Doctor Web’s overview of malware detected on mobile devices in October 2019
November 13, 2019
The second autumn month turned out to be rough for Android users. Doctor Web virus analysts detected numerous malicious applications on Google Play, such as Android.Click clicker trojans that subscribed users to premium services. The detected threats also included malicious software from the Android.Joker family. They also subscribed users to expensive services and were able to execute arbitrary code. Our experts found other trojans as well.
PRINCIPAL TRENDS IN OCTOBER
- A growing number of threats on Google Play
Mobile threat of the month
In early October, Doctor Web reported a few clicker trojans that were added to the Dr.Web virus database as Android.Click.322.origin, Android.Click.323.origin, and Android.Click.324.origin. These malicious apps covertly opened webpages where they subscribed their victims to premium mobile services. The trojans have the following unique features:
- they are embedded into harmless applications;
- they are protected by a program packer;
- they are disguised as well-known SDKs;
- they attack users from specific countries.
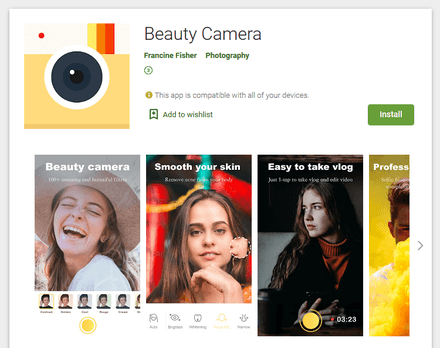
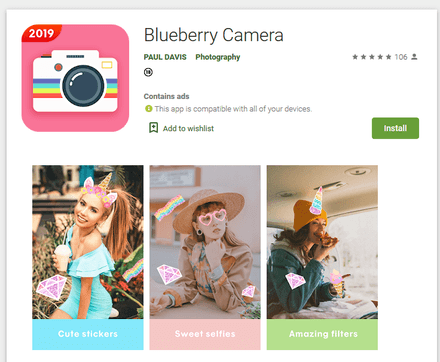
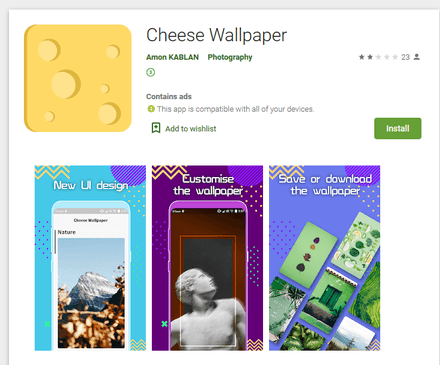
Our virus analysts continued detecting additional modifications to these clickers throughout the entire month, having found Android.Click.791, Android.Click.800, Android.Click.802, Android.Click.808, Android.Click.839, and Android.Click.841. Later, they detected similar malicious applications, dubbed Android.Click.329.origin, Android.Click.328.origin, and Android.Click.844. They also subscribed victims to premium services, but may have been developed by different virus writers. All these trojans were hidden in seemingly harmless applications such as camera apps, photo editors and wallpaper collections.
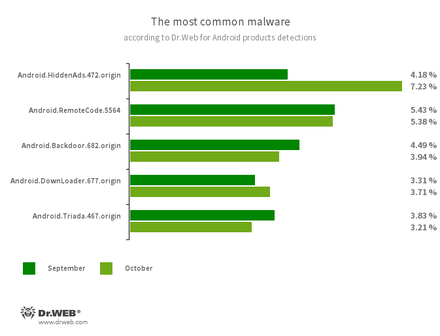
According to statistics collected by Dr.Web for Android
- Android.HiddenAds.472.origin
- A trojan that delivers annoying advertisements.
- Android.RemoteCode.5564
- A malicious application that downloads and executes arbitrary code.
- Android.Backdoor.682.origin
- A trojan that executes cybercriminals’ commands and helps them control infected mobile devices.
- Android.DownLoader.677.origin
- A downloader of other malicious software.
- Android.Triada.465.origin
- A multi-functional trojan that performs various malicious actions.
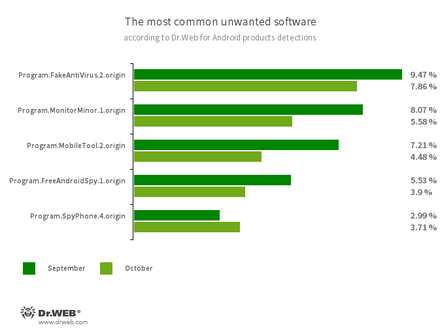
- Program.FakeAntiVirus.2.origin
Detection of adware that imitates anti-virus software. - Program.MonitorMinor.1.origin
- Program.MobileTool.2.origin
- Program.FreeAndroidSpy.1.origin
- Program.SpyPhone.4.origin
Spyware that monitors activities of Android users and may serve as a tool for cyber espionage.
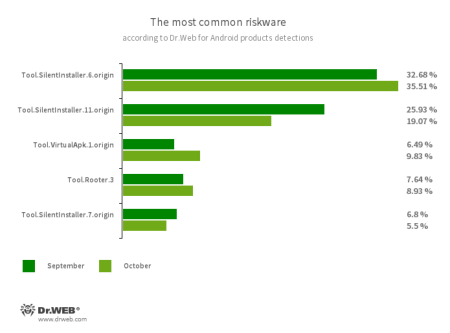
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.11.origin
- Tool.VirtualApk.1.origin
A riskware platform that allows applications to launch APK files without installing them. - Tool.Rooter.3
A utility designed to obtain root privileges on Android devices. It may be used by cybercriminals and malware.
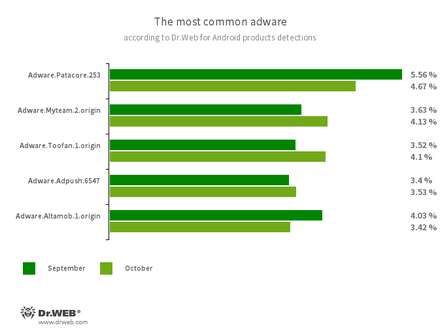
Program modules that incorporate themselves into Android applications and display obnoxious ads on mobile devices:
- Adware.Patacore.253
- Adware.Myteam.2.origin
- Adware.Toofan.1.origin
- Adware.Adpush.6547
- Adware.Altamob.1.origin
Trojans on Google Play
Apart from clicker trojans, Doctor Web virus analysts revealed several versions, as well as modifications to already known malware from the Android.Joker family on Google Play. The list included Android.Joker.6, Android.Joker.7, Android.Joker.8, Android.Joker.9, Android.Joker.12, Android.Joker.18, and Android.Joker.20.origin. These trojans download and launch malicious auxiliary modules that can execute arbitrary code and subscribe users to premium mobile services. They are distributed under the guise of useful and harmless applications such as wallpaper collections, camera apps with artistic filters, various utilities, photo editors, games, online messengers and other software.
Apart from that, our experts detected another trojan adware from the Android.HiddenAds family, dubbed Android.HiddenAds.477.origin. Cybercriminals were spreading it as a video player and an application that provided information about phone calls. Upon launch, the trojan hid its icon from the Android home screen and began displaying annoying ads.
Additionally, the Dr.Web virus database was updated to detect the trojans Android.SmsSpy.10437 and Android.SmsSpy.10447. They were embedded into an image collection and a camera app. Both malicious applications hooked the contents of incoming text messages. Android.SmsSpy.10437 was also able to execute arbitrary code downloaded from the command and control server.
To protect your Android device from malware and unwanted programs, we recommend you install Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 140 million downloads on Google Play alone
- Free for users of Dr.Web home products