New Android ransomware unlocks devices free of charge
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
August 6, 2014
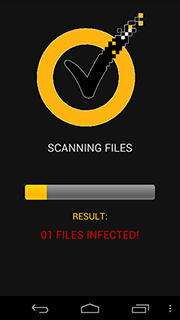
The new locker Trojan, dubbed Android.Locker.27.origin by Dr.Web, is spread under the guise of an anti-virus. When launched, it displays a file scan progress bar and after a while supposedly detects malicious programs.
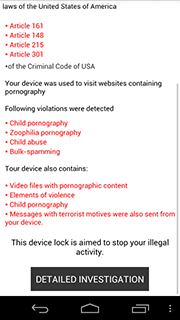
After that, the malware requests administrator privileges, locks the device regardless of what actions the user takes and displays a warning about some violation of law.

|
 |
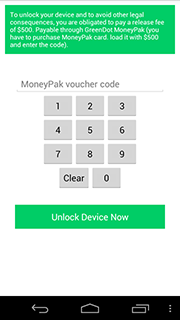
To unlock the device and get the charges dropped, the user has to pay a $500 ransom by loading a GreenDot MoneyPak card with the demanded amount and providing the fraudsters with the card number.
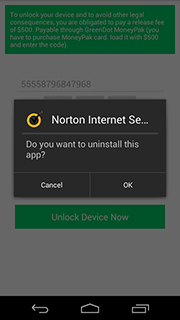
The main difference between Android.Locker.27.origin and other similar malware is the payment verification procedure. In particular, the Trojan makes sure that the entered number consists of 14 digits, and does not contain the most predictable combinations like "00000", "11111", "22222", etc., on up to "99999", as well as a sequence like "12345". If these requirements are met, the Trojan forwards the card number to the attackers' server, unlocks the device and initiates its own removal. Thus, affected users can easily—and completely for free—rid themselves of this very unpleasant threat by entering almost any combination of 14 digits.
Unlike this harmless locker Trojan, many similar programs are far less friendly and can cause more serious problems. Therefore, Doctor Web recommends that users protect their devices with reliable anti-virus software.