.1474, and Android.FakeApp.1485). Their main task is to load fraudulent websites that invite potential victims to become investors. Malicious actors ask users to provide their personal information and invite them to invest their money in supposedly profitable financial projects or instruments.
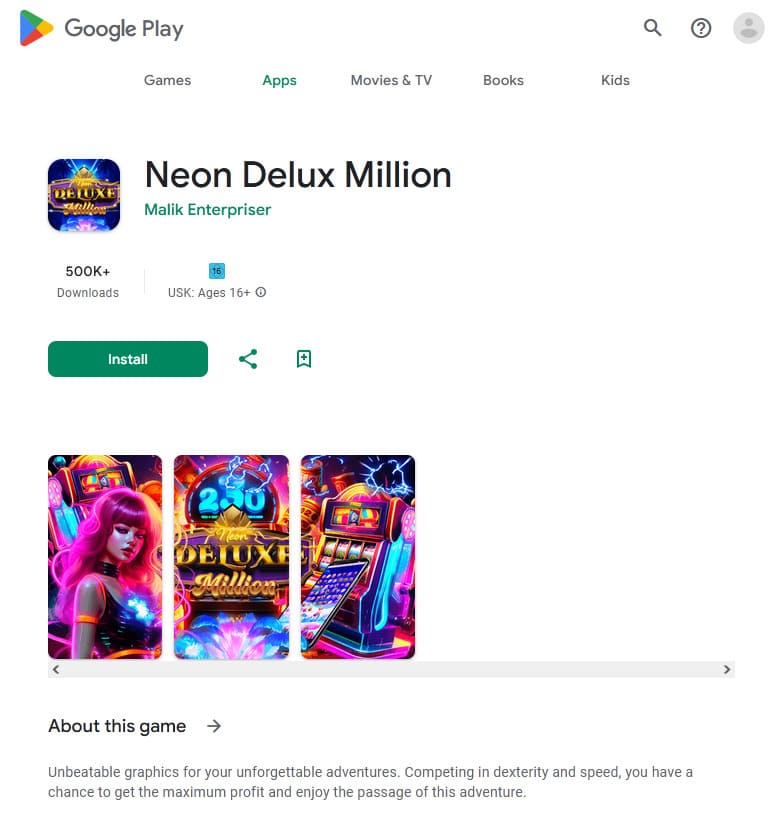
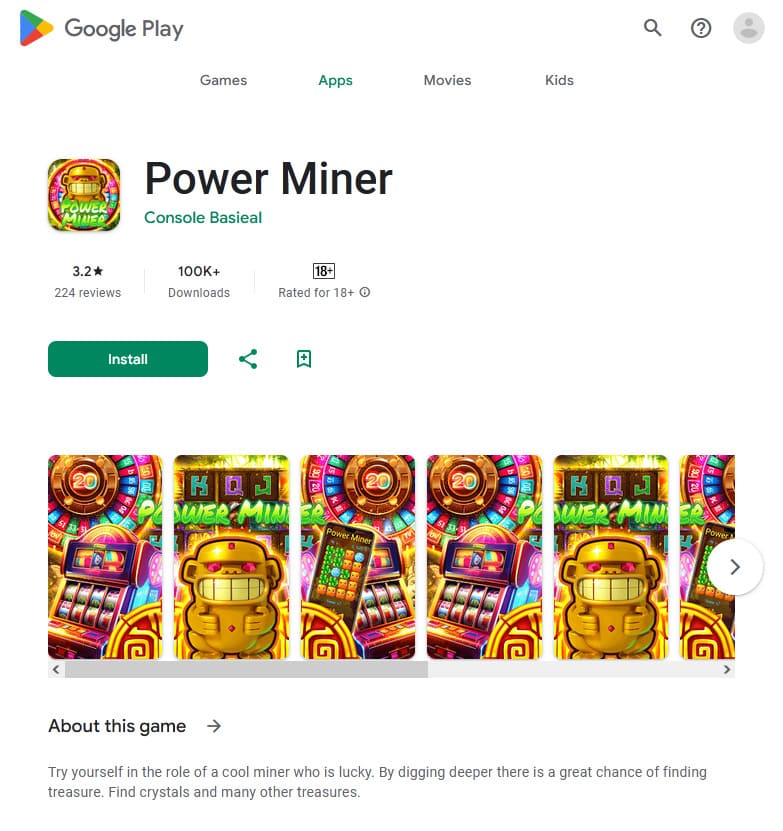
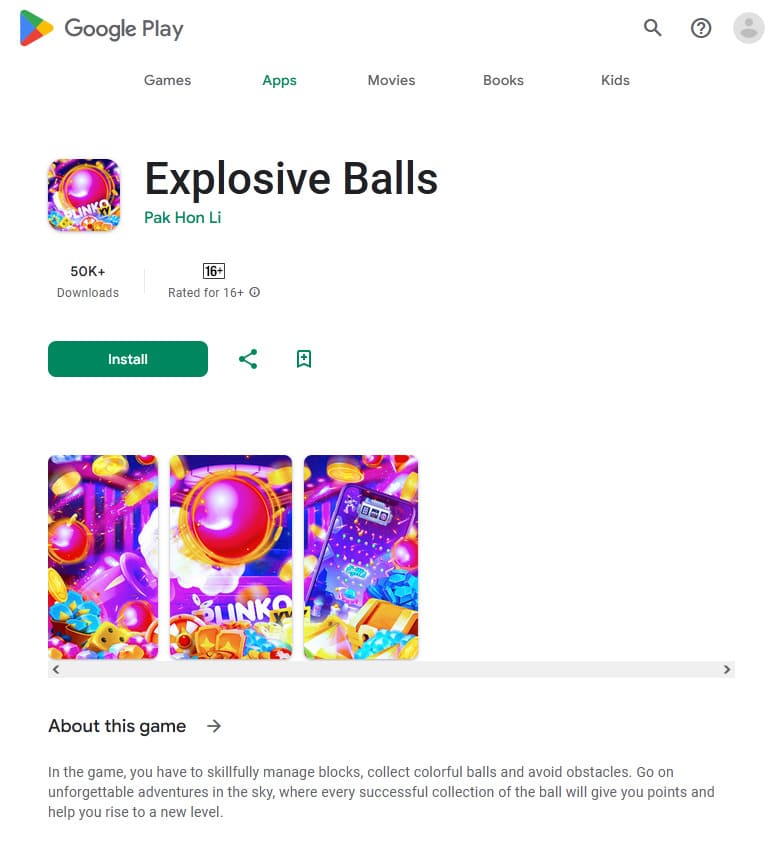
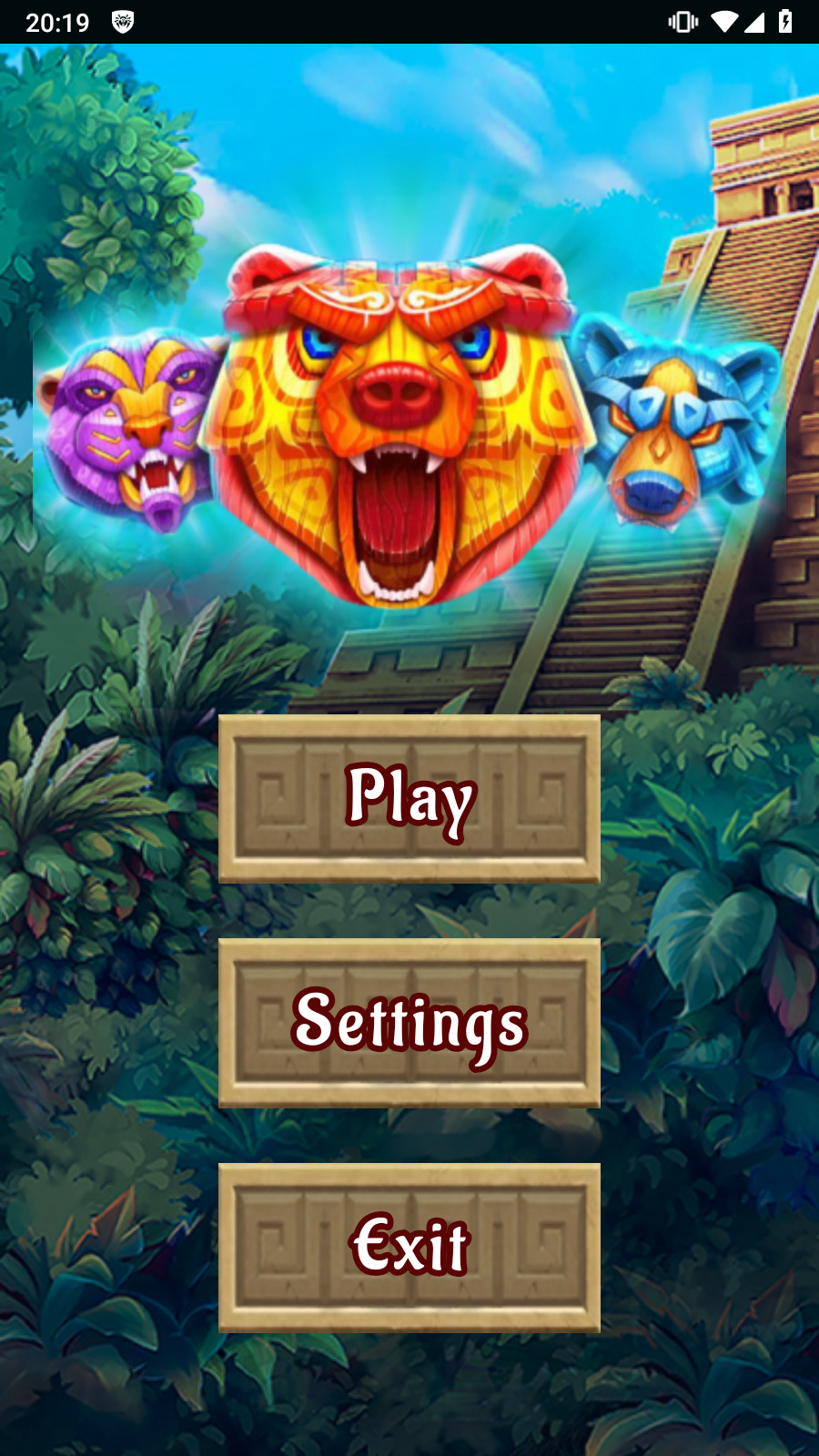
Other fake programs (like Android.FakeApp.1433, Android.FakeApp.1444, Android.FakeApp.1450, Android.FakeApp.1451, Android.FakeApp.1455, Android.FakeApp.1457, Android.FakeApp.1476, and others) were again disguised as various games. Under certain conditions, instead of launching games, these loaded online casino or bookmaker websites.
Examples of how these trojan apps work as games:
Examples of the online casino and bookmaker sites they load:
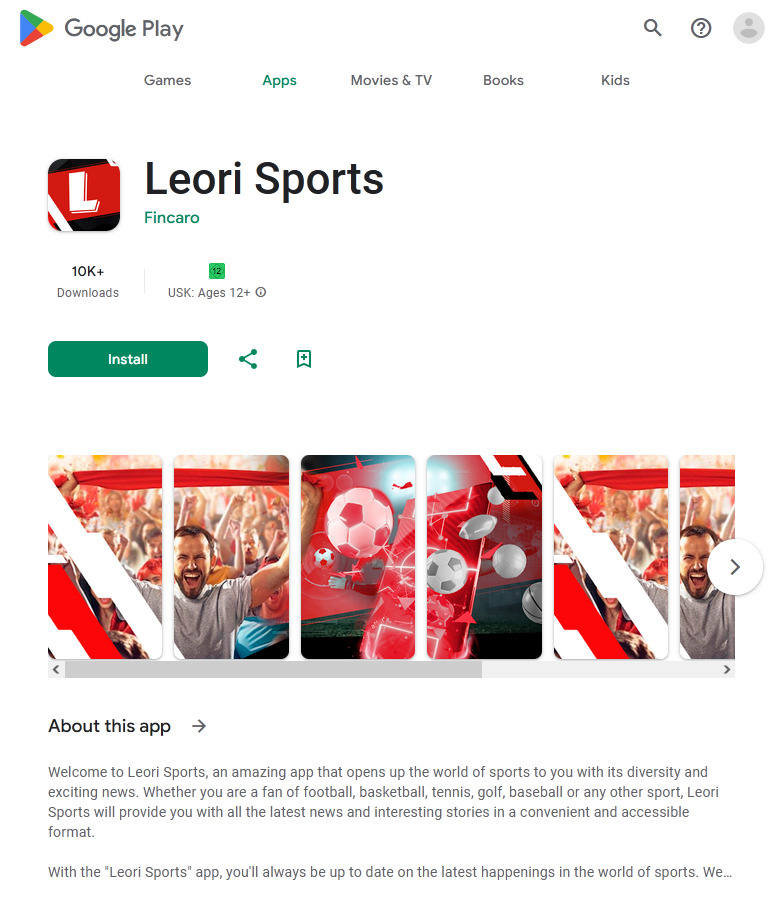
Similar functionality was found in the Android.FakeApp.1478 trojan, which was hiding in an app for accessing sports news and publications. It could load bookmaker sites.
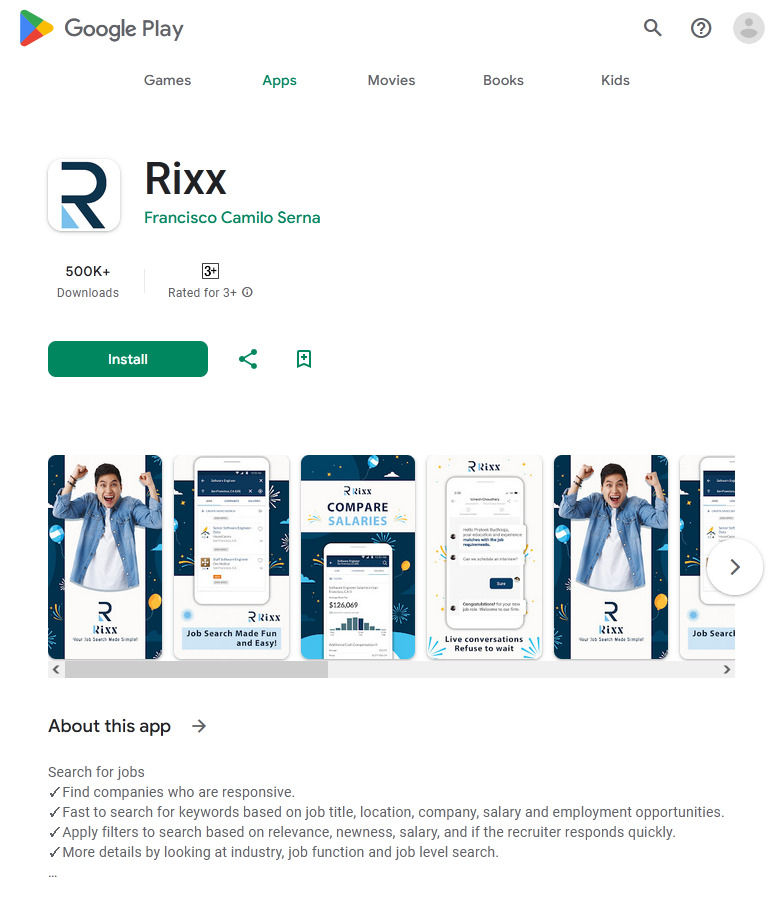
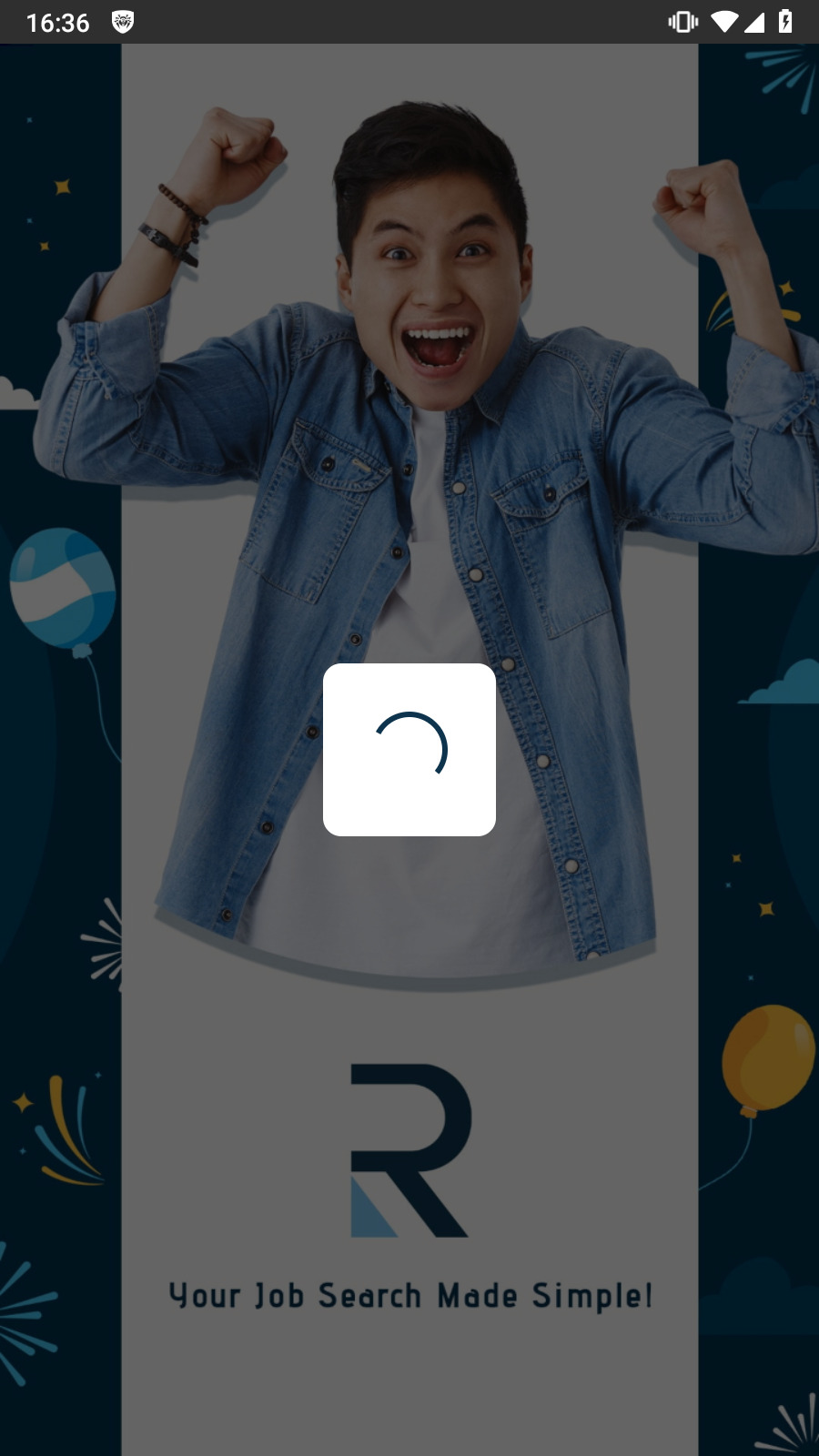
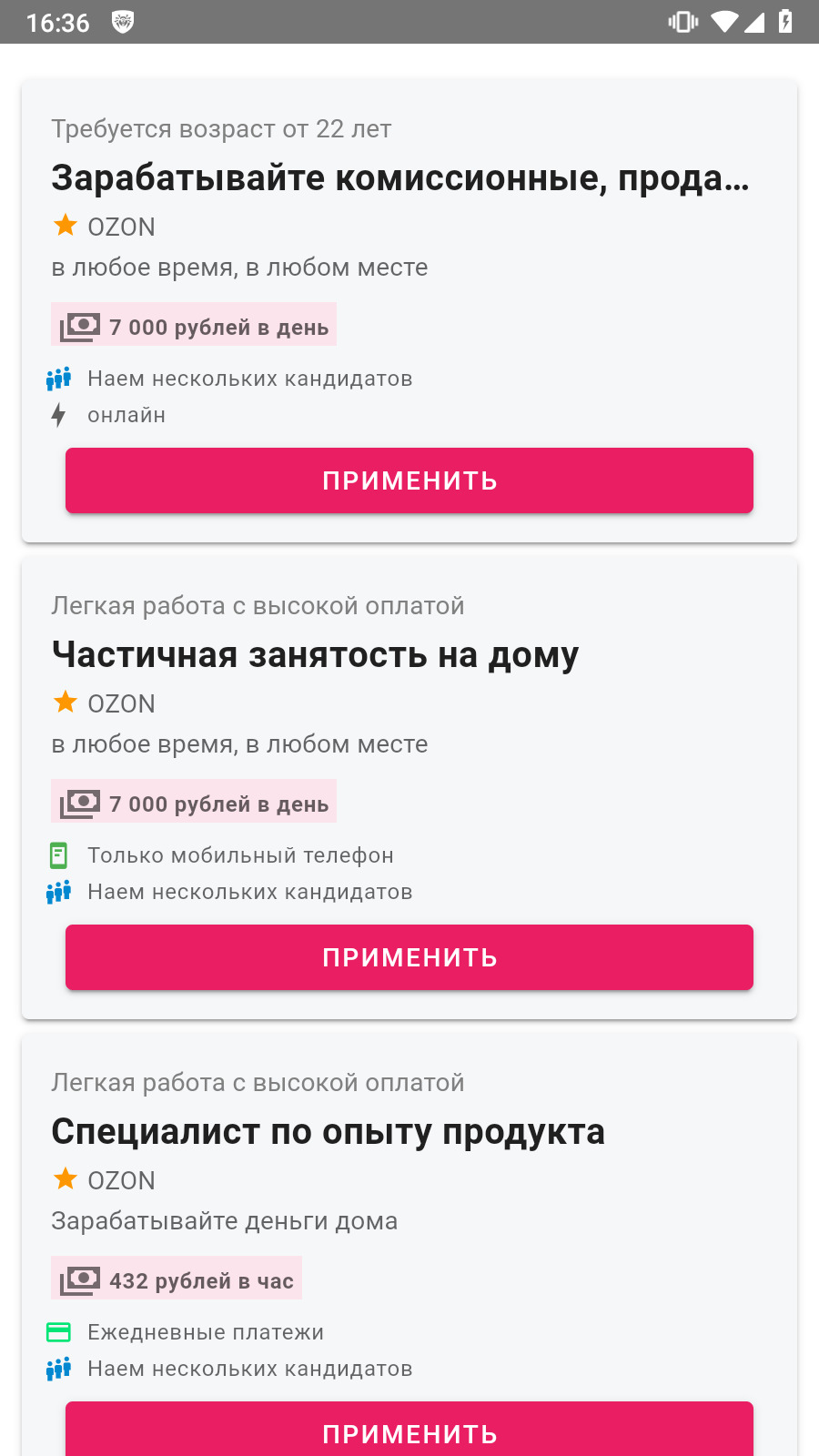
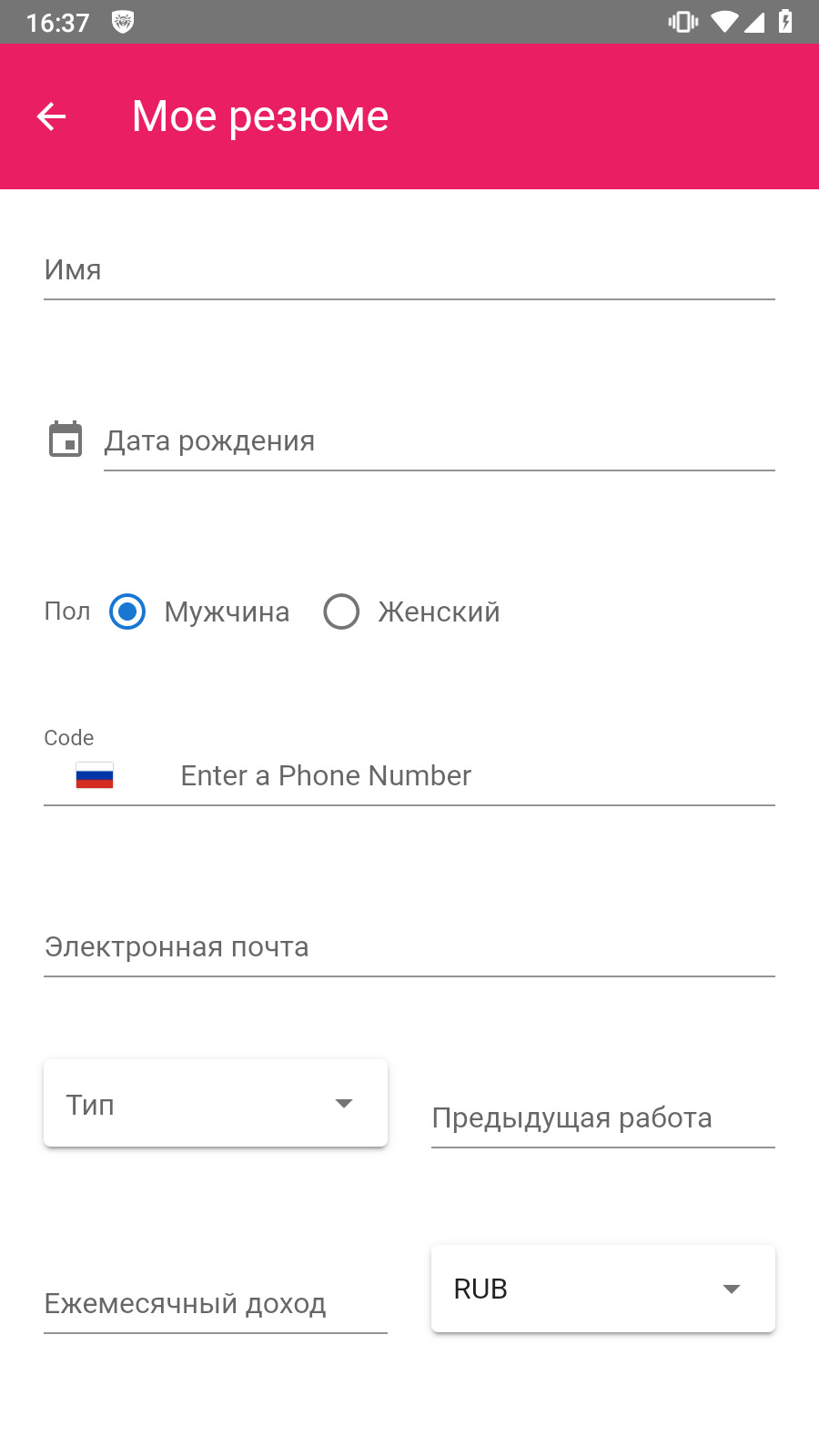
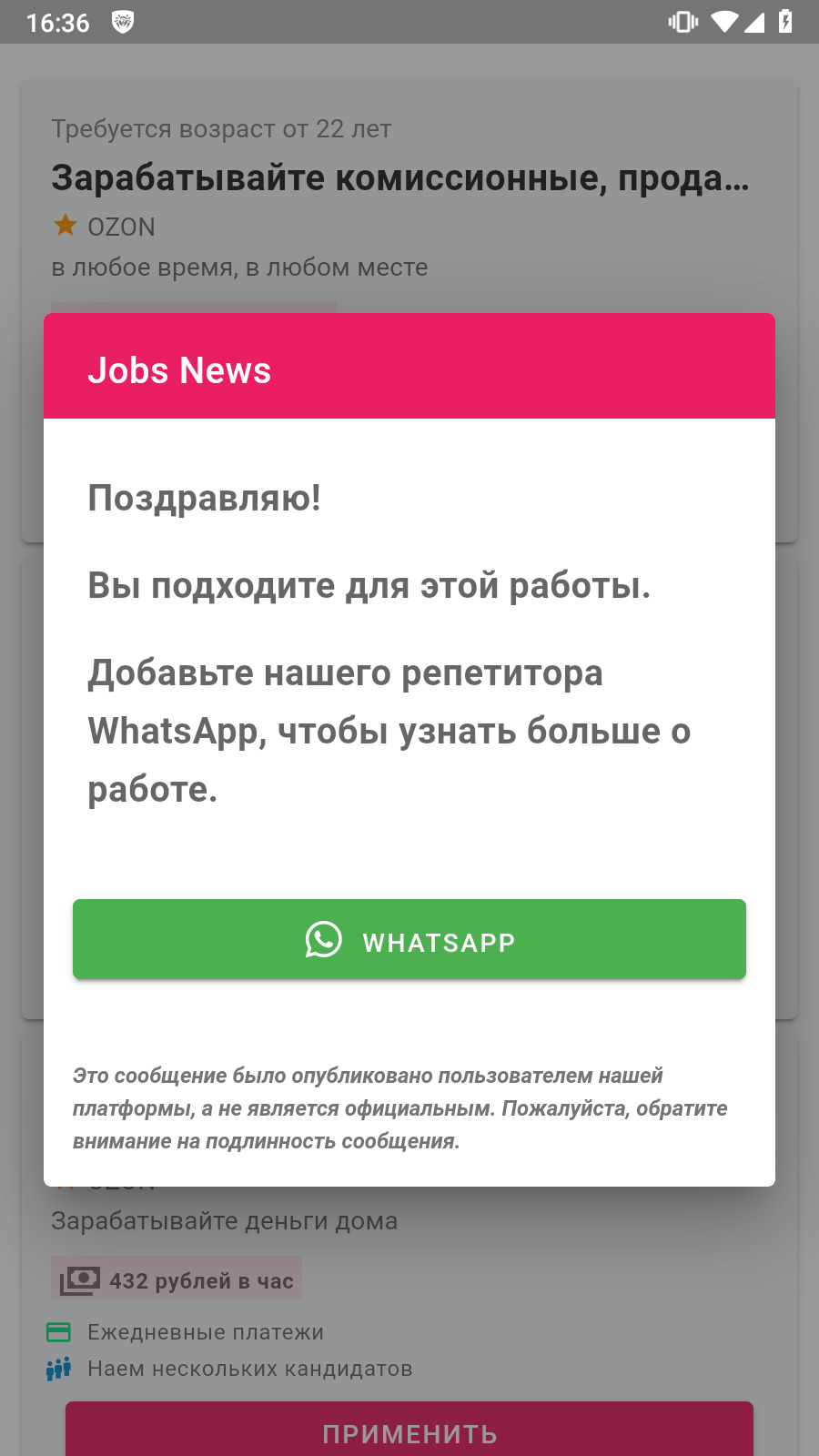
In addition, new trojan apps were found that allegedly could help Android device owners search for a job. One was called Rixx (Android.FakeApp.1468), and the other—Catalogue (Android.FakeApp.1471). Upon launching, these malicious apps show a fake vacancy listing. When potential victims try to respond to one of the job offers, they are asked to enter their personal data into a special form, or to contact the “employer” via instant messengers, like WhatsApp or Telegram.
Below is an example of how one of these malicious apps works. The trojan displays a phishing form, disguised as a window for creating a resume, or asks the user to contact the “employer” via the messenger.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.
Indicators of compromise
Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products
Free download