February 2019 mobile malware review from Doctor Web
March 1, 2019
The last winter month of 2019 was not a quiet time for users of Android devices. In mid-February, Doctor Web specialists found about 40 Trojans of the Android.HiddenAds family on Google Play. The cybercriminals distributed them via advertisements in popular social media and online services. In addition, owners of Android-based smartphones and tablets were targeted by the Trojans Android.FakeApp, used in fraudulent schemes, Trojan downloaders, and other malicious and unwanted applications.
PRINCIPAL TRENDS IN FEBRUARY
- The detection of new malicious programs on Google Play
Mobile threat of the month
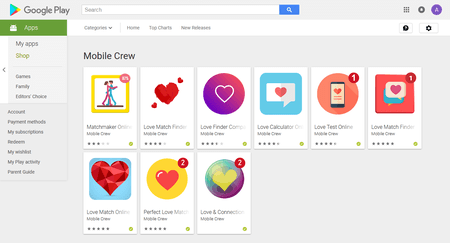
Last month, Doctor Web’s malware analysts revealed 39 Trojans of the Android.HiddenAds family on Google Play. The attackers actively advertised the Trojans on popular online services with audiences of millions, such as YouTube and WhatsApp. Cybercriminals were offering powerful photo and video editing programs; but in fact, smartphone and tablet owners installed Trojans with a small set of functions. Some 10,000,000 users fell victim to the attackers.
The Trojans were constantly displaying ads, overlaying the interface of other programs and even the operating system. As a result, infected devices became very inconvenient to work with.
For more information about these malicious applications read the news article on our website.
According to statistics collected by Dr.Web for Android
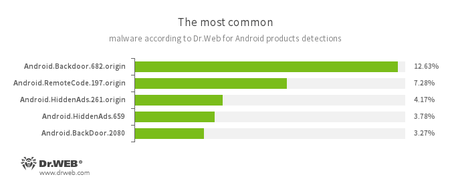
- Android.Backdoor.682.origin
- Android.Backdoor.2080
- Trojans that execute the commands of attackers and allow them to control infected mobile devices.
- Android.RemoteCode.197.origin
- A malicious application designed to download and execute arbitrary code.
- Android.HiddenAds.261.origin
- Android.HiddenAds.659
- Trojans designed to display intrusive advertisements. They are distributed as popular applications by other malicious programs, which in some cases, covertly install them in the system catalog.
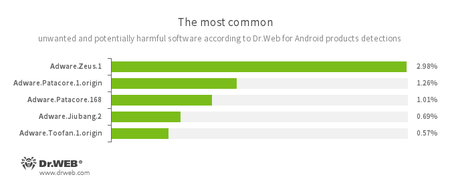
- Adware.Zeus.1
- Adware.Patacore.1.origin
- Adware.Patacore.168
- Adware.Jiubang.2
- Android.Toofan.1.origin
- Unwanted program modules that incorporate themselves into Android applications and display obnoxious ads on mobile devices.
Threats on Google Play
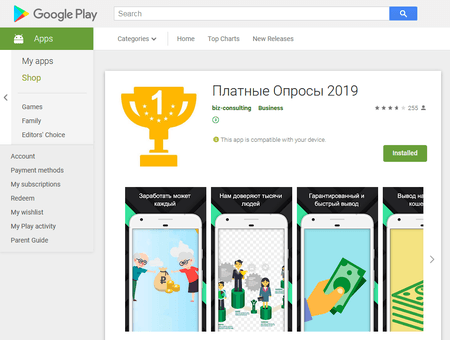
Apart from the Android.HiddenAds Trojans, other malware was found on Google Play as well, including new Trojans of the Android.FakeApp family, such as Android.FakeApp.155, Android.FakeApp.154, and Android.FakeApp.158. Cybercriminals were using them for fraud. Users were invited to install applications to take part in online polls for a large sum of cash in return. The Trojans loaded websites with those “polls” where potential victims, after answering a few simple questions, were asked to make a verification payment, supposedly needed to transfer funds to the participant. If users agreed to pay, they did not receive any reward in return.
Android users were also targeted by the Trojan Android.RemoteCode.2958, which downloaded other malware. It was distributed under the guise of benign games and applications and downloaded arbitrary code from the Internet.
Another Trojan, dubbed Android.Proxy.4, used the infected devices as proxy servers to redirect the network traffic of cybercriminals. Like other malware, it was hidden in seemingly innocuous and useful applications.
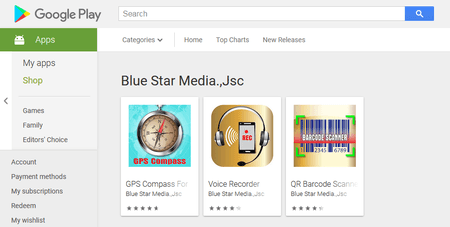
In addition, the Dr.Web virus database was updated with an entry for applications with the built-in unwanted Adware.Sharf.2 module. It was displaying ads that overlayed software windows and system interface. Doctor Web malware analysts found Adware.Sharf.2 in various programs such as a voice recorder, a GPS compass, and a QR code scanner.
Several games turned out to contain other unwanted advertising modules, dubbed Adware.Patacore.2 and Adware.Patacore.168 by Dr.Web classification. They also displayed obnoxious banners.
We continue detecting more and more malicious and unwanted applications on Google Play, so owners of mobile devices running Android are advised to only install programs from well-known and trusted developers. In all cases, pay attention to the reviews of other users. To protect smartphones and tablets, we recommend you install Dr.Web for Android.
Your Android needs protection!
Use Dr.Web
- First Russian anti-virus for Android
- Over 140 million downloads—just from Google Play!
- Available free of charge for users who purchase Dr.Web home products