Doctor Web’s review of virus activity on mobile devices in 2024
January 30, 2025
Among the most active unwanted software programs were apps offering users the opportunity to complete various tasks in exchange for virtual rewards, which can supposedly be converted into real money. The most commonly detected riskware apps were tools that allow Android programs to launch without being installed. And the most active adware programs were specially modified WhatsApp messenger versions whose functions had been injected with code for loading adware URLs.
Over the course of last year, Doctor Web's malware analysts discovered hundreds of new threats on Google Play, with over 26.7 million cumulative downloads. Among these were malicious programs, including a spyware trojan, and unwanted and adware apps.
Our experts also uncovered a new attack on Android-based TV box sets. Around 1.3 million devices were affected by a backdoor that infected the system storage and, when commanded by attackers, could download and install third-party software.
In addition, Doctor Web’s virus analysts noted the growing popularity of a number of techniques aimed at making Android malware more complicated to analyze and more difficult for antiviruses to detect. These techniques included various manipulations with the ZIP archive format (the APK files of Android apps are based on the ZIP format), manipulations with the apps’ configuration file AndroidManifest.xml, and others. These methods were most often found to be used in banking trojans.
PRINCIPAL TRENDS IN 2024
- Ad-displaying malware remained the most widespread threat;
- An increase in banking trojan activity;
- Cybercriminals increasingly used simple Android.Banker banking trojans, which steal only login data for online bank accounts and also verification codes from SMS;
- Threat actors increasingly resorted to manipulating the format of APK apps and their structural components to avoid being detected by anti-viruses and to make it more difficult for their malware to be analyzed;
- An increase in the number of Android.Locker ransomware trojans and Android.Click trojan clickers;
- The emergence of many new threats on Google Play.
The most notable events of 2024
Last May, Doctor Web’s experts informed users about the Android.Click.414.origin trojan clicker, which was found in an app used to control sex toys and in software for tracking physical activity. Both programs were distributed through Google Play and had more than 1.5 million installs combined. Android.Click.414.origin had a modular structure and used its components to execute certain tasks. For example, the trojan covertly loaded advertising websites and performed various actions on them. It could scroll webpages, enter text into forms, mute audio on webpages, and take screenshots of webpages to analyze their contents and click on desired areas. In addition, Android.Click.414.origin sent detailed information about infected devices to its C&C server. At the same time, the clicker did not specifically attack certain users, and it did not start on devices where the interface language was set to Chinese.
Some versions of the Love Spouse and QRunning programs had the Android.Click.414.origin trojan hidden in them
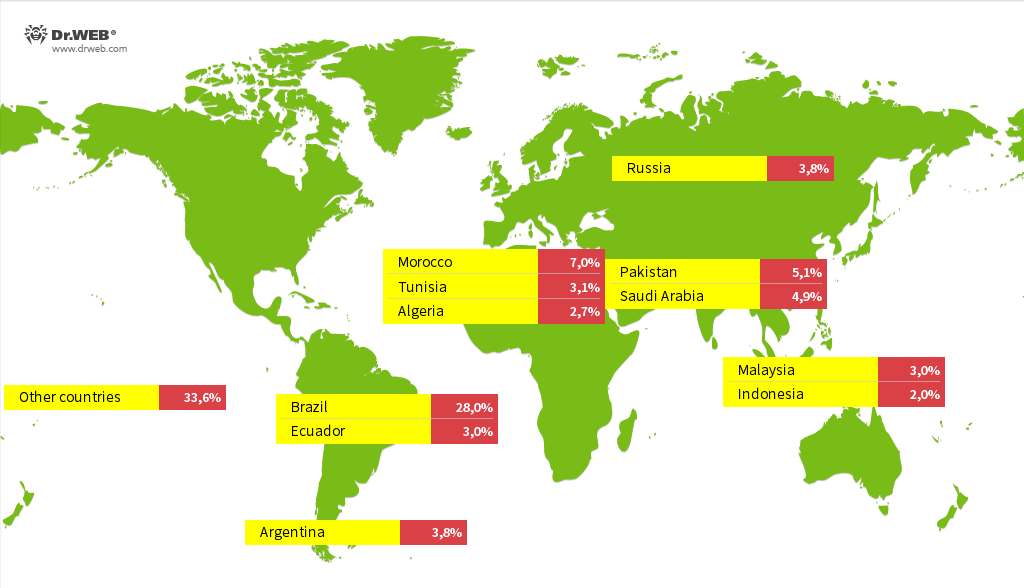
In September, our specialists revealed the details of their analysis regarding cases of Android TV box sets being infected with the Android.Vo1d backdoor. This modular malware affected nearly 1.3 million devices belonging to users in 197 countries. It placed its components into the system storage area and could covertly download and install third-party software when commanded by threat actors.
Countries found to have the highest number of TV boxes infected with the Android.Vo1d backdoor
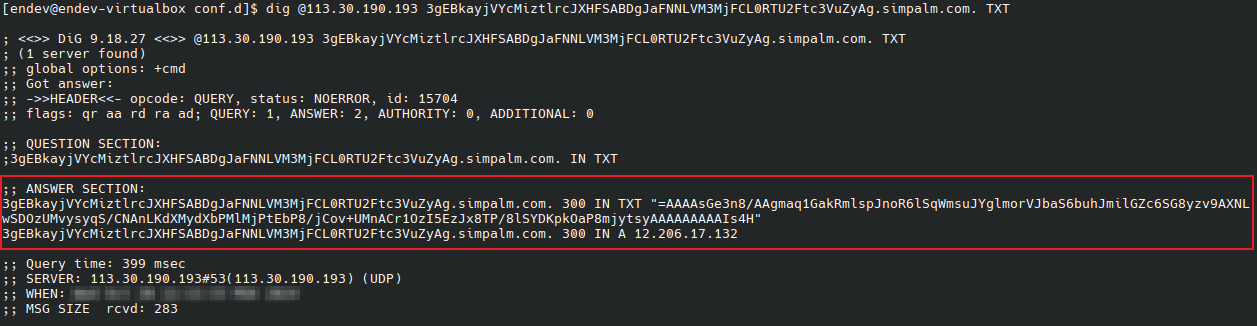
Already in November, our virus analysts used Android.FakeApp.1669 as an example to show how threat actors use the DNS protocol to covertly connect malware to C&C servers. Android.FakeApp.1669 is a rather primitive trojan whose only task is to load target websites. It differs from most of the threats similar to it in that it receives the addresses of target sites from the TXT record of a malicious DNS server. For this, it uses the modified code of an open source dnsjava library. At the same time, Android.FakeApp.1669 manifests its malicious nature only when connected to the Internet through certain providers; in other cases it operates as harmless software.
An example of a target domain’s TXT record. It was sent by the DNS server upon request via the Linux ‘dig’ tool while one of the Android.FakeApp.1669 modifications was undergoing analysis
Statistics
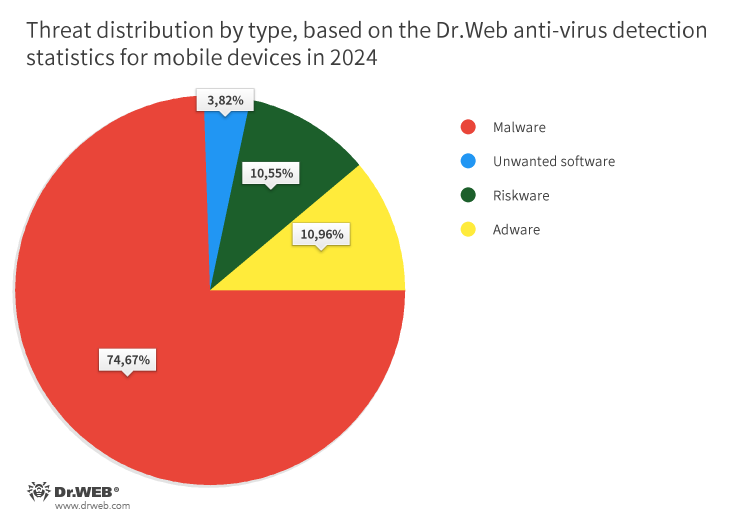
According to detection statistics collected by Dr.Web Security Space for mobile devices, malicious programs were the threats most commonly detected in 2024.They accounted for 74.67% of all registered detections. Adware programs, with a share of 10.96%, ranked second. Riskware apps, which accounted for 10.55% of all detections, ranked third. The fourth most common threats were unwanted apps, which users encountered in 3.82% of cases.
Malicious programs
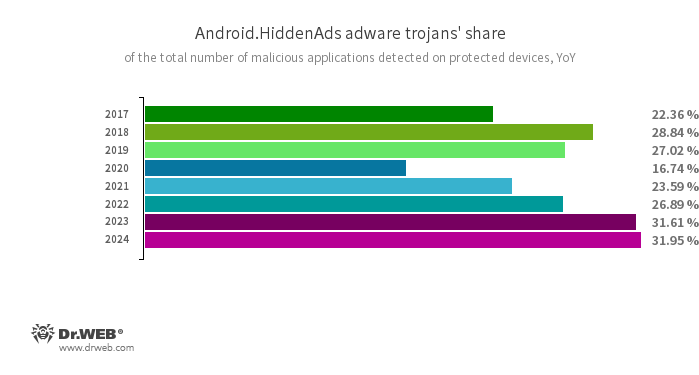
Once again the malicious Android apps most commonly encountered were ad-displaying trojans from the Android.HiddenAds family. Over the course of last year, their share of the total number of malware programs detected by the Dr.Web anti-virus increased by 0.34 pp. to 31.95% of all detections.
In this malware family, the most active member was Android.HiddenAds.3956 (15.10% of the detections for the entire family and 4.84% of all malware detected). This is one of many variants of Android.HiddenAds.1994 malware that users have been encountering for several years now. This particular version, Android.HiddenAds.3956, emerged in 2023 along with other modifications. We predicted that it could take a leading position in the family, which is what eventually happened. In 2024, its new variants also became widespread: Android.HiddenAds.3980, Android.HiddenAds.3989, Android.HiddenAds.3994, Android.HiddenAds.655.origin, Android.HiddenAds.657.origin, and some others.
At the same time, our experts also noticed activity on the part of the Android.HiddenAds.Aegis subfamily. Unlike most other Android.HiddenAds malware, members of this group have the ability to autorun and have some other features. Modifications like Android.HiddenAds.Aegis.1, Android.HiddenAds.Aegis.4.origin, Android.HiddenAds.Aegis.7.origin, and Android.HiddenAds.Aegis.1.origin were the ones most commonly detected on devices protected by Dr.Web anti-virus.
The second most widespread malicious programs were trojans from the Android.FakeApp family, which cybercriminals use in various fraudulent schemes. Last year, they accounted for 18.28% of all malware detections, which is 16.45 pp. higher than the year before. Typically, such trojans load unwanted websites designed for phishing attacks and online fraud.
Android.Spy trojans, which have spyware functionality, ranked third with a share of 11.52%; their share decreased by 16.7 pp., compared to 2023. As in the year before, the most common member of this family was Android.Spy.5106. It accounted for 5.95% of all detected malware.
In 2024, we observed a mixed trend in the distribution of malware that is designed to download and install other apps and capable of executing arbitrary code. Compared to the previous year, the share of Android.DownLoader downloader trojans decreased by 0.49 pp. to 1.69%; the share of Android.Mobifun trojans decreased by 0.15 pp. to 0.10%; and the share of Android.Xiny trojans decreased by 0.14 pp. to 0.13%. At the same time, Android.Triada and Android.RemoteCode trojans were detected more often. The number of detection cases for the former increased by 0.6 pp. to 2.74%, and for the latter by 0.95 pp. to 3.78%.
The share of Android.Packed malware protected by software packers decreased from 7.98% to 5.49%, nearly returning to the 2022 figure. The number of attacks involving Android.MobiDash adware trojans also decreased—from 10.06% to 5.38%. At the same time, the number of Android.Locker ransomware and Android.Proxy trojan detections increased slightly—from 1.15% to 1.60% and from 0.57% to 0.81%, respectively. Android.Proxy trojans allow threat actors using infected Android devices to redirect their network traffic through them. In addition, the activity of Android.Click malicious programs increased significantly, from 0.82% to 3.56%. These trojans can open advertising websites and perform clicks on webpages.
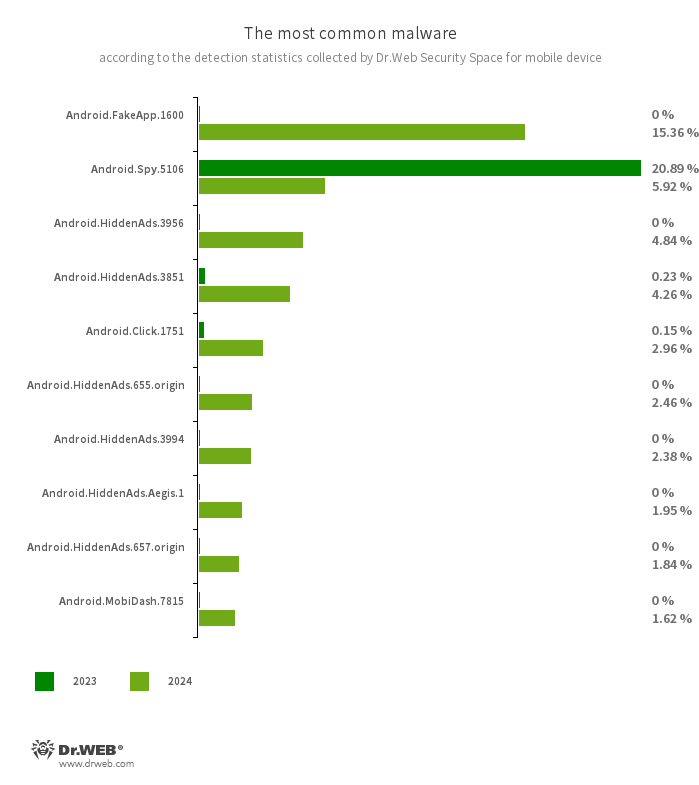
The ten most commonly detected malicious programs in 2024:
- Android.FakeApp.1600
- A trojan app that loads a website that is hardcoded into its settings. Known modifications of this malicious program load an online casino site.
- Android.Spy.5106
- The detection name for a trojan that presents itself as modified versions of unofficial WhatsApp messenger mods. This malicious program can steal the contents of notifications and offer users other apps from unknown sources for installation. And when such a modified messenger is used, it can also display dialog boxes containing remotely configurable content.
- Android.HiddenAds.3956
- Android.HiddenAds.3851
- Android.HiddenAds.655.origin
- Android.HiddenAds.3994
- Android.HiddenAds.657.origin
- Trojan apps designed to display intrusive ads. Members of the Android.HiddenAds family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.Click.1751
- This trojan is built into third-party WhatsApp messenger mods and camouflaged as Google library classes. While the host application is being used, Android.Click.1751 connects to one of the C&C servers and receives two URLs from it. One of them is intended for Russian-speaking users, and the other is for everyone else. The trojan then displays a dialog box whose contents it has also received from a remote server. When a user clicks on the confirmation button, malware loads the corresponding link in the browser.
- Android.HiddenAds.Aegis.1
- A trojan app that conceals its presence on Android devices and displays intrusive ads. It has a number of characteristics that differentiate it from other members of the Android.HiddenAds family. For example, this trojan can run automatically after its installation. Moreover, it implements a mechanism that allows its service to remain constantly running. And, in some cases, it can also use hidden Android operating system functions.
- Android.MobiDash.7815
- A trojan app that displays obnoxious ads. It is a special software module that developers incorporate into applications.
Unwanted software
The unwanted program most commonly detected in 2024 was Program.FakeMoney.11. It accounted for more than half (52.10%) of the total number of unwanted software detected on protected devices. It belongs to a class of apps that offer users a chance to make money by completing various tasks but ultimately do not provide any real rewards.
Programs that Dr.Web anti-virus detects as Program.CloudInject.1 ranked second, with a share of 19.21% (up 9.75 pp. from the previous year). Such apps are modified through the CloudInject cloud service. When modified, they have dangerous permissions and an obfuscated code added to them, and the purpose of that code cannot be controlled.
Program.FakeAntiVirus.1 program activity declined for the second year in a row. With a share of 10.07%, which is down 9.35 pp. from 2023, these programs became the third most widespread unwanted software. They imitate anti-virus software, detect nonexistent threats, and ask users to buy full versions to “fix” the issues that have allegedly been found.
Over the course of last year, users encountered a variety of programs for monitoring and controlling activity. Such software can be used to collect data, both with the consent of device owners and without their knowledge. In the latter case, these actually turn into spying tools. The following monitoring programs were most often detected on devices protected by Dr.Web anti-virus: Program.TrackView.1.origin (2.40% of cases), Program.SecretVideoRecorder.1.origin (2.03% of cases), Program.wSpy.3.origin (0.98% of cases), Program.SecretVideoRecorder.2.origin (0.90% of cases), Program.Reptilicus.8.origin (0.64% of cases), Program.wSpy.1.origin (0.39% of cases), and Program.MonitorMinor.11 (0.38% of cases).
Additionally, Program.Opensite.2.origin Android programs, with a share of 0.60% of all the unwanted software detected, were also spotted. These programs are designed to load target websites and display ads.
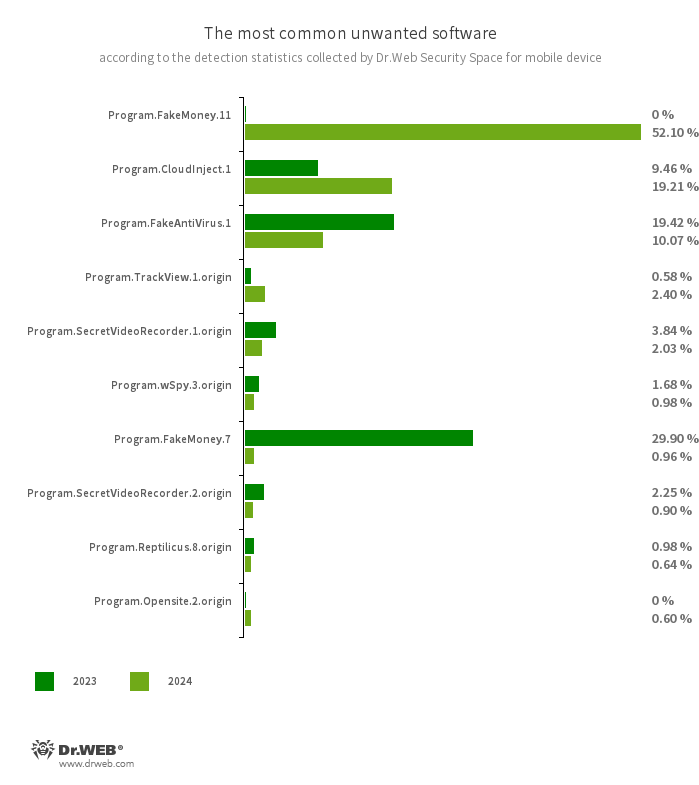
The ten unwanted programs most commonly detected in 2024:
- Program.FakeMoney.11
- Program.FakeMoney.7
- The detection name for Android applications that allegedly allow users to earn money by completing different tasks. These apps make it look as if rewards are accruing for each one that is completed. At the same time, users are told that they have to accumulate a certain sum to withdraw their “earnings”. Typically, such apps have a list of popular payment systems and banks that supposedly could be used to withdraw the rewards. But even if users succeed in accumulating the needed amount, in reality they cannot get any real payments. This virus record is also used to detect other unwanted software based on the source code of such apps.
- Program.CloudInject.1
- The detection name for Android programs that have been modified using the CloudInject cloud service and the eponymous Android utility (the latter was added to the Dr.Web virus database as Tool.CloudInject). Such programs are modified on a remote server; meanwhile, the modders (users) who are interested in such modifications cannot control exactly what will be added to the apps. Moreover, these programs receive a number of dangerous system permissions. Once modification is complete, users can remotely manage these apps. They can block them, display custom dialogs, and track when other software is being installed or removed from a device, etc.
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.TrackView.1.origin
- The detection name for a program that allows users to be monitored via their Android devices. Malicious actors can utilize it to track a target device’s location, use the camera to record video and take photos, eavesdrop via the microphone, record audio, etc.
- Program.SecretVideoRecorder.1.origin
- Program.SecretVideoRecorder.2.origin
- The detection name for various modifications of an application that is designed to record videos and take photos in the background, using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
- Program.wSpy.3.origin
- This is a commercial spyware app designed to covertly monitor Android device user activity. It allows intruders to read SMS and chats in popular messaging software, listen to the surroundings, track device location and browser history, gain access to the phonebook and contacts, photos and videos, and take screenshots and pictures through a device’s built-in camera. In addition, it has keylogger functionality.
- Program.Reptilicus.8.origin
- An application that allows Android device users to be monitored. It can track device location, collect information from SMS and social media messages, intercept phone calls and record the surroundings, take screenshots, act as a keylogger, copy files from a target device and perform other actions.
- Program.Opensite.2.origin
- The detection name for single-type Android programs whose function is to load target websites and display ads. Such apps often masquerade as other software. For instance, there exist modifications that are distributed under the guise of YouTube player. They load a genuine YouTube website and display advertisement banners, using the advertising SDKs connected to them.
Riskware
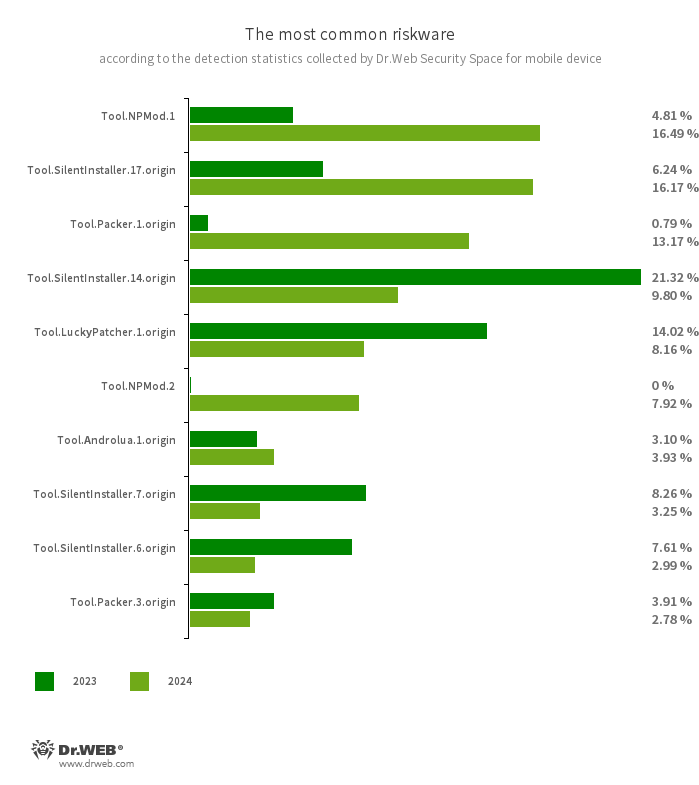
In 2024, Tool.SilentInstaller utilities, which allow Android programs to launch without being installed, retained their leading positions in terms of riskware software detection numbers. In total, they accounted for more than a third of all apps of this type identified on protected devices. Modifications like Tool.SilentInstaller.17.origin (16.17%), Tool.SilentInstaller.14.origin (9.80%), Tool.SilentInstaller.7.origin (3.25%), and Tool.SilentInstaller.6.origin (2.99%) were most often detected.
Other common riskware apps were programs modified using the NP Manager utility. This tool embeds a special module into the target software, which allows the digital signature verification process to be bypassed once the apps have been modified. Dr.Web anti-virus detects such programs as different variants of the Tool.NPMod family. Of these, Tool.NPMod.1 variants were most commonly detected. Over the course of 2024, they significantly strengthened their position, accounting for 16.49% of all riskware detections, up 11.68 pp. from 2023. At the same time, the share of programs modified using the NP Manager tool and detected with another virus record, Tool.NPMod.2, was 7.92%. As a result, members of this family were responsible for almost a quarter of potentially dangerous software detections.
Programs protected by the Tool.Packer.1.origin packer were also among the leaders. They were detected in 13.17% of cases, up 12.38 pp. from the year before. Moreover, the number of Tool.Androlua.1.origin detections increased from 3.10% to 3.93%. This is a framework that makes it possible to modify Android apps and run Lua scripts that can potentially be malicious.
At the same time, one 2023 leader, the Tool.LuckyPatcher family of utilities, was, on the contrary, less active—down from 14.02% to 8.16%. These tools allow Android programs to be modified and scripts downloaded from the Internet to be added to them. Also less frequently encountered were programs protected by the obfuscating utility Tool.Obfuscapk (down from 3.22% to 1.05%) and by the packer Tool.ApkProtector (down from 10.14% to 3.39%).
The ten most widespread riskware apps detected on protected Android devices in 2024:
- Tool.NPMod.1
- Tool.NPMod.2
- The detection name for Android programs that have been modified using the NP Manager utility. A special module is embedded in such apps, and it allows them to bypass digital signature verification once they have been modified.
- Tool.SilentInstaller.17.origin
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.6.origin
- Riskware platforms that allow applications to launch APK files without installing them. They create a virtual runtime environment in the context of the apps in which they are integrated. The APK files, launched with the help of these platforms, can operate as if they are part of such programs and can also obtain the same permissions.
- Tool.Packer.1.origin
- A packer tool designed to protect Android applications from unauthorized modification and reverse engineering. This tool is not malicious in itself, but it can be used to protect both harmless and malicious software.
- Tool.LuckyPatcher.1.origin
- A tool that allows apps installed on Android devices to be modified (i.e., by creating patches for them) in order to change the logic of their work or to bypass certain restrictions. For instance, users can apply it to disable root-access verification in banking software or to obtain unlimited resources in games. To add patches, this utility downloads from the Internet specially prepared scripts, which can be crafted and added to the common database by any third party. The functionality of such scripts can prove to be malicious; thus, patches made with this tool can pose a potential threat.
- Tool.Androlua.1.origin
- The detection name for some potentially dangerous versions of a specialized framework for developing Android software in the Lua scripting language. The main logic of Lua-based apps resides in the corresponding scripts that are encrypted and decrypted by the interpreter upon execution. By default, this framework often requests access to a large number of system permissions in order to operate. As a result, the Lua scripts that it executes can potentially perform various malicious actions in accordance with the acquired permissions.
- Tool.Packer.3.origin
- The detection name for Android programs whose code is encoded and obfuscated by the NP Manager tool.
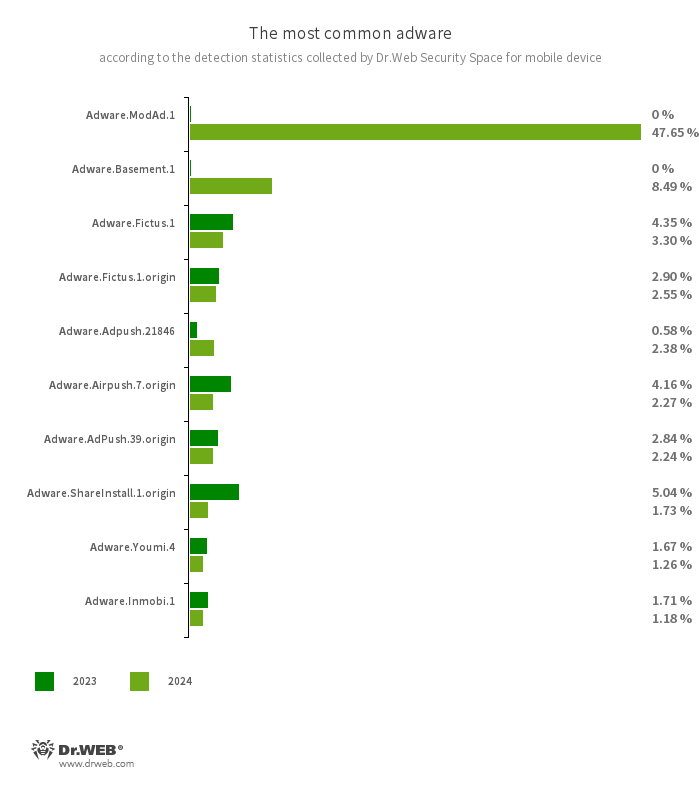
Adware
The most common adware in 2024 was the new Adware.ModAd family, which accounted for 47.45% of detections. The previous year’s leaders, members of the Adware.Adpush family, dropped to second place with a share of 14.76% (a 21.06 pp. decrease in the number of detections). Third place, with a share of 8.68%, was occupied by another new adware family, Adware.Basement.
Also commonly encountered were families like Adware.Airpush (their share decreased from 8.59% to 4.35%), Adware.Fictus (down from 4.41% to 3.29%), Adware.Leadbolt (down from 4.37% to 2.26%), and Adware.ShareInstall (down from 5.04% to 1.71%). Unwanted ad-displaying Adware.MagicPush programs, which ranked second in 2023, significantly curtailed their activity and did not even make it into the top 10; they moved straight to eleventh place with a share of 1.19% (a 8.39 pp. decrease).
The ten most widespread adware apps detected on protected Android devices in 2024:
- Adware.ModAd.1
- The detection name for some modified versions (mods) of the WhatsApp messenger, whose functions have been injected with a specific code. This code is responsible for loading target URLs by displaying web content (via the Android WebView component) when the messenger is in operation. Such web addresses perform redirects to advertised sites, including online casino, bookmaker, and adult sites.
- Adware.Basement.1
- These are apps that display unwanted ads which often lead to malicious and fraudulent websites. They share a common code base with the Program.FakeMoney.11 unwanted applications.
- Adware.Fictus.1
- Adware.Fictus.1.origin
- An adware module that malicious actors embed into cloned versions of popular Android games and applications. Its incorporation is facilitated by a specialized net2share packer. Copies of software created this way are then distributed through various software catalogs. When installed on Android devices, such apps and games display obnoxious ads.
- Adware.Adpush.21846
- Adware.AdPush.39.origin
- Adware modules that can be built into Android apps. They display notifications containing ads that mislead users. For example, such notifications can look like messages from the operating system. In addition, these modules collect a variety of confidential data and are able to download other apps and initiate their installation.
- Adware.Airpush.7.origin
- Adware modules that can be built into Android apps and display various ads. Depending on the modules’ version and modification, these can be notifications containing ads, pop-up windows or banners. Malicious actors often use these modules to distribute malware by offering their potential victims diverse software for installation. Moreover, such modules collect personal information and send it to a remote server.
- Adware.ShareInstall.1.origin
- An adware module that can be built into Android applications. It displays notifications containing ads on the Android OS lock screen.
- Adware.Youmi.4
- The detection name for an unwanted adware module that adds advertizing shortcuts onto the Android OS home screen.
- Adware.Inmobi.1
- The detection name for some versions of the Inmobi adware SDK. These are capable of making phone calls and adding event entries into an Android device’s calendar.
Threats on Google Play
In 2024, Doctor Web’s virus analysts discovered over 200 threats with more than 26.7 million combined downloads. In addition to Android.Click.414.origin, these included many other threats, such as ad-displaying Android.HiddenAds trojans. They were distributed under the guise of all kinds of software: image-editing programs, QR code scanners, image collection apps, and even an “anti-theft” alarm for protecting smartphones from falling into the wrong hands. Such trojans conceal their icons after installation and proceed to display aggressive ads that overlap the interface of the operating system and other programs and prevent the device from being used normally.
Examples of adware trojans discovered on Google Play in 2024. Android.HiddenAds.4013 was hiding in the photo editor “Cool Fix Photo Enhancer”, Android.HiddenAds.4034 was in the “Cool Darkness Wallpaper” image-collection app, Android.HiddenAds.4025 was in the QR scanning program “QR Code Assistant”, and Android.HiddenAds.656.origin was in the “anti-theft” alarm program “Warning Sound GBD”
Our experts also discovered various trojans that threat actors were protecting with a complicated software packer.
The “Lie Detector Fun Prank” program was the Android.Packed.57156 trojan, and the “Speaker Dust and Water Cleaner” app was the Android.Packed.57159 trojan; both were protected with a software packer
Other malware we found were members of the Android.FakeApp family, which are used in various fraudulent schemes. The main task of most of these trojans is to open a target URL, while some of them, under certain conditions, can also operate as the software they are disguised as. Many of them were distributed as different apps, including financial programs, like teaching aids and reference books, profit calculators, apps for accessing trading, and instruments for home bookkeeping. Others were disguised as notepads and diaries, software for participating in quiz games, surveys, etc. They also loaded fraudulent investment sites.
Examples of Android.FakeApp trojans that opened links to fraudulent websites: Android.FakeApp.1681 (disguised as the “SenseStrategy” app), Android.FakeApp.1708 (disguised as the “QuntFinanzas” app)
Some Android.FakeApp fake programs were distributed as a variety of games. Many of them could actually provide the declared functionality, but their main task was to load online casino and bookmaker sites.
Examples of Android.FakeApp trojans that were disguised as games and loaded bookmaker and online casino websites: Android.FakeApp.1622 (“3D Card Merge Game”) and Android.FakeApp.1630 (“Crazy Lucky Candy”)
Some trojans from this family were once again camouflaged as job-search programs. Such scam apps load fake vacancy listings and offer users the opportunity to create a resume by providing personal information. In other cases, the trojans can ask potential victims to contact “the employer” via a messenger. In reality, they will actually be writing to the scammers, who will try to lure them into one or another fraudulent scheme.
Examples of the Android.FakeApp trojans that scammers passed off as job-search apps: Android.FakeApp.1627 (the “Aimer” app) and Android.FakeApp.1703 (the “FreeEarn” app)
In addition, more trojans that subscribe users to paid services were uncovered on Google Play. One of them was Android.Subscription.22, which was being distributed as the “InstaPhoto Editor” photo-editing program.
The Android.Subscription.22 trojan is designed to subscribe users to paid services
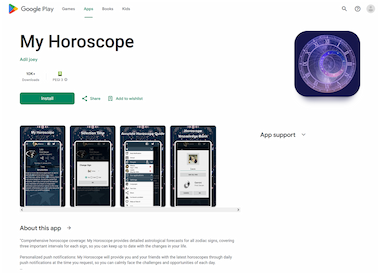
Other such trojans were members of the related Android.Joker and Android.Harly families, which have a modular architecture. The former can download additional components from the Internet, while the latter are distinguished by the fact that they typically store the modules they need in encrypted form in their file resources.
Examples of apps that subscribed victims to paid services. The Android.Joker.2280 was hiding in the horoscope program “My Horoscope”, and the Android.Harly.87 was hiding in the game “BlockBuster”
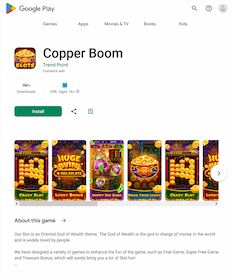
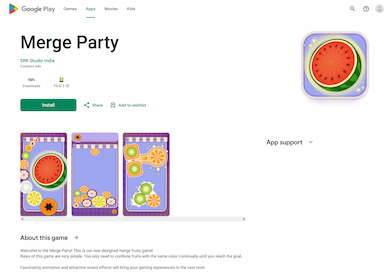
In addition to malware, Doctor Web’s specialists discovered new unwanted software on Google Play, which included different modifications of Program.FakeMoney.11 and Program.FakeMoney.14. These belong to a family of programs that offer users virtual rewards for completing various tasks (often this involves watching ads). The rewards can allegedly be converted into real money or prizes, but to withdraw their “earned” reward, users must collect a certain sum. However, even if they succeed in doing so, they will not get any real payments.
One of the Program.FakeMoney.11 variants was distributed as the game “Copper Boom”, and Program.FakeMoney.14 was disguised as the game “Merge Party”
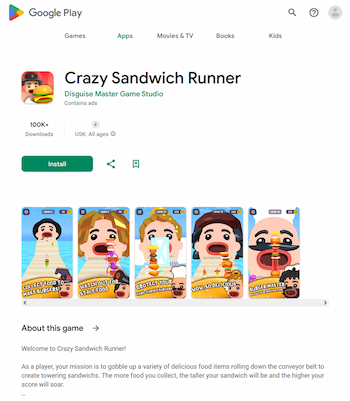
In addition, throughout the year, our malware analysts discovered new adware programs. Among them were apps and games with the built-in adware module Adware.StrawAd, which is capable of displaying ads from various advertising service providers.
Examples of games containing the adware module Adware.StrawAd: “Crazy Sandwich Runner” (Adware.StrawAd.1), “Poppy Punch Playtime” (Adware.StrawAd.3), “Finger Heart Matching” (Adware.StrawAd.6), and “Toimon Battle Playground” (Adware.StrawAd.9)
Adware.Basement adware programs were also distributed via Google Play. Ads from these often lead to malicious and fraudulent websites. It is noteworthy that this family shares a code base with the unwanted Program.FakeMoney.11 apps.
Examples of Adware.Basement unwanted adware programs: “Lie Detector: Lie Prank Test”, “TapAlarm:Don't touch my phone”, and “Magic Voice Changer” are examples for Adware.Basement.1; and “Auto Clicker:Tap Auto” for Adware.Basement.2
Banking trojans
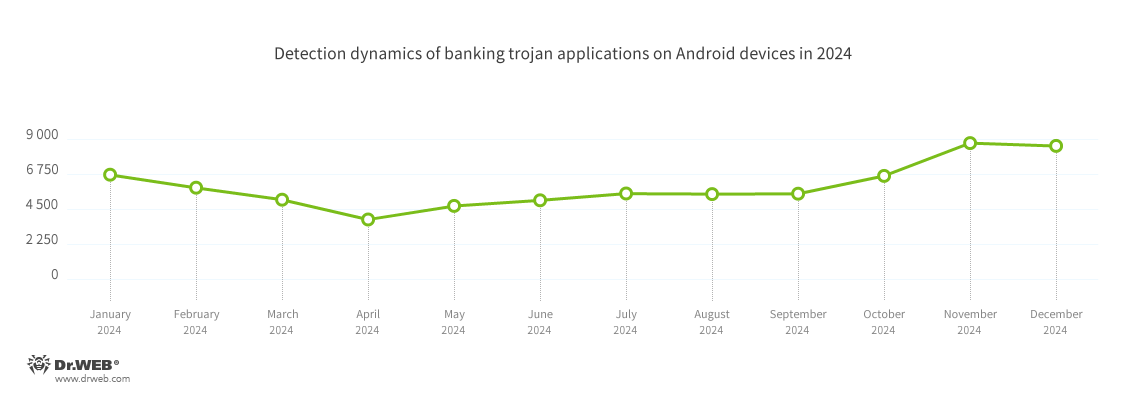
According to detection statistics provided by Dr.Web Security Space for mobile devices, in 2024, banking trojans represented 6.29% of the total number of registered malicious apps, which is up 2.71 pp. from the previous year. Starting in January, their activity steadily declined, but from mid-spring onwards, the number of attacks started to increase again. Their activity remained virtually unchanged during the third quarter, after which they continued to be more active, reaching an annual maximum in November.
In 2024, well-known banking trojan families became widespread again. Among them were the malicious programs Coper, Hydra (Android.BankBot.1048.origin, Android.BankBot.563.origin), Ermac (Android.BankBot.1015.origin, Android.BankBot.15017), Alien (Android.BankBot.745.origin, Android.BankBot.1078.origin), Anubis (Android.BankBot.670.origin). In addition, attacks using the following were observed: Cerberus (Android.BankBot.11404), GodFather (Android.BankBot.GodFather.3, Android.BankBot.GodFather.14.origin), and Zanubis (Android.BankBot.Zanubis.7.origin).
Over the course of 2024, malicious actors actively distributed Android.SpyMax spyware trojans, which have rich malicious functionality. They are also widely used as banking trojans. This family originally included the multifunctional RAT trojan SpyNote (RAT — Remote Administration Trojan or Remote Access Trojan). However, after its source code was leaked, many new modifications based on this code started to emerge, including CraxsRAT and G700 RAT. Dr.Web Security Space detection statistics show that members of this family became more active in the second half of 2023; since then, almost every month they have been detected in increasing numbers, and this trend continues.
Android.SpyMax trojans target users all over the world. Last year, they were also found to be involved in numerous attacks on Russian users, as 46.23% of the detections of this family were registered on devices belonging to this particular audience. These trojans were also most actively distributed among Brazilian (35.46% of detections) and Turkish (5.80% of detections) Android device owners.
It is noteworthy that these malicious programs are mainly distributed in Russia not via spam or classic phishing, but during one stage of telephone fraud. At the beginning of their call, threat actors traditionally try to convince their victims that they are employees of a bank or a law enforcement agency. They inform them about a problem that has allegedly occurred, e.g., an attempt to steal money from the victim’s bank account or an unplanned loan; or, on the contrary, they report “good news” about free money that is supposedly due their victims from the government. When the scammers realize that a user has believed them, they encourage their victim to install an “anti-virus update”, a “banking program”, or some other similar app—for example, to “ensure a secure transaction”. Such a program will, in fact, contain an Android.SpyMax trojan.
In 2024, Russian users also encountered the Falcon banking trojan family (Android.BankBot.988.origin, Android.Banker.5703) and the Mamont family (Android.Banker.637.origin, Android.Banker.712.origin). In addition, attacks involving the banking trojans Android.Banker.791.origin and Android.Banker.829.origin were observed. These targeted Android device owners from Russia and Uzbekistan. Other attacks were perpetrated by Android.Banker.802.origin and affected Russian, Azerbaijani, and Uzbekistani users. Android.Banker.757.origin targeted users from Russia, Uzbekistan, Tajikistan, and Kazakhstan.
Our experts once again detected attacks coming from the MoqHao trojans (Android.Banker.367.origin, Android.Banker.430.origin, Android.Banker.470.origin, Android.Banker.593.origin) that were aimed at users from many countries, including Southeast Asian and Asia-Pacific countries. The same audience was also targeted by other trojans. For example, South Korean Android device owners encountered families like Fakecalls (Android.BankBot.919.origin, Android.BankBot.14423, Android.Banker.5297), IOBot (Android.BankBot.IOBot.1.origin), and Wroba (Android.Banker.360.origin). Other Wroba modifications (Android.BankBot.907.origin, Android.BankBot.1128.origin) attacked users from Japan.
Banking trojans that threatened Chinese users included, for instance, the Android.Banker.480.origin trojan, and Vietnamese users were attacked by Android.BankBot.1111.origin. At the same time, cybercriminals used trojans like TgToxic (Android.BankBot.TgToxic.1) to attack bank customers from Indonesia, Thailand, and Taiwan, and the GoldDigger trojan (Android.BankBot.GoldDigger.3) was used to target users from Thailand and Vietnam.
Attacks on Iranian users were again recorded. These users encountered such banking trojans as Android.Banker.709.origin, Android.Banker.5292, Android.Banker.777.origin, Android.BankBot.1106.origin, and some others. And banking trojans that attacked Turkish bank customers included representatives of the Tambir family (Android.BankBot.1104.origin, Android.BankBot.1099.origin, Android.BankBot.1117.origin), along with some others.
Banking trojans like Android.Banker.797.origin, Android.Banker.817.origin and Android.Banker.5435 targeted Indian users. These trojans were camouflaged as software that was allegedly related to the credit institutions Airtel Payments Bank, PM KISAN, and IndusInd Bank. In addition, Rewardsteal banking trojans (Android.Banker.719.origin, Android.Banker.5147, Android.Banker.5443) remained active. These primarily targeted Indian customers of banks like Axis bank, HDFC Bank, SBI, ICICI Bank, RBL bank, and Citi bank.
In Latin American counties, PixPirate (Android.BankBot.1026.origin) trojan activity was observed; these trojans target Brazilian bank customers.
Among the trojans targeting European users were Anatsa (Android.BankBot.Anatsa.1.origin) and Copybara (Android.BankBot.15140 and Android.BankBot.1100.origin). The latter mainly targets users from Italy, the United Kingdom, and Spain.
During 2024, Doctor Web’s virus analysts observed an increase in the popularity of certain methods of protecting Android malware (primarily banking trojans) from analysis and detection. In particular, attackers performed various manipulations with the ZIP format on which Android APK files are based. As a result, many instruments of static analysis that use standard algorithms to work with ZIP archives are unable to correctly process such “damaged” files. At the same time, the Android OS accepts such modified trojans as normal programs, allowing them to be installed and run.
One common technique is to manipulate the fields compression method and compressed size in the local file header inside the APK. Threat actors intentionally specify the wrong values for the fields compressed size and uncompressed size or write an incorrect or nonexistent compression method in the compression method field. Another option is to specify a method that does not involve compression for the archive. The header fields compressed size and uncompressed size will not match, although they should.
Another popular technique is to use incorrect information about the disk in the ECDR (End of Central Directory Record) and in the CD (Central Directory that contains data about files and archive parameters). Both these parameters should match for a single archive. However, cybercriminals can specify different values for these as if it were not a single archive, but a multi-archive.
Also widespread was a technique whereby a flag was set in the local file headers of some files in the archive, indicating that these files are encrypted. In reality they are not encrypted but due to this, such an archive will be parsed incorrectly.
Along with manipulating the structure of APK files, malware creators also used other practices, such as modifying the AndroidManifest.xml configuration file of Android apps. In particular, they added garbage bytes b'\x00' to this file’s attribute structure, causing it to be read incorrectly.
Prospects and trends
The past year has shown that cybercriminals are still actively enriching themselves at the expense of Android device owners. Their main tools remain ad-displaying and banking trojans, malicious programs with spyware capabilities, and fraudulent software. In this regard, we should expect the emergence of new threats of this type in 2025.
Despite the steps taken to improve the security of Google Play, this app catalog still remains an Android threat distribution source. Therefore, new malicious and unwanted apps emerging in it should not be ruled out.
Another case of Android TV box sets being infected was detected last year, indicating that malware creators use different attack vectors. It is quite possible that threat actors will not only turn their attention to such devices again, but will also continue to look for other potential targets among the variety of Android gadgets.
It is possible that malware developers will continue to actively introduce new techniques that allow their malicious programs to bypass analysis and detection.
Doctor Web’s specialists continue to both monitor the evolution of mobile cyber threats and ensure that our users are protected. To improve your mobile device security, install Dr.Web Security Space, which helps in the fight against malicious, unwanted, and other dangerous programs; fraudsters; and other threats.