Doctor Web’s overview of virus activity on mobile devices in 2020
January 19, 2020
In 2020, trojans allowing cybercriminals to generate illegal profit were among the most widespread Android malware. Malicious apps capable of downloading and executing arbitrary code, as well as trojans designed to download and install software without users’ knowledge and consent were among them. In addition, malware creators actively used various adware trojans and clicker trojans that loaded websites and clicked on web links.
Backdoors allowing attackers to remotely control infected devices and trojans turning Android gadgets into proxy servers for cybercriminals to redirect traffic also posed a serious threat.
Cyber espionage continues to remain relevant. In the last 12 months, Android device owners were targeted by numerous applications allowing the attackers to spy on them and control their actions. Many of these apps are not malicious alone, but do pose a potential threat since they can be used with or without users’ permission.
There were also new threats on Google Play which is the official app store and the source for other digital content for the Android OS. Google Play is considered to be the most reliable place to download software and games, but attackers are still able to spread malware and unwanted apps there. Numerous adware trojans, bogus apps, and malware that subscribed users to premium services and were capable of executing arbitrary code, were among the threats Doctor Web’s specialists uncovered on the platform. Moreover, banking trojans and applications with built-in unwanted adware modules were also spread through Google Play.
In 2020, malicious actors actively exploited the COVID-19 pandemic to spread malware. Amid worldwide troubles, banking trojans, ransomware, spyware trojans, fraudulent software and other threats were seen targeting Android users.
PRINCIPAL TRENDS IN 2020
- New threats on Google Play
- Various packers and utilities used to protect malware and unwanted apps
- New trojans utilizing different techniques to conceal malicious functionality
- Adware trojans and malicious downloaders prevail among threats detected on Android devices
Most notable events
In March, Doctor Web’s malware analysts uncovered the trojan dubbed Android.Circle.1. It was spread through Google Play as image collection apps, astrology programs, games, utilities and other useful software for Android devices. Once installed, it received and executed commands from cybercriminals using BeanShell scripts. For instance, Android.Circle.1 could display ads and load websites while imitating user actions by automatically clicking on links and banners.
Throughout the year our malware analysts discovered other trojans from the same family as Android.Circle.1.
In May, Doctor Web’s specialists traced the spread of the new modification of the Android.FakeApp.176 scam trojan, which has been known for several years now. To attract users, malicious actors passed it off as well-known games and apps. Cybercriminals promoted yet another incarnation of this trojan as a mobile version of the Valorant game and advertised it on YouTube.
Android.FakeApp.176’s only function is to load affiliate services websites where users are prompted to complete specific tasks such as installing apps and games or completing surveys. For each successfully completed task the affiliate service member receives a reward. In case of the new modification of the Android.FakeApp.176, the scam was based on false claims that upon finishing a few tasks, the user would supposedly gain access to the game, which didn’t actually exist. As a result, victims didn’t receive the reward and only helped malware writers generate profit.
Already in December, Doctor Web reported on the Android.Mixi.44.origin trojan found in the Eye Care application. It covertly opened web links and loaded websites, which then displayed on-top of other app’s windows. In addition, this malware monitored which apps users installed and attempted to credit every installation to the cybercriminals so they received rewards from advertising and affiliate services.
Over the past 12 months, Doctor Web’s specialists found numerous threats on the Google Play app store. Adware trojans from the Android.HiddenAds family displaying obnoxious banners on-top of other apps’ windows, Android.Joker multifunctional trojans subscribing users to premium services and executing arbitrary code, as well as other malicious and unwanted applications were among them.
Using the pandemic to their benefit, cybercriminals actively spread various Android malware as legitimate and useful software.
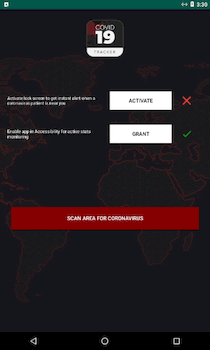
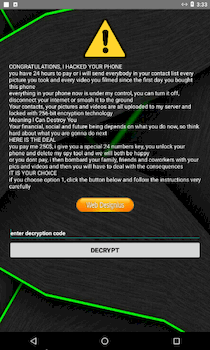
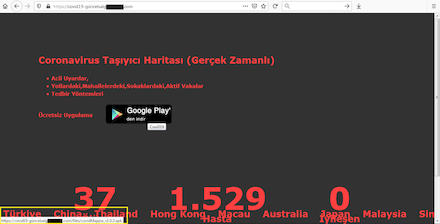
In March, for example, users were attacked by the Android.Locker.7145 ransomware trojan. Its creators spread it as an app that allegedly allowed users to track coronavirus infection statistics. Instead, it encrypted files stored on Android devices and demanded users pay a ransom of $250 US dollars.
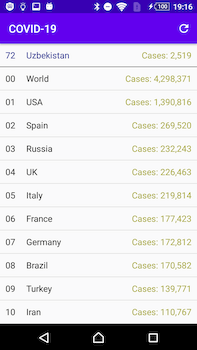
In May, the Android.Spy.660.origin spyware trojan was spotted, targeting primarily Uzbek users. Unlike Android.Locker.7145, it was built into the app that actually provided the information on the number of infected people. With this function, however, Android.Spy.660.origin was also collecting users’ SMS, call history, and contacts list and sending them to the remote server.
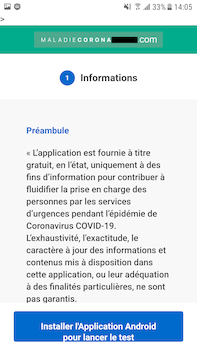
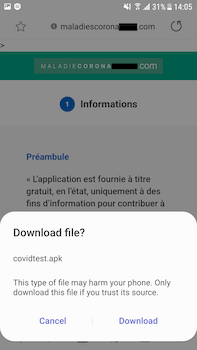
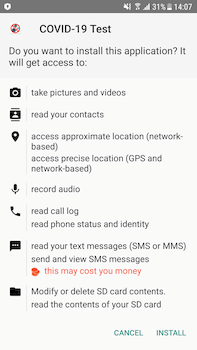
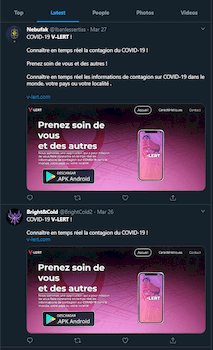
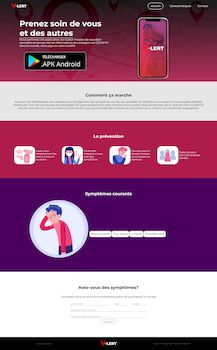
Another COVID-19-related spyware trojan, dubbed Android.Spy.772.origin, attacked French users. It was distributed through a fraudulent website that mimicked a French online information platform related to the coronavirus. Android.Spy.772.origin was downloaded from the fake website and disguised as an app designed to check symptoms and identify possible infection.
Upon launching, however, the trojan only loaded the original website in its window and proceeded to spy on the victim. It sent various confidential information to cybercriminals, including SMS, location data, phone call logs and contacts. It could also record the surrounding environment using the device’s microphone, take pictures and record videos using the camera.
Many banking trojans were among the malware spread amid the pandemic. Android.BankBot.2550, which is yet another modification of the infamous Anubis trojan, was one of them. Our specialists recorded cases when malware writers used social networks, such as Twitter, to distribute it. Cybercriminals lured potential victims to their websites and prompted them to install an app that promised to provide updates and information on the coronavirus. In reality, users downloaded a malware program designed to syphon their money and personal information.
Android.BankBot.2550 displayed phishing windows to steal logins, passwords and banking card information. It also intercepted SMS, could take screenshots, automatically turn off the Google Play Protect built into the Android OS, operate as a keylogger and perform other malicious actions.p>
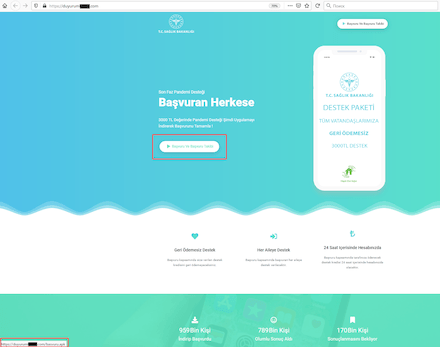
Furthermore, some banking trojans were spreading under the guise of apps that could allegedly help users receive financial support from the government. Amid the pandemic and difficult financial situation related to it many countries did, in fact, allocate the money to support their citizens – and cybercriminals took advantage of this. For example, the Android.BankBot.684.origin and Android.BankBot.687.origin banking trojans targeting users from Turkey were spread as software that was supposedly designed to help users receive financial support. These trojans also found their way onto users’ Android devices through the malicious websites.
These bankers attempted to steal users’ logins and passwords to access their mobile banking accounts. To do so, the bankers displayed phishing windows on-top of legitimate banking software UI. Moreover, they were able to steal banking card information, intercept and send SMS, execute USSD commands, block the screen of the infected device and perform other malicious actions upon attackers’ commands.
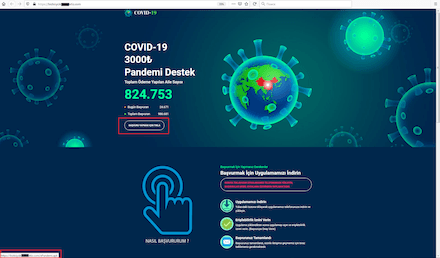
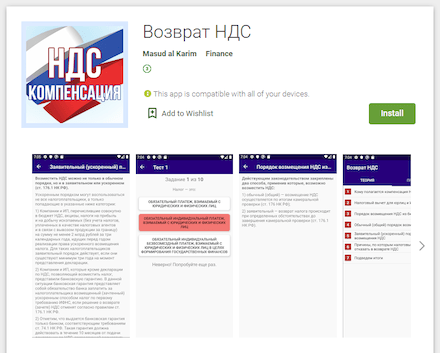
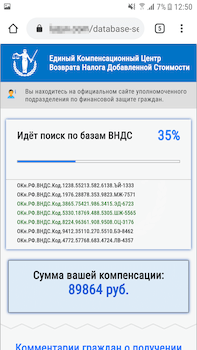
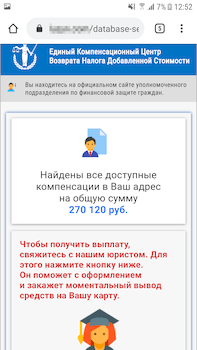
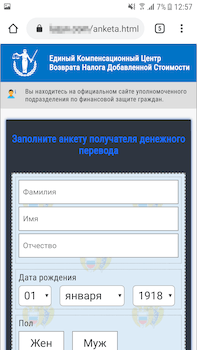
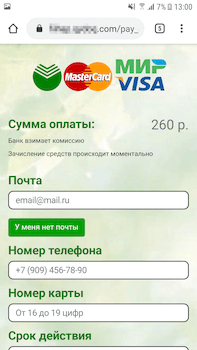
During the pandemic, the topics of welfare allowances, payouts and compensation was also regularly exploited. In particular, scammers were actively spreading various modifications of the Android.FakeApp family malware. Throughout 2020, Doctor Web’s specialists uncovered many of these trojans on Google Play. Cybercriminals spread them as reference software and handbooks with information about welfare payouts and tax refunds. Many of these trojans were targeting users from Russia where the government was also financially supporting its citizens. When victims tried to find information about available payouts, they ended up installing trojans.
This type of malware loaded fraudulent websites where users were asked to provide their personal information, allegedly to verify whether any payout or compensation was available. After that, websites imitated the database search and users were asked to provide their banking card information to pay a commission for the money “transfer” or to pay a fee for the documents “registration”. But in reality, victims didn’t receive any payout or compensations. They were just giving away their own money and providing cybercriminals with their confidential information.
Statistics
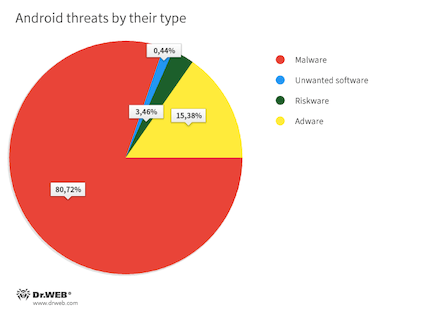
According to statistics collected by Dr.Web for Android anti-virus products, malicious applications were most often detected on Android devices. They accounted for 80.72% of the total number of identified threats. Adware with a 15.38% detection share was the second most common threat. Riskware ranked third as it was detected in 3.46% of cases. Potentially unwanted applications accounted for a mere 0,44% of all detections.
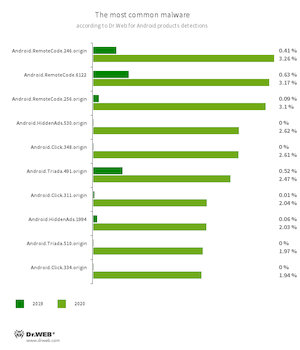
Trojans capable of downloading and executing arbitrary code, as well as downloading and installing other software, were among the most common malicious programs. They accounted for over 50% of the malware detected on Android devices. With that, various modifications of the Android.RemoteCode, Android.Triada, Android.DownLoader, and Android.Xiny trojan families prevailed.
Adware trojans were among the most active threats as well. They accounted for almost a quarter of all malicious apps identified on protected devices. Numerous modifications of the Android.HiddenAds and Android.MobiDash trojans were among them.
- Android.RemoteCode.246.origin
- Android.RemoteCode.6122
- Android.RemoteCode.256.origin
- Malicious applications that download and execute arbitrary code. Depending on their modification, they can load various websites, open web links, click on advertisement banners, subscribe users to premium services and perform other actions.
- Android.HiddenAds.530.origin
- Android.HiddenAds.1994
- Trojans designed to display obnoxious ads and distributed as popular applications. In some cases, they can be installed in the system directory by other malware.
- Android.Triada.491.origin
- Android.Triada.510.origin
- Multifunctional trojans that perform various malicious actions. This malware belongs to the trojan family that infects other apps’ processes. Some modifications of this family were found in the firmware of Android devices that attackers implanted during manufacturing. Some of them can also exploit various vulnerabilities to gain access to protected system files and folders.
- Android.Click.311.origin
- Android.Click.334.origin
- Android.Click.348.origin
- Trojans that automatically load websites and click on links and banners. They can be spread as harmless apps so users don’t perceive them as threatening.
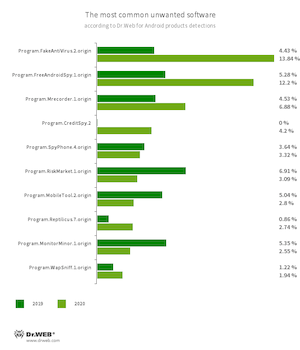
Applications that alerted Android users to nonexistent or fake threats and prompted them to buy the full version of software to “cure” their devices were some of the most common unwanted apps. Various spyware apps were also detected quite often.
- Program.FakeAntiVirus.2.origin
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them and demand they purchase full version software.
- Program.FreeAndroidSpy.1.origin
- Program.Mrecorder.1.origin
- Program.SpyPhone.4.origin
- Program.MobileTool.2.origin
- Program.Reptilicus.7.origin
- Program.MonitorMinor.1.origin
- Software that monitors Android user activity and may serve as a tool for cyber espionage. These apps can track device locations, collect information from SMS and social media messages, copy documents, photo and video, spy on phone calls, etc.
- Program.RiskMarket.1.origin
- An app store that contains trojan software and recommends users install it.
- Program.WapSniff.1.origin
- An Android program designed to intercept messages from WhatsApp.
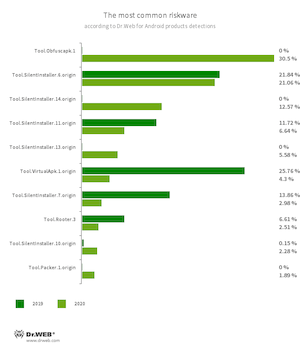
Programs capable of downloading and running other apps without installing them were among the most common riskware. Dr.Web for Android anti-virus products also detected a large number of apps protected by special packers and obfuscators on Android devices. Cybercriminals often use these tools to protect malware and unwanted software from anti-viruses.
- Tool.Obfuscapk.1
- The detection name for applications protected by the Obfuscapk obfuscation tool. This tool is used to automatically modify and scramble Android apps’ source code to make reverse engineering more difficult. Cybercriminals use the tool to protect malicious applications from being detected by anti-virus programs.
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.11.origin
- Tool.SilentInstaller.13.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.10.origin
- Tool.VirtualApk.1.origin
- Riskware platforms that allow applications to launch APK files without installation. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Rooter.3
- A utility designed to obtain root privileges on Android devices. Ordinary users, cybercriminals and malware may all use it.
- Tool.Packer.1.origin
- A packer tool designed to protect Android applications from unauthorised modification and reverse engineering. This tool is not malicious itself, but it can be used to protect both harmless and malicious software.
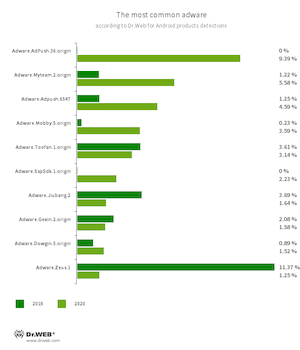
The most widespread adware were advertising modules displaying ads in the notification panel of Android devices. They also displayed obnoxious banners atop other apps’ windows and the operating system UI.
- Adware.AdPush.36.origin
- Adware.AdPush.6547
- Adware.MyTeam.2.origin
- Adware.Mobby.5.origin
- Adware.Toofan.1.origin
- Adware.SspSdk.1.origin
- Adware.Jiubang.2
- Adware.Gexin.2.origin
- Adware.Dowgin.5.origin
- Adware.Zeus.1
- Program modules incorporated into Android applications and designed to display obnoxious ads on Android devices. Depending on their family and modifications, they can display full screen ads and block other apps’ windows, show various notifications, create shortcuts and load websites.
Banking trojans
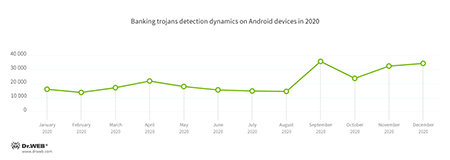
In 2020, the intensity of attacks using banking trojans remained approximately the same throughout the first three quarters. A noticeable increase in their activity was observed only in spring, which coincided with the beginning of the pandemic.
With the onset of autumn and the second wave of the coronavirus outbreak, the number of banking trojan detections significantly rose and remained at high levels until the end of the year. With that, the peak of their activity fell on September. The reason for this was that in August, the Cerberus banking trojan source code was leaked to the public, making it possible for other malware creators to build their own bankers based on the code. Dr.Web anti-virus products detect various samples of Cerberus as modifications of the Android.BankBot family.
Banking malware found its way onto the Android devices using various means, including downloads from malicious websites. Apart from the bogus coronavirus-related sites mentioned earlier, cybercriminals created many other fake online resources. For instance, Android.Banker.388.origin, which was spread among Vietnamese users in May, was downloaded from the fake Ministry of Public Security website.
Cybercriminals that attacked Japanese users were creating fictitious post office and delivery services websites from which various Android banking trojans were downloaded onto victims’ devices.
The Google Play app catalogue was another common spreading route. In June, for example, Doctor Web’s virus analysts discovered several banking trojans there. One them was Android.BankBot.3260, which was disguised as a note-taking app. Another one was Android.BankBot.733.origin which was spread as a tool to install software and system updates, as well as to protect against cyber threats.
In June, the Android.Banker.3259 trojan was found. It hid in the application allegedly designed to manage phone calls and SMS.
Prospects and trends
Cybercriminals are continuously searching for innovative ways to protect their malware. In 2021, we can expect the emergence of more multifunctional threats and trojans protected with various packers designed to interfere with anti-virus software detection capabilities.
Malware creators will continue using malicious software to generate illicit profits. In turn, users will likely face new adware trojans, software downloaders and clickers created and used for various criminal profiteering schemes.
Cyber espionage and targeted attacks will also remain a threat. Finally, it is highly likely that malware designed to infect Android devices by exploiting system or network vulnerabilities will emerge. To protect your Android device from malware, unwanted programs and other threats, we recommend installing Dr.Web for Android. It is also necessary to install all the available system updates and latest versions of the software you use.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products