Doctor Web’s Q3 2024 virus activity review
October 1, 2024
On Android devices, the most commonly detected threats were trojans from the Android.FakeApp family, which are used for fraudulent purposes; Android.HiddenAds adware trojans; and Android.Siggen malicious apps possessing different functionality. At the same time, in August, our experts discovered Android.Vo1d, a new trojan that had infected nearly 1.3 million TV box sets running Android. In addition, several banking trojans targeting Indonesian users were found.
Doctor Web’s virus laboratory also uncovered many new threats on Google Play throughout the third quarter.
Principal trends in Q3 2024
- Adware programs remained the most commonly detected threats.
- Malicious scripts were again predominant in malicious email traffic.
- Over 1 million Android-based TV box sets were found to be infected with the Android.Vo1d backdoor.
- New threats were discovered on Google Play.
According to Doctor Web’s statistics service
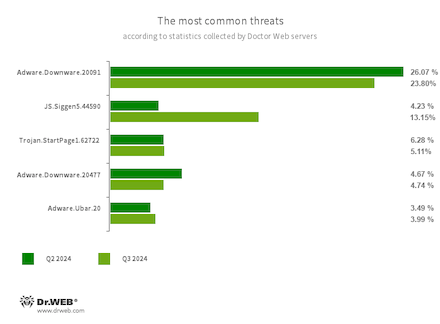
The most common threats in Q3 2024:
- Adware.Downware.20091
- Adware.Downware.20477
- Adware that often serves as an intermediary installer of pirated software.
- JS.Siggen5.44590
- Malicious code added to the es5-ext-main public JavaScript library. It shows a specific message if the package is installed on a server with the time zone of a Russian city.
- Trojan.StartPage1.62722
- A malicious program that can modify the home page in the browser settings.
- Adware.Ubar.20
- A torrent client designed to install unwanted programs on a user’s device.
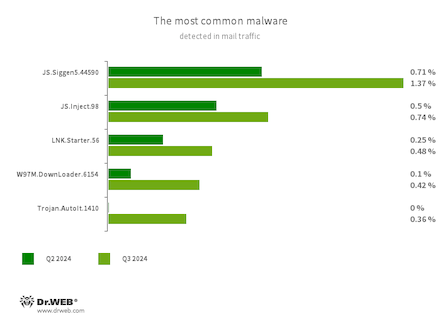
Statistics for malware discovered in email traffic
- JS.Siggen5.44590
- Malicious code added to the es5-ext-main public JavaScript library. It shows a specific message if the package is installed on a server with the time zone of a Russian city.
- JS.Inject
- A family of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- LNK.Starter.56
- The detection name for a shortcut that is crafted in a specific way. This shortcut is distributed through removable media, like USB flash drives. To mislead users and conceal its activities, it has a default icon of a disk. When launched, it executes malicious VBS scripts from a hidden directory located on the same drive as the shortcut itself.
- W97M.DownLoader.6154
- A family of downloader trojans that exploit vulnerabilities in Microsoft Office documents. They can also download other malicious programs to a compromised computer.
- Trojan.AutoIt.1410
- The detection name for packed versions of the Trojan.AutoIt.289 malicious app that are written in the AutoIt scripting language. This trojan is distributed as part of a group of several malicious applications, including a miner, a backdoor, and a self-propagating module. Trojan.AutoIt.289 performs various malicious actions that make it difficult for the main payload to be detected.
Encryption ransomware
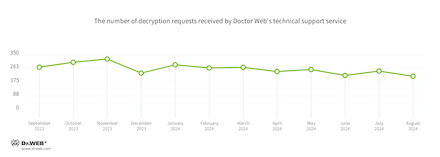
In Q3 2024, the number of requests made to decrypt files affected by encoder trojans decreased by 15.73%, compared to Q2 2024.
The dynamics of the requests Doctor Web’s technical service received to decrypt files affected by encoder trojans:
The most common encoders of Q3 2024:
- Trojan.Encoder.35534 — 19.38%
- Trojan.Encoder.3953 — 9.42%
- Trojan.Encoder.38200 — 3.99%
- Trojan.Encoder.26996 — 2.89%
- Trojan.Encoder.35067 — 2.72%
Network fraud
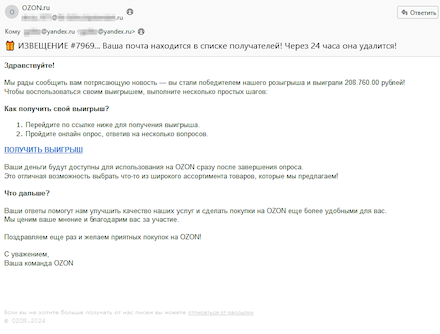
During Q3 2024, Internet scammers continued distributing spam emails containing links leading to various fraudulent sites. Russian-speaking users, for example, again dealt with messages that were supposedly sent on behalf of well-known online stores. Some of these mails offered users the ability to participate in prize draws or get a gift. After clicking on the links in such emails, potential victims were directed to fraudulent sites where they were asked to pay a commission to “receive” their gift or their winnings.
Scammers, allegedly on behalf of an online store, offer their potential victim the chance to “receive their winnings” of 208,760 rubles
In other emails, users were supposedly given a discount that could be used to purchase goods in a large electronics store. The links from such messages led to a fake website designed in the style of the genuine store’s site. When potential victims placed an “order” on this fake Internet resource, they had to provide their personal data and bank card information.
A fraudulent email that lets recipients “activate a promo code” for buying electronics
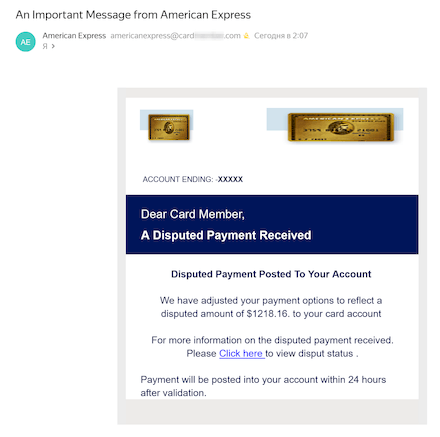
Finance-themed spam remains popular among fraudsters. For instance, threat actors were sending unwanted emails for users to “confirm” their receipt of large money transfers. An example of one such mail targeting English-speaking users is shown below. It contained a link that led to the phishing login form of an online bank that outwardly resembled the form on the real bank’s website.
The user supposedly needs to confirm receipt of US $1,218.16
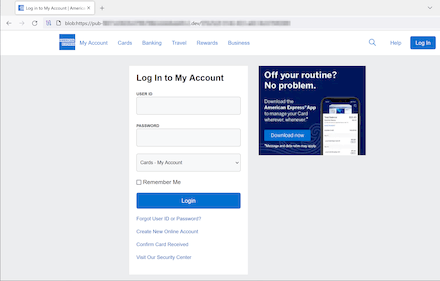
A phishing site that fraudsters pass off as a genuine bank website
Among the unwanted emails targeting Japanese users, our experts detected yet more fake bank notifications—for example, ones that supposedly contained the previous month’s bank card statement. In one of these messages, the scammers camouflaged the link to the phishing site. In the text of the letter, users saw links to the real addresses of the bank’s website, but when they clicked on them, they were taken to a fraudulent Internet resource.
All the links in this email actually lead to a phishing website
French-speaking users (from Belgium, in particular) encountered phishing emails informing them that their bank accounts were “blocked”. To get them “unblocked”, they were asked to follow a link that actually led to the fraudsters’ website.
Scammers scare potential victims with a “blocked” bank account message
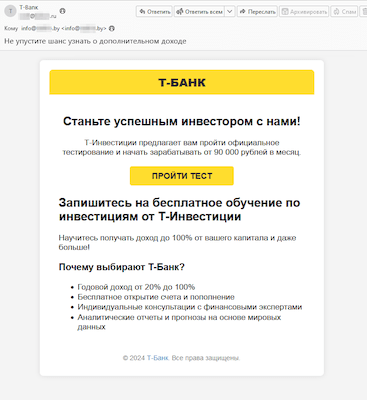
And among Russian users, email spam, sent presumably on behalf of famous banks and offering investor opportunities, was once again actively being distributed. The links in such unwanted emails lead to fraudulent sites where visitors, under the pretense of accessing investing services, are asked to provide personal data.
The user, allegedly on behalf of the bank, is being offered the chance to complete a test and become an investor
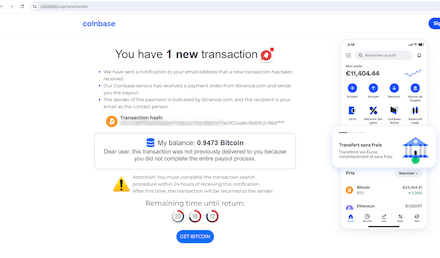
At the same time, Doctor Web’s Internet analysts detected new phishing websites targeting cryptocurrency owners. On one of them, for example, visitors were informed, supposedly on behalf of a large cryptocurrency exchange, about an undelivered Bitcoin transfer. To “complete” the transaction, potential victims were asked to pay a “commission”. Naturally, no cryptocurrency was ever received by the users—all they did was give their own assets to the scammers.
This fraudulent site informs users about a supposedly unreceived Bitcoin transfer
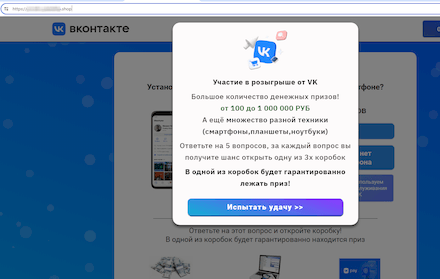
In addition, websites were detected that imitated the look of the VKontakte Russian social network. Visitors to these fake sites were offered the chance to participate in some prize drawing, for which they needed to open several virtual gift boxes. After the potential victims opened the “correct” boxes and allegedly won a large amount of money, the site proposed that they pay a “fee” to receive their “winnings”.
A fraudulent site offering visitors the opportunity to “try their luck”
This user has supposedly won a prize of 194,562 rubles
Malicious and unwanted programs for mobile devices
According to detection statistics collected by Dr.Web Security Space for mobile devices, in Q3 2024, Android.FakeApp malicious apps, which threat actors use in various fraudulent schemes, were most often detected on protected devices. The second most common were adware trojans from the Android.HiddenAds family. These were followed by Android.Siggen trojans.
Over the past observation period, our specialists discovered many new threats on Google Play. Among them were different trojan variants from the Android.FakeApp and Android.HiddenAds families. Moreover, an attack on Android TV box sets was detected, with the Android.Vo1d backdoor infecting about 1.3 million devices from users in 197 countries. It placed its component in the system storage area and, when commanded by threat actors, could covertly download and install third-party software. Additionally, banking trojans Android.SmsSpy.888.origin and Android.SmsSpy.11629 were found that targeted Indonesian users.
The following Q3 2024 events involving mobile malware are the most noteworthy:
- The discovery of the Android.Vo1d backdoor, which infected over a million TV box sets,
- High activity on the part of Android.FakeApp malicious apps,
- High activity on the part of Android.HiddenAds ad-displaying trojans,
- The emergence of new threats on Google Play.
To find out more about the security-threat landscape for mobile devices in Q3 2024, read our special overview.