Doctor Web’s Q4 2025 review of virus activity on mobile devices
January 12, 2026
At the same time, noticeable banking trojan activity was observed, with users encountering them 65.52% more frequently. This growth was largely due to members of the Android.Banker family. Such malicious programs intercept SMS with one-time codes for confirming banking transactions and can also imitate the appearance of legitimate bank software and display phishing windows.
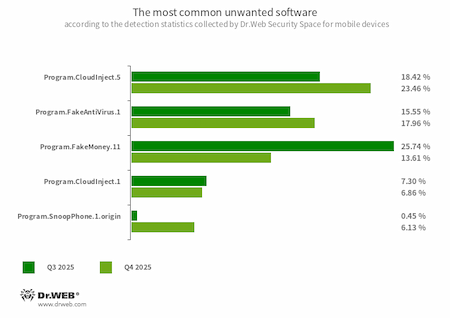
Android apps modified with the CloudInject cloud service (Dr.Web anti-virus detects them as Program.CloudInject) were the most widespread unwanted software. CloudInject adds dangerous system permissions to the apps and obfuscated code, while the purpose of that code cannot be controlled. Program.FakeAntiVirus (fake anti-viruses) and Program.FakeMoney (apps) were also commonly found on protected devices. The former detect non-existing threats and ask users to purchase the full version to “cure” the infection, while the latter allegedly allow users to make money by completing various tasks.
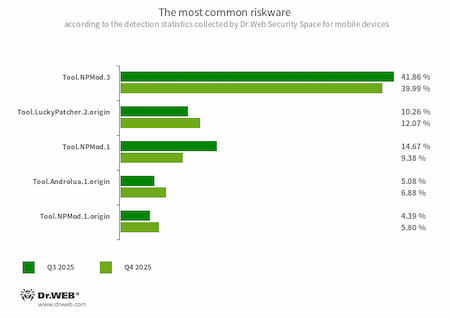
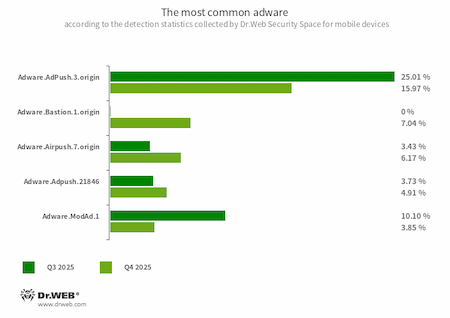
The most widespread riskware programs in Q4 were Tool.NPMod apps, programs modified using the NP Manager utility. This tool obfuscates the code of the modified apps and adds a special module to them that allows digital signature verification to be bypassed once applications are modified. Among the adware detections, members of the Adware.Adpush family retained their lead. These are special software modules that developers integrate into apps to display notifications containing advertisements.
In October, our specialists informed users about the dangerous backdoor Android.Backdoor.Baohuo.1.origin. Threat actors embedded it into unofficial Telegram X messenger modifications and distributed it through malicious websites and third-party Android app catalogs. This malware steals logins and passwords for Telegram accounts as well as other confidential data. Moreover, with its help, threat actors can practically control the victim’s account and covertly perform various actions in the messenger on their behalf. For example, the attackers can join Telegram channels and leave them, conceal new authorized devices, conceal certain messages, etc. Malicious actors use several control mechanisms to operate Android.Backdoor.Baohuo.1.origin. One of them is the Redis database, which has not been seen previously in Android threats. In total, this backdoor infected around 58,000 devices, including about 3,000 different models of smartphones, tablets, TB box sets, and cars with on-board Android-based computers.
Over the past quarter, Doctor Web’s anti-virus laboratory discovered new malware on Google Play. Among these programs were Android.Joker trojans, which subscribe victims to paid services, and various Android.FakeApp fake programs, which are used in fraudulent schemes. They had at least 263,000 downloads combined.
PRINCIPAL TRENDS OF Q4 2025
- Ad-displaying trojans remain the most widespread Android threats
- The number of banking trojan attacks increased
- Malicious actors distributed the dangerous backdoor Android.Backdoor.Baohuo.1.origin, which was built into Telegram X messenger modifications
- More malicious programs emerged on Google Play
According to statistics collected by Dr.Web Security Space for mobile devices
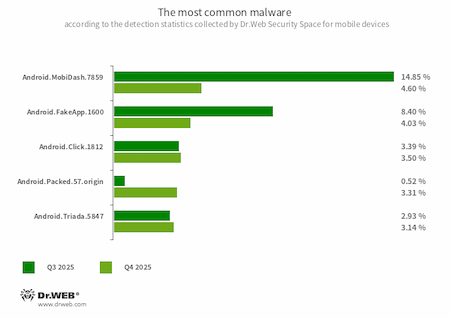
- Android.MobiDash.7859
- A trojan app that displays obnoxious ads. It is a special software module that developers incorporate into applications.
- Android.FakeApp.1600
- A trojan app that loads the website that is hardcoded into its settings. Known modifications of this malicious program load an online casino site.
- Android.Click.1812
- The detection name for malicious WhatsApp messenger mods that can covertly load various websites in the background.
- Android.Packed.57.origin
- The detection name for an obfuscator that is used to protect apps, including malicious ones (for example, some Android.SpyMax banking trojan versions).
- Android.Triada.5847
- The detection name for a packer for Android.Triada trojans that is designed to protect them from being detected and analyzed. Threat actors most often use the packer together with the malicious Telegram messenger mods in which these trojans are embedded.
- Program.CloudInject.5
- Program.CloudInject.1
- The detection name for Android programs that have been modified using the CloudInject cloud service and the eponymous Android utility (the latter was added to the Dr.Web virus database as Tool.CloudInject). Such programs are modified on a remote server; meanwhile, the modders (users) who are interested in such modifications cannot control exactly what will be added to the apps. Moreover, these programs receive a number of dangerous system permissions. Once modification is complete, modders can remotely manage these apps—blocking them, displaying custom dialogs, tracking when other software is being installed or removed from a device, etc.
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.FakeMoney.11
- The detection name for Android applications that allegedly allow users to earn money by completing different tasks. These apps make it look as if rewards are accruing for each one that is completed. At the same time, users are told that they have to accumulate a certain sum to withdraw their “earnings”. Typically, such apps have a list of popular payment systems and banks that supposedly could be used to withdraw the rewards. But even if users succeed in accumulating the needed amount, in reality they cannot get any real payments. This virus record is also used to detect other unwanted software based on the source code of such apps.
- Program.SnoopPhone.1.origin
- An application designed to monitor the activity of Android device owners. It allows intruders to read SMS, collect call information, track device location, and record the surroundings.
- Tool.NPMod.3
- Tool.NPMod.1
- Tool.NPMod.1.origin
- The detection name for Android programs that have been modified using the NP Manager utility. A special module is embedded in such apps, and it allows them to bypass digital signature verification once they have been modified.
- Tool.LuckyPatcher.2.origin
- A tool that allows apps installed on Android devices to be modified (i.e., by creating patches for them) in order to change the logic of their work or to bypass certain restrictions. For instance, users can apply it to disable root-access verification in banking software or to obtain unlimited resources in games. To add patches, this utility downloads specially prepared scripts from the Internet, which can be crafted and added to a shared database by any third party. The functionality of such scripts can prove to be malicious; thus, patches made with this tool can pose a potential threat.
- Tool.Androlua.1.origin
- The detection name for some potentially dangerous versions of a specialized framework for developing Android software based on the Lua scripting language. The main logic of Lua-based apps resides in corresponding scripts that are encrypted and decrypted by the interpreter upon execution. By default, this framework often requests access to a large number of system permissions in order to operate. As a result, the Lua scripts that it executes can potentially perform various malicious actions in accordance with the acquired permissions.
- Adware.AdPush.3.origin
- Adware.Adpush.21846
- Adware modules that can be built into Android apps. They display notifications containing ads that mislead users. For example, such notifications can look like messages from the operating system. In addition, these modules collect a variety of confidential data and are able to download other apps and initiate their installation.
- Adware.Bastion.1.origin
- The detection name for optimization programs that periodically create notifications with misleading messages about allegedly low storage and “system errors” in order to display ads during the “optimization”.
- Adware.Airpush.7.origin
- Adware modules that can be built into Android apps and display various ads. Depending on the modules’ version and modification, these can be notifications containing ads, pop-up windows or banners. Malicious actors often use these modules to distribute malware by offering their potential victims diverse software for installation. Moreover, such modules collect personal information and send it to a remote server.
- Adware.ModAd.1
- The detection name for some modified versions (mods) of the WhatsApp messenger, whose functions have been injected with a specific code. This code is responsible for loading target URLs by displaying web content (via the Android WebView component) when the messenger is in operation. Such web addresses perform redirects to advertised sites, including online casino, bookmaker, and adult sites.
Threats on Google Play
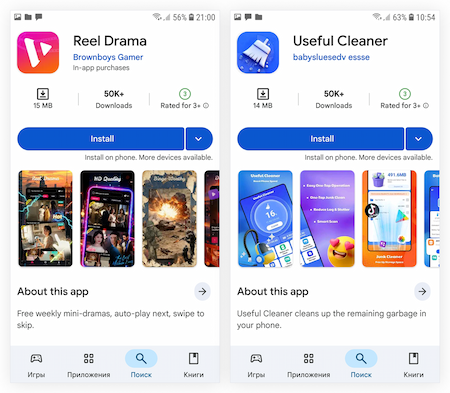
Over the course of Q4 2025, Doctor Web’s virus analysts detected over 20 Android.Joker malicious programs on Google Play. These are designed to subscribe users to paid services; Threat actors camouflaged them as various software: messengers, system optimization tools, image-editing apps, and apps that allow users to watch movies.
Examples of Android.Joker malicious apps that were detected. Android.Joker.2496 masqueraded as Useful Cleaner, a tool for clearing out “junk” from the phone, and one of the Android.Joker.2495 modifications was passed off as the movie player Reel Drama
Our experts also discovered several new fake programs from the Android.FakeApp family. As before, some of them were distributed as financial apps and were designed to load fraudulent websites. Other fakes were passed off as games. Under certain conditions (for instance, if a user’s IP address met the attackers’ requirements), they could load bookmaker and online casino sites.
The Chicken Road Fun game was the fake app Android.FakeApp.1910. It could open an online casino website instead of providing the declared functionality
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.