Doctor Web’s overview of malware detected on mobile devices in December 2016
December 26, 2016
The past month was quite eventful in terms of mobile security. The month began with an Android Trojan that infected system libraries, injected itself into application processes, and then covertly downloaded and installed various software. Later, Doctor Web’s security researchers detected malware programs which were preinstalled into dozens models of Android devices and covertly installed unwanted applications.
Principal trends of December
- The emergence of Android application infecting system libraries and performing injections into application processes;
- Detection of malware programs preinstalled on numerous Android devices.
Mobile threat of the month
At the beginning of December, Doctor Web detected Android.Loki.16.origin that covertly downloaded and installed software on mobile devices. This Trojan tried to get root privileges by using exploits and then copied several additional modules into system catalogs. The modules allowed the Trojan to infect system libraries and to launch itself together with the modules, obtaning the root privileges. As a result, Android.Loki.16.origin could download, install, and remove applications without user knowledge. For more details about this incident, refer to the news article.
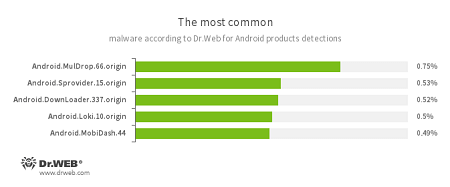
According to statistics collected by Dr.Web for Android
- Android.MulDrop.66.origin
A Trojan that distributes and installs other malicious programs on Android devices. - Android.Sprovider.15.origin
A Trojan that downloads and installs various applications. In addition, it can show advertisements. - Android.DownLoader.337.origin
A Trojan designed to download other malware applications. - Android.Loki.10.origin
A Trojan designed to download other malware applications. - Android.MobiDash.44
A Trojan that delivers annoying advertisements.
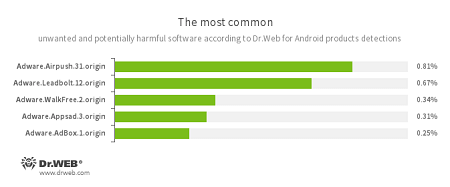
- Adware.Airpush.31.origin
- Adware.Leadbolt.12.origin
- Adware.WalkFree.1.origin
- Adware.Appsad.3.origin
- Adware.AdBox.1.origin
An unwanted program module that is incorporated into Android applications and is responsible for displaying annoying ads on mobile devices.
Firmware Trojans
In mid-December, Doctor Web’s specialists found several Trojans incorporated into the firmware of dozens of Android mobile devices models. One of them, dubbed Android.DownLoader.473.origin, covertly downloaded and installed software—for example, the unwanted application Adware.AdBox.1.origin that displayed advertisements. Another Trojan, added to the virus database as Android.Sprovider.7, also downloaded applications and tried to install them. In addition, it opened various web pages in a browser, made phone calls, and showed advertisements. For more information about these Trojans, refer to the corresponding news article.
Cybercriminals actively continue contriving various methods to infect mobile devices—they even began to inject Trojans into devices’ firmware. Thus, consumers are under the risk to buy an infected device. To detect preinstalled malware programs, Android users should install Dr.Web for Android. If the Trojan is detected in the system catalogs, it is recommended that you contact the technical support service and ask for the system update to neutralize the threat.