December 30, 2016
In 2016, Android users again faced a large number of threats posed by malware. Throughout the previous twelve months, cybercriminals have been spreading banking Trojans, one of which has managed to infect almost 40,000 smartphones and tablets worldwide. New malicious programs were discovered—they were preinstalled by cybercriminals into the original factory firmware in dozens of models of Android devices. Android Trojans that can inject their code into other running processes or can infect system libraries have emerged. In addition, many new malicious applications made their way into the official Google Play store. Besides, cybercriminals have been distributing Trojans that were aggressively displaying ads, attempted to obtain root privileges on a device, and covertly installed software.
PRINCIPAL TRENDS OF THE YEAR
- The number of malicious and unwanted adware programs which covertly downloaded and installed other software had grown.
- New Android Trojans infecting processes and system libraries appeared.
- New preinstalled Trojans were detected.
- The number of Android bankers increased together with the number of attacks on bank customers of different countries.
- New Trojans were detected on the Google Play store.
- New malicious and unwanted applications for iOS were found.
Mobile malware landscape
Android continues being the world’s most popular mobile operating system used in a large number of modern mobile devices. In 2016, cybercriminals once again directed their attacks primarily at the users of Android-based smartphones and tablets. Most of the malicious and unwanted programs, with which cybercriminals infected Android devices, were used as a way to generate illegal income for those criminals. The interest of cybercriminals to SMS-sending Trojans, which had been once favored by the malefactors, has continued to decrease, while malware that uses other means of monetization is being used more often as a primary source of income for cybercriminals. This trend was already noticed in 2015.
Trojans that aggressively display advertisements have become widely spread. They display banners on top of running apps, put messages into the notification panel, create shortcuts on the home screen of the operating system, open web pages or Google Play store pages predefined by the Trojan.
Another popular way among cybercriminals to generate profit is using Trojans to download and install software to users’ devices without the user permission, when the criminals get paid for every successful installation. In order to work without being noticed, many of such malicious programs try to get root privileges on the device and copy themselves into the system directory. Some of such Trojans capable of stealthily installing other software are even preinstalled by cybercriminals into the manufacturer’s firmware of various mobile devices. In addition, Trojans infecting processes of system applications have appeared, after which they obtain elevated privileges and can stealthily install software on the device. Such malicious programs were discovered in February, 2016. Later in December, Doctor Web’s virus analysts examined new versions of those Trojans that were now able to infect not only system processes but also system libraries.
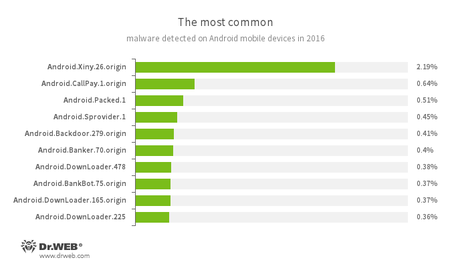
According to the statistics of threat detection by Dr.Web products for Android, in 2016, the most frequently detected Trojan on Android-based smartphones and tablets was Android.Xiny.26.origin that tried to get root privileges on the infected device by using exploits and downloaded and installed software without the user consent. Besides, it also displayed ads. Second comes the Android.Callpay.1.origin Trojan. It gave the owners of Android devices access to erotic materials, but, in return, it secretly made calls to premium-rate telephone numbers. In third place by the number of detections are the Trojans which Dr.Web anti-virus products for Android dubbed as Android.Packed.1. Such malicious apps are protected with the help of software packers and can perform a wide range of malicious actions.
- Android.Sprovider.1
A Trojan that downloads and installs various applications. In addition, it can show advertisements. - Android.Backdoor.279.origin
A multi-purpose backdoor for Android that receives instructions from the server and can perform a wide range of tasks. - Android.Banker.70.origin
A representative of banking Trojans which steal private information and money from user bank accounts. - Android.DownLoader
A family of Trojans which download and install other malware applications on mobile devices. - Android.BankBot.75.origin
A representative of banking Trojan family designed to steal provate information and money from user bank accounts.
This statistics shows that adware and downloader Trojans were more wide spread among malicious programs detected in 2016.
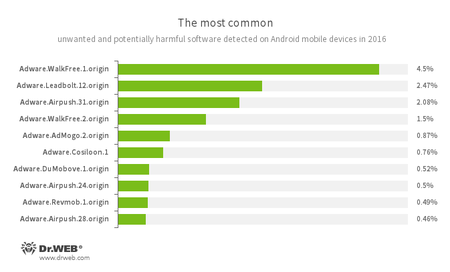
The same situation is displayed by the statistics of unwanted and potentially dangerous programs. In 2016, Android devices were attacked by unwanted applications and adware plug-ins. The first place went to the adware program Adware.WalkFree.1.origin, then goes Adware.Leadbolt.12.origin, and the last is Adware.Airpush.31.origin. The following diagram shows top 10 frequently detected unwanted applications found on mobile devices in 2016:
- Adware.AdMogo.2.origin
- Adware.Cosiloon.1
- Adware.DuMobove.1
- Adware.Revmob.1.origin
An unwanted program module that is incorporated into Android applications and is responsible for displaying annoying ads on mobile devices.
The most of adware plug-ins for Android shows banners, pop-ups, and messages on the status bar. However, many of them can also download application and prompt a user to install them.
Judging by that, the next year, adware Trojans and unwanted applications that show advertisements and covertly install other programs will be much more popular among cybercriminals.
Preinstalled Trojans
Malware programs incorporated into the firmware of Android mobile devices usually have system privileges and can perform a wide range of functions without user knowledge—for example, they can covertly download, install, and remove applications. In 2016, Doctor Web specialists registered several cases involving such Trojans. In mid-January, the firmware one of popular Android devices was found to contain Android.Cooee.1. Android.Cooee.1 was incorporated in a graphical shell and was designed for showing advertisements. Moreover, it was able to download and run other applications, including malicious ones.
In March, Doctor Web specialists examined Android.Gmobi.1, a malicious program for Android that was detected in such Google Play apps as TrendMicro Dr.Safety, TrendMicro Dr.Booster and Asus WebStorage, and was also preinstalled on several dozens of mobile devices. This Trojan is a specialized program SDK (Software Development Kit) platform usually used by either mobile device manufacturers or by software developers.
That platform allowed to remotely update the operating system and collect analytical data. It also showed various notifications and was used as a mobile payment system. However, it also performed malicious actions. For example, Android.Gmobi.1 showed advertisements, created shortcuts on the home screen, opened various web pages in a browser and on Google Play, downloaded, installed, and run other software. In addition, it sent private information to the command and control server.
In November, Doctor Web’s security researchers detected the Trojan Android.Spy.332.origin which was initially a benign system program for firmware updating. However, a new version of that program became performing some malicious functions. Android.Spy.332.origin covertly downloaded, installed, and removed applications, executed shell commands, and sent user personal information, including data on SMS messages, phone calls, and mobile device information, to the command and control server. After mass media informed users about that Trojan, the operating system was soon updated.
Due to incorporation of Trojans and other unwanted applications into the Android system catalog allows virus makers to perform any malicious actions, it is likely that the firmware of some models of mobile devices will be again infected with malicious programs.
Trojans on Google Play
Despite the fact that Google Play is an official and reliable source of software for Android, various Trojans can still periodically be found in Google Play applications. The past year was marked by the emergence of numerous such cases—for example, Android.Click.47.origin was found incorporated into allegedly benign applications. Once launched Android.Click.47.origin downloaded a list of webpages from the command and control server and concealed the list. The Trojan then automatically opened all the advertising links located on those webpages, tapped on banners and other interactive elements, generating income for cybercriminals.
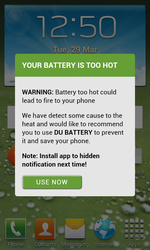
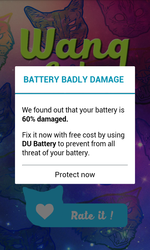
In March, Doctor Web’s specialists discovered Android.Spy.277.origin on Google Play. That Trojan was embedded into over 100 applications. The Trojan sent detailed information on user mobile device and displayed advertisements. It also scared users that the device’s battery is damaged. To repair the battery, the user was prompted to install some applications. In addition, Android.Spy.277.origin showed advertisements on the status bar and created shortcuts, which lead to some Google Play applications, on the home screen.
Later in April, Doctor Web’s security researchers found the similar Trojan—Android.Click.95—that was preinstalled in more than 190 applications. The Trojan checked whether an application specified by the Trojan was on the device. If the application was missing, Android.Click.95 opened a fraudulent website which prompted the user to choose another browser because the current one was allegedly not safe to use, or the Trojan showed another fake warning, for example, about battery malfunction. To solve those problems, the user was then prompted to install some application.
In June, the Trojan Android.PWS.Vk.3 was also discovered in Google Play. It allowed to listen to VK music by stealing user login credentials for their VK user profiles and sent them to cybercriminals.
Later that month, news about Android.Valeriy.1.origin were published by Doctor Web. This Trojan was able to load dubious websites and display them as advertisements in order to get users’ mobile phone number and subscribe them to chargeable services. Then a certain subscription fee was written off from the user’s mobile account every day. Android.Valeriy.1.origin intercepted and blocked all incoming confirmation messages. As a result, the victim did not have any idea that they were subscribed to some services. In addition, the Trojan could tap on advertisements, open links, and download unwanted applications including malicious ones.
In July, one more Trojan was found in Google Play—Android.Spy.305.origin. The Trojan was incorporated into more than 150 applications. Its main goal was to show annoying advertisements. However, it could also send user private information to virus makers.
Another Trojan, discovered in September, was Android.SockBot.1. Once installed, Android.SockBot.1 covertly connected to the Internet and transformed a mobile device into a proxy server. This technique helped cybercriminals anonymously connect to remote computers and other machines that had an Internet connection. In addition, they could intercept and redirect network traffic, steal private information, and perform DDoS attacks on web servers.
This year was also marked by the discovery of Android.MulDrop.924, about which Doctor Web published the news article in November. It allowed mobile device users to use multiple accounts simultaneously.
Part of its functionality was located in two auxiliary modules, which were encrypted and hidden inside a PNG image in the resource catalog of Android.MulDrop.924. One of those components not only performed benign functions but also contained several advertising plug-ins used by the Trojan’s authors to generate income. The malicious module Android.DownLoader.451.origin was one of them—it covertly downloaded applications and invited users to install them. In addition, it could display advertisements on the status bar of a device.
Despite the fact that Google tries to prevent the spread of Trojans on Google Play, this app store can still contain malicious applications. Virus makers continuously find different ways to bypass all protection mechanisms so new infected applications may be found on Google Play the next year.
Banking Trojans
More and more owners of Android devices use their smartphones and tablets to access online banking services. For this reason, cybercriminals continue improving banking Trojans and are increasing the number of attacks on bank customers, trying to steal money from users in dozens of countries. In 2016, Dr.Web anti-virus products for Android detected over 2,100,000 cases when such malware infiltrated Android-based devices, which is a 138% increase over the previous year.
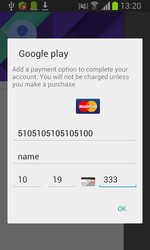
An important circumstance that occurred this year is the distribution of Android banking Trojans via the Google AdSense advertising platform. When smartphone or tablet users used the Chrome web browser to visit a web site that contained an advertisement created by the cybercriminals, APK files of Trojans were automatically downloaded to the device. By exploiting this vulnerability, cybercriminals have been for several months actively distributing such banking Trojans as Android.Banker.70.origin and Android.BankBot.75.origin. Later, Google released an update for Chrome that fixed this problem.
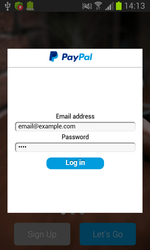
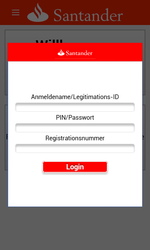
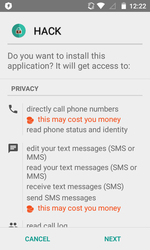
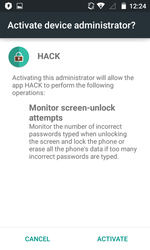
Among the banking Trojans distributed in 2016 was Android.SmsSpy.88.origin—Doctor Web reported about this malware in May. This malware is known since 2014, but cybercriminals are still actively advancing it. Android.SmsSpy.88.origin steals logins and passwords from user accounts used for mobile banking by displaying a fake authentication window on top of the original mobile banking app launched by the user. Cybercriminals can create such dialog for any app, so the Trojan can attack bank customers all over the world. Android.SmsSpy.88.origin also steals information about credit and debit cards, intercepts incoming SMS messages, secretly sends SMS messages, and can even act as a ransomware Trojan by blocking the screen of the mobile device and then demanding a ransom for unblocking it.
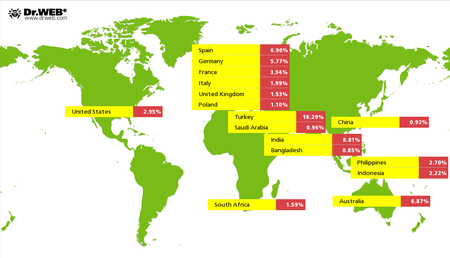
As a result of the examination, Doctor Web’s specialists determined that since the start of 2016, cybercriminals have attacked users from over 200 countries by means of Android.SmsSpy.88.origin, while the overall number of infected devices has reached almost 40,000.
In October, a new strain of Android.SmsSpy.88.origin emerged that was named Android.BankBot.136.origin. To this malware, the cybercriminals have added the capabilities that allowed it to work even on the newer Android versions, which had improved mechanisms of protection against malware. As a result, the Trojan became able to display phishing windows and intercept text messages on an even larger number of mobile device models.
In 2016, virus analysts at Doctor Web have also discovered another banking Trojan—Android.BankBot.104.origin. It was distributed by posing as a hack tool for mobile games and a game cheating program. Upon making its way onto a mobile device, Android.BankBot.104.origin detected whether a mobile banking service is used on the device, and then checked the balance on all the available bank accounts. If it found that money was available on any account, it tried to stealthily transfer it to cybercriminals.
Stealing money from bank accounts as well as obtaining financial or other confidential data belonging to the users of Android devices yields high profits for cybercriminals. It can be said with confidence that next year cybercriminals will continue attacking the bank customers.
Ransomware Trojans
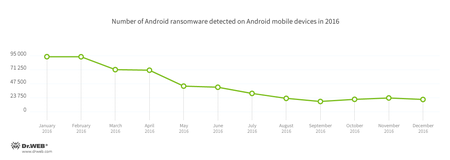
Android Trojans that block mobile devices and extort a ransom for unlocking them pose a serious threat. In 2016, cybercriminals were again distributing such malware among the owners of Android smartphones and tablets. During the last twelve months, Dr.Web antivirus products have detected over 540,000 cases of ransomware Trojans getting into Android devices. This is 58% fewer cases than in 2015. The most intense attacks using such Trojans happened during the first months of this year; and then the rate at which this malware was spreading has decreased. The history of Android ransomware detections on mobile devices can be seen in the following diagram:
Examples of the messages that are displayed by such malware are shown in the pictures below:
Despite a decrease in the number of infections involving Android ransomware in 2016, this malware is still a serious threat to smartphone and tablet owners. It can be said without doubt that next year cybercriminals will keep Android ransomware in the array of their weapons and will continue to attack users with this malware.
Trojans for iOS
Cybercriminals that attack users of mobile devices focus their attention mainly on smartphones and tablets running Android. However, this does not mean that cybercriminals have no interest in other platforms—for example, in iOS, developed by Apple. Malware and unwanted apps for this mobile OS are currently not widely spread, but the number of such malicious programs is gradually increasing year by year. In 2016, several new threats for iOS have also appeared.
In February, in the official App Store a potentially harmful app— Program.IPhoneOS.Unwanted.ZergHelper.1—was discovered, which functioned as an app catalog for users in China. The danger of this app was that any sorts of third-party apps were distributed through it, including hacked apps and apps that had not been reviewed and approved by Apple. As a result users were at risk of downloading Trojans or other malware with the help of Program.IPhoneOS.Unwanted.ZergHelper.1. Furthermore, this catalog could install its own updates onto the devices, bypassing the App Store, and also requested the users to enter their Apple ID and password, which were then sent to a remote server.
As early as in March an IPhoneOS.AceDeciever.6 Trojan was added to the Dr.Web virus database. It was part of an app named 爱思助手that had been created by cybercriminals and was intended for PCs running Windows. The authors of this program advertised it as an alternative to the iTunes utility that could be used to manage mobile devices. This app was added to the Dr.Web virus database under the name Trojan.AceDeciever.2.
Once a smartphone or tablet running iOS was connected with a USB-cable to a PC on which the Trojan.AceDeciever.2 had been installed, the IPhoneOS.AceDeciever.6 Trojan was automatically uploaded and installed to the mobile device using a vulnerability in FairPlay—Apple’s DRM mechanism for digital media content. Once IPhoneOS.AceDeciever.6 got to the mobile device it requested the user to enter the user’s Apple ID and a password, after which the Trojan sent this information to the cybercriminals server.
Smartphones and tablets running iOS are considered to be more protected as compared to Android devices. However, with an increasing frequency cybercriminals show their interest towards iOS devices as well. It may be expected that next year new malware may appear that will be employed to attack the users of the mobile OS developed by Apple.
Prospects and trends
The majority of modern mobile devices run the Android operating system, partly for this reason the largest share of attacks targets the owners of such devices. One of the main threats for users of Android smartphones and tablets comes from banking Trojans. There is a growing number of malicious apps of this kind that detect when a legitimate banking app is launched and then overlay the original banking app with a similarly-looking fake input form to harvest the user’s banking login credentials. Undoubtedly, cybercriminals will keep using this social engineering mechanism. Moreover, there is little doubt that cybercriminals will also continue improving the functionality of banking Trojans.
Another current threat for owners of Android-based smartphones is posed by the Trojans that attempt to get root privileges and stealthily download and install programs to the device. Most probably, in 2017, the number of such malicious apps will increase. Furthermore, Trojans that will use new ways to infect mobile devices may appear.
During the several past years, there were a number of cases when new phones came with various Trojans and unwanted programs pre-installed on them by cybercriminals. There is a high probability that this will continue to happen; that is why, next year, it is reasonable to expect new instances of infected firmware in mobile devices.
Despite the efforts that Google makes to ensure the safety of its official app store, cybercriminals still manage to publish various Trojans in it, which is demonstrated by the numerous cases in 2016 of finding malware in the Google Play store. Most probably, in 2017, owners of Android users will again encounter cases when Trojans appear in the official app store of the Android OS.
Ransomware targeting Android devices still poses a serious threat to the users. It is reasonable to expect that next year new attacks involving this kind of malware may happen again. Besides, one cannot exclude the possibility that new threats that are designed to operate on iOS devices may emerge. Smartphones and tablets running this operating system are still sufficiently protected. However, the year 2016 has shown that the interest of virus makers towards this platform remains. Cybercriminals are always trying to make profits wherever it is possible—for this reason, in 2017, iOS devices will remain a potential target for attacks by cybercriminals.