Mobile threats in August 2014
Virus reviews | Threats to mobile devices | All the news
September 1, 2014
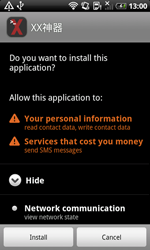
In early August security researchers discovered another attack targeting Chinese Android handhelds that aimed at acquiring confidential information and sending SMS without user consent. To achieve their objectives, criminals unleashed the malicious program Android.SmsSend.1404.origin which immediately performed several tasks. In particular after its launch, the malware would check whether another malignant application (Android.SmsBot.146.origin, as classified by Doctor Web) is installed on the device. If the app was not found, it would prompt the user to install it as a certain important software update.
 |
 |
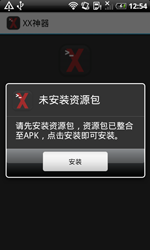 |
After that, Android.SmsSend.1404.origin would prompt users to submit their confidential information in a special web form and transmit the data to criminals. In addition, the Trojan covertly sends an SMS message with its download link to all the contacts found in the device's phone book, thus facilitating its further distribution.
 |
 |
The program installed by the malware is a common bot application that executes instructions it receives from criminals. In particular, the bot can send SMS and intercept all incoming short messages.
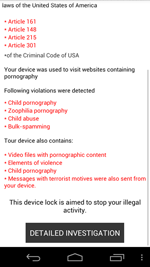
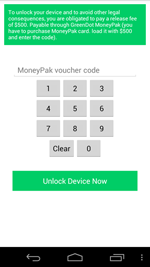
Also in the past month, incidents occurred that involved Android.Locker programs which interfere with normal use of infected devices. Android.Locker.27.origin, about which Doctor Web previously issued a report, emerged as one of the most notable threats of this kind. This malicious program is distributed in the guise of an anti-virus, and like other ransomware, it locks Android-powered devices and demands a ransom to unlock them. However, thanks to its faulty payment verification mechanism, users whose devices were compromised by the extortionist could get rid of this nuisance threat completely for free. In particular, Android.Locker.27.origin would verify that the entered payment code was 14 digits long and that it did not contain certain numerical combinations. If these conditions were satisfied, the malware would remove the lock and uninstall itself.
 |
 |
 |
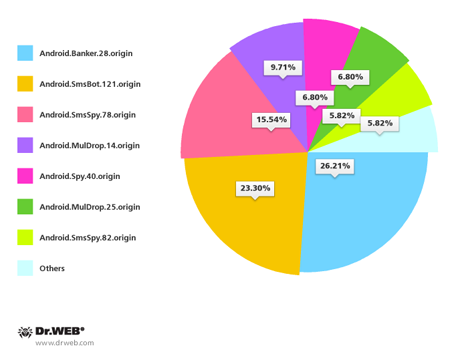
August also had its share of Android malware for South Korean handhelds. As before, the programs were mostly distributed with unwanted bulk SMS messages released by criminals. Doctor Web registered more than 100 of these spam campaigns. The most common malicious applications distributed by means of short messages included Android.Banker.28.origin (26.21%), Android.SmsBot.121.origin (23.30%), Android.SmsSpy.78.origin (15.54%) and Android.MulDrop.14.origin (9.71%).
In spite of SMS spam being the most common method for distributing Android malware, malware makers also resort to other delivery methods. For example, last month download links for the dangerous program Android.Backdoor.96.origin were sent to users via email. This program is a backdoor that spreads in the guise of an anti-virus and can execute the various instructions it receives from criminals.
 |
 |
In particular, it can steal confidential information such as SMS, contacts, browsing history and GPS coordinates. It can also toggle on the microphone, send USSD queries, display various messages and record all calls into audio files for forwarding to a remote server along with other acquired data.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live