Harmless virus and other malicious trends of august 2009
Virus reviews | All the news
Delphi and other development environments under attack
Win32.Induc — the virus infecting installed Delphi IDE versions 4 up to 7 — has been discovered in the wild several months ago. This malicious program infects a library file used during project compiling. Any program compiled with the infected IDE is infected before one performs any actions with it.
Though Win32.Induc doesn’t take any other actions, its spreading technique can be adopted by other virus makers in the future. Dr.Web anti-virus solutions still detect the virus and offer users to cure it. Even though it seems harmless it is still dangerous.
Absence of any destructive features contributed to a wide-scale spreading of the virus whose code became a part of many popular harmless applications developed using infected Delphi IDE. Consequently as its signature was added to virus databases by anti-virus vendors, their anti-virus solutions started blocking operation of such programs causing troubles to their developers as well as to users. However, with adding entries for curing Win32.Induc to databases the number of infections by the virus decreased significantly.
Unlike Win32.Induc, ACAD.Siggen discovered in August was spread as a module of the Visual Lisp IDE used by Autodesk AutoCAD. ACAD.Siggen infected AutoCAD-files opened in an infected system because it was launched simultaneously with AutoCAD.
Social networking web-sites – virus maker paradise
The steadily growing popularity of Twitter and Facebook drives malefactors to make them a part of their schemes for spreading malware. Unfortunately people are still gullible enough to respond to tempting offers that lure them into visiting bogus web-sites.
In August the long known family of Win32.HLLW.Facebook viruses offered users to work on virus-makers in the most peculiar way. As before a virus used messages posted on social networking web-sites to draw users to bogus web-resources faking legitimate web-sites and prompt the victim to download a supposed video codec from the malicious web-site. If the user launched an infected executable file, his system got infected. Here the most interesting part was the new deception tendency. Many web-services protect their resources from automatic registration that can be used by spammers. They resort to different challenge-response tests to ensure that a message is not generated by a robot. The most common test is CAPTCHA – a user is asked to enter a randomly generated text displayed as an image.

Img. 2. A message prompting a user to pass a CAPTCHA test.
Win32.HLLW.Facebook.194 included in latest versions of Win32.HLLW.Facebook enabled virus makers to force users to pass such tests. The module forced a user to enter a correct text and send it to cyber criminals' server. Once a CAPTCHA test task was received from a remote server, a dialogue providing a user with an input field poped up on the screen blocking access to any other components of the system. Users tricked in such a way help cyber criminals to create accounts on various web-sites that were later used to send out spam messages.
Bot-net commands in posts from one of the Twitter accounts became another way to exploit social networking web-sites. Encoded information posted under one of the microblog’s accounts was retrieved over RSS by bots installed and running in compromised systems. Trojan.PWS.Finanz.410 was among malicious programs that received commands via Twitter.
Google-owned Jaiku social networking and microblogging service was also used as a bot command and control centre with bots retrieving information through RSS.
Such approach to botnet management has certain benefits such as disguised traffic and low detection probability. Since Twitter allows creating private accounts with tweets accessible only to a limited number of users, inappropriate usage of such accounts can be hard to discover.
Fake Mozilla Firefox updates
Adware.FF.1 is another malicious program spread from bogus web-sites. This one brought troubles to users of FireFox.
In the modern world where intruders root out vulnerabilities in popular software, developers have to release security patches on regular basis and prompt users to download and install them. People get used to almost daily updates of operating systems, anti-viruses, browsers and even text editors. In August cyber-criminals decided to take advantage of frequent update releases from Adobe and offered Adware.FF.1 as an update for Adobe Flash Player. The design of a bogus web-site used to spread the malicious “update” was very similar to that of the legitimate site of Adobe Systems. The malicious web-site domain name also made its address look similar to the URL of the official Adobe web-site. Some links placed on the fake web-resource directed a user to the legitimate site. Launching a downloaded fake updating file installed a Mozilla FireFox plugin that altered Google context ads.
Adware.FF.3 — a modification of Adware.FF.1 — featured a genuine Adobe Flash Player installer to avoid suspicions.
Virus included
Virus makers are known to exploit releases of popular software products to spread malware. When iWorks'09 was released by Apple, cyber-criminals "offered" a distribution package infected with a Mac.Iservice Trojan to users willing to obtain the new product. Surely an upcoming release of Mac OS X Snow Leopard was no event for malefactors to pass by. Distribution of the OS infected with a Mac.DnsChange virus was available for downloading via torrent. The virus faked DNS requests sent by a browser.
Trojan for Skype
Another significant event that occurred at the end of August 2009 was discovery of a proof-of-concept Trojan.SkypeSpy capable of intercepting Skype’s audio stream and writing the data into an MP3 file. The source code of Trojan.SkypeSpy was made available to the public which may result in appearance of numerous modifications of the program However, such viruses are not likely to be found in big numbers since the most obvious application for such programs is industrial espionage rather than establishing a total control over communications of all users on the Internet.
It once again shows that any popular technology will attract attention of cyber-criminals sooner or later.
Botnet invoice
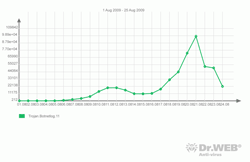
Nefarious activities of Trojan.Botnetlog.11 that spread as an attached invoice were first discovered in August 2009.
To push a user towards opening the “invoice” file the would-be-victim was provided with a delivery failure notification stating that a package couldn’t be delivered because the destination address was incorrect. An attached zip archive was detected by Dr.Web software as Trojan.Botnetlog.11. See more details about Trojan.Botnetlog.11 in a news post dated of August 12, 2009.
It should be noted that virtually each new mailing of the Trojan delivers a new modification of this malicious program compressed with a different packer. However, Dr.Web technologies allow automatic adding of new samples of Trojan.Botnetlog.11 to the virus database for even more reliable detection of Trojans of this type..
Later modifications of this program are detected by Dr.Web as Trojan.DownLoad.45107. The graphs show how Trojan.Botnetlog.11 spread over the Internet in August.
Phishing web-site included
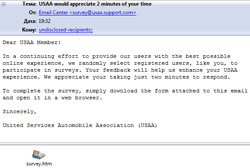
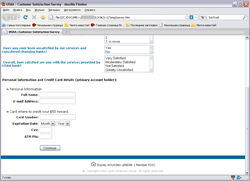
The new phishing technique adopted by cyber-criminals in August 2009 didn't aim to lure a user to enter his personal information at a fraudulent web-site but instead provided a necessary web-form attached to a message. A user was expected to open and fill out the form in a web-browser and press a confirmation button that would send the data to a server run by cyber-criminals.
This new technique makes work of cyber-fraudsters easier because it doesn’t require maintaining a web-site that can be closed down at any moment. At the same time a server that receives data from users can be difficult to shut down since it’s hard to prove that people owing and running the server have anything to do with phishing. This technique was applied to get personal information of PayPal and USAA customers.
Classical phishing attacks were directed at customers of Ally Bank, Bank of America, Chase Bank, Key Bank, SunTrust Bank, PayPal and eBay users.
Conclusions
Win32.Induc was the most notable event of the past month. It was widely discussed whether a harmless virus should be cured or not. The position of Doctor Web is quite clear. Win32.Induc must be cured since its spreading methods can be later be used by other virus makers.
Social networking web-sites are still widely used to spread malware. Virus-makers adopt more sophisticated techniques for distribution of viruses. Controlling bots over Twitter is a good example of such new techniques. Alas, a lack of judgment on the part of users of social networking services plays into hands of cyber-criminals.
An unusual technique was used by intruders to make users pass a CAPTCHA response test. This scheme is likely to be employed many times in the future since CAPTCHA response-challenge test is the most common method for detection spam bots and cyber-criminals do their best to bypass the test.
Availability of the Trojan.SkypeSpy source code to the public means that other malicious programs, capable of intercepting communication over Skype, may appear soon. However, ths threat mainly concerns those who use Skype to hold important negotiations.
Viruses detected in e-mail traffic in August
| 2009-08-01 00:00:00 - 2009-09-01 00:00:00 | ||
| 1 | Win32.HLLM.Beagle | 5,865,108 (21.93%) |
| 2 | Win32.HLLM.Netsky.35328 | 4,849,868 (18.14%) |
| 3 | Trojan.DownLoad.36339 | 4,134,857 (15.46%) |
| 4 | Trojan.PWS.Panda.122 | 1,961,029 (7.33%) |
| 5 | Win32.HLLM.MyDoom.based | 1,292,488 (4.83%) |
| 6 | Trojan.MulDrop.19648 | 1,157,909 (4.33%) |
| 7 | Trojan.Botnetlog.9 | 1,096,090 (4.10%) |
| 8 | Win32.HLLM.MyDoom.33808 | 855,011 (3.20%) |
| 9 | Win32.HLLM.MyDoom.44 | 792,728 (2.96%) |
| 10 | Win32.HLLM.Netsky.based | 436,017 (1.63%) |
| 11 | Win32.HLLM.Beagle.32768 | 428,610 (1.60%) |
| 12 | Win32.HLLM.Perf | 423,470 (1.58%) |
| 13 | Trojan.MulDrop.13408 | 400,116 (1.50%) |
| 14 | Win32.HLLM.MyDoom.49 | 357,537 (1.34%) |
| 15 | Exploit.IframeBO | 335,231 (1.25%) |
| 16 | Trojan.DownLoader.47449 | 330,465 (1.24%) |
| 17 | Win32.HLLM.Beagle.27136 | 282,600 (1.06%) |
| 18 | Exploit.IFrame.43 | 243,633 (0.91%) |
| 19 | Trojan.PWS.Panda.114 | 241,519 (0.90%) |
| 20 | W97M.Dig | 238,903 (0.89%) |
Total scanned: 97,916,911,140
Infected: 26,740,352(0.0273%)
Viruses detected on user machines in August
| 2009-08-01 00:00:00 - 2009-09-01 00:00:00 | ||
| 1 | Trojan.WinSpy.173 | 2,122,087 (12.83%) |
| 2 | Win32.HLLW.Gavir.ini | 945,441 (5.71%) |
| 3 | Trojan.PWS.Panda.122 | 934,309 (5.65%) |
| 4 | Win32.HLLW.Shadow.based | 692,403 (4.19%) |
| 5 | Win32.HLLM.Beagle | 685,142 (4.14%) |
| 6 | Win32.HLLM.Netsky.35328 | 553,701 (3.35%) |
| 7 | DDoS.Kardraw | 488,474 (2.95%) |
| 8 | Trojan.MulDrop.16727 | 459,047 (2.77%) |
| 9 | Win32.HLLM.MyDoom.49 | 384,980 (2.33%) |
| 10 | Win32.Alman | 374,155 (2.26%) |
| 11 | Win32.Sector.17 | 341,899 (2.07%) |
| 12 | Win32.Virut.14 | 334,440 (2.02%) |
| 13 | Trojan.WinSpy.180 | 319,031 (1.93%) |
| 14 | Win32.HLLW.Autoruner.5555 | 288,362 (1.74%) |
| 15 | Trojan.Botnetlog.11 | 254,197 (1.54%) |
| 16 | Win32.HLLP.Whboy | 243,831 (1.47%) |
| 17 | Win32.HLLW.Autoruner.2536 | 241,360 (1.46%) |
| 18 | Trojan.DownLoader.47449 | 240,895 (1.46%) |
| 19 | Trojan.Boroda | 187,808 (1.14%) |
| 20 | Win32.HLLM.Netsky.based | 187,327 (1.13%) |
Total scanned: 147,141,361,062
Infected: 16,543,297(0.0112%)
_i.gif)
_i.gif)