December 2015 virus activity review from Doctor Web
December 24, 2015
As usual, the first winter month turns out to be rather uneventful in terms of information security, since it is quite rare that virus makers are extremely active on the threshold of New Year and Christmas. This December is not an exception. At the beginning of the month, security researchers detected an installer of unwanted applications for OS X and a Trojan for Linux designed to download and install various programs. Also they have registered a spread of a dangerous banking Trojan for Google Android, which was detected at the beginning of the year and has already compromised more than 31,000 mobile devices.
PRINCIPAL TRENDS IN DECEMBER
- Distribution of new Trojan for Linux
- New installer of unwanted applications that targets OS X
- Distribution of new dangerous banking Trojan for Android
Threat of the month
Virus makers become more and more interested in targeting OS X. It is proved by an increase in new malware for this operating system. The majority of threats for Apple computers are designed to deliver advertisements and install unwanted applications. A suchlike malicious program, Adware.Mac.Tuguu.1, was detected by Doctor Web security researchers. This Trojan can covertly install various additional programs (usually useless, but sometimes even malicious) to user’s Mac computer.
Adware.Mac.Tuguu.1 is distributed under the guise of free programs for OS X. Once launched, this dangerous application reads the content of the ".payload” configuration file located in the same folder as the setup file of the application. Then it detects the address of the command and control server (C&C server), modifies it and refers to the server for the list of additional programs that the user will be prompted to install. All information transmitted between the server and the Trojan is encrypted. Judging from inner numeration used by the installer, there are 736 programs that can be installed on a Mac. Before the installation, Adware.Mac.Tuguu.1 checks if the offered programs are compatible with each other. For example, it will not install the MacKeeper application along with the MacKeeper Grouped application. What is more, Adware.Mac.Tuguu.1 tries to make sure that such software was not installed earlier. Then, before the end of its operation, it checks that the installation was completed successfully. For more information about this Trojan, refer to the review published by Doctor Web.
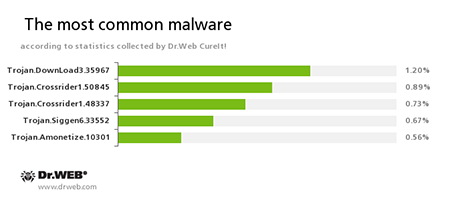
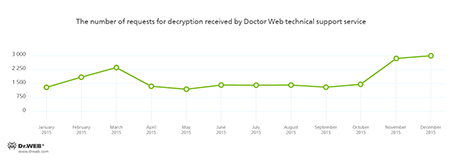
According to statistics collected by Dr.Web CureIt!
Trojan.DownLoad3.35967
A Trojan that can download other malicious programs from the Internet and install them on the infected computer.Trojan.Crossrider1.42770, Trojan.Crossrider1.50845
Trojans designed to display various advertisements.Trojan.Siggen6.33552
A malicious program designed to install other dangerous software on the infected computer.Trojan.Amonetize.10301
A malicious program designed to install other unwanted applications on the computer.
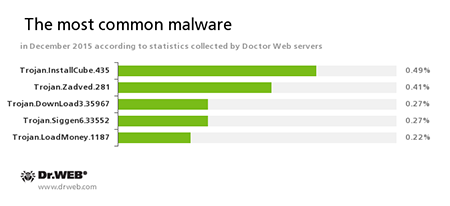
According to Doctor Web statistics servers
Trojan.InstallCube
A family of downloader programs designed to install unwanted and useless applications on the user’s computer.Trojan.Zadved
This Trojan displays fake search results in the browser window and imitates pop-up messages from social networking sites. In addition to this, the malware can replace advertisements displayed on different Internet resources.Trojan.DownLoad3.35967
A Trojan that can download other malicious programs from the Internet and install them on the infected computer.Trojan.Siggen6.33552
A malicious program designed to install other dangerous software on the infected computer.Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer.
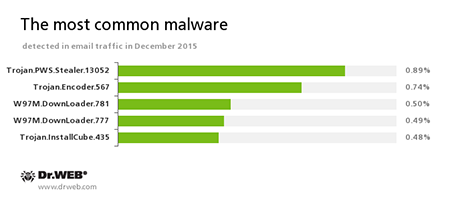
Statistics concerning malicious programs discovered in email traffic
Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on the infected computer.Trojan.Encoder.567
A malicious program belonging to the family of encryption ransomware Trojans that encrypt files and demand a ransom for decryption of compromised data. This program can encrypt important user files, for example, of the following types: .jpg, .jpeg, .doc, .docx, .xls, xlsx, .dbf, .1cd, .psd, .dwg, .xml, .zip, .rar, .db3, .pdf, .rtf, .7z, .kwm, .arj, .xlsm, .key, .cer, .accdb, .odt, .ppt, .mdb, .dt, .gsf, .ppsx, .pptx.W97M.DownLoader
A family of downloader Trojans that exploit vulnerabilities of office applications and can download other malicious programs to the compromised computer.Trojan.InstallCube
A family of downloader programs designed to install unwanted and useless applications on the user’s computer.
Botnets
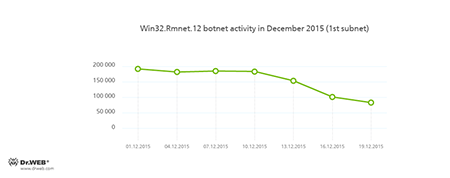
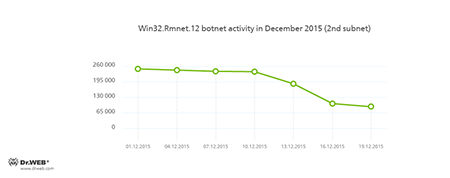
Doctor Web security researchers continue to monitor the botnet created by criminals using a dangerous Win32.Rmnet.12 file infector. By the end of the month, a decrease in the both subnets` activity was registered, which is shown in the following graphs:
Rmnet is a family of viruses spread without any user intervention. They can embed content into loaded webpages (this theoretically allows cybercriminals to get access to the victim's bank account information), steal cookies and passwords stored by popular FTP clients, and execute other commands issued by cybercriminals.
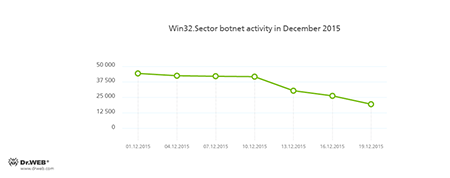
The botnet consisting of computers infected with the Win32.Sector file virus is still active. This malicious program can perform the following actions:
- Download various executable files via P2P networks and run them on infected machines.
- Inject its code into running processes.
- Prevent some anti-viruses from operating and block access to the websites of their respective developers.
- Infect files on local disks, removable media (where the malware creates the autorun.inf file during the infection process), and in shared folders.
Its average daily activity can be seen in the following picture:
Encryption ransomware
The most common ransomware programs in December 2015
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows
| Data Loss Prevention | |
|---|---|
 |  |
Linux
The number of malware for Linux keeps growing. Thus, in December 2015, Doctor Web security researchers detected Linux.Rekoobe.1 Trojan that is able to download files from the C&C server and upload them to it upon a command from cybercriminals. The Trojan can also interact with the Linux command interpreter on the compromised device. It should be noted that the first modifications of Linux.Rekoobe.1 were intended to infect Linux devices with the SPARC architecture. However, virus makers have apparently decided to modify the Trojan in order to make it compatible with Intel-based computers. Doctor Web specialists registered the samples of Linux.Rekoobe.1 for 32-bit, as well as for 64-bit Intel-compatible Linux system.
Under specific circumstances, the Trojan establishes the connection to the server via a proxy server. Moreover, to verify encrypted data from the C&C server, Linux.Rekoobe.1 applies a rather complicated procedure. Nevertheless, Linux.Rekoobe.1 can execute only three commands such as: to download or upload files, to send the received commands to the Linux interpreter, and to transmit the output to the remote server—thus, cybercriminals are able to interact with the compromised devise remotely.
For more information regarding this Trojan, refer to the news article published by Doctor Web.
Dangerous websites
During December 2015, 210,987 URLs of non-recommended websites were added to Dr.Web database.
| November 2015 | December 2015 | Dynamics |
|---|---|---|
| +670,545 | +210,987 | -68.53% |
Malicious and unwanted programs for mobile devices
In December, cybercriminals were showing interest in mobile devices—thus, the last month of the year was rather stressful for their owners. Virus makers continued to distribute various banking Trojans that could steal money from users’ bank accounts. Moreover, security researchers have detected a big number of new SMS Trojans. This month, yet another malware program designed to compromise iOS mobile devices was detected.
Among the most noticeable December events related to mobile malware we can mention
- Distribution of dangerous banking Trojans
- Emergence of new SMS Trojans
- Detection of a new Trojan for iOS
Find out more about malicious and unwanted programs for mobile devices in our special overview.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live
[% END %]