Mobile threats in July 2014
Virus reviews | Hot news | Threats to mobile devices | All the news | Virus alerts
August 5, 2014
Making an illicit profit by stealing online bank account information and Android users' funds with the aid of various Trojans is becoming increasingly popular. Threats serving this purpose appeared several years ago, but they haven't seen much use until recently. Attacks involving malware like this are carried out in many countries, but has been one of the primary targets for quite a while. Doctor Web's virus analysts registered a substantial increase in the number of incidents involving such malicious programs in that country. For example, in June several new malicious programs were discovered including Android.Banker.28.origin.
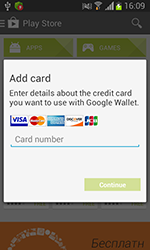
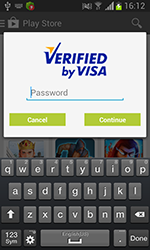
Spread in the guise of a Google Play client, this Trojan employs social engineering tricks to steal confidential banking information (NPKI certificates, online bank account login, phone number, credit card number and passwords). The program becomes operational only if an actual banking client application is running on a device. To lure the user into divulging all the information it needs, the Trojan mimics the look and feel of a legitimate application. The collected data is forwarded to criminals and can later be used to access victims' bank accounts and carry out unauthorised transactions.
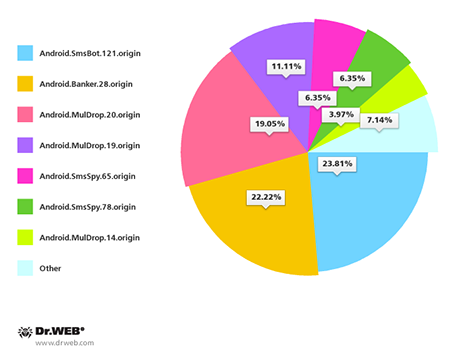
Most threats discovered in are distributed by means of unwanted SMS messages containing Trojan download links. Here,Android.Banker.28.origin is no exception. It accounts for 22.22% of SMS spam incidents. All in all, in the past month Doctor Web's security researchers registered 126 such spam campaigns. The percentage of Trojans distributed by means of these short messages is shown in the pie chart below.
Distributed as Adobe Flash Player, Android.BankBot.21.origin targeted devices in Russia. This program mimicked the dialogue used to associate a credit card with a Google Play account. The acquired information and all incoming messages were forwarded to criminals. In addition, cybercriminals could order the malware to perform other tasks such as sending short messages.
 |
 |
May 2014 saw the emergence of ransomware for Android that locks compromised devices and encrypts files before demanding a ransom from users who want to restore their devices to normal operation or get back their files. The number of programs like this has surged in a short period of time. In May, only two definitions for such malware were present in the Dr.Web virus database, but by the end of July, that figure soared to 54. In just two months, the number of these threats increased 27 times, i.e., by 2,600%.
Android.Locker.19.origin is one of the ransom programs discovered in July—it targets Android devices in the USA. When launched on a mobile device, the Trojan locks it and displays a ransom message. Once the device is locked, Android.Locker.19.origin won't allow the user to perform any action with the OS interface. It is noteworthy that this Trojan can not only lock a device, but can also encrypt files, but the attackers didn't use this feature. It is likely that it will be enabled in future versions of the Trojan.
 |
 |
 |
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live