Doctor Web’s overview of malware detected on mobile devices in August 2019
September 9, 2019
In the last month of summer, Doctor Web virus analysts detected the clicker trojan Android.Click.312.origin on Google Play built into harmless applications. We also detected additional malicious software, including the Android.DownLoader.915.origin downloader trojan and trojan adware of the Android.HiddenAds family, distributed under the guise of useful software, as well as the Android.Banker.346.origin banker.
PRINCIPAL TRENDS IN AUGUST
- Detection of new malware on Google Play
- Emergence of new adware modules
Mobile threat of the month
In early August, Doctor Web reported the Android.Click.312.origin trojan detected in 34 applications on Google Play. It was a malicious module that developers built into their software. A total of 101.7 million users downloaded the software with this trojan.
Android.Click.312.origin opened links via invisible WebView at the direction of the command and control server. It could also load websites in a browser and advertise applications on Google Play. Features of the trojan are as follows:
- it began operating 8 hours after startup;
- some features were implemented using reflection;
- it could subscribe users to premium mobile services using WAP-Click.
For more information on Android.Click.312.origin, refer to the news article on our website.
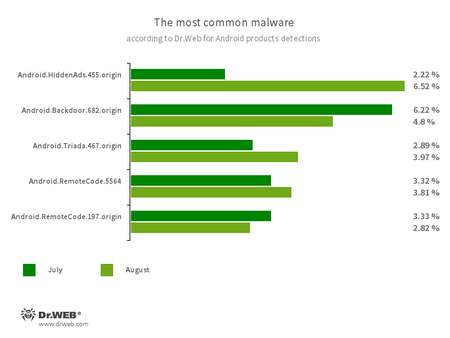
According to statistics collected by Dr.Web for Android
- Android.HiddenAds.455.origin
- A trojan designed to display unwanted ads on mobile devices.
- Android.Backdoor.682.origin
- A trojan that executes cybercriminals’ commands and helps them control infected mobile devices.
- Android.Triada.467.origin
- A multi-functional trojan that performs various malicious actions.
- Android.RemoteCode.197.origin
- Android.RemoteCode.5564
- Malicious applications designed to download and execute arbitrary code.
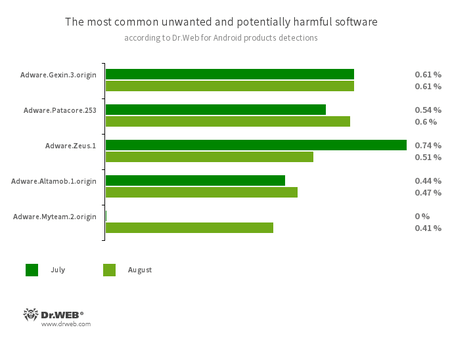
Program modules that incorporate themselves into Android applications and display obnoxious ads on mobile devices:
- Adware.Gexin.3.origin
- Adware.Patacore.253
- Adware.Zeus.1
- Adware.Altamob.1.origin
- Adware.Myteam.2.origin (a new threat)
Threats on Google Play
Along with the Android.Click.312.origin clicker, we detected the downloader trojan Android.DownLoader.915.origin among the malware on Google Play. It spread as a VPN client. It downloaded and attempted to install applications, as well as opened Instagram, Telegram, and Google Play web pages and other services specified by attackers.
Virus analysts also identified new trojan adware of the Android.HiddenAds family; for example, Android.HiddenAds.1598 and Android.HiddenAds.467.origin. Like other malicious programs of this family, they hid the software icons where they were embedded and displayed obnoxious ads.
At the end of August, Doctor Web experts discovered another banking trojan that attacked Brazilian Android users. This malware was dubbed Android.Banker.346.origin. Like similar trojans reported by our company earlier (for example, at the end of 2018), Android.Banker.346.origin uses the Android Accessibility Service to steal information from text messages, which could contain transaction confirmation codes and other confidential data. The banker also opens phishing pages at the command of cybercriminals.
To protect your Android device from malware and unwanted programs, we recommend that you install Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 140 million downloads on Google Play alone
- Free for users of Dr.Web home products