Doctor Web’s Q3 2024 review of virus activity on mobile devices
October 1, 2024
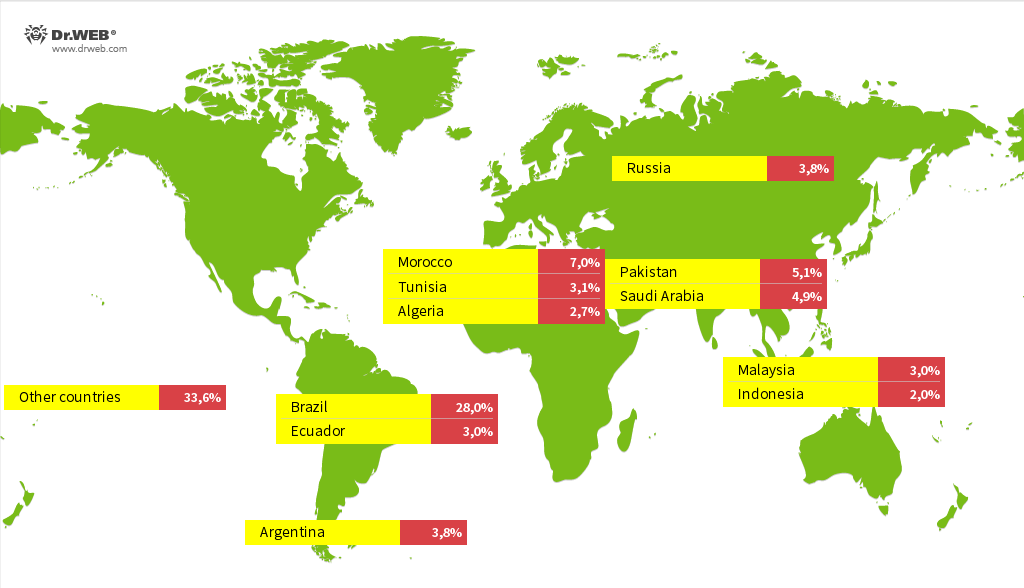
In August, Doctor Web’s experts discovered the Android.Vo1d backdoor, which had infected nearly 1.3 million Android TV box sets belonging to users in 197 countries. This malicious app places its components into the system storage area of infected devices and, when commanded by threat actors, can covertly download and install various programs.
In addition, banking trojans targeting Indonesian users were found. One of these, Android.SmsSpy.888.origin, is protected with a software packer and detected as Android.Siggen.Susp.9415. It was distributed under the guise of the BRI bank customer support app BRImo Support.
When launched, the trojan loads the real bank website https://bri.co.id in WebView. At the same time, it uses a Telegram bot API to send technical information about the infected device into the Telegram chat created by the threat actors.
Android.SmsSpy.888.origin intercepts incoming SMS and also sends them into this chat. When it receives messages like 55555, <number>, <text>, it interprets them as commands and sends corresponding messages containing the text <text> to the number <number>. This way, the malware can both send SMS spam and spread among users.
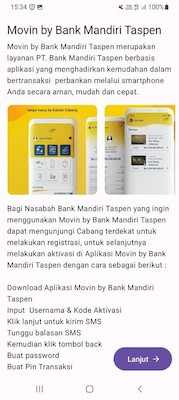
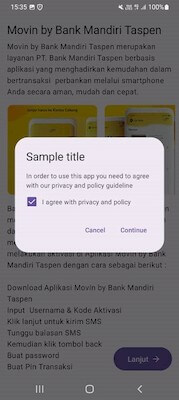
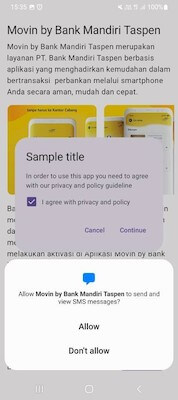
Another trojan that attacked Indonesian users was Android.SmsSpy.11629. This malicious program is an SMS spy that is distributed under the guise of all kinds of apps. The variant in question was targeting Bank Mandiri Taspen customers and was passed off by the attackers as an official banking app—Movin by Bank Mandiri Taspen. The trojan displays instructions to potential victims and asks them to accept a user agreement. When a user accepts it, the trojan requests the permissions needed to work with SMS.
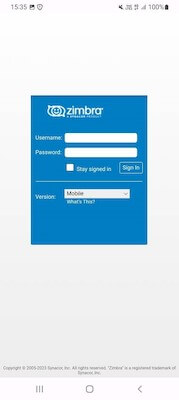
Next, the malicious program loads a real page of the bank’s website https://mail.bankmantap.co.id/: in WebView:
Android.SmsSpy.11629 intercepts all incoming SMS. Next, it uses the Telegram bot API to send these messages into the attackers’ Telegram chat. It adds the text developed by : @AbyssalArmy to all of the messages.
At the same time, our malware analysts again discovered threats on Google Play. Among them were many new fake apps and several ad-displaying trojans.
PRINCIPAL TRENDS OF Q3 2024
- The Android.Vo1d backdoor infected over a million TV box sets
- High activity on the part of Android.FakeApp malicious apps, which are used to commit fraud
- High activity on the part of Android.HiddenAds adware trojans
- The emergence of new malware on Google Play
According to statistics collected by Dr.Web Security Space for mobile devices
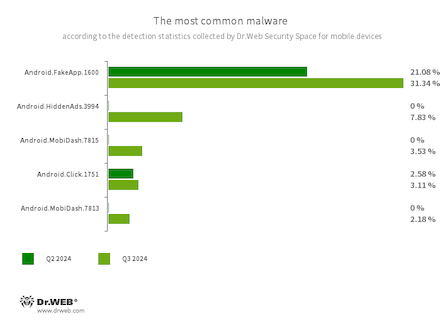
- Android.FakeApp.1600
- A trojan app that loads a website that is hardcoded into its settings. Known modifications of this malicious program load an online casino site.
- Android.HiddenAds.3994
- A trojan app designed to display intrusive ads. Members of the Android.HiddenAds family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.MobiDash.7815
- Android.MobiDash.7813
- Trojans that display obnoxious ads. These are special software modules that developers incorporate into applications.
- Android.Click.1751
- This trojan is built into third-party WhatsApp messenger mods and camouflaged as Google library classes. While the host application is being used, Android.Click.1751 connects to one of the C&C servers. It receives two URLs from it. One of them is intended for Russian-speaking users, and the other is for everyone else. The trojan then displays a dialog box whose contents it has also received from a remote server. When a user clicks on the confirmation button, malware loads the corresponding link in their browser.
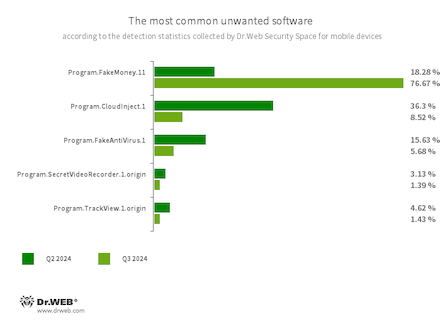
- Program.FakeMoney.11
- The detection name for Android applications that allegedly allow users to earn money by completing different tasks. These apps make it look as if rewards are accruing for each one that is completed. At the same time, users are told they have to accumulate a certain sum to withdraw their “earnings”. Typically, such apps have a list of popular payment systems and banks that supposedly could be used to withdraw the rewards. But even if users succeed in accumulating the needed amount, in reality they cannot get any real payments. This virus record is also used to detect other unwanted software based on the source code of such apps.
- Program.CloudInject.1
- The detection name for Android programs that have been modified using the CloudInject cloud service and the eponymous Android utility (the latter was added to the Dr.Web virus database as Tool.CloudInject). Such programs are modified on a remote server; meanwhile, the modders (users) who are interested in such modifications cannot control exactly what will be added to the apps. Moreover, these programs receive a number of dangerous system permissions. Once modification is complete, users can remotely manage these apps. They can block them, display custom dialogs, and track when other software is being installed or removed from a device, etc.
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.SecretVideoRecorder.1.origin
- The detection name for various modifications of an application that is designed to record videos and take photos in the background, using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
- Program.TrackView.1.origin
- The detection name for a program that allows users to be monitored via their Android devices. Malicious actors can utilize it to track a target device’s location, use the camera to record video and take photos, eavesdrop via the microphone, record audio, etc.
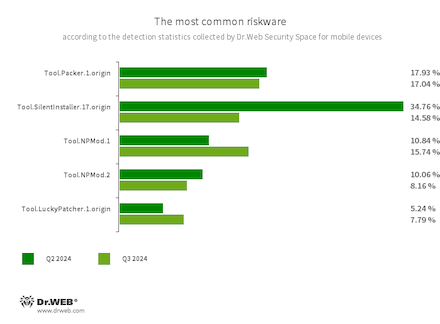
- Tool.Packer.1.origin
- A packer tool designed to protect Android applications from unauthorized modifications and reverse engineering. This tool is not malicious in itself, but it can be used to protect both harmless and malicious software.
- Tool.SilentInstaller.17.origin
- A riskware platform that allows applications to launch APK files without installing them. It creates a virtual runtime environment in the context of the apps in which they are integrated. The APK files, launched with the help of this platform, can operate as if they are part of such programs and can also obtain the same permissions.
- Tool.NPMod.1
- Tool.NPMod.2
- The detection name for Android programs that have been modified using the NP Manager utility. A special module is embedded in such apps, and it allows them to bypass digital signature verification once they have been modified.
- Tool.LuckyPatcher.1.origin
- A tool that allows apps installed on Android devices to be modified (i.e., by creating patches for them) in order to change the logic of their work or to bypass certain restrictions. For instance, users can apply it to disable root-access verification in banking software or to obtain unlimited resources in games. To add patches, this utility downloads specially prepared scripts from the Internet, which can be crafted and added to the common database by any third party. The functionality of such scripts can prove to be malicious; thus, patches made with this tool can pose a potential threat.
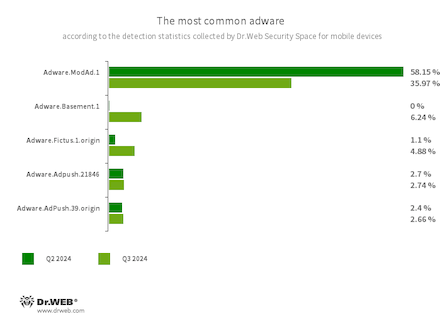
- Adware.ModAd.1
- The detection name for some modified versions (mods) of the WhatsApp messenger, whose functions have been injected with a specific code. This code is responsible for loading target URLs by displaying web content (via the Android WebView component) when the messenger is in operation. Such web addresses perform redirects to advertised sites, including online casino, bookmaker, and adult sites.
- Adware.Basement.1
- These are apps that display unwanted ads which often lead to malicious and fraudulent websites. They share a common code base with the Program.FakeMoney.11 unwanted applications.
- Adware.Fictus.1.origin
- An adware module that malicious actors embed into the cloned versions of popular Android games and applications. Its incorporation is facilitated by a specialized net2share packer. Copies of software created this way are then distributed through various software catalogs. When installed on Android devices, such apps and games display obnoxious ads.
- Adware.Adpush.21846
- Adware.AdPush.39.origin
- Adware modules that can be built into Android apps. They display notifications containing ads that mislead users. For example, such notifications can look like messages from the operating system. In addition, these modules collect a variety of confidential data and are able to download other apps and initiate their installation.
Threats on Google Play
In Q3 2024, Doctor Web’s malware analysts continued uncovering threats on Google Play. Among these were many new Android.FakeApp fake programs that were distributed under the guise of a variety of software. Malicious actors passed some of them off as finance-related programs, such as investing apps, financial reference books and teaching aids, different home bookkeeping tools, and so on. Quite a few of these did actually provide the stated functionality, but their primary task is to load fraudulent websites. Such sites promise potential victims quick and easy money through investments, trading natural resources, cryptocurrency, etc. To supposedly join the “service”, users are asked to register an account or to provide personal data by filling out an “application”.
It is noteworthy that fraudsters disguised one of the Android.FakeApp trojans as an online dating and chat app. However, it also loaded a bogus “investing” site.
Other Android.FakeApp trojans were again distributed as games. Under certain conditions, they loaded online casino and bookmaker sites.
Among these fake apps, our experts also detected new trojan variants that masquerade as job-search tools. Such malware loads fake job lists and suggests to users that they contact the applicable employer via a messenger (this “employer” is, in fact, a fraudster) or that they create a “resume” by providing personal data.
Doctor Web’s virus analysts also discovered more Android.HiddenAds trojans on Google Play. These trojans conceal their icons from the home screen menu and start displaying intrusive ads. The detected malware was camouflaged as various apps, including image collections, photo-editing software, and barcode scanners.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.