Doctor Web’s annual virus activity review for 2022
March 29, 2023
The most prominent email threats were various malicious scripts, phishing PDF documents and webpages, and malicious programs that exploited vulnerabilities in Microsoft Office documents. Backdoors and other trojans were also active in email traffic.
In spring 2022, Doctor Web published research on an APT attack that had targeted one of Kazakhstan’s telecom companies. Our specialists found out that the Calypso APT hacker group was behind this campaign. With that, the malicious actors were primarily interested in mail servers belonging to Asian companies that had Microsoft Exchange software installed on them. However, companies from other countries also fell victim to them.
During last year, our virus analysts discovered several attacks involving Linux malware. In September, cybercriminals attempted to infect a number of corporate computers with a crypto miner. And in December, a backdoor trojan that hacked websites based on the CMS WordPress was uncovered. To do so, it exploited vulnerabilities in many outdated versions of this platform’s plugins.
Doctor Web’s Internet analysts also noticed high activity on the part of fraudsters who have continued creating new phishing and fake websites. Phony sites of well-known banks, online stores, oil and gas corporations, logistics firms, and other companies enjoyed popularity among malicious actors. Moreover, these attackers skillfully adjusted their illegal activities to events taking place all over the globe.
However, mobile device owners were not forgotten either. Over the course of last year, Android users faced spyware apps, ad-displaying trojans, fraudulent software, and unwanted adware applications. With that, the malefactors again used Google Play to distribute all kinds of threats, which were downloaded by tens of millions of users. At the same time, our specialists discovered trojan apps designed to steal cryptocurrency from both Android and iOS-based device owners. In most cases, cybercriminals hid these trojans in modified versions of popular crypto-wallet software.
Principal trends of the year
- The detection of new targeted attacks
- The emergence of new threats for mobile devices
- An increase in the number of incidents involving ransomware trojans
- An increase in the number of fraudulent websites
The most notable events of 2022
In March 2022, Doctor Web released its research on an APT attack that targeted one of Kazakhstan’s telecom companies. In autumn 2021, this company had requested assistance regarding the possible infection of its corporate network. The investigation of this case revealed that the Calypso APT hacker group was behind this attack. Moreover, the company’s servers had been compromised much earlier—back in 2019. Threat actors used a variety of malicious instruments, but the main ones employed were backdoors Backdoor.PlugX.93 and BackDoor.Whitebird.30 and the tools Fast Reverse Proxy (FRP) and RemCom. Their primary target was mail servers belonging to Asian companies that had Microsoft Exchange software installed on them. However, companies from some other countries, including Egypt, Italy, the USA, and Canada also became victims of this APT attack.
In April, Doctor Web’s virus analysts warned users about the increasing number of attacks targeting Russian companies and organizations—when malicious actors encrypted files but did not demand a ransom for their decryption or leave any contact information for getting in touch with them. To access the infrastructure of targeted companies, the attackers used several schemes. First, they exploited different variants of the ProxyLogon and ProxyShell vulnerabilities in Microsoft Exchange software. Secondly, incidents of gaining access to administrative accounts data through a memory dump of the lsass.exe process via the ProcDump tool were recorded. If succeeded, attackers connected to the domain controller from where they installed Bitlocker and Jetico BestCrypt Volume Encryption software, used to encrypt storage devices. Second, incidents were recorded of cybercriminals using the ProcDump tool to gain access to administrative account data via a memory dump of the lsass.exe process. If successful, the attackers would connect to the domain controller that facilitated the installation of Bitlocker and Jetico BestCrypt Volume Encryption software on corporate network devices. This software was used to encrypt storage devices.
At the end of the summer, our analysts uncovered an attempt to infect some corporate Linux-based computers belonging to one of our clients, which involved a Linux.Siggen.4074 crypto-miner. The analysis our specialists performed revealed that a task to download this trojan was added into the cron scheduler. Because the Dr.Web anti-virus was present on the targeted systems, those attempts were successfully suppressed. And this once again showed the importance of protecting Linux systems as much as other platforms.
Already in December the need for such protection was demonstrated by the Linux.BackDoor.WordPressExploit.1 backdoor trojan discovered by our specialists. This malware was hijacking CMS WordPress-based websites, exploiting several dozen vulnerabilities in outdated versions of plugins for this platform, for which essential patches had not been installed. If such an attack was successful, a JavaScript downloaded from a remote server was injected into the webpages of targeted sites. After that, whenever users clicked anywhere on the infected pages, they were redirected to the websites the attackers wanted them to go to.
Over the course of the last year, fraudsters were highly active. With that, in addition to common scam schemes, they added new tricks to their arsenal that reflected their desire to capitalize on world events.
The malware landscape
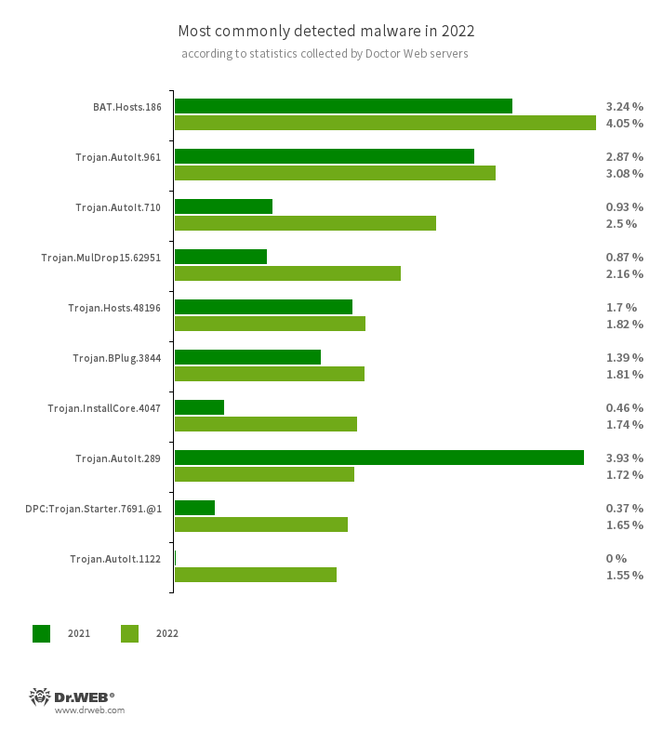
An analysis of Dr.Web detection statistics revealed a 121.60% increase in the total number of threats detected, compared to 2021. At the same time, the number of unique files decreased by 24.84%. Users were most often targeted by the type of trojans that attackers deploy in conjunction with other malware in order to make the latter difficult to detect. Moreover, users were faced with adware trojans and various software installers.
- BAT.Hosts.186
- A malicious script written in the Windows command interpreter language. It modifies the hosts file of systems by adding a certain list of domains to it.
- Trojan.AutoIt.961
- Trojan.AutoIt.710
- Trojan.AutoIt.289
- Trojan.AutoIt.1122
- A special tool written in the AutoIt scripting language and distributed as a component of a crypto-miner or a RAT trojan. It performs various malicious actions to make the main payload more difficult to detect.
- Trojan.MulDrop15.62951
- The detection name for a dropper that distributes and installs other malware on targeted computers.
- Trojan.Hosts.48196
- The detection name for a modified Windows OS hosts file. It is edited in such a way that users are unable to access websites of anti-virus companies and various IT forums that provide help with computer infections.
- Trojan.BPlug.3844
- A malicious browser extension designed to perform web injections into viewed webpages and block third-party advertisements.
- Trojan.InstallCore.4047
- A common adware installer that shows ads and installs additional programs without the user’s permission.
- DPC:Trojan.Starter.7691.@1
- The detection name for a threat whose process is initialized on a target system by executing the command line with certain parameters. In this particular case, an attempt to run the Trojan.Starter.7691 malware was detected. This trojan launches another malicious software on the target device.
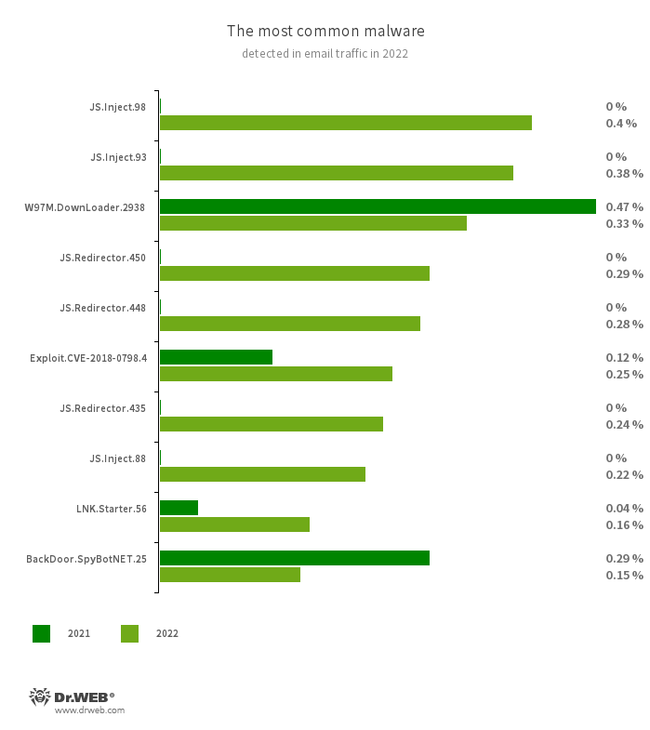
The most common threats in email traffic in 2022 were malicious software that exploited vulnerabilities in Microsoft Office documents and a wide variety of malicious scripts. In addition, cybercriminals were actively spreading fraudulent emails with phishing PDF documents and HTML files. These, for instance, could come as bogus login forms that imitate the authorization process on well-known sites. The data entered there was sent to the attackers.
- JS.Inject
- A family of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- W97M.DownLoader.2938
- A family of downloader trojans that exploit vulnerabilities in Microsoft Office documents. They can also download other malicious programs to a compromised computer.
- JS.Redirector.450
- JS.Redirector.448
- JS.Redirector.435
- Malicious scripts that redirect users to webpages controlled by fraudsters.
- LNK.Starter.56
- The detection name for a shortcut that is crafted in a specific way. This shortcut is distributed through removable media, like USB flash drives. To mislead users and cover up its operation, it has a default icon of a disk. When launched, it executes malicious VBS scripts from a hidden directory located on the same drive as the shortcut itself.
- Exploit.CVE-2018-0798.4
- An exploit designed to take advantage of Microsoft Office software vulnerabilities and allow an attacker to run arbitrary code.
- BackDoor.SpyBotNET.25
- A backdoor that is written in .NET. It is designed to operate with a file system (for example, it is able to copy, create, and delete files) and can terminate processes and take screenshots.
Encryption ransomware
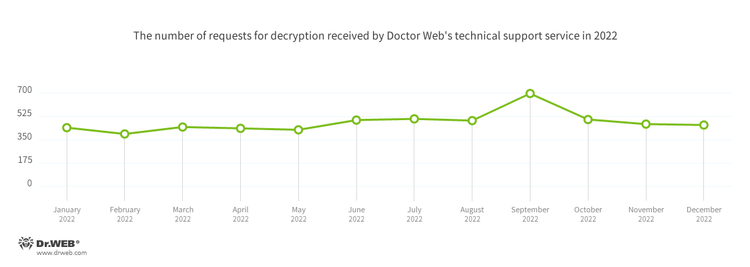
In 2022, Doctor Web’s virus laboratory registered 2.81% more requests to decrypt files affected by encryption trojans than in 2021. The registration dynamics of those requests for the 12 months of last year can be seen in the graph below:
The most common encoders of 2022:
- Trojan.Encoder.26996
- A trojan encoder known as STOP Ransomware. It attempts to obtain a private key from a server. If unsuccessful, it uses the hardcoded one. It is one of the few encoders that encrypts user data with the Salsa20 stream cipher.
- Trojan.Encoder.3953
- An encoder trojan that has several versions and modifications. It uses the AES-256 algorithm in CBS mode to encrypt files.
- Trojan.Encoder.567
- A trojan encoder written in Delphi. This encoder has many versions that use various encryption algorithms. Typically, it is distributed as email attachments.
- Trojan.Encoder.11539
- An encryptor that has different modifications for each different encryption algorithm set. Typically, it is distributed as email attachments and uses the AES-256 algorithm in CBC mode to encrypt files.
- Trojan.Encoder.30356
- A trojan encoder written in Delphi. It uses the AES-256 symmetric algorithm to encrypt files and asymmetric RSA-2048 to protect the private key.
Network fraud
In 2022, Doctor Web’s Internet analysts discovered a significant number of fraudulent and bogus websites covering a variety of topics. For instance, in February they noticed an increase in the number of sites disguised as online delivery services. For each visitor, a unique page containing confidential information was generated. On this page, potential victims were asked to enter their bankcard info to pay for an alleged “service”.
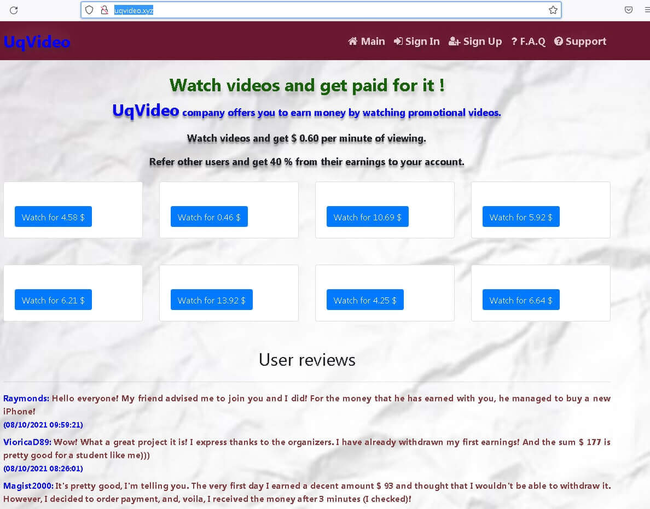
In March, they observed an increase in the activity of websites that allegedly paid users to watch videos. Potential victims were redirected from such sites to other Internet resources, where registration was mandatory and bankcard information had to be indicated. When this data was entered, it was sent to the attackers, and the users themselves did not receive any promised payouts.
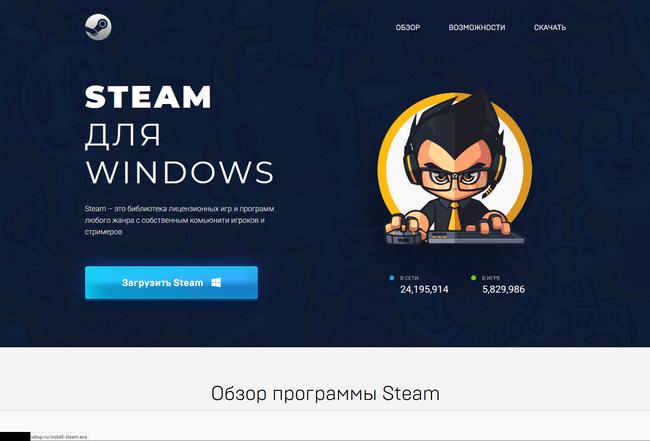
In April and May, fraudulent sites were successfully masquerading as official resources of developers of various well-known apps, like browsers, gaming platform clients, etc. Threat actors used those to distribute fake software installers with adware, unwanted software, and even malware. Below are examples of such imitation websites:
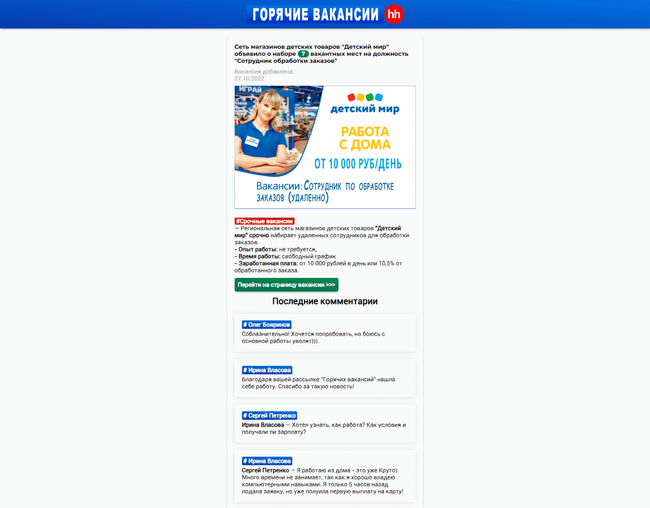
During autumn, fraudsters pretending to be acting on behalf of large Russian companies became active, offering employment with lucrative working conditions. For example, they created fake vacancies for the position of “remote order processing employee”. Candidates had to register an account and allegedly could immediately start working. However, in order to withdraw the money that they “earned”, they had to “activate” an account by paying a certain amount of their own money.
Below is an example of a fake website containing job offers. It uses the logo and name of the company on whose behalf a bogus vacancy was distributed.
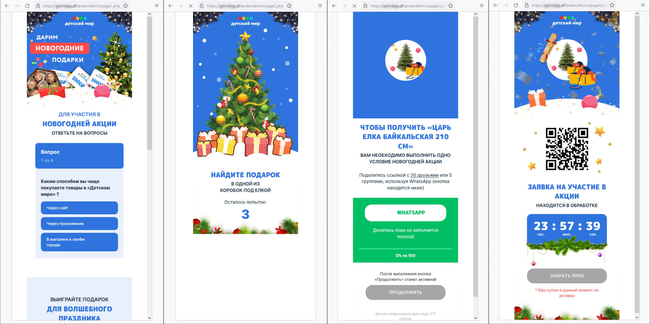
At the end of the year, Doctor Web’s Internet analysts observed an increase in the number of fraudulent sites on which visitors were encouraged to participate in promotions that were allegedly organized by famous companies and online stores. On such sites, mini-contests and prize draws were simulated. To “receive” a prize, users had to share a special link with a certain number of their contacts or group chats on WhatsApp messenger. Such links could lead to a variety of websites, including advertizing or malicious ones. Thus, scammers actually carried out their spam campaigns with the help of users themselves. At the same time, victims of this scheme did not receive their promised prizes as they were misled from the very beginning.
Among the fraudulent sites discovered in 2022 were again numerous Internet resources offering users “free” lottery tickets. They simulated prize draws, making every visitor a “winner”. Next, potential victims were asked to provide their personal information and bankcard data and to pay a “fee” or a “tax” to “receive” their prize.
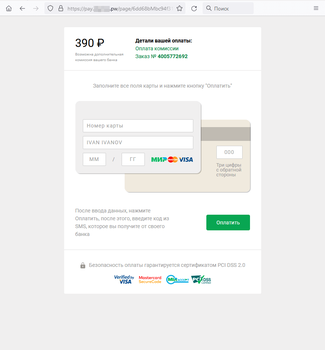
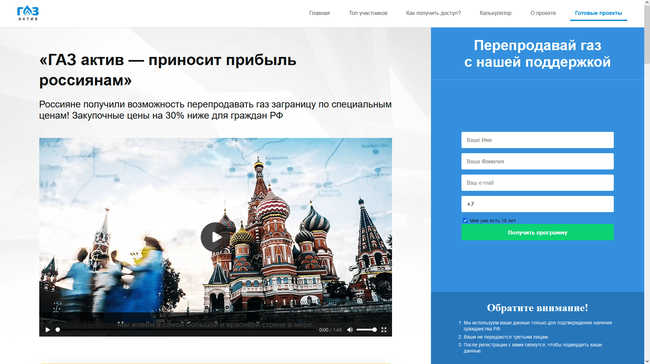
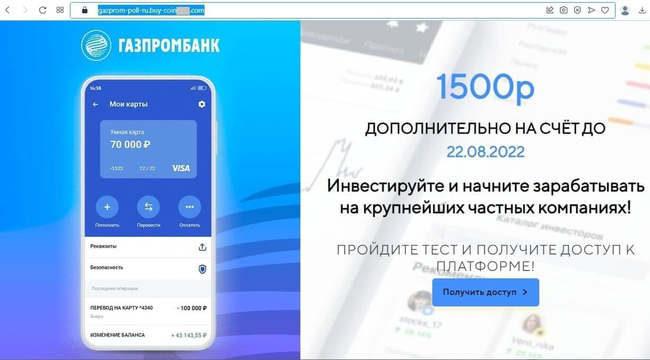
But most often, users came across bogus investment-themed sites. Such Internet resources were allegedly related to major Russian companies in the financial and oil and gas sectors and offered visitors the chance to make a profit by investing in shares, oil and gas projects, and other lucrative assets. To “begin earning money”, users had to take a poll or complete some basic test by answering several simple questions. Next, they were asked to register an account by providing their personal information. In reality, this information was sent to the fraudsters who could then lure potential victims into various bogus money-draining schemes. The next screenshots depict examples of such dangerous websites:
Mobile devices
According to Dr.Web for Android detection statistics, the most widespread Android malware of 2022 was Android.Spy.4498. Together with its other variants—Android.Spy.4837 and Android.Spy.5106, it was detected in over 41% of cases. Threat actors embed it in some unofficial modifications of WhatsApp messenger. This trojan is able to steal the contents of notifications and can offer users apps from unknown sources for installation and display various dialog boxes.
Among the most active were again adware trojans from the Android.HiddenAds family. They accounted for almost 27% of all detected malicious programs. Also active were adware trojans from the Android.MobiDash (4.81% of detections), Android.Locker ransomware trojans (1.50% of detections), and Android.FakeApp fraudulent apps (0.98% of detections). At the same time, users were less likely to encounter trojan applications designed to download and install other apps and apps capable of running arbitrary code.
Among the unwanted software, the most prominent once again was the Program.FakeAntiVirus.1 app. It acts like an anti-virus application and offers users the opportunity to purchase a license to cure non-existent threats. It accounted for over 65% of all unwanted apps detected. Highly active were various spying apps and also programs that present users with an opportunity to make money by completing different tasks. The latter, in reality, misled Android device owners and did not reward them with any real money.
Among riskware software, the leading positions detection-wise were again taken by Tool.SilentInstaller instruments, which were identified on protected devices in 66.83% of cases. These tools allow Android applications to run without having to install them. Cybercriminals can use them to launch the malware they distribute. Tools from the Tool.VirtualApk family, similar in functionality, were detected in 1.81% of cases. With that, tools from the Tool.Androlua family were noticeably more active. These allow apps written in the Lua scripting language to be run. They accounted for 4.81% of all riskware detections.
The most widespread adware of 2022 were Adware.Adpush (60.70% of adware detractions), Adware.SspSdk (5.47% of detections), and Adware.Airpush (5.35% of detections). Similar to most adware of their kind, they come in the form of specialized modules that can be integrated into Android apps and games.
Over the course of last year, Doctor Web’s malware analysts discovered over 280 different threats on Google Play, which were downloaded at least 45,000,000 times. Fraudulent apps from the Android.FakeApp family were most often observed. These were distributed under the guise of all different kinds of software. When launched, they connected to a remote server and, in accordance with the commands received, could display the contents of various websites (including fraudulent and phishing ones) instead of providing the functionality expected by users.
Other trojans that subscribed victims to paid services were discovered. Among them were members of the Android.Joker and Android.Subscription families. Moreover, our specialists discovered new password-stealing trojans from the Android.PWS.Facebook family that targeted Facebook social network users.
Adware trojans from the Android.HiddenAds family were again spread via the Google Play catalog. They were accompanied by multifunctional malicious apps from the Android.Triada family and some other threats. Among them, for instance, were the Android.Proxy.35 trojan, which turned infected devices into proxy servers; unwanted apps from the Program.FakeMoney family, which promised users they could make money by completing tasks, and the new adware apps—Adware.AdNoty and Adware.FireAd.
Prospects and possible trends
Last year demonstrated that cyber threats are constantly evolving, and that attackers are interested in both regular users and the corporate sector. As a result, next year we should expect the emergence of new malware and new APT attacks organized by malicious actors.
Adware-displaying trojans and banking malware generate income for cybercriminals; therefore, they will remain relevant threats. At the same time, the trend of increasingly more attacks being carried out on bank customers using the MaaS model (Malware as a Service) is likely to continue. Consequently, the number of unique banking malware families may gradually decrease over time, and several large suppliers will share this shadow market.
Fraud will remain a relevant problem in 2023. Malicious actors are very creative, and along with their old schemes, they will likely add new tricks to their arsenal. In addition, as usual they will exploit the current information agenda.
Attacks on mobile device owners will continue, and not only Android users will be at risk; Apple device owners may also face new threats. New attacks on other platforms should also be expected, first and foremost Linux and macOS.
[% END %]