Viruses can remove anti-viruses again
Real-time threat news | All the news | Virus alerts
December 14, 2010
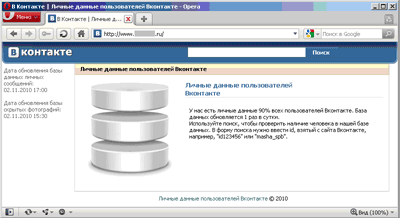
Trojan.VkBase.1 is a malicious program featuring such a technique. By now it has targeted only Russian users searching for someone else's personal information. Sooner or later such people may come across with a web-site where they are offered access to personal data of registered users of a Russian social networking web-site
The promised information downloaded by the user is an executable file detected by Dr.Web as Trojan.VkBase.1.
Launching the file brings up a Windows Explorer window is expected to display the long-sought data. Meanwhile, the malicious program is being installed into the system and the search for an installed anti-virus is performed.
Once an anti-virus is found, the system is restarted in the Safe mode to remove the anti-virus. The Trojan is equipped with routines that enable it to uninstall a large number of anti-malware applications.
Since Dr.Web SelfPROtect runs even in the Safe Mode, the Trojan utilizes an additional component (Trojan.AVKill.2942), that could exploit a vulnerability of the self-protection component to remove Dr.Web. The vulnerability has already been closed. Removing other anti-viruses didn't require employment of additional modules.
Once the anti-virus is removed, Windows is loaded in the normal mode and Trojan.Winlock.2477 blocks access to the system. Criminals demand from the user to refill the balance of a cell phone account in order to unlock the system. A fake warning also informs the user that their data has been encrypted and will be lost in 90 minutes.
Once the system is unlocked, Trojan.Fakealert.19448 (as detected by Dr.Web) mimics behaviour of the uninstalled anti-virus. It displays the icon of the removed anti-virus in the system tray. Clicking on the icon shows a window with the look and feel similar to those featured by the neutralized anti-virus. The user is informed that his computer is still protected. Clicking on the image closes it. The trick makes an inexperienced user to believe that their anti-virus is still operational.
Currently users of Dr.Web anti-viruses for Windows are protected from Trojan.VkBase.1 and against other malicious programs that may feature similar anti-virus removal techniques.