April 2, 2012
According to statistics collected by Dr.Web CureIt!, in March the absolute leader in terms of the most-detected virus was Trojan.Mayachok.1, which blocks access to the Internet from an infected computer. Banking Trojan horses such as Trojan.Carberp, which steals passwords stored by online banking clients and trading platforms, were also found in large numbers.
Viruses and Trojan downloaders were frequently detected in mail traffic. In this regard, we must note an incident that took place in early March when a bulk spam mailing containing a malicious attachment went out.
Political spam containing a hoax. A special post-election gift for Russians
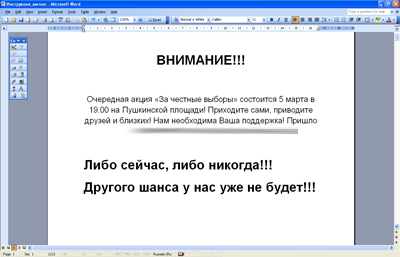
On March 5, Doctor Web analysts registered a mass mailing where messages called on users to attend an opposition-organized rally. These e-mails contained a short text prompting recipients to read the attached instructions.
The attached document contained several macros, and once opened with a word processor, those macros would save and launch the Windows-destroying program, Trojan.KillFiles.9055.
Trojan.KillFiles.9055 copies itself into a temporary folder and adds its entry into the registry so it can launch automatically. Simultaneously, the Trojan replaces the contents of all of the files found on the C drive (.msc, .exe, .doc, .xls, .rar, .zip, and .7z) with meaningless data and marks them for deletion upon reboot, which renders Windows non-operational (a system reboot will not help). Trojan.KillFiles.9055 alters the properties of its process so that it becomes critical to the system, and its termination brings up the BSOD or restarts the system.
Then the Trojan horse notifies a remote server that the system has been broken down successfully. Fortunately, a timely warning and the fact that macro processing in Microsoft Word is often disabled by default made it possible to avoid mass infection.
New threats to Android
On March 6, 2012, Google Inc. announced the rebranding of Android Market. The site was not only renamed Google Play and given a new address, play.google.com, but also was expected to unite projects such as video services, Android Market, Google Music, and Google eBookstore.
Criminals didn't hesitate to take advantage of this event, and numerous bogus sites copying Google.Play’s design emerged on the Internet. Some of them spread malicious software for Android. There are specially designed partnership programs that make it possible to create fake websites that distribute various malicious applications, including Android.SmsSend Trojan horses, to visitors.
For example, one such affiliate programs offers website owners the option to add a special script to their site code in order to redirect visitors using mobile devices to a "partner" resource. Usually this is accomplished by means of JavaScript or special .htaccess directives.
At the same time, many Android users are unaware of the fact that Android Market no longer exists. A huge number of reviews where various experts advise users to download software exclusively from Android Market are available on the Internet. People entering such queries in search engines are shown links to websites mimicking Android Market. Some sites offer harmless applications and games, however, others distribute malicious software.
The Android.Moghava. horse is one of the most remarkable pieces of malware added to the virus databases in March. Its malicious payload is contained in a module that is installed as a service named “stamper”. This service starts periodically and searches for JPEG images on a memory card connected to the device, particularly in the /DCIM/Camera/ folder, which by default stores photos made with a phone camera. If the Trojan horse finds image files in the folder, it adds an Ayatollah Khomeini portrait to all the images.
In addition, the I-Girl program—actively advertised on social networking websites, forums, and in many spam mailing lists—has been spreading very widely. The program is a chat bot represented on the device's screen as a pretty girl. A user can chat with this virtual interlocutor in real time and even make her remove her clothes. But after a while, the user will suddenly discover that their subscriber account has been depleted by an amount that depends on the duration of the "conversation". Furthermore, sometimes money is withdrawn from the account even when the girl doesn’t respond. It turns out that to communicate with the bot, one must pay for each message using a special virtual currency, and in order to refill the balance, the program covertly sends short messages to premium numbers. In addition, I-Girl sends the device ID to its developers' site.
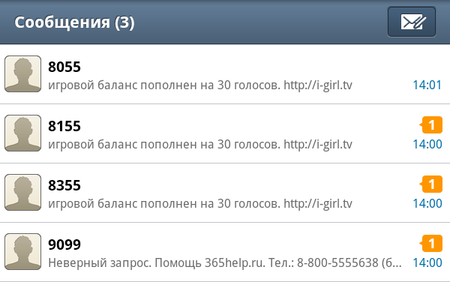

While not an immediate threat to Android, Doctor Web found it necessary to add I-Girl to the list of dangerous software, since this application threatens the welfare of users and is distributed using techniques employed to spread malware, e.g., forcibly redirecting users to the site that spreads the program and with annoying spam.
New Trojan for Mac OS X
In mid-March, intruders discovered a new way to spread malware for Mac OS X—an idea that first came to the authors of Trojan.Muxler (OSX/Revir).
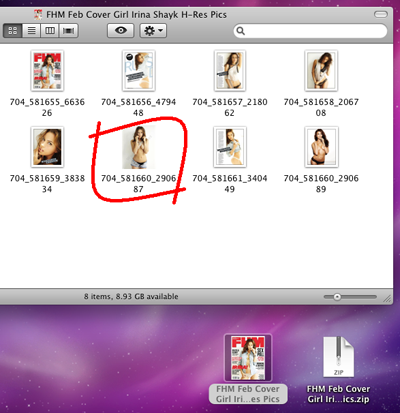
A threat is concealed in a ZIP archive containing various photographs. Archive samples were uploaded to virustotal.com as Pictures, and the Ariticle of Renzin Dorjee.zip, and FHM Feb Cover Girl Irina Shayk H-Res Pics.zip. There is speculation that the spread of these malicious programs is connected with increased Sino-Tibetan tension and is directed primarily against various organisations advocating Tibet's independence.
When the archive content is extracted, an application is saved on the disk alongside photos. Its icon, displayed in the Finder window, is virtually indistinguishable from the other images. Intruders count on careless users to launch the application mistakenly once they fail to distinguish the program icon from neighbouring thumbnail images.
Trojan.Muxler.3 is spread this way. This program allows intruders to perform various commands to download and run programs, and also to create Mac OS X desktop screenshots. In addition, Trojan.Muxler.3 downloads the CurlUpload file from the Internet and stores it in the /tmp folder. The file is detected by Dr.Web as Trojan.Muxler.2 and is used to upload various files from an infected machine to a remote server.
Also found in the wild recently were BackDoor.Lamadai.1, which exploits the vulnerability Exploit.CVE2011-3544, and BackDoor.Lamadai.2 and BackDoor.Macontrol.1, which take advantage of the vulnerability in Microsoft Office for Mac (Exploit.MS09-027.1).
Trojan.Winlock lives
Traditionally ransomware use a special application that replaces the Windows shell or userinit.exe to block access to the system and display ransom text. Simultaneously, the piece of malwar malware usually monitors and blocks the launch of various system utilities such as Task Manager, Command Prompt, Registry Editor, etc. The makers of Trojan.Winlock.5729 chose a completely different and simpler approach.
The Trojan horse code is spread with a modified distribution of the Artmoney program which is used to adjust various computer game parameters. In addition to Artmoney, the installer incorporates three files: the modified logonui.exe file named iogonui.exe (responsible for displaying the Windows XP logon screen) and two self-extracting archives containing bat-files. Starting an infected installer executes the password_on.bat file. This file contains a set of commands that searches the hard drive for the c:\users folder, typically found under Windows Vista and Windows 7. If discovered, the harmful components are removed. If the folder is not found, the Trojan horse believes that it is running under Windows XP. In this case, Trojan.Winlock.5729 modifies the system registry to replace the logonui.exe file with iogonui.exe, and changes the password for the Windows account of the current user and local users named admin, administrator, админ and администратор. If the current user account has restricted permissions, the Trojan horse process ends. Another bat-file, password_off.bat, is used to remove all passwords and set the original UIHost value in the registry.
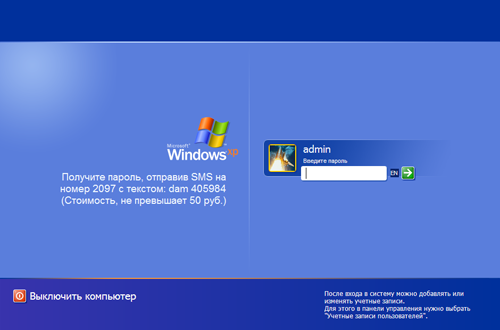
The iogonui.exe file is a genuine logonui.exe file that comes with the Windows XP distribution, but a resource editor was used to change the standard Windows welcome screen with a demand that the user send a paid SMS.
Thus, once the user logs off or reboots the system, they will not be able to log in, as the passwords for all user accounts will have been changed.
Other threats in March 2012
Doctor Web registered the spread of a new Trojan horse program that mines bitcoins, an electronic currency. When launched in the infected system, Trojan.IEMine.1 creates an Internet Explorer COM-object with an invisible window and commands the browser to open a web page created and owned by criminals. This page contains JavaScript code that mines Bitcoins. Calculations run on the target web page consume a lot of hardware resources which may result in a noticeable decrease in system performance on low-end machines.
In addition, tough competition between owners of GoldSource game servers drove them to employ flooder programs against their competitors. Meanwhile, such programs can be dangerous to the users themselves. Back in February, several applications rendering GoldSource servers non-operational appeared in the public domain. One of them, added to the Dr.Web virus database as Flooder.HLDS, is a program that has a graphical interface and emulates a large number of connections to a game server which can make the server freeze and cause errors.
Flooder.HLDS.2 is another malevolent program that sends a certain data packet to the server which causes the server to crash. The program offers several options to communicate with the server. Both applications have been spread widely via game-related forums, and the number of attacks on game servers orchestrated using these programs increased significantly during this month.
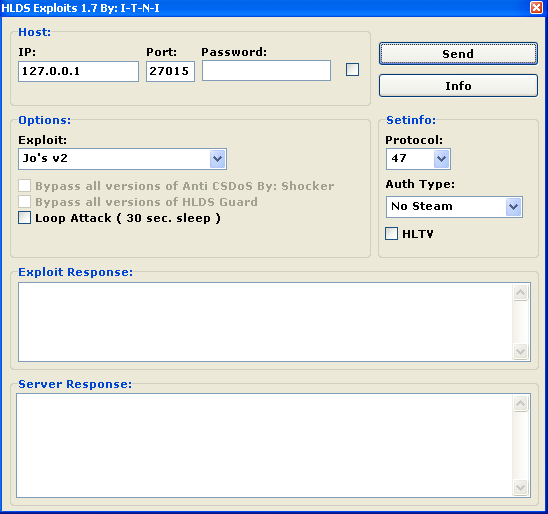
Doctor Web's virus analysts got hold of copies of Flooder.HLDS.2 from game forums. When run, this application infects the system with BackDoor.DarkNess.47 backdoor and Trojan.Wmchange.14. The former acts as a backdoor and DDoS bot, while the Trojan horse changes WebMoney wallet IDs in the memory of the compromised computer to steal money from the user’s account. Thus, would-be criminals themselves are becoming victims of virus attacks and subjecting their own computers to the risk of infection.
Top 20 malware detected in March in mail traffic
| 01.03.2012 00:00 - 31.03.2012 16:00 | ||
| 1 | JS.Siggen.192 | 16675353 (42.27%) |
| 2 | Win32.Rmnet.12 | 14293914 (36.24%) |
| 3 | Win32.HLLP.Whboy | 3336057 (8.46%) |
| 4 | Trojan.DownLoad2.24758 | 1260064 (3.19%) |
| 5 | Trojan.Oficla.zip | 775752 (1.97%) |
| 6 | Win32.HLLP.Neshta | 564643 (1.43%) |
| 7 | Trojan.Inject.57506 | 276708 (0.70%) |
| 8 | Trojan.DownLoad2.32643 | 194468 (0.49%) |
| 9 | Trojan.Tenagour.9 | 180616 (0.46%) |
| 10 | Trojan.Tenagour.3 | 152860 (0.39%) |
| 11 | Trojan.Carberp.208 | 130417 (0.33%) |
| 12 | Trojan.Siggen2.62026 | 116670 (0.30%) |
| 13 | Trojan.Siggen2.58686 | 101121 (0.26%) |
| 14 | Trojan.IFrameClick.3 | 99859 (0.25%) |
| 15 | Trojan.PWS.Panda.368 | 86438 (0.22%) |
| 16 | Trojan.WMALoader | 79203 (0.20%) |
| 17 | Trojan.Packed.19696 | 70133 (0.18%) |
| 18 | Trojan.NtRootKit.6725 | 46797 (0.12%) |
| 19 | Trojan.Fraudster.261 | 42210 (0.11%) |
| 20 | Trojan.DownLoad2.34604 | 41211 (0.10%) |
| Total scanned: | 38,656,062,243 |
| Infected: | 39,445,438 (0.10%) |
Top 20 malware detected in March on user PCs
| 01.03.2012 00:00 - 31.03.2012 16:00 | ||
| 1 | JS.Siggen.192 | 198194452 (76.33%) |
| 2 | Win32.Rmnet.12 | 38403209 (14.79%) |
| 3 | Win32.HLLP.Neshta | 8647504 (3.33%) |
| 4 | JS.IFrame.112 | 3918622 (1.51%) |
| 5 | JS.DownLoader.216 | 1382451 (0.53%) |
| 6 | JS.IFrame.167 | 705427 (0.27%) |
| 7 | JS.IFrame.95 | 642246 (0.25%) |
| 8 | BAT.Batalia.491 | 475531 (0.18%) |
| 9 | Trojan.IFrameClick.3 | 424833 (0.16%) |
| 10 | Trojan.PWS.Ibank.456 | 403856 (0.16%) |
| 11 | JS.IFrame.236 | 378860 (0.15%) |
| 12 | Trojan.MulDrop1.48542 | 368040 (0.14%) |
| 13 | JS.Autoruner | 336441 (0.13%) |
| 14 | Win32.HLLP.Whboy | 279385 (0.11%) |
| 15 | Trojan.Packed.20771 | 201975 (0.08%) |
| 16 | Trojan.Fraudster.261 | 193834 (0.07%) |
| 17 | Trojan.Hosts.5571 | 182009 (0.07%) |
| 18 | Trojan.DownLoad.968 | 163980 (0.06%) |
| 19 | Adware.Predictad.1 | 147480 (0.06%) |
| 20 | Win32.Siggen.8 | 142900 (0.06%) |
| Total scanned: | 357,755,042,533,173,265 |
| Infected: | 259,668,933 (0.00%) |


![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments