Baohuo, the gray eminence. Android backdoor hijacks Telegram accounts, gaining complete control over them
Real-time threat news | Threats to mobile devices | All the news
October 23, 2025
Android.Backdoor.Baohuo.1.origin started being distributed back in mid-2024, as evidenced by earlier modifications found during its analysis. The main method for delivering this backdoor to target devices is through in-app ads in mobile programs. Potential victims are shown ads that encourage them to install the Telegram X messenger. When clicking on such banners, users are redirected to malicious websites from which the trojan APK file is downloaded.
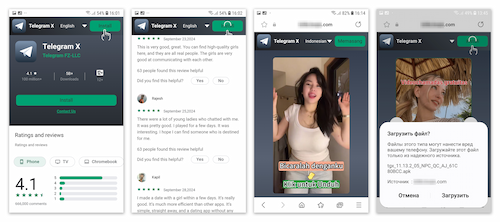
These sites are designed to look like an app catalog, while the messenger itself is positioned on them as a platform for conveniently finding a partner for communication and dating. This is indicated by banners with overlaid advertizing text about “free video chats” and invitations to “talk” (for instance, disguised as screenshots of the video call window) as well as by reviews from supposedly happy users that the threat actors actually composed. It should be noted that these webpages have functionality for selecting the displayed language, but the images themselves do not change.
One of the malicious sites from which the trojan version of Telegram X is downloaded. Potential victims are offered the chance to install an app where, according to “reviews”, it is easy to find a partner for communication and dating
Currently, cybercriminals have prepared standard templates with banners in only two languages—Portuguese, for users from Brazil, and Indonesian. Thus, Brazilian and Indonesian audiences are the main target for the attackers. At the same time, it is possible that over time, the threat actors’ interest will extend to users from other countries.
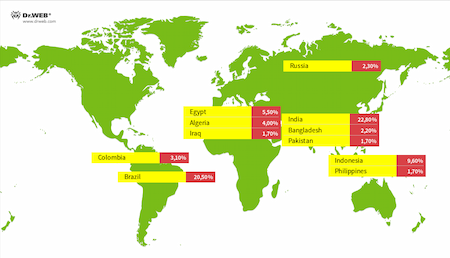
Studying the attackers’ network infrastructure allowed us to determine the scale of their activity. On average, Doctor Web’s malware analysts observe about 20,000 active connections of Android.Backdoor.Baohuo.1.origin. At the same time, the total number of infected devices has exceeded 58,000. Around 3,000 different models of smartphones, tablets, TV box sets, and even cars with Android-based on-board computers have been infected.
Countries with the highest number of devices infected with Android.Backdoor.Baohuo.1.origin (according to Doctor Web’s anti-virus laboratory)
However, malicious websites are not the only source for Android.Backdoor.Baohuo.1.origin’s distribution. Our experts have also detected it in third-party app catalogs, including APKPure, ApkSum, and AndroidP. Additionally, in the APKPure app store, the malware is posted on behalf of the official messenger developer, despite the fact that the digital signatures of the original version and the trojan modification are different. We have notified the online platforms where the trojanized versions of Telegram X were found.
The modified Telegram X with Android.Backdoor.Baohuo.1.origin implanted in it was distributed through APKPure on behalf of the messenger’s genuine developer
Doctor Web’s anti-virus laboratory discovered several Android.Backdoor.Baohuo.1.origin variations, which can be conditionally divided into 3 main modification groups:
- versions where the threat actors embedded the backdoor into the main executable DEX file of the messenger;
- versions where the backdoor is dynamically loaded in the form of a patch into the executable DEX file using the LSPatch tool;
- versions where the backdoor is located in a separate DEX file in the app’s resources directory and loaded dynamically.
Regardless of the modification type, Android.Backdoor.Baohuo.1.origin initializes when the messenger is launched. The messenger itself remains functional, and for users it looks like a regular program. In reality, however, malicious actors have complete control over it through the backdoor and can even alter the logic of its operation.
When cybercriminals need to perform an action that does not require interfering with the app’s main functionality, they use pre-prepared “mirrors” of the necessary messenger methods. For example, mirrors can be used to display phishing messages in windows that look indistinguishable from real Telegram X windows.
Methods are separate blocks of code in the structure of Android programs that are responsible for performing certain tasks.
If the action is not standard for the messenger, then the Xposed framework is used. It directly changes a certain functionality of the app via dynamic method modification. In particular, it can be used to hide certain chats and authorized devices as well as to steal the clipboard contents.
The main difference between the earlier versions of the malicious program and the current ones is in how the malware is controlled. Older versions communicated with cybercriminals and received commands from them via a C2 server, which is a traditional channel. However, over time, malware writers added to Android.Backdoor.Baohuo.1.origin the ability to receive additional commands that come from the Redis database, thus expanding its functionality. At the same time, they also provided for the duplication of new commands through a regular C2 server in case the database becomes unavailable. This is the first known case of using Redis to control Android malware.
When launched, Android.Backdoor.Baohuo.1.origin connects to the initial C2 server to download a configuration that, among other parameters, contains data to connect to Redis. Through this database, threat actors not only send specific commands to the malicious app but also update the trojan’s settings. For example, they assign current addresses for the C2 server and the NPS server. Malware writers use the latter to connect infected devices to their internal network (intranet) and turn them into a proxy for accessing the Internet.
Android.Backdoor.Baohuo.1.origin regularly connects to the C2 server via API requests and can receive the following tasks:
- upload incoming SMS and contacts from the infected device’s phonebook to the C2 server;
- upload the contents of the clipboard to the C2 server when minimizing the messenger and restoring its window;
- receive URLs from the C2 server to display ads, as well as the server address from which the trojan’s update in the form of a DEX file will be downloaded;
- receive encryption keys that are used when certain data is uploaded to the C2 server (for instance, the clipboard contents);
- request a group of commands for collecting information about installed apps, the message history, and contacts from the device’s phonebook, and about the devices logged into Telegram (this request is executed every 30 minutes);
- request an URL from the C2 server to download an update for Telegram X;
- request from the C2 server a configuration which is then saved as a JSON file;
- request information about the Redis database;
- upload information about the device to the C2 server whenever messenger network activity is detected;
- receive from the C2 server a list of bots that are to be added to the Telegram contact list;
- upload the following information to the C2 server every 3 minutes: the current app’s permissions, the device’s state (whether its screen is on or off, whether the app is active), and the mobile phone number with the name and password for the Telegram account;
- every minute, request commands in the same format as the commands from the Redis database.
To receive commands via Redis, Android.Backdoor.Baohuo.1.origin connects to the attackers’ corresponding server where it registers its own sub-channel. Threat actors connect to this sub-channel and post tasks in it, which the backdoor then executes. The malicious program can receive the following commands:
- create a blacklist of chats that will not be displayed in the Telegram X window;
- conceal specified devices from the user in the list of authorized devices for their account;
- block notifications from blacklisted chats for a specified time;
- display a window with information about the Telegram X messenger update (when the user clicks it, they are redirected to a target website);
- send the C2 server information about all of the installed apps;
- terminate the user’s current authorized Telegram login session on the infected device;
- display a window with information about the Telegram X app update, where the user is asked to install an APK file (if the file is missing, the trojan downloads it first);
- remove the Telegram Premium icon in the app’s interface for the current user;
- upload to the C2 server information from the Telegram X databases that store chat history, messages, and other confidential data;
- subscribe the user to a specified Telegram channel;
- leave a specified Telegram channel;
- join a specified Telegram channel on behalf of the user, using the provided URL;
- obtain the list of devices authorized in Telegram;
- request the user’s authentication token and upload it to the C2 server.
It should be noted that hijacking data from the clipboard (when the user minimizes the messenger and restores its window) allows various scenarios for stealing confidential data to be implemented. For example, the victim can copy the password or mnemonic phrase used to access their crypto wallet, copy text from some important document to send it to business partners, etc. The trojan will intercept this information from the clipboard and send it to the malicious actors.
Dr.Web Security Space for mobile devices successfully detects and deletes all known versions of Android.Backdoor.Baohuo.1.origin, so this malware does not pose a threat to our users.
More details about Android.Backdoor.Baohuo.1.origin
Indicators of compromise