Fraudsters spread a mobile trojan disguised as a Valorant game
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
May 28, 2020
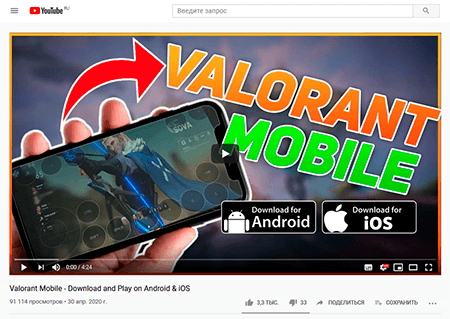
The Valorant game is still under development and available only as a beta testing version on computers running Windows. However, fraudulent videos are created so that the gaming process on mobile devices seems plausible.
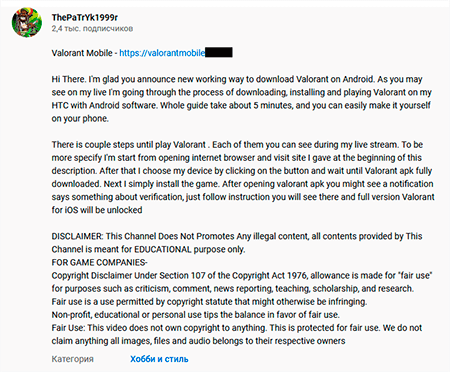
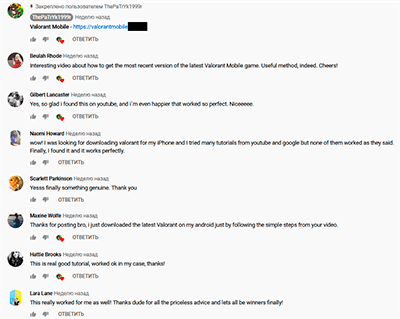
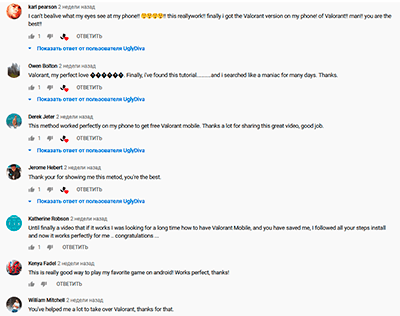
To make it appear more believable, these videos are accompanied by a detailed description and numerous comments from other users who seemingly successfully installed the game on their mobile devices. All these comments are fake.
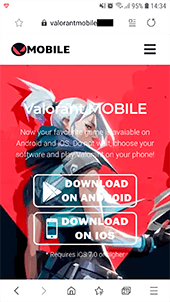
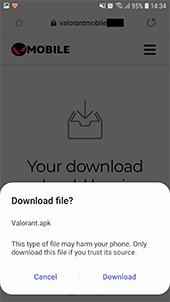
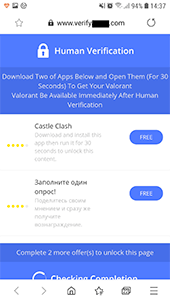
To download the game, users are prompted to visit a website designed to look like the official Valorant project website. It contains two links that apparently lead to the game download. If a visitor tries to use the link from the iOS device, the website will redirect the request to the affiliate program web portal. If the request is performed from an Android device, the APK file with Android.FakeApp.176 will be downloaded instead. Since this file is received from a third-party source rather than the official Google Play store, on most modern devices a necessary system security settings change must be applied to install it.
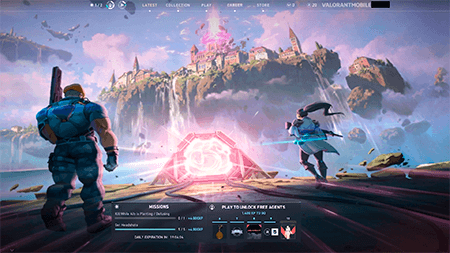
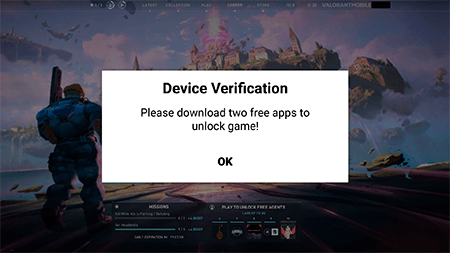
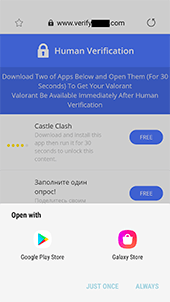
This malware imitates the game’s launch process but then offers a device validation to “unlock” it. To do so, the user is asked to download and install two additional apps.
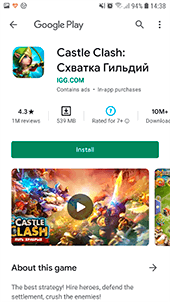
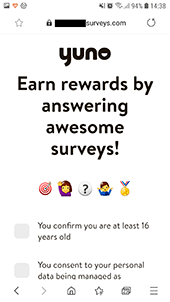
If the user agrees to “unlock” the game, a trojan loads the same affiliate service website, as with the iOS devices, in the browser. This website checks various parameters and redirects the user to another affiliate program website. There, the visitor is proposed to complete the tasks in order to receive a reward. In this example the user is required to install and launch a game from Google Play, as well as to participate in an online survey.
Such websites represent typical services that help clients earn money through affiliate clicks, artificial increases in the number of website visitors, monetization through the software advertizing and pay-per-install schemes in order to increase software popularity and number of installations, as well as monetizing online surveys and other online marketing campaigns on the Internet.
In fact, some of these services provide real rewards to users. For example, they can receive an in-game currency or other game bonuses upon completing the task. However, in the case of the Android.FakeApp.176 trojan, users receive no reward at all. The mobile version of the Valorant game does not currently exist, and the only purpose of this fake app is to load the affiliate website to help malware developers receive rewards by taking advantage of their victims.
This type of illegal profiting through use of malicious apps spread as legitimate games isn’t new. For example, the same version of the Android.FakeApp.176 trojan was spread under the guise of the mobile version of the recent Call of Duty: Warzone game, which is only available on consoles and PC. Moreover, back in 2018 fraudsters were spreading one of the modifications of this trojan, disguised as the Fortnite game, and as the Apex Legends game back in a 2019. Both games quickly gained popularity among players, which malware creators quickly turned to their own advantage. The new title announced less than two months ago has already gained millions of fans and scammers promptly stepped in once again.
Doctor Web recommends users take the information from the Internet with a grain of salt and not open suspicious links or install dubious applications from unknown sources.
Dr. Web for Android Anti-Virus solutions reliably detects and deletes all known modifications of the Android.FakeApp.176 from Android devices, keeping our users well protected from this threat.
More details about Android.FakeApp.176

Ваш Android нуждается в защите.
Используйте Dr.Web
- Первый российский антивирус для Android
- Более 140 миллионов скачиваний только с Google Play
- Бесплатный для пользователей домашних продуктов Dr.Web