Doctor Web’s review of virus activity on mobile devices in 2025
January 15, 2026
Overview
As in the previous year, the most common unwanted software programs were those offering game-like tasks to complete in exchange for virtual rewards. Users were promised the ability to convert their rewards into real money, but, in reality, no such opportunities were provided.
The most active riskware programs were apps modified with the NP Manager tool. This tool obfuscates and protects the code of modified programs so that it becomes more difficult to be analyzed and detected, and also allows digital signature verification to be bypassed once the programs are modified. The most commonly detected adware programs were unofficial WhatsApp messenger mods that automatically open advertising links when the app is in use.
Last year, new cases of malware being implanted into the firmware of various Android device models were recorded. We informed users about one of them in spring 2025. Cybercriminals had managed to pre-install the Android.Clipper.31 trojan on several budget smartphone models and used it to steal their victims’ cryptocurrency.
Also in spring, our specialists discovered the Android.Spy.1292.origin trojan, which threat actors had embedded into a modified version of Alpine Quest mapping software. This malware targeted Russian military personnel and was used for cyberespionage purposes.
In late summer, Doctor Web’s anti-virus laboratory informed users about Android.Backdoor.916.origin, a backdoor being distributed via popular messengers. The attackers used it to spy on employees of Russian companies and collect their confidential information.
Already in the fall, we warned about the dangerous Android.Backdoor.Baohuo.1.origin backdoor, which cybercriminals had embedded into modifications of the Telegram X messenger. This malicious program allowed intruders to hack their victims’ Telegram accounts and control the messenger on behalf of the account owners.
Over the last 12 months, Doctor Web's anti-virus laboratory identified more than 180 threats on Google Play, which have been downloaded over 2,165,000 times. Among them were various trojans that subscribe users to paid services and fake apps used for fraud, as well as new adware and unwanted software.
In 2025, malware creators continued utilizing various techniques aimed at complicating the analysis of malicious Android programs and evading anti-viruses. Converting DEX code into C code was one of the popular methods employed. In addition, our virus analysts noted that when creating malware, threat actors are using AI assistants that help write their apps’ code.
Principal trends in 2025
- Ad-displaying trojans were once again the most common Android threats
- The NP Manager tool, used to obfuscate the code of modified apps and allow digital signature verification to be bypassed after the apps are modified, has grown in popularity
- Banking trojans were more active
- New cases of Android devices with infected firmware have been identified
- Cybercriminals continued using both new and well-known techniques to protect malware from detection and analysis
- Malware creators have been actively using AI assistants to write malicious code
- New threats emerged on Google Play
The most notable events of 2025
In April 2025, Doctor Web’s experts uncovered a large-scale campaign to steal cryptocurrency from Android device owners. Threat actors compromised the supply chain of several Chinese manufacturers and embedded the Android.Clipper.31 trojan into the firmware of several budget smartphone models. Malware creators built this trojan into a modified version of WhatsApp messenger. For this, they used the LSPatch instrument, which allows them to alter the apps’ operating logic without changing their code.
Android.Clipper.31 intercepts messages sent and received in the messenger, searches for the addresses of the Tron and Ethereum crypto wallets in them, and replaces them with addresses belonging to the attackers. At the same time, the trojan conceals this substitution, and in such messages, victims are shown the correct wallets. Android.Clipper.31 also sends all jpg, png, and jpeg images to threat actors in order to search for saved mnemonic phrases that allow access to crypto wallets. Cybercriminals also embedded Android.Clipper.31 in dozens of other apps, including popular crypto wallet programs, QR scanners, and other messengers, like Telegram. These modifications were distributed through malicious websites.
In 2025, new cases emerged of malware being preinstalled into the system area of Android devices. One malicious group, for example, was able to embed new versions of dangerous Android.Triada trojans into the firmware of a number of budget smartphones. Triada malware poses a threat because it can infect the Zygote system process. This process is directly involved in launching all applications in the system, so Triada trojans can subsequently inject themselves into any application on the device, effectively gaining complete control over it. Threat actors use these trojans to download and install other malware as well as unwanted apps and adware. Moreover, attackers can use them to spy on victims, subscribe users to paid services, and so on. New cases of Android TV box sets having infected firmware were also identified. These cases involved new versions of the Android.Vo1d trojan, which our company discovered in 2024. The Vo1d malware is a backdoor that places its component into the system area of infected devices and can covertly download and install third-party software upon receiving attackers’ commands.
Also in April, our anti-virus laboratory detected a campaign to distribute the Android.Spy.1292.origin spyware trojan, targeting Russian military personnel. Threat actors embedded this malware into one of the versions of Alpine Quest mapping software and distributed it via their Telegram channel, which they passed off as the official one. A Russian Android app catalog was another source for its distribution.
The Telegram channel that attackers used to distribute a malicious Alpine Quest modification containing Android.Spy.1292.origin
Android.Spy.1292.origin sent a variety of confidential data to the cybercriminals, including mobile phone number and account information, phone book contacts, and the device’s geolocation and the files stored in its memory. The trojan could also steal certain files when commanded to do so by the attackers. Threat actors were interested in confidential documents that users sent via popular messaging apps as well as the Alpine Quest app’s location log file.
In August, we reported on cases of the Android.Backdoor.916.origin backdoor being distributed via direct messages in popular messaging apps. The attackers offered potential victims an “anti-virus” that could be installed from the APK file attached to the messages. This file was, in fact, concealed malware. Our anti-virus laboratory discovered the first Android.Backdoor.916.origin versions in January 2025 and has been monitoring their activity ever since, which allowed us to quickly identify this campaign.
Android.Backdoor.916.origin misleads users by imitating the operation of an anti-virus
When installed on an Android device, Android.Backdoor.916.origin allows confidential information to be stolen and users to be spied on. For instance, via this backdoor, threat actors can listen to conversations, broadcast from a device’s camera, track geolocation, and steal content from messengers and browsers. Moreover, Android.Backdoor.916.origin implements keylogger functionality to intercept entered text, including passwords. According to our experts, the backdoor is used in targeted attacks and is not intended for mass distribution. The primary target for cybercriminals is employees of Russian companies.
In October, Doctor Web published information on the multi-functional backdoor Android.Backdoor.Baohuo.1.origin, which our malware analysts discovered in modified versions of the Telegram X messenger. The main source of its distribution was via malicious websites to which potential victims are directed through ads in mobile programs. On such sites, users are encouraged to install Telegram X, supposedly to find a partner for conversation and dating. And these Internet resources are primarily targeting residents of Indonesia and Brazil. At the same time, we also detected this backdoor in a number of third-party Android app catalogs.
An example of a malicious website from which the trojan version of Telegram X was downloaded
One of Android.Backdoor.Baohuo.1.origin’s tasks is to steal confidential data. For example, the malicious program steals the login and password from the victim’s Telegram account, the messenger’s chat history, incoming SMS, and the phone book contacts; it can also intercept the clipboard contents. However, threat actors use it not only as a spyware tool. With the help of Android.Backdoor.Baohuo.1.origin, they can practically control both the hacked account and the messenger itself, altering its functionality. For instance, the backdoor allows threat actors to covertly add and remove users from Telegram channels, join conversations on their behalf and conceal devices authorized for their account. To perform actions that require changing the app’s operating logic, the Xposed framework is used. Cybercriminals control the backdoor both in the traditional way–via a C2 server–and by sending commands through the Redis database, something not seen previously in other Android malware. The total number of devices infected with Android.Backdoor.Baohuo.1.origin exceeded 58,000, while over 3,000 different models of smartphones, tablets, TV box sets, and even cars with Android-based on-board computers, were affected.
Countries with the highest number of devices infected with Android.Backdoor.Baohuo.1.origin
Statistics
According to detection statistics collected by Dr.Web Security Space for mobile devices, the most common Android threats in 2025 were various malicious programs. Users encountered them in 81.11% of cases. These were followed by potentially dangerous apps, whose share was 10.73%. Adware apps, detected in 5.89% of cases, ranked third. Unwanted programs were the least detected threats as they accounted for 2.27% of detections.
Compared to the previous year, the share of malicious and potentially dangerous programs increased, while the share of unwanted software and adware decreased.
Malicious programs
For several years, ad-displaying trojans from the Android.HiddenAds family have been the most commonly detected malware. In 2025, the situation did not change, although over the course of the last 12 months, their share slightly decreased from 31.95% to 27.42%.
These trojans display intrusive ads in the form of full-screen banners and videos. To make it harder for users to detect and delete them from their infected devices, such malicious programs try to “hide” after installation. For example, they can conceal or substitute their icons in the home screen menu.
The most active member of this family, accounting for more than a third of detections, was Android.HiddenAds.657.origin. This trojan came to the attention of our virus analysts back in 2024, and has been in the lead ever since. Android.HiddenAds.657.origin is one of many variants of Android.HiddenAds.1994, a malicious app known since 2021. Several new versions of the latter, like Android.HiddenAds.666.origin and Android.HiddenAds.673.origin, were also distributed in 2025. It is possible that over time they may also rise to the top positions, as previously happened with other Android.HiddenAds.1994 modifications.
Over the course of 2025, users again encountered Aegis, a subfamily of Android.HiddenAds. But the share of such trojans in the total number of times the family was detected significantly decreased—from 17.37% to 3.11%. These trojans can automatically run after installation. Among the most active variants were Android.HiddenAds.Aegis.1 and Android.HiddenAds.Aegis.8.origin.
The second most common malware programs were the ad-displaying trojans Android.MobiDash, whose share increased from 5.38% to 15.64%. Android.MobiDash.7859 was the top modification among them. These trojans were followed by Android.FakeApp—fake programs that cybercriminals use for fraudulent purposes. Android.FakeApp malware can load various websites instead of providing the declared functionality. Such trojans accounted for 10.94% of detections, which is lower than the 2024 figure, when their share was 18.28%. Such a decrease was, in part, due to the fact that the Android.FakeApp.1600 trojan was less active. However, this malicious program still remains the most widespread member of the family. Its main task is to load online casino websites.
The share of trojans from the Android.Spy family, which implement a variety of spyware functionality, decreased from 11.52% to 3.09%. At the same time, the activity of banking trojans increased. Their share of the total number of malware detections was 6.94%, compared to 6.29% a year earlier.
In 2025, the number of software packer detections increased from 5.49% to 6.01%. Threat actors can use such instruments to shield malware from detection and analysis. Malicious apps containing the packer Android.Packed.57146 were most commonly detected on protected devices.
Various malicious WhatsApp messenger mods were also widespread. Among them were modifications (Dr.Web detects them as Android.Click.1812) that load websites without the victims noticing. Multi-functional trojans from the Android.Triada family also increased their activity—from 2.74% to 7.48%. Cybercriminals can embed such trojans into the firmware of Android devices.
The ten malicious programs most commonly detected in 2025:
- Android.HiddenAds.657.origin
- Android.HiddenAds.4214
- Android.HiddenAds.655.origin
- Android.HiddenAds.4213
- Android.HiddenAds.666.origin
- Trojan apps designed to display intrusive ads. Members of the Android.HiddenAds family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.MobiDash.7859
- A trojan app that displays obnoxious ads. It is a special software module that developers incorporate into applications.
- Android.FakeApp.1600
- A trojan app that loads the website that is hardcoded into its settings. Known modifications of this malicious program load an online casino site.
- Android.Click.1812
- The detection name for malicious WhatsApp messenger mods that can covertly load various websites in the background.
- Android.Packed.57146
- The detection name for malicious apps that are packed with a popular commercial code obfuscator.
- Android.Triada.5847
- The detection name for a packer for Android.Triada trojans that is designed to protect them from being detected and analyzed. Threat actors most often use the packer together with the malicious Telegram messenger mods in which these trojans are embedded.
Unwanted software
Program.FakeMoney.11 apps were once again the most widespread unwanted software of 2025, accounting for 51.96% of detections. These programs offer users a reward for completing certain tasks and supposedly allow them to convert the reward into real money. In reality, no actual payouts are made. Along with Program.FakeMoney.11, other similar programs, like Program.FakeMoney.14 and Program.FakeMoney.16, also became widespread. However, users encountered them much less frequently.
Program.FakeAntiVirus.1 apps, which imitate the operation of anti-virus software and detect non-existent threats, were in second place with a share of 10.37%. In order for the infection to be “cured”, they encourage users to buy the full version of the software.
With a share of 6.41%, Program.CloudInject.1 apps, which are modified in the CloudInject cloud service, were the third most frequently encountered unwanted software. Variants of them, detected as Program.CloudInject.5, accounted for 5.08% and came in close behind them, occupying fourth place. Changes to such programs are made directly on a remote server, while access to the service is provided by the utility Tool.CloudInject, which is only a shell for working with it. When apps are modified, dangerous system permissions and an obfuscated code are added to them. Moreover, modders can remotely control the modified apps via the CloudInject service. For example, they can lock the apps and demand that a code be entered to further use them.
In 2025, there was a slight increase in the number of apps detected that can be utilized to monitor users and control their activity. In the hands of malicious actors, such instruments become spyware. For example, the share of the Program.TrackView.1.origin app and its variant, Program.TrackView.2.origin, increased from 2.40% to 2.91% and from 0.21% to 0.97%, respectively. The share of Program.SecretVideoRecorder.1.origin increased from 2.03% to 2.56%, and its variant Program.SecretVideoRecorder.2.origin increased from 0.90% to 1.02%. Program.SnoopPhone.1.origin's figure increased from 0.31% to 1.01%.
The ten unwanted programs most commonly detected in 2025:
- Program.FakeMoney.11
- Program.FakeMoney.14
- The detection name for Android applications that allegedly allow users to earn money by completing different tasks. These apps make it look as if rewards are accruing for each one that is completed. At the same time, users are told that they have to accumulate a certain sum to withdraw their “earnings”. Typically, such apps have a list of popular payment systems and banks that supposedly could be used to withdraw the rewards. But even if users succeed in accumulating the needed amount, in reality they cannot get any real payments. This virus record is also used to detect other unwanted software based on the source code of such apps.
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.CloudInject.1
- Program.CloudInject.5
- The detection name for Android programs that have been modified using the CloudInject cloud service and the eponymous Android utility (the latter was added to the Dr.Web virus database as Tool.CloudInject). Such programs are modified on a remote server; meanwhile, the modders (users) who are interested in such modifications cannot control exactly what will be added to the apps. Moreover, these programs receive a number of dangerous system permissions. Once modification is complete, modders can remotely manage these apps—blocking them, displaying custom dialogs, tracking when other software is being installed or removed from a device, etc.
- Program.TrackView.1.origin
- Program.TrackView.2.origin
- The detection name for a program that allows users to be monitored via their Android devices. Malicious actors can utilize it to track a target device’s location, take photos and video with the camera, eavesdrop via the microphone, record audio, etc.
- Program.SecretVideoRecorder.1.origin
- Program.SecretVideoRecorder.2.origin
- The detection name for various modifications of an application that is designed to record videos and take photos in the background, using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
- Program.SnoopPhone.1.origin
- An application designed to monitor the activity of Android device owners. It allows intruders to read SMS, collect call information, track device location, and record the surroundings.
Riskware
In 2025, the most widespread, potentially dangerous software programs were apps modified using NP Manager, a tool that has been designed to modify programs and that contains various modules for obfuscating and protecting the apps’ code. It is also used to bypass digital signature verification after changes have been made to the apps. Threat actors often use this tool to protect malicious programs in order to make it harder for anti-viruses to detect them. Compared to 2024, the share of such apps increased from 24.52% to 53.59%, and they accounted for more than half of the riskware detections. Most commonly detected on protected devices were variants Tool.NPMod.3 (32.85%), Tool.NPMod.1 (12.61%), Tool.NPMod.1.origin (3.02%), and Tool.NPMod.4 (2.31%).
Tool.Androlua programs—frameworks for developing Android apps in the Lua programming language—were detected more frequently. Their share is now 8.11%, up from 3.93%. Such frameworks require many system permissions, including permission to use the Accessibility Service. Programs created with their help are based on Lua scripts that are encrypted and then decrypted right before execution. Such scripts can potentially be malicious. The share of apps modified with Tool.LuckyPatcher increased from 8.16% to 10.06%. This utility modifies installed apps by downloading specially prepared scripts from the Internet.
At the same time, the share of Tool.SilentInstaller utilities, which allow Android apps to be launched without installing them, decreased from 33.10% to 10.55%. The most commonly detected variants of this family in 2025 were Tool.SilentInstaller.14.origin (4.66%), Tool.SilentInstaller.6.origin (2.07%), and Tool.SilentInstaller.7.origin (1.88%). In addition, the share of the programs protected with the software packer Tool.Packer.1.origin decreased from 13.17% to 2.58%.
The ten riskware apps most commonly detected on protected Android devices in 2025:
- Tool.NPMod.3
- Tool.NPMod.1
- Tool.NPMod.1.origin
- Tool.NPMod.4
- The detection name for Android programs that have been modified using the NP Manager utility. This tool contains modules for obfuscating and protecting the apps’ code as well as for bypassing their digital signature verification after they are modified. The obfuscation it adds is often used in malware to make it more difficult to detect and analyze.
- Tool.Androlua.1.origin
- The detection name for some potentially dangerous versions of a specialized framework for developing Android software in the Lua scripting language. The main logic of Lua-based apps resides in the corresponding scripts that are encrypted and decrypted by the interpreter before execution. By default, this framework often requests access to a large number of system permissions in order to operate, including permission to use theAccessibility Service in Android. As a result, the Lua scripts that it executes can potentially perform various malicious actions in accordance with the acquired permissions.
- Tool.LuckyPatcher.2.origin
- Tool.LuckyPatcher.1.origin
- A tool that allows apps installed on Android devices to be modified (i.e., by creating patches for them) in order to change the logic of their work or to bypass certain restrictions. For instance, users can apply it to disable root-access verification in banking software or to obtain unlimited resources in games. To add patches, this utility downloads from the Internet specially prepared scripts, which can be crafted and added to the common database by any third party. The functionality of such scripts can prove to be malicious; thus, patches made with this tool can pose a potential threat.
- Tool.SilentInstaller.14.origin
- A riskware platform that allows applications to launch APK files without installing them. It creates a virtual runtime environment in the context of the apps in which they are integrated. The APK files, launched with the help of this platform, can operate as if they are part of such programs and can also obtain the same permissions.
- Tool.Packer.1.origin
- A packer tool designed to protect Android applications from unauthorized modification and reverse engineering. This tool is not malicious in itself, but it can be used to protect both harmless and malicious software.
Adware
Third-party WhatsApp messenger mods, detected as Adware.ModAd.1, topped the list of adware programs detected in 2025. Such modifications are given the functionality needed to open links when the messenger is being worked with. These links redirect users to advertised websites. Compared to 2024, Adware.ModAd.1’s share of all adware apps detected on protected devices decreased from 47.45% to 26.90%.
Adware.Adpush modules, which are embedded into Android apps and display notifications containing ads, ranked second, increasing their share from 14.76% to 26.19%. Third place, with 8.88%, was occupied by members of the Adware.Basement family. Their share remained almost the same, compared to the previous year. Such programs can display ads that lead to malicious websites.
Also prevalent were such adware families as Adware.Airpush (their detection rate rose from 4.35% to 5.14%), Adware.Fictus (an increase from 3.29% to 6.21% was observed), Adware.Youmi (an increase from 1.62% to 2.91% was observed), as well as Adware.Leadbolt (an increase from 2.26% to 2.41% was observed) and Adware.Jiubang (an increase from 1.70% to 2.38% was observed).
The ten most widespread adware programs detected on protected Android devices in 2025:
- Adware.ModAd.1
- The detection name for some modified versions (mods) of the WhatsApp messenger, whose functions have been injected with a specific code. This code is responsible for loading target URLs by displaying web content (via the Android WebView component) when the messenger is in operation. Such web addresses perform redirects to advertised sites, including online casino, bookmaker, and adult sites.
- Adware.AdPush.3.origin
- Adware.Adpush.21846
- Adware.AdPush.39.origin
- Adware modules that can be built into Android apps. They display notifications containing ads that mislead users. For example, such notifications can look like messages from the operating system. In addition, these modules collect a variety of confidential data and are able to download other apps and initiate their installation.
- Adware.Basement.1
- These apps display unwanted ads that often lead to malicious and fraudulent websites. They share a common code base with Program.FakeMoney.11 unwanted applications.
- Adware.Fictus.1.origin
- An adware module that malicious actors embed into cloned versions of popular Android games and applications. Its incorporation is facilitated by a specialized net2share packer. Copies of software created this way are then distributed through various software catalogs. When installed on Android devices, such apps and games display obnoxious ads.
- Adware.Airpush.7.origin
- Adware modules that can be built into Android apps and display various ads. Depending on the modules’ version and modification, these can be notifications containing ads, pop-up windows or banners. Malicious actors often use these modules to distribute malware by offering their potential victims diverse software for installation. Moreover, such modules collect personal information and send it to a remote server.
- Adware.Youmi.4
- The detection name for an unwanted adware module that adds advertising shortcuts onto the Android OS home screen.
- Adware.Jiubang.1
- Unwanted ad-displaying software for Android devices that displays a banner showing recommended programs when applications are being installed.
- Adware.Inmobi.1
- The detection name for some versions of the Inmobi adware SDK. These are capable of making phone calls and adding event entries into an Android device’s calendar.
Threats on Google Play
In 2025, Doctor Web’s anti-virus laboratory discovered over 180 malicious, unwanted, and adware apps, which have been installed a combined total of at least 2,165,040 times. Among them were various modifications of the trojans Android.HiddenAds.4213 and Android.HiddenAds.4215, which concealed their presence on infected devices and displayed ads on top of the system interface and other programs. These trojans were distributed under the guise of image-editing tools, camera apps for taking photos and videos, and some other software.
The programs Time Shift Cam and Fusion Collage Editor were adware trojans from the Android.HiddenAds family
Cybercriminals distributed the cryptocurrency-stealing trojans Android.CoinSteal.202, Android.CoinSteal.203, and Android.CoinSteal.206, disguising them as official software from the Dydx crypto exchange and from the blockchain platforms Raydium and Aerodrome Finance.
The programs Raydium and Dydx Exchange were, in fact, trojans for stealing cryptocurrency
These malicious apps asked users to enter a mnemonic phrase—supposedly for connecting to a crypto wallet. But the information provided was actually sent to the attackers. To further confuse potential victims, the forms for entering mnemonic phrases could be disguised as requests from other crypto platforms.
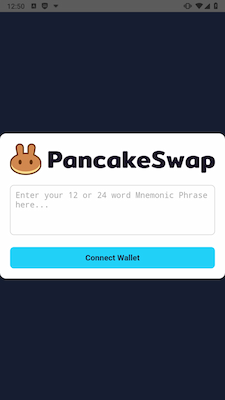
Android.CoinSteal.206 displays a phishing form, supposedly from the crypto exchange PancakeSwap, that asks users to enter the mnemonic phrase for accessing their crypto wallet
Throughout the year, our specialists uncovered over 80 malicious Android.Joker programs that subscribe users to paid services. They were disguised as various software, including messengers, photography apps, system tools, image-editing programs, and apps for working with documents.
Examples of the discovered Android.Joker trojans. Android.Joker.2494 was distributed as the messenger File Text Messages, and Android.Joker.2496–as the utility Useful Cleaner for optimizing a smartphone’s operation
Cybercriminals again distributed all sorts of Android.FakeApp fake programs, using them in a number of fraudulent schemes. The programs’ main task is to load target websites. Threat actors passed off some of these trojans as finance-related software. Such apps loaded phishing websites as well as fraudulent sites that were supposedly related to investments and online earnings. Other fake apps from this family were distributed as games and, under certain conditions, could load online casino and bookmaker websites. We discovered over 100 such programs on Google Play.
Examples of Android.FakeApp fake programs. The trojan Android.FakeApp.1863 was hidden in the TPAO app and targeted Turkish users, offering them the opportunity to manage deposits and income. The trojan Android.FakeApp.1840 was distributed as the game Pino Bounce and could load an online casino site
Doctor Web’s virus analysts also discovered new adware. Dubbed Adware.Adpush.21912, this program was hidden in the Coin News Promax app with information about cryptocurrencies. Adware.Adpush.21912 displays notifications which, when clicked, load into WebView the link specified by the С2 server.
The Coin News Promax app from Google Play was the adware program Adware.Adpush.21912
In addition, our specialists found Program.FakeMoney.16, an unwanted app distributed as a program called Zeus Jackpot Mania. In this app, users, in a game-like style, obtained virtual rewards that allegedly could be converted into real money and withdrawn from the program.
The Zeus Jackpot Mania app was the unwanted software Program.FakeMoney.16
To “withdraw” the money, users were asked to submit some information to the program, but they did not receive any payouts.
Program.FakeMoney.16 asks the user to provide their full name and information about their bank account
Banking trojans
According to the detection statistics provided by Dr.Web Security Space for mobile devices, in 2025, the share of banking trojans, out of the total number of malicious apps registered, was 6.94%, which is slightly more than the 6.29% figure from the year before. During the first three months, banking trojan activity remained at approximately the same level, but at the beginning of the second quarter, it significantly increased. After that, it began to gradually decline, reaching the annual minimum in July. From August onwards, the number of detections began to grow again, peaking in October. At the end of the year, another decline was observed.
In 2025, threat actors continued using a number of popular banking trojan families to carry out their attacks. Among the most active were the malicious apps Android.Banker.Mamont, Coper, Android.BankBot.Ermac, and some others. Moreover, new versions of NGate trojans were found. These trojans use NFC technology to steal money. They send data from the NFC chip of infected devices to the attackers, allowing fraudsters to withdraw money from victims’ accounts at ATMs or make purchases using contactless payment without further user involvement. Among the most active were modifications like Android.Banker.NGate.8, Android.Banker.NGate.17, and Android.Banker.NGate.5.origin.
Android.SpyMax, malicious apps with spyware functionality, continued to be distributed. These trojans are based on leaked source code of the SpyNote RAT trojan. Cybercriminals use them in a variety of scenarios, including as banking trojans. At the same time, compared to 2024, the activity of Android.SpyMax malware decreased. These trojans accounted for 12.35% of banking trojan detections, compared to 32.04% the year before.
In 2025, Russian users were most likely to encounter various banking trojans belonging to the extensive Mamont family, as classified by Doctor Web (e.g., Android.Banker.790.origin, Android.Banker.Mamont.3.origin, and Android.Banker.Mamont.28.origin). This family includes different malicious apps that malware creators continue to actively modify and develop. These apps intercept SMS containing one-time codes from credit organizations and steal bank card data and other confidential information.
Throughout the year, our experts observed the activity of banking trojans targeting users from Uzbekistan and neighboring countries, including Armenia, Azerbaijan, and Kyrgyzstan. Trojans like Android.Banker.951.origin, Android.Banker.881.origin, and Android.Banker.963.origin were most frequently detected on protected devices. They hijack verification codes from SMS coming from banks. Cybercriminals constantly modify such trojans to make it harder for them to be detected. Turkish users were most often attacked by the Android.BankBot.Coper.12.origin, Android.Banker.5685, and Android.Banker.864.origin banking trojans, which are also capable of stealing the contents of SMS.
At the same time, Iranian residents encountered the trojans Android.BankBot.1190.origin and Android.BankBot.1191.origin and modifications of them. These malicious programs steal banking information from SMS, finding data about the victim’s bank cards, accounts, available funds, completed transactions, etc., and then send it to the attackers. They also collect contact information from the phone book and can send SMS on the attackers’ command.
Users from many Southeast Asian and the Asia-Pacific region countries, including Indonesia and South Korea, were attacked by the Android.BankBot.Remo.1.origin trojan. This malicious program utilizes the Accessibility Services of the Android OS to steal data from bank software and crypto wallets installed on infected devices. In addition to the Remo trojan, users in South Korea also encountered such trojans as Android.BankBot.15140, Android.BankBot.Ermac.6.origin, and GoldDigger (Android.BankBot.GoldDigger.9, Android.BankBot.GoldDigger.11).
The GoldDigger malware was also used to attack Indonesian and Thai users. And the banking trojan Android.BankBot.Gigabud.1.origin was used against customers of credit organizations in Indonesia and Malaysia. At the same time, threat actors continued to use MoqHao trojans in attacks on Japanese audiences. The most widely used MoqHao modifications included Android.Banker.672.origin, Android.Banker.5063, Android.Banker.740.origin, and a number of others.
One banking trojans targeting users in India was Android.Banker.6209. This trojan imitates the appearance of genuine banking software to steal victims’ data, including their names, bank card numbers and CVV security codes. In addition, RewardSteal banking trojans, such as Android.Banker.814.origin, Android.Banker.913.origin, and Android.Banker.5132, continued to be active. To steal banking data, they are camouflaged as software that appears to be backed by large Indian credit organizations, for example, ICICI, SBI, Axis, and PM Kisan.
Android device owners in Brazil were most frequently attacked by Android.BankBot.1183.origin malicious apps and some members of the NGate family, like Android.Banker.NGate.8, Android.Banker.NGate.9, and Android.Banker.NGate.14.
In 2025, malware creators continued utilizing different techniques to protect Android banking trojans from analysis and detection. For instance, various code obfuscation and concealment methods were popular, such as DEX to C (which involves converting executable DEX code into C programming language code). Another widespread solution that was employed involved obfuscating malicious apps with the NP Manager utility.
Techniques involving manipulating the format of ZIP archives, which are essentially APK files of Android apps, remain popular. These include manipulating the compression method and compressed size fields in the header structure of the local file inside the APK, and also using incorrect disk data in ECDR and CD records. We covered these techniques in more detail in our previous review, in the section dedicated to banking trojans. After such manipulations, trojan apps remain fully functional, but many static analysis instruments perceive them as damaged and are unable to process them correctly.
Malware creators have increased their use of dropper programs to conceal their main payload in order to, for example, bypass the internal protection on Google Play. Cybercriminals are also using AI assistants when writing banking trojan code, which simplifies the malware-development process and leads to the emergence of new families. Moreover, threat actors are increasingly using Telegram bots to control banking trojans and exfiltrate data from infected devices.
Prospects and trends
In 2025, we observed high activity on the part of ad-displaying trojans, which remain the most common threats targeting the Android OS. Various fake programs used for fraudulent purposes, including phishing and money theft, were also widespread again. In addition, the number of attacks involving banking trojans continued to increase. All of these malicious apps are a source of illegal income for cybercriminals, which is why their popularity remains high. In 2026, they are highly likely to once again be one of the most popular money-making tools for cybercriminals. Meanwhile, malware creators are increasingly using Telegram bots to control banking trojans. This trend is likely to continue.
The emergence of Android.Clipper.31 malware and new versions of the Android.Vo1d and Android.Triada trojans in the firmware of smartphones and TV box sets indicates the continued interest of attackers in distributing malware in ways that significantly complicate its detection. It is likely that this trend will continue in the new year and that we will see more cases of malicious programs being pre-installed on smartphones, TV box sets, and other types of Android devices.
We should also expect that more sophisticated malicious apps, ones capable of performing a wider range of tasks, will emerge. These could be yet other backdoors and various spyware trojans. Moreover, malware creators will likely use official app catalogs, including Google Play, to distribute malware and unwanted software.
Threat actors will also continue implementing various protection methods for the instruments they create. They will also use AI assistants more often when writing code, which will lead to the emergence of more new families.
Doctor Web monitors the threat landscape in the mobile segment and promptly responds to emerging challenges. We recommend to Android users that they install Dr.Web Security Space for mobile devices to protect themselves from malicious and other dangerous programs.