Dr.Web was the first to detect Trojan loader for smart Linux devices with MIPS/MIPSEL architectures
Real-time threat news | Hot news | All the news | Virus alerts
August 24, 2017
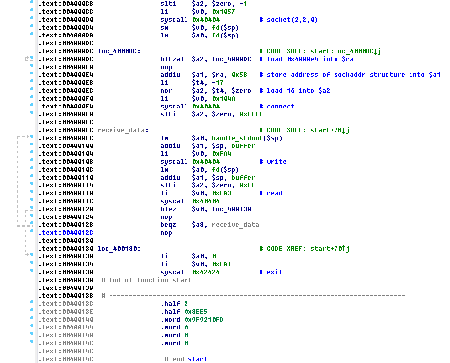
Virus analysts have been familiar with Trojans of the Linux.Hajime family since 2016. These are network worms for Linux distributed over the Telnet protocol. After obtaining a password via a brute-force attack and logging on to a device successfully, a malicious module saves a loader written in the Assembler language. Then, the malicious program connects the infected device to a decentralized P2P botnet. Linux.Hajime can infect devices with the ARM, MIPS, and MIPSEL architectures. The Trojan loaders, written in the Assembler language, are not detected by modern anti-viruses, except for the loader for ARM devices, which was described in detail by one anti-virus company in a research report.
In addition to the loader for ARM devices, similar modules for devices with the MIPS and MIPSEL architectures have been distributed “in the wild” for over six months already. The first of them is Linux.DownLoader.506 and the second is Linux.DownLoader.356. At the moment this article was being written, only Dr.Web products were able to detect both these worms. Moreover, Doctor Web virus analysts have found that, in addition to using Trojan loaders, cybercriminals are infecting devices using standard utilities—for example, they are downloading Linux.Hajime via wget. And starting on July 11, 2017, they began downloading the Trojan to the attacked devices with the help of tftp utility.
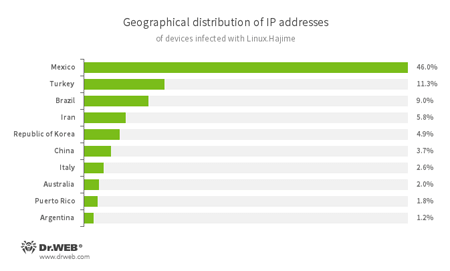
Statistics collected by Doctor Web specialists show that Mexico ranks first among the countries to which the IP addresses of the devices infected by Linux.Hajime belong. Turkey and Brazil are also in the top three. The geographical distribution of the infected devices’ IP addresses is shown in the diagram below:
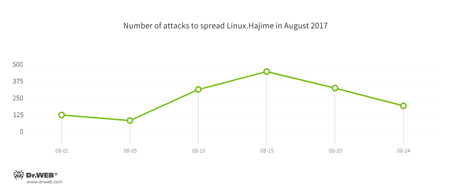
The following diagram shows the number of attacks carried out for the purpose of distributing Linux.Hajime in August 2017, as detected by Doctor Web.
Doctor Web reminds users that one of the most reliable ways to prevent attacks on Linux devices is to promptly change the default login and password. It is also recommended that users place restrictions on external connections being made to their devices via the Telnet and SSH protocols and to timely update their firmware. Dr.Web for Linux detects and deletes all the aforementioned versions of Linux.Hajime loaders and allows devices to be scanned remotely.