January 2013 virus activity review from Doctor Web
Virus reviews | All the news | Virus alerts
February 4, 2013
Viruses
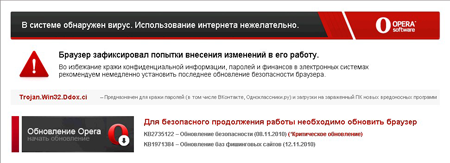
Trojan.Mayachok.2 became the undisputed leader among malware detected by Dr.Web CureIt!. Recall that Trojan.Mayachok.2, known to Dr.Web since spring 2011, stands apart from other versions of this rather common malware. It is a VBR bootkit, which means that the Trojan infects NTFS Volume Boot Records. Trojan.Mayachok.2 incorporates drivers for both 32-bit and 64-bit versions of Microsoft Windows. The program's main objective is to block Internet access and display a web page in the browser that prompts users to download a security update. To get the update, users must submit their phone number and enter a confirmation code delivered in a reply SMS. Thus, the victim becomes subscribed to a chargeable service, and a fee will be regularly debited from their mobile phone account.
Since the malicious object that replaces web pages loaded in the browser resides in the memory, reinstalling the browser, resorting to the system Restore feature and running Windows in safe mode won't rid the system of the Trojan. The infection is best treated by scanning the infected computer with Dr.Web CureIt! or Dr.Web LiveCD. A detailed technical analysis of the threat can be found in one of our previous reviews.
Conversely, the number of Trojan.Mayachok detections by Dr.Web CureIt! in RAM was rather high (over 40,000 instances). Also detected frequently in January was Trojan.Mayachok.18550. Fake installers, detected by Dr.Web as Trojan.SMSSend, are still frequently being found on machines as are BackDoor.IRC.NgrBot.42 programs. A list of the top 20 most common threats detected on desktops and laptops by Dr.Web CureIt! in January 2013 is presented in the table below:
| Name | % |
|---|---|
| Trojan.MayachokMEM.4 | 4.85 |
| Trojan.Mayachok.2 | 2.39 |
| Trojan.SMSSend.2363 | 2.26 |
| Trojan.Mayachok.18550 | 1.50 |
| BackDoor.IRC.NgrBot.42 | 0.94 |
| Trojan.BhoSiggen.6713 | 0.87 |
| Trojan.StartPage.48148 | 0.85 |
| Trojan.DownLoader7.16737 | 0.75 |
| Win32.HLLP.Neshta | 0.71 |
| Trojan.Hosts.5268 | 0.66 |
| Win32.HLLW.Phorpiex.54 | 0.64 |
| Trojan.Mayachok.18024 | 0.60 |
| Trojan.Mayachok.18397 | 0.59 |
| Win32.Sector.22 | 0.54 |
| Trojan.Mayachok.17994 | 0.53 |
| Trojan.Mayachok.1 | 0.47 |
| Win32.HLLW.Gavir.ini | 0.46 |
| Trojan.Click2.47013 | 0.46 |
| BackDoor.Butirat.245 | 0.45 |
| Trojan.Mayachok.18566 | 0.45 |
Black.Energy reborn
In January 2013, Doctor Web discovered a new version of the Trojan BlackEnergy that was dubbed BackDoor.BlackEnergy.36. The breakdown of the BlackEnergy botnet—the largest botnet designed to send spam—was reported by many world media outlets in summer 2012. The Black.Energy botnet was capable of sending as many as 18 billion messages per day at its peak period of activity. But, thanks to the joint efforts of information security activists, by autumn of last year, the botnet's main controlling servers were shut down, and by December, the botnet ceased to operate completely.
However, in January 2013, criminals attempted to create a new botnet with the malware BackDoor.BlackEnergy.36. Unlike its previous editions in the malware family, BackDoor.BlackEnergy.39 has its configuration file encrypted and stored in the dynamic linking library whose code is injected into the process svchost.exe or explorer.exe when the Trojan is launched. In addition, the criminals slightly modified the network protocol used by BackDoor.BlackEnergy.36 to communicate with the control center. At first, the criminals didn't send any commands to the bots. Apparently, they expected the growing botnet to reach a certain number of zombie machines. However, they soon employed it to mount a DDoS attack on one of the most popular Russian entertainment sites. The Trojan was discovered while Doctor Web's virus analysts were monitoring another large botnet, Backdoor.Andromeda. More detailed information about this threat can be found in news stories published at drweb.com.
Threats to Android
The wide popularity of mobile devices running Android has led to a natural increase in interest on the part of criminals in personal information stored on such devices. A trend toward increased growth in the quantity of malware and riskware designed to retrieve confidential information was noted starting in 2012 and persisted and persisted in early 2013
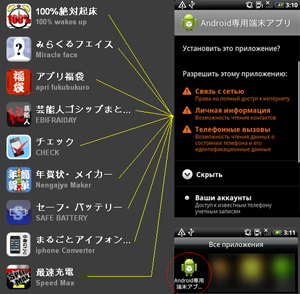
Another Trojan for Android designed to steal information from phone books on devices belonging to Japanese users was discovered at the beginning of January. Like other similar malicious applications, Android.MailSteal.2.origin is distributed by means of spam emails that prompt users to install one or another useful program. Clicking on the link brings careless users to a site that simulates Google Play’s official catalogue, and here, they can unsuspectingly install the Trojan on their device. It is worth mentioning that criminals attempt to give their victims freedom of choice by offering several different applications, but all of them contain the same malware. Android.MailSteal.2.uses a standard approach to disguise its operation: when launched, it notifies the user that it is performing an initial configuration, but after a while, it reports that it was unable to run on the target mobile device. Simultaneously it covertly searches for contact information and, when found, transmits the relevant data, such as email addresses and phone numbers, to a remote server. The acquired information can later be used by criminals in their spam campaigns or sold on the black market.
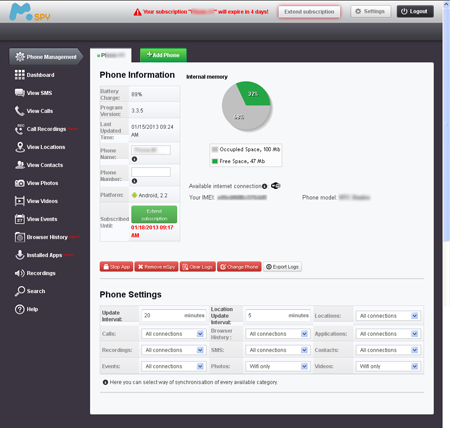
In January Doctor Web's virus analysts also discovered a significant number of new commercial spyware: Program.SpyMob.origin, Program.MSpy.2.origin, Android.Phoggi.1.origin, Program.OwnSpy.1.origin, Program.Copyten.1.origin, and Program.Spector.1.origin. In addition, the virus databases have been updated to include definitions for modifications of spyware programs for the Blackberry mobile platform. These were dubbed BlackBerry.Phoggi, Program.Spector.1, Program.Spector.2, and Program.Spector.3.
Recall that commercial spyware can control various features of a mobile device: they can monitor SMS communications, incoming and outgoing phone calls and acquire a device's GPS coordinates. Such programs are often used without the knowledge of the device's owner, so the owner’s personal information can be at risk. The wide variety of spyware found in January indicates that such services are in high demand, and that the number of such programs will grow steadily.
Other threats in January
In early January 2013 Doctor Web discovered a new Trojan called BackDoor.Finder, which is located predominantly in the USA. The Trojan injects its code into the processes of the most popular browsers (Microsoft Internet Explorer, Mozilla Firefox, Maxtron, Chrome, Safari, Mozilla, Opera, Netscape and Avant), intercepts queries to various search engines (google.com, bing.com, yahoo.com, ask.com, search.aol.com, search.icq.com, search.xxx, www.wiki.com, www.alexa.com or yandex.com) and displays links to sites designedby hackers instead of search results. More information about this threat can be found in one of our news stories.
BackDoor.Butirat.245, a program belonging to a well-known malware family, was also discovered in January. When commanded by intruders, this malware can download and launch executables in an infected system and steal passwords stored by popular FTP client software. For additional information about this threat, please refer to a virus review published at drweb.com.