November 22, 2023
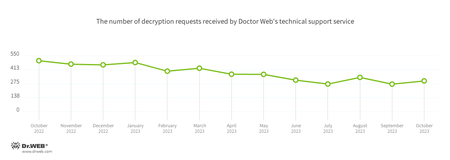
The number of user requests to decrypt files affected by encoder trojans increased by 11.48%, compared to the previous month. The most common encoder in October was Trojan.Encoder.26996, which accounted for 22.54% of the incidents recorded. Second place was taken by Trojan.Encoder.3953, with a share of 15.49%. Ranked third, Trojan.Encoder.35534 had a share of 7.51%.
Over the course of October, Doctor Web’s specialists uncovered dozens of malicious apps on Google Play. Among them were trojans that turned Android devices into proxy servers, as well as fake apps that cybercriminals used for fraudulent purposes.
Principal trends in October
- A decrease in the total number of detected threats
- An increase in the number of user requests to decrypt files affected by trojan encoders
- The emergence of many new malicious apps on Google Play
According to Doctor Web’s statistics service
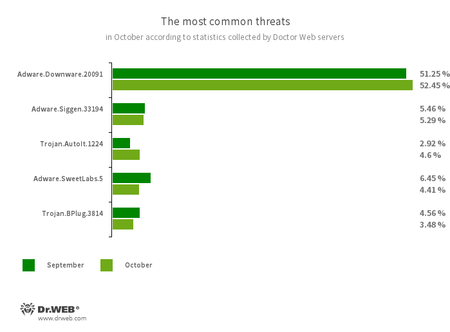
The most common threats in October:
- Adware.Downware.20091
- Adware that often serves as an intermediary installer of pirated software.
- Adware.Siggen.33194
- The detection name for a freeware browser that was created with an Electron framework and has a built-in adware component. This browser is distributed via various websites and loaded onto users’ computers when they try downloading torrent files.
- Trojan.AutoIt.1224
- The detection name for a packed version of the Trojan.AutoIt.289 malicious app, written in the AutoIt scripting language. This trojan is distributed as part of a group of several malicious applications, including a miner, a backdoor, and a self-propagating module. Trojan.AutoIt.289 performs various malicious actions that make it difficult for the main payload to be detected.
- Adware.SweetLabs.5
- An alternative app store and an add-on for Windows GUI (graphical user interface) from the creators of “OpenCandy” adware.
- Trojan.BPlug.3814
- The detection name for a malicious component of the WinSafe browser extension. This component is a JavaScript file that displays intrusive ads in browsers.
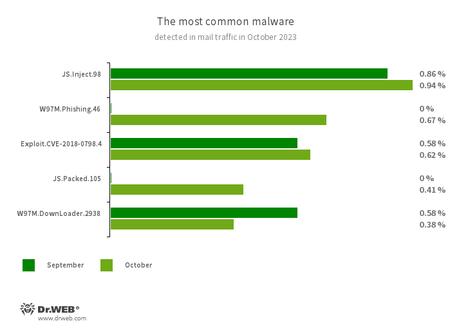
Statistics for malware discovered in email traffic
- JS.Inject
- A family of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- W97M.Phishing.46
- Microsoft Word phishing documents that target users who want to become investors. They contain links to fraudulent websites.
- Exploit.CVE-2018-0798.4
- An exploit designed to take advantage of Microsoft Office software vulnerabilities and allow an attacker to run arbitrary code.
- JS.Packed.105
- An encrypted JavaScript containing the JS.BackDoor.49 backdoor. This backdoor executes remote server commands, can run executable files and libraries, and also has keylogger functionality.
- W97M.DownLoader.2938
- A family of downloader trojans that exploit vulnerabilities in Microsoft Office documents. They can also download other malicious programs to a compromised computer.
Encryption ransomware
In October, the number of requests to decrypt files affected by encoder trojans increased by 11.48%, compared to September.
The most common encoders of October:
- Trojan.Encoder.26996 — 22.54%
- Trojan.Encoder.3953 — 15.49%
- Trojan.Encoder.35534 — 7.51%
- Trojan.Encoder.30356 — 2.35%
- Trojan.Encoder.37369 — 2.35%
Dangerous websites
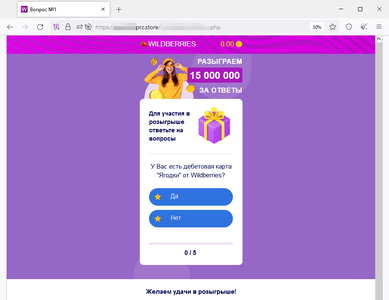
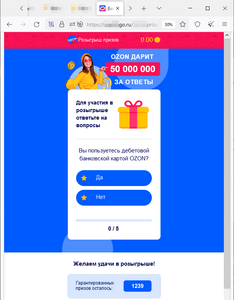
In October, Doctor Web Internet analysts identified more websites that fraudsters were trying to pass off as legitimate resources of well-known online stores by mimicking their appearance. Visitors of such sites can allegedly participate in a drawing for money prizes. To do this, they are asked to take a survey and play a game, which, in fact, is a simulation as the so-called “victory” is pre-programmed into it. To “get” the prize, users have to pay a “commission” to have the money transferred to their bank account. In the end, scammers’ victims do not receive any payouts. On the contrary, they transfer their own money to the fraudsters and also risk revealing their bank card details.
Examples of such sites:
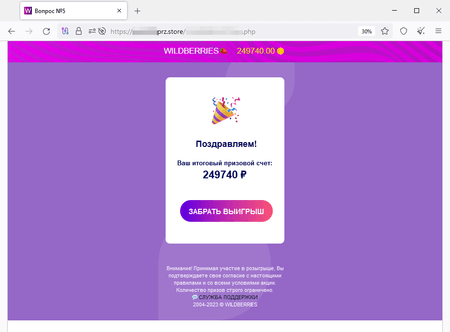
During the prize “draw”, the site’s visitor allegedly won 249,740 rubles:
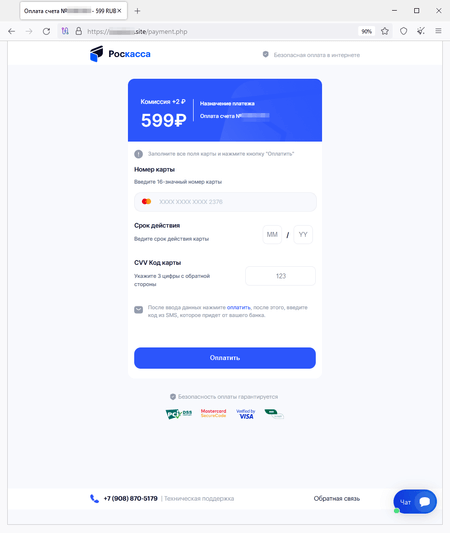
A phishing form for paying the “commission” to receive non-existent winnings:
Malicious and unwanted programs for mobile devices
According to detection statistics collected by Dr.Web for Android, in October, users were most often attacked by adware trojans from the Android.HiddenAds family. Moreover, the activity of banking trojans and spyware malicious apps increased, compared to the previous month.
Over the course of October, Doctor Web’s specialists discovered over 50 malicious programs on Google Play. Among them were Android.Proxy.4gproxy trojans, which turned infected devices into proxy servers, and more fraudulent apps from the Android.FakeApp family.
The following October events involving mobile malware are the most noteworthy:
- An increase in the activity of adware trojan apps,
- An increase in banking malware and spyware trojan activity,
- The detection of new malicious apps on Google Play.
To find out more about the security-threat landscape for mobile devices in October, read our special overview.