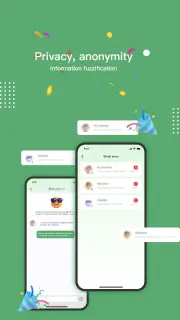
Smart-sex-toy users targeted by clicker trojan
Real-time threat news | Hot news | Threats to mobile devices | All the news
4 may 2024
Origins Tracing™ technology, which detects threats based on behavioral analysis, has been used in the Dr.Web for Android antivirus for more than a decade. It was this component that prevented the infection of one of our user’s devices by detecting the presence of suspicious components in a Love Spouse app downloaded from the Google Play store. The application is used to control adult toys. It contained the Android.Click.414.origin clicker trojan disguised as the com.android.logcatch library, a standard debugging component. In addition to the Love Spouse app, the same trojan has been detected in the QRunning physical activity tracking app. Both apps were developed by Chinese companies. The apps are quite popular, having been installed on over 1.5 million devices. Apparently, the malicious code was embedded recently, in the last few versions of the apps. It should be mentioned that the Love Spouse developer has since updated that application, and as of version 1.8.8, it no longer contains the trojan. However, no corrective updates have been released yet for QRunning.
Screenshots of Love Spouse and QRunning apps
This malware is a modification of the Android.Click.410.origin trojan that popped up on our radar last April. At that time, the virus lab received a ticket from our user whose antivirus had detected a new file on the system partition of their V88mini TV box. It was the downloader for Android.Click.410.origin. There is no reliable information on how exactly the infection occurred. However, we should note that the operating system installed on this device was not what it claimed to be. The product card claimed that the TV box was based on Android 12, and the system information page showed the same. However, the Build ID value, which is a unique identifier of the OS build, corresponds to Android 7. Unfortunately, this situation is quite typical for low-end TV boxes. And as if to prove this point, a similar ticket soon came in from another user. The same Android.Click.410.origin trojan and the same OS spoofing tactics were observed on a X96Q TV box. Only in this case the trojan was embedded in the Desk Clock application.
Probable culprits. For more information on just how big of a threat these devices can be, see our news story on Pandora trojans
Detailed analysis revealed that the trojan has a modular design. One of the modules is used to gather information about the device, while the other two modules stealthily download webpages, display advertisements and perform clicks. The trojan can also detect that its host application is running in a controlled environment. If it detects signs of emulation, it tells its control server not to send advertising tasks. It is also worth noting that the trojan is selective and will not even run on devices where the interface language is set to Chinese.
If successfully launched, the trojan sends fairly detailed device information (brand, model, OS version, IP address, region selected in the settings, carrier code, and others) to its control server and then activates one of its two built-in strategies. As part of these tasks, the trojan secretly loads websites using the WebView component included in the Android operating system. This component allows webpages to be loaded without launching a browser. The trojan can scroll webpages, enter text into forms, and mute audio if the websites it opens play audio or video. To perform these actions, the trojan executes JavaScript code received from its C2 server in the WebView where the target ad page is loaded. In addition, the trojan can take screenshots of the loaded page and send them to the server, analyze them pixel by pixel, and determine clickable areas. For some tasks, the trojan uses Bing, Yahoo, and Google search engines to provide advertising links based on keywords.
Initially, this malware was detected in apps available on unofficial Android app sites, but in February 2024, this trojan infiltrated the official Google Play app store. The Love Spouse app was most likely compromised sometime after the release of version 1.8.1, which did not yet contain the trojan.
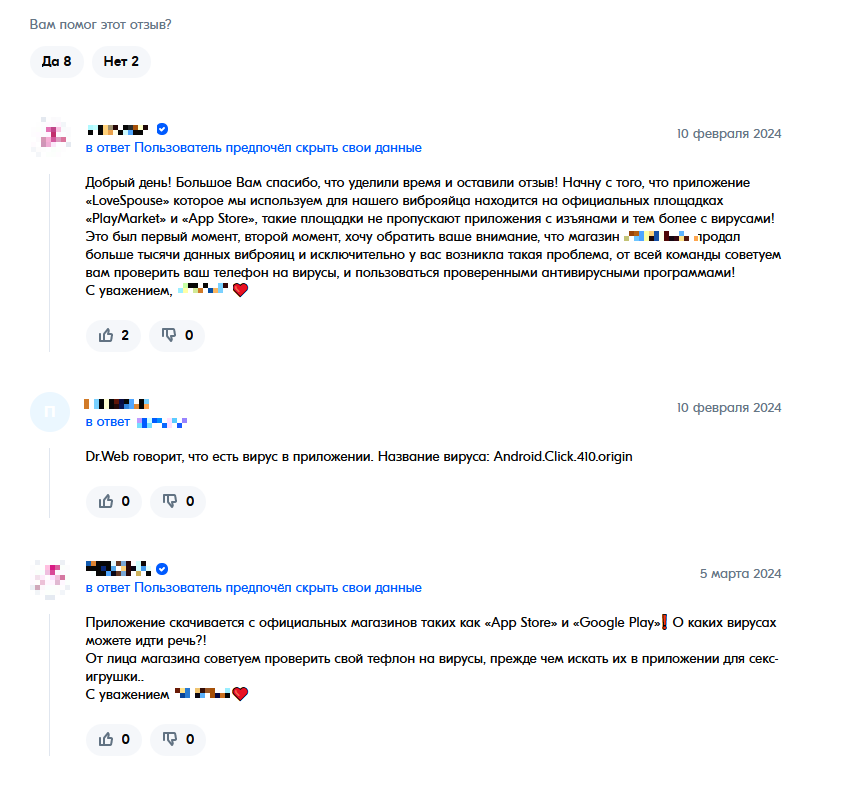
The seller is surprised by the feedback from one of our users that there is a trojan in the Love Spouse app and recommends using “a reputable antivirus instead”.
Doctor Web reminds users to be careful when installing software on their devices. Dr.Web Security Space for Android detects and neutralizes Android.Click trojans, protecting our users' devices from malware.
Indicators of compromise