January 11, 2010
Fraud techniques—2010’s “Top Ten”
Below you can find information about the malicious programs used in fraud schemes during 2010. Following the long-standing tradition of top ten charts, we’ll start from the bottom. Next to the name of each scheme or malware type involved, you’ll see the corresponding name given to it by Dr.Web.
10. Pseudo-services
Offering interesting and often illegally acquired information for a small fee is a common fraud scheme. Users pay for such services with short messages that cost around 10 USD. Promised secrets range from private information about social network users to intelligence information from top-secret archives The quality of such services is questionable. Moreover, promises of this sort are often no more than bluffs — the criminals provide nothing in exchange for the money they receive. Links to bogus sites where such services are offered are usually spread over banner networks on sites providing access to free content.
9. Fake archives. Trojan.SMSSend
Criminals set up fake torrent trackers and file storages that supposedly contain popular music, movies, and e-books. As a consequence, such bogus resources top the results returned by search engines for popular queries. Victims believe that the files they download when using such resources are archives containing information they need, while, in fact, the files are executables that look like self-extracting archives. As the user tries to decompress the archive contents, they are informed at a certain point in the data extracting process that a payment must be made to complete the process. Ultimately users are deceived twice — they send money to criminals and never obtain any useful information. The archives contain nothing but the graphic shell and junk data, while their large size (apparently aiming to put users off guard) may exceed 70 MB.
8. Boot blockers. Trojan.MBRlock
In November 2010 virus analysts registered a blocker in the wild that rewrote the MBR code to prevent the installed operating system from loading. When victims turned on their computers, ransom demands appeared on their screens.
7. IM-client blockers. Trojan.IMLock
Over the course of several months in 2010, criminals spread a malicious program that blocked the launch of popular instant-messaging clients. The malware targeted users of ICQ and Skype. Instead of the messenger window, the Trojan displayed a window that mimicked the design of the blocked software. The user was offered the opportunity to regain access to the instant-messaging service by sending a paid short message.
6. Fake anti-viruses. Trojan.Fakealert
Fake anti-viruses have a look and feel similar to those of popular anti-virus software, and their design often combines the UI features of several anti-virus programs. However, such malicious programs and anti-viruses have nothing in common. Once installed, the fakes immediately notify users that the system is infected (and to some extent, this is true) and prompt users to purchase a commercial version of the product to cure the infection.
5. Redirection to malicious websites. Trojan.Hosts
Such malicious programs modify the host file, thus a user attempting to go to a popular website (e.g. a popular social networking site) gets redirected to a fake site that copies the design of the legitimate web resource. A user may be ordered to pay the criminals to re-gain full access to the original site.
4. Redirection to a local web server. Trojan.HttpBlock
Unlike Trojan.Hosts, these programs redirect a user to web pages generated by the web server installed on the compromised machine. With this approach, criminals save themselves the trouble of finding a hoster that wouldn’t take down their bogus site as soon as its malicious nature is exposed.
3. Data encryption. Trojan.Encoder
Last year saw the appearance of a multitude of new modifications of encryption Trojans targeting user documents. Once files are encrypted, these Trojans notify users that they have to pay criminals to decrypt the documents. In most cases Doctor Web releases corresponding decryption utilities in a timely manner, but since sometimes no quick decryption is possible and the ransom can be rather large, Trojan.Encoder comes in at No. 3 in the chart.
2. Windows blockers. Trojan.Winlock
Most common Windows blockers have had users and virus analysts on guard since late 2009, and so they rightfully take the second position. Blockers are malicious programs that display a window containing the criminals’ demands on top of all other windows, making those windows inaccessible until the victim pays a ransom. In 2010, Doctor Web virus analysts registered several surges of Winlock, and yet many new modifications of such programs are found in the wild at present.
1. Banking Trojans. Trojan.PWS.Ibank, Trojan.PWS.Banker, Trojan.PWS.Multi
The top spot in Doctor Web’s 2010 Malware Hit Parade goes to banking Trojans. These are malicious programs that help criminals gain unauthorized access to bank accounts over online banking systems. In 2011, we are likely to witness a shift in the criminals’ attention away from home users and towards companies which keep far greater sums of money in their accounts.
Statistics on user requests
Below you can see several graphs showing the history of user requests related to cyber fraud in 2010.
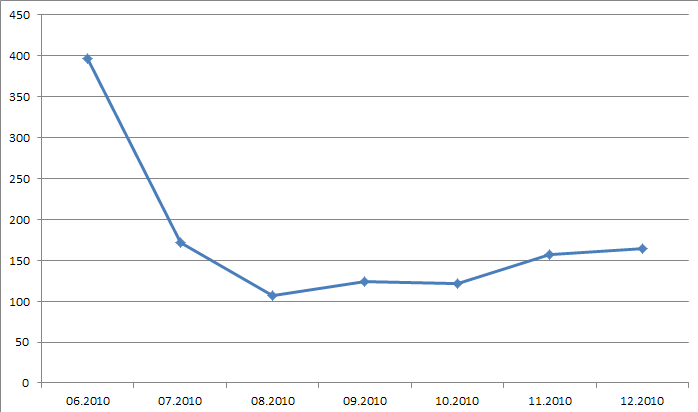
The first graph shows how the number of requests made to Doctor Web technical support, which is free for victims of cyber-fraud, varied throughout 2010. You can see that in June, when free support became available to users, the number of requests reached 400. By August when fewer variations of fraud malware were found in the wild, the number went down too. However, by the end of the year it increased again as criminals adopted more reliable methods to convert their virtual income into actual money.
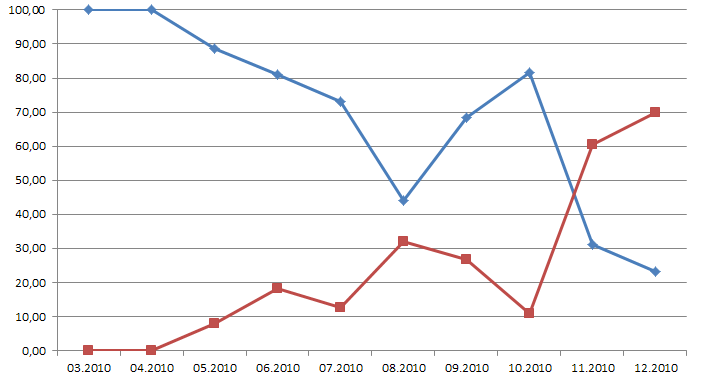
The second graph shows the percentage ratio between the numbers of requests related to fraud schemes incorporating different methods for converting criminal income into money. The blue line represents requests related to malware that demanded paid short messages from users, while the red line represents fraudware that demanded a balance refill. You can see that after a breaking point in November 2010, criminals shifted their preferences towards the second scheme.
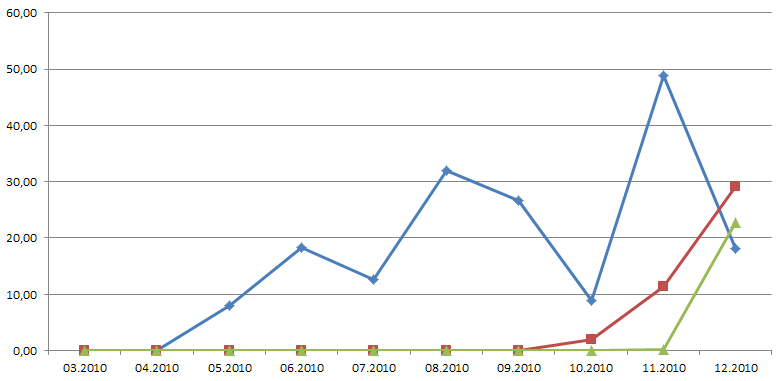
The third graph shows the percentage ratio between the total number of requests and the number of incidents when criminals demanded a balance refill over a payment terminal. The red and blue lines stand for different mobile operators. By December, fraudsters had adopted a new variant of the balance refill scheme which is represented on the graph by the green line. In the latter case, users refill balances for criminals by sending paid short messages. This scheme is as convenient as the standard short message scheme, but here criminals don’t need to deal with short code aggregators.
Other notable events in 2010
Other significant events of the last year include the emergence of the first 64-bit BackDoor.Tdss rootkit for Windows featuring bootkit technologies used to infect systems. The number of multi-component malicious programs incorporating bootkit technologies is growing.
It is also worth mentioning that the number of viruses for Android and other mobile platforms has increased as well. Doctor Web responds to emerging threats with prompt releases of new anti-viruses for most popular mobile OSs.
A standing recommendation for users is to follow the basic rules of information security: Ensure that your operating system and frequently used applications are updated regularly, install an anti-virus that is updated automatically, use alternative web-browsers, and do not use a system, especially one connected to the Internet, with administrator rights.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments