May 15, 2012
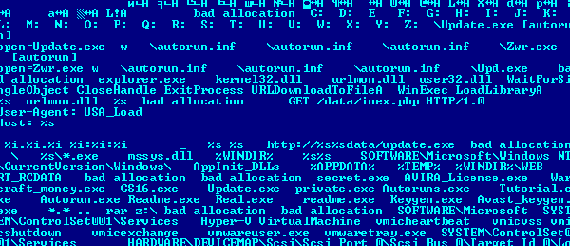
Win32.HLLW.Autoruner.64548 spreads as many other worms do: it creates its copy on a disk and places the file autorun.inf into the root directory to launch the worm as soon as the device is connected to the computer. When launched on the infected computer, Win32.HLLW.Autoruner.64548 searches disks for RAR archives and places itself into them under one of the following names: secret.exe, AVIRA_License.exe, Warcraft_money.exe, CS16.exe, Update.exe, private.exe, Autoruns.exe, Tutorial.exe, Autorun.exe, Readme.exe, Real.exe, readme.exe, Keygen.exe, or Avast_keygen.exe. In some cases, such a modification damages archives.
In addition, the worm has a payload module. Its body also contains an executable file that Win32.HLLW.Autoruner.64548 saves into the Windows folder as mssys.dll. The malicious program registers the library file in the registry. The worm injects the payload code into a copy of its own process. Then the malware connects to a remote server and waits for malicious commands to download and run executable files.
Win32.HLLW.Autoruner.64548 represents a rare category of malicious programs that can infect RAR archives. When unpacking RAR archives, pay attention if suspicious executable files appear in the archive: their accidental launch may harm your computer. The worm's signature has been added to the Dr.Web virus databases.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments