March 2015 Android malware overview
April 2, 2015
PRINCIPAL TRENDS IN MARCH
- SMS Trojans
- Backdoors
- Growing number of encryption ransomware programs
- New malicious programs that generate illicit profits
The number of entries for malicious and unwanted software in the Dr.Web for Android virus database
| February 2015 | March 2015 | Movement |
|---|---|---|
| 6,665 | 7,103 | +6.57% |
Mobile threat of the month
In the past month Doctor Web security researchers discovered the dangerous multi-purpose program Android.Titan.1 which covertly sends SMS, makes calls, and collects all sorts of confidential information. This threat’s distribution and features:
- Criminals spread the malware via file hosting services by dispatching short messages containing a link to download the program.
- When launched on a handheld, it will delete its icon to conceal itself from the user.
- It can covertly make calls even when the infected device is in standby mode and its screen is turned off. The screen remains inactive throughout the malware-initiated call, so that the user remains unaware of the unwanted activity occurring on their device.
- The program's payload is incorporated into a library file, so some anti-viruses may fail to detect the Trojan.
However, the malware is detected and neutralised by Dr.Web anti-viruses for Android. More information about this malware can be found in the corresponding publication on Doctor Web's site.
SMS Trojans
SMS Trojans remain among the most active malicious programs for Android. Android.Bodkel programs were the ones most commonly detected in March. Some of these programs were spread in Russia via a social networking site where criminals started communities for those using illegal copies of commercial software for Android. The criminals also lured potential victims to a number of dubious sites with free offers to download such programs.
Once one of these malicious programs was installed on a device, it would covertly send premium short messages, bypass CAPTCHA verification to subscribe the user to chargeable services, and perform a wide range of other malicious tasks on command. Some of the Android.Bodkel Trojans used in this attack:
The number of entries for SMS Trojans for Android.Bodkel in the Dr.Web virus database:
| February 2015 | March 2015 | Growth |
|---|---|---|
| 154 | 169 | +9,74% |
Also last month, virus writers continued to design and distribute Android.SmsSend programs. Android.SmsSend virus definitions in the Dr.Web virus database:
| February 2015 | March 2015 | Movement |
|---|---|---|
| 3,264 | 3,529 | +8,12% |
Banking Trojans
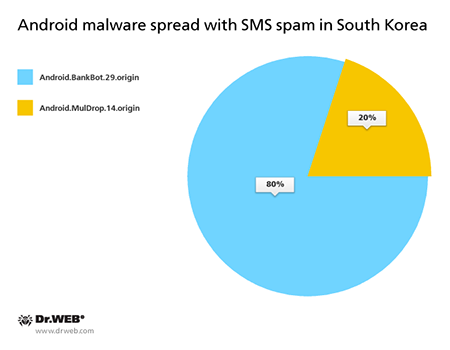
The past month also saw incidents involving criminals spreading various banking Trojans for Android. In particular, such malicious applications were once again engaged in attacks in South Korea where criminals reprised their technique of using SMS spam messages containing a link to get users to download the malware, but the number of such spam campaigns in March decreased significantly compared with previous months and included fewer than 20 incidents. Virus makers used the following malicious program in their attacks on customers of banks in South Korea:
Android.BankBot.29.origin
The banking Trojan steals the authentication information used by the clients of some South Korean financial organisations. Once a popular online banking application is launched, the malware replaces its interface with a fake one that prompts the user to enter all the confidential information necessary to control their bank account. The divulged data is forwarded to criminals. Under the pretext of subscribing the user to a banking service, it attempts to install the malicious program Android.Banker.32.origin.
Android.MulDrop.14.origin
This Trojan is designed to distribute and install other malware, including various banking Trojans, onto Android handhelds. It is being spread primarily in South Korea.
Ransomware
March also experienced the discovery of new ransomware species of the Android.Locker family. These programs lock Android devices and demand a ransom to unlock them. Virus definitions for these ransomware programs in the Dr.Web virus database:
| February 2015 | March 2015 | Growth |
|---|---|---|
| 174 | 190 | +9,2% |
Other malicious applications
Android.Gazon.1
This Trojan is designed to generate illicit profits for intruders by loading sites involved in different kinds of surveys in the compromised device's browser. Threat distribution and features:
- It is spread by virus writers in the guise of an Amazon discount coupon. It can also use an SMS worm routine to penetrate other devices. It sends short messages to all of the contacts found in the phone book on the infected handheld, inviting the recipients to open a link to get a coupon.
- When launched, it will load a web survey page in the browser. If the user completes it, the malware's makers receive monetary compensation.
Android.Backdoor.160.origin
A multi-purpose backdoor for Android that can perform a wide range of tasks. Distribution and features:
- Criminals use Baidu Cloud push notifications to spread it.
- It can intercepts SMS, records audio with the device's microphone, acquires location data, and uploads the user’s photo and all their contact information from the phone book to a remote server.
- It can send text messages, make calls, and download and delete files.
- Has several modifications (Android.Backdoor.161.origin, Android.Backdoor.165.origin).