Clicker for Android subscribes users to paid services
Hot news | Threats to mobile devices | All the news | Virus alerts
October 17, 2019
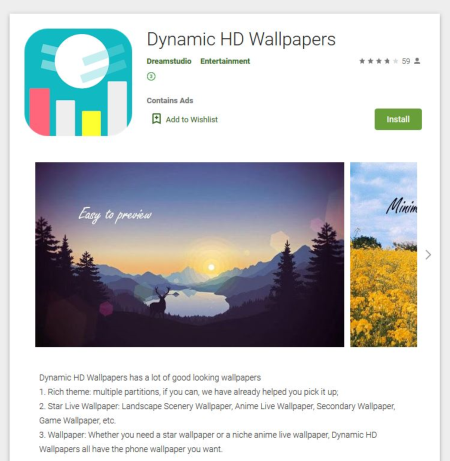
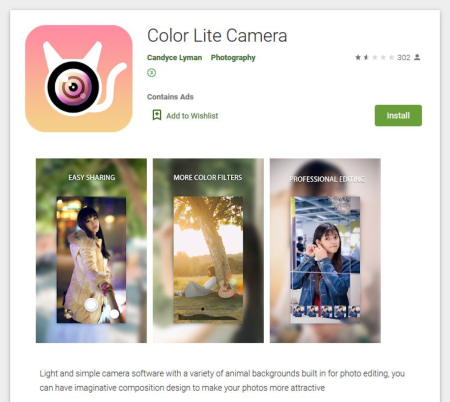
Virus analysts have identified several modifications of this malicious code, dubbed Android.Click.322.origin, Android.Click.323.origin, and Android.Click.324.origin. To hide their true purpose, as well as make the trojans harder to detect, cybercriminals used several tricks. They integrated the clicker into harmless applications, such as camera apps and image collections, that did work as described. As a result, users and information security experts had no obvious reason to consider them as a threat.
Apart from that, all malware was protected by the commercial Jiagu packer, which makes it harder for antiviruses to detect them and hinders the code analysis. Thus, the trojan was more likely to avoid detection by the built-in security tools of Google Play.
Besides, virus writers tried to disguise the trojan as well-known advertising and analytics libraries. After being added to the host software, it embedded itself in the Facebook and Adjust SDKs, hiding among their components.
The clicker attacked users selectively; it did not perform any malicious actions if the potential victim was not residing in one of the attackers’ countries of interest.
See below examples of apps with this trojan:
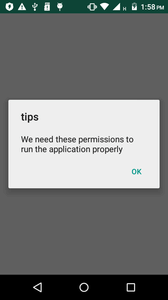
Upon installation and launch, the clicker (hereinafter, we will take its modification Android.Click.322.origin as an example) prompts the user to give it access to notifications of the operating system:
If the user grants it the permissions, the trojan will be able to hide all notifications about incoming text messages and hook them.
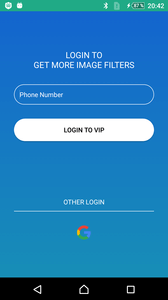
Next, the clicker sends the technical data about the infected device to the command and control server and checks the serial number of the victim’s SIM card. If it corresponds to one of the target countries, Android.Click.322.origin sends information about the phone number to the server. The clicker also displays a phishing window to users of certain countries, where it offers them to enter the phone number or log in to their Google account:
If the victim’s SIM card is not registered in a country of interest, the trojan does not take any action and stops its malicious activity. The studied modifications attack residents of the following states:
- Austria
- Italy
- France
- Thailand
- Malaysia
- Germany
- Qatar
- Poland
- Greece
- Ireland
After transmitting the number, Android.Click.322.origin waits for a command from the command and control server, which sends tasks with websites to load and JavaScript code. This code controls the clicker via JavascriptInterface, displays pop-up notifications on the device, clicks on web pages, and performs other actions.
After receiving a website address, Android.Click.322.origin opens it in an invisible WebView, where it also loads the received JavaScript code with the parameters for clicking. After opening a website with a premium service, the trojan automatically clicks on the corresponding links and buttons. Then it hooks verification codes from text messages and independently confirms the subscription.
Even though the clicker is not designed to work with text messages and has no access to them, it bypasses the restriction as follows. The trojan service monitors notifications from the default application that works with text messages. When there is an incoming message, the service hides the system notification. Then it hooks the information about the received text from the notification and transmits it to the trojan broadcast receiver. As a result, the user does not see any notifications about incoming texts and does not know what is happening. They only know about the subscription when money withdraws from their account, or if they go to the message menu and see texts related to the premium service.
Doctor Web experts have contacted Google and the detected malicious applications were removed from Google Play. All known modifications of this clicker are successfully detected and removed by Dr.Web for Android and do not pose any threat to our users.
Read more about Android.Click.322.origin
#Android, #Google_Play, #clicker, #paid_subscription

Your Android needs protection.
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 140 million downloads on Google Play alone
- Free for users of Dr.Web home products