Doctor Web warns: Cybercriminals spread Android Trojans via Instagram
Real-time threat news | Hot news | Threats to mobile devices | All the news
February 19, 2019
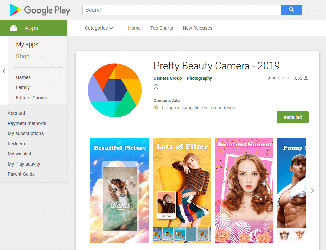
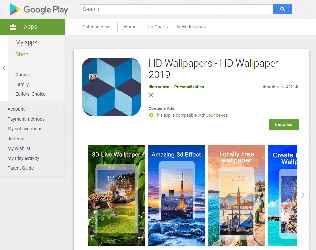
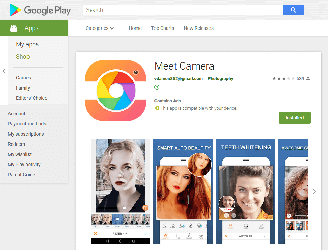
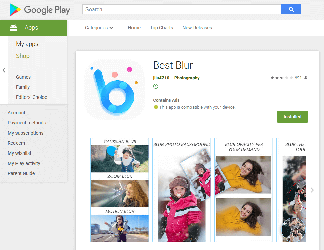
During February, malware analysts revealed 39 new modifications of the Android.HiddenAds Trojan family on Google Play. They were hidden in useful and seemingly safe programs: photography applications, image and video editors, collections of desktop wallpapers, system utilities, games, and other software. Overall, they were installed by at least 9,940,305 users. Doctor Web has notified Google of the detected Trojans, but as of the publishing date of this news, some of them were still available for downloading.
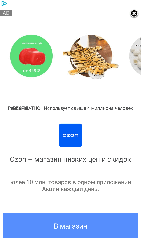
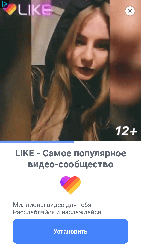
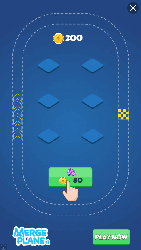
The main function of Android.HiddenAds malware is to display ads. They constantly show windows with banners and video ads that overlap other programs and the system interface, making it difficult to work with infected devices. See below an example of such an ad:
Since Trojans display banners almost continuously, cybercriminals quickly cover their expenses for promoting their software via popular online services.
To stay on smartphones and tablets for as long as possible, the Android.HiddenAds Trojans hide their icons from the list of applications on the home screen. After that, they can no longer be launched manually and also become harder to find and remove. Besides, over time, some users may forget which programs they have installed, and it also helps the Trojans ‘survive’.
Almost all malware of the Android.HiddenAds family detected in February hide their icons, too, but also create shortcuts instead. Most likely, the Trojan makers tried to divert suspicion, reducing the risk of removal for their software. Unlike icons on the home screen, shortcuts do not allow you to remove applications from the context menu. So if an inexperienced user suspects something and tries to remove the Trojan by deleting its icon, only a shortcut will be removed, while the Trojan will remain on the device and continue to work covertly and bring money to the attackers.
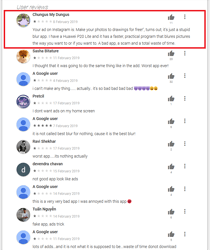
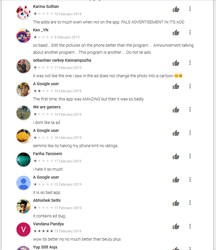
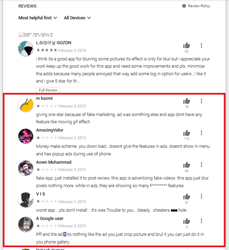
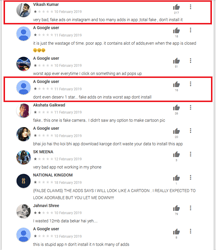
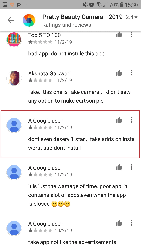
Android users installed many of these malicious applications after viewing ads on Instagram and YouTube, where the cybercriminals promised functional and powerful photo and video processing tools. At first glance, the Trojans match the description and do not arouse suspicion among potential victims. However, apart from one or several basic functions, they contain nothing of what was declared. Here is what users complain about in the reviews:
An active promotional campaign set up by the cybercriminals attracts a large number of mobile device users and increases the number of downloads. Some of these Trojans even get featured in Google Play sections promoting new products and applications gaining popularity, which also increases the number of users that download the malware.
Information about all Trojans that our experts have found as of the publication date of this material is in the summary spreadsheet. However, since cybercriminals constantly create new Android.HiddenAds malware and actively advertise it, other modifications may soon be detected.
| Application package name | Number of downloads |
|---|---|
| com.funshionstyle.ledcaller | 1 000 000+ |
| com.uniokan.pipphotoframer | 50 000+ |
| com.flextool.scanner.play | 100 000+ |
| com.flextool.superfastscanner | 100 000+ |
| com.piano.tiles.songs.black.white.game | 10 000+ |
| com.pop.stars.pop.cube | 10 000+ |
| com.mp3audio.musicplayer.fly.fun | 100 000+ |
| com.picsart.photo.editor | 50 000+ |
| com.loopshapes.infinite.puzzle | 100+ |
| com.cdtushudw.brand.logo.expert | 10 000+ |
| com.aardingw.chess.queen | 50 000+ |
| com.particle.sand.box | 100+ |
| checkers.online.classic.board.tactics | 500 000+ |
| com.wind.pics.blur.editor | 1 000 000+ |
| com.draughts.checkersnew | 50 000+ |
| com.watermark.zooms.camera | 10 000+ |
| com.photo.cut.out.studio | 1 000 000+ |
| com.camera.easy.photo.beauty | 100 000+ |
| com.camera.easy.photo.beauty.Pro | 10 000+ |
| com.soon.ygy.photograph.camera | 500 000+ |
| com.music.play.hi.cloud | 500 000+ |
| com.scanfactory.smartscan | 100 000+ |
| com.personalife.hdwallpaper | 10 000+ |
| com.smartmob.minicleaner | 100 000+ |
| com.beautylife.livepipcamera | 100 000+ |
| com.callcolorshow.callflash | 10 000+ |
| com.mobwontools.pixel.blur.cam | 1 000 000+ |
| com.video.nin.cut.face | 100 000+ |
| com.magicvcam.meet.photograph | 100 000+ |
| com.best.blur.editor.photo | 100,000+ |
| com.autocleaner.supercleaner | 10 000+ |
| com.wallpapers.project.hd.hd3d.best.live | 10 000+ |
| com.camera.selfie.beauty.candy.cam | 5+ |
| com.wallpaper.hd3d.hd.lock.screen.best3d.best | 50 000+ |
| com.selfie.beauty.candy.camera.pro | 1 000 000+ |
| com.cam.air.crush | 1 000 000+ |
| com.fancy.photo.blur.editor | 1 000 000+ |
| com.photoeditor.background.change | 100 000+ |
| com.eraser.ygycamera.background | 100 000+ |
Users are advised to perform a full scan of mobile devices with Dr.Web for Android and remove the Trojans that are detected.
Users of smartphones and tablets should be wary of ads on the Internet and avoid downloading all advertised software, even if it is distributed via Google Play. Only install applications from trusted developers and pay attention to the reviews from other users.
#Android, #fraud, #Google_Play, #Trojan