January 2015 virus activity review from Doctor Web
April 2, 2015
PRINCIPAL TRENDS IN MARCH
- Mass spam mailings spreading encryption ransomware.
- New malicious programs for Android.
Threat of the month
In March 2015, Doctor Web security researchers completed their examination of the multi-purpose spying program BackDoor.Yebot. Another malicious program, dubbed Trojan.Siggen6.31836 by Dr.Web, facilitates the backdoor's distribution. BackDoor.Yebot' possesses the ability to:
- run an FTP server on an infected computer;
- run a SOCKS 5 proxy server on an infected computer;
- modify the RDP protocol to provide remote access to the infected computer;
- log keystrokes on an infected PC (key logging);
- set feedback with an infected PC for FTP, RDP and Socks5 if the network uses NAT (back connect);
- intercept data according to PCRE patterns (Perl Compatible Regular Expressions)—a library that implements regular expressions in Perl, for which the Trojan intercepts all possible features associated with web surfing;
- intercept SCard tokens;
- inject arbitrary content into web pages loaded in browser windows (web injections);
- intercept various system functions, depending on the accepted configuration file;
- modify the code of the running process, depending on the accepted configuration file;
- interact with the various functional modules (plug-ins);
- take screenshots;
- search the infected system for private keys.
For more information about this malware, and its distribution and operation, please refer to the review published on Doctor Web's site.
Encryption ransomware
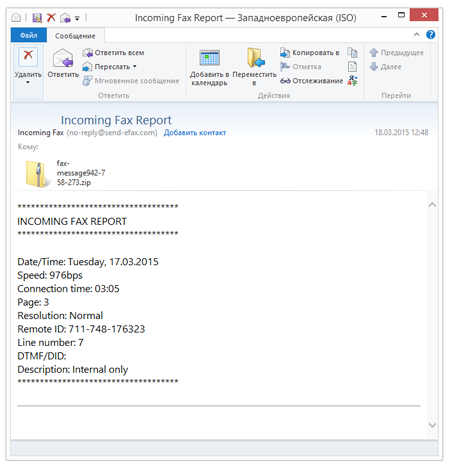
March also witnessed the intensified activity of criminals who spread encryption ransomware with spam. For example, virus makers carried out mass mailings of new incoming fax messages bearing the headline "Incoming Fax Report". Disguised as a fax message, the attached ZIP archive contains a malicious SCR file detected by Dr.Web as Trojan.DownLoader11.32458.
If an attempt is made to open the attachment, the malicious program Trojan.DownLoader11.32458 extracts and launches the encryption ransomware Trojan.Encoder.514 on the target machine. The ransomware then encrypts data stored on the disk and demands a ransom for its recovery. More information about this incident can be found in a review published by Doctor Web.
The most common ransomware programs in March 2015:
| February 2015 | March 2015 | Growth |
|---|---|---|
| 1,840 | 2,361 | + 28.31% |
The most common ransomware programs in March 2015:
- Trojan.Encoder.761;
- Trojan.Encoder.858;
- BAT.Encoder;
- Trojan.Encoder.741;
- Trojan.Encoder.567.
Dr.Web Security Space 10.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows
| Preventive protection | Data Loss Prevention |
|---|---|
 |  |
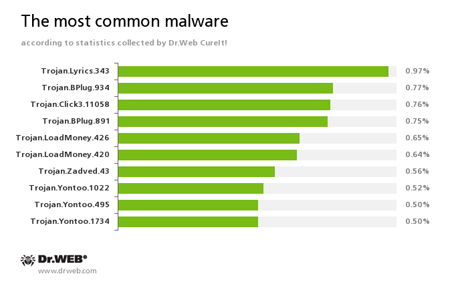
According to statistics gathered by Dr.Web CureIt!
Trojan.Lyrics
A family of Trojans that display annoying ads and open objectionable web pages without user consent.
Trojan.BPlug
These plugins for popular browsers display annoying ads to users as they browse web pages.
Trojan.Click
Malicious programs designed to generate traffic for various sites by redirecting users to the corresponding web pages.
Trojan.LoadMoney
Downloader programs generated by servers belonging to the LoadMoney referral programme. These programs download and install various unwanted software programs on a victim's computer.
Trojan.Zadved
Browser plugins that display fake search results and pop-up messages from social networking sites. Furthermore, their payload enables them to replace advertisements on various sites.
Trojan.Yontoo
Plugins for popular browsers that demonstrate ads to users as they browse web pages.
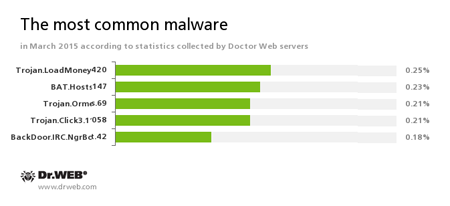
According to Doctor Web's statistics servers
Trojan.LoadMoney
Downloader programs generated by servers belonging to the LoadMoney referral programme. These programs download and install various unwanted software programs on a victim's computer.
BAT.Hosts.147
This malicious script modifies the file hosts located in the Windows system folder and containing DNS server IP addresses. As a result of its activity, when a user tries to go to one of the sites specified in the file, the browser is automatically redirected to a specially crafted malicious web page.
Trojan.Ormes.69
An advertising Trojan that displays annoying ads in the browser.
Trojan.Click
Malicious programs designed to generate traffic for various sites by redirecting users to the corresponding web pages.
BackDoor.IRC.NgrBot.42
A fairly common Trojan which is known to the information security researchers since 2011. Malicious programs of this family are able to execute intruder-issued commands on infected machines, and cybercriminals use the IRC (Internet Relay Chat) text-messaging protocol to control those PCs.
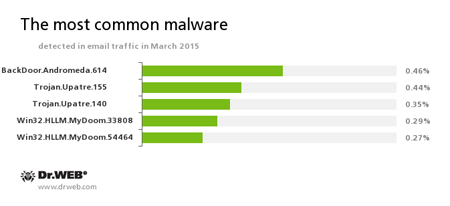
Statistics concerning malicious programs discovered in email traffic
BackDoor.Andromeda
The downloader Trojans are designed to download other malware from remote servers of the cybercriminals and run this malware on infected machines.
Trojan.Upatre
A family of Trojans that covertly downloads and installs other malicious applications on the infected computer.
Win32.HLLM.MyDoom
A long-known and common family of worms that spread via email without user participation. Emails containing copies of the worm are sent to addresses found on the infected computer.
Botnets
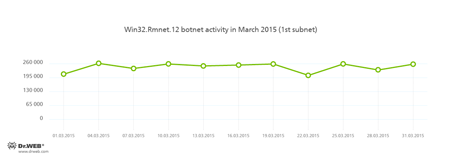
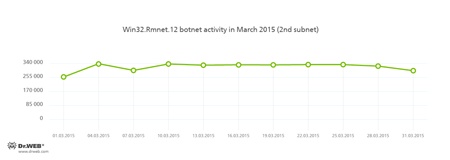
Doctor Web's security researchers continue to monitor the botnet created by criminals using the file infector Win32.Rmnet.12. The average daily activity of the botnet's two subnets is shown in the following graphs:
Rmnet is a family of viruses spread without any user intervention. They can embed content into loaded webpages (this theoretically allows cybercriminals to get access to the victim's bank account information) as well as steal cookies and passwords stored by popular FTP clients and execute other commands issued by cybercriminals.
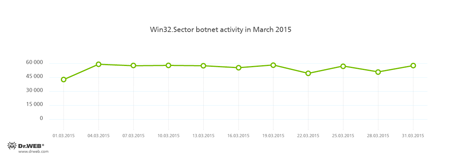
Also operational was the botnet consisting of machines compromised by the file infector Win32.Sector. This malicious program performs the following tasks in an infected system:
- Download various executable files via a P2P network and launch them on the infected machines.
- Inject their code into running processes.
- Can prevent some anti-viruses from operating and block access to the sites of their respective developers.
- Infect files on local disks, removable media (where it creates the file autorun.inf during the infection process), and in shared folders.
The average daily activity of this botnet in March 2015 is illustrated in the graph below:
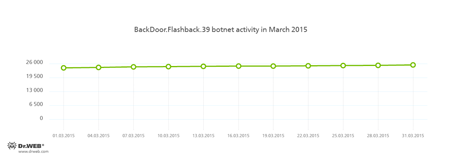
Meanwhile, Doctor Web security researchers continue to monitor the BackDoor.Flashback.39 botnet:
BackDoor.Flashback.39
The Trojan for Mac OS X which was distributed on a wide scale in April 2012. The infection was carried out via Java vulnerabilities. The purpose of this Trojan is to download and run a payload on the infected machine; the payload can be any executable file specified in the directive the Trojan receives from the hacker who controls it.
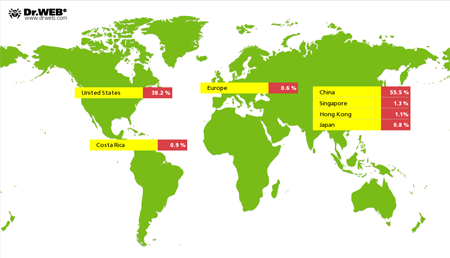
The malicious program Linux.BackDoor.Gates.5 continued to carry out DDoS attacks on various websites. In March 2015 Doctor Web security researchers registered 2,236 IP addresses on which attacks were mounted—nearly twice as many compared with the previous month. As before, most targets of the attacks were located in China; the United States ranked second:
Fraudulent and non-recommended sites
Parental Control, which is available in Dr.Web Security Space 10.0, can provide protection from various Internet scams. The Parental Control component lets you limit access to websites related to a certain topic and filter suspicious content. In addition, using its database of non-recommended URLs, the component can shield users from fraudulent sites, potentially dangerous and shocking content, and from sites known to distribute malware.
During March 2015, Doctor Web added 74,108 URLs into the Dr.Web database of non-recommended sites.
| February 2015 | March 2015 | Movement |
|---|---|---|
| 22,033 | 74,108 | + 236.35% |
Malicious and unwanted software for Android
March proved to be a turbulent month for Android devices: Criminals were relentless in their attacks, employing both known and new malicious programs. The most common Trojans for Android in March:
- SMS Trojans
- Ransomware
- Banking Trojans
For more information about malicious programs for Android, please refer to our corresponding review.
Find out more with Dr.Web
Virus statistics Virus encyclopedia All virus reviews Laboratory-live
[% END %]