Doctor Web virus activity review: Macs and Linux under attack again
Virus reviews | All the news
December 1, 2014
Viruses
According to statistics collected with Dr.Web CureIt!, in November 2014, the advertising Trojan programs Trojan.BPlug.123, Trojan.BPlug.100 , Trojan.Packed.24524 and Trojan.BPlug.48 were most frequently detected on PCs—together, they make up 8.7% of the malware identified. Other dangerous applications are far behind in the detection rankings.
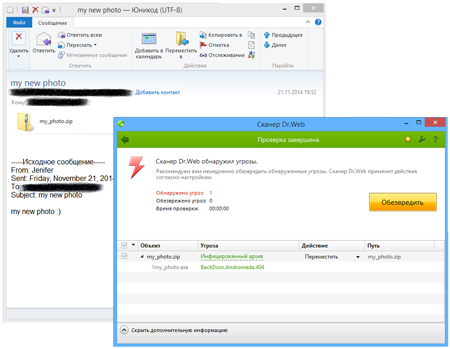
However, Doctor Web's statistics servers show a slightly different picture: Trojan.InstallCore.12, which installs different adware, toolbars and browser extensions that are commonly used by developers to generate profit from all sorts of dubious programs, ranks first. BackDoor.Andromeda.404, which downloads other malicious programs into an infected system when commanded to do so by intruders, ranks second. In November, cybercriminals distributed this malware in large quantities via email. In particular, they used emails with the subject line "my new photo", and the backdoor was concealed in the attached file my_photo.zip
Trojan.InstallMonster.1017 ranks third among the Trojans identified in November—this malignant application is spread by criminals under various referral programmes. Also discovered in the last month of autumn were Trojans from the Trojan.Bayanker, Trojan.MulDrop, Trojan.LoadMoney and Trojan.Zadved families.
In November, BackDoor.Andromeda.404 was by far the Trojan most frequently discovered in email traffic; as previously mentioned, in mid-November criminals sent a mass spam email containing this backdoor. It accounted for 2.4% of the malware detected. Its close relative BackDoor.Andromeda.559 ranked second. The third and fourth positions were taken by Trojan.Download programs. The “Top 10” also includes applications that steal confidential information—Trojan.PWS.Panda and Trojan.PWS.Stealer programs.
The botnets monitored by Doctor Web security researchers didn't undergo any significant changes in the past month. The one created by hackers using the file infector Win32.Rmnet.12 (two of its subnets are controlled by Doctor Web's virus analysts) is still operational. In the first subnet, an average of 278,400 infected hosts contacted command and control (C&C) servers on a daily basis, while in the second one, around 394,000 infected machines were active. The botnet comprised of computers compromised by another file infector—Win32.Sector—shrank slightly in November. Roughly 50,300 nodes per day were active in it. The number of machines running Mac OS X and infected with BackDoor.Flashback.39 also declined slightly, reaching 13,250.
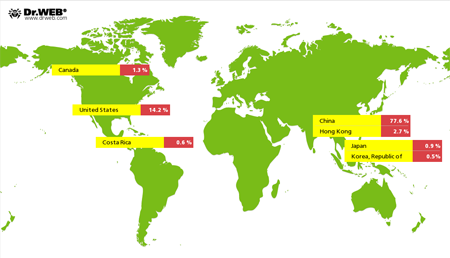
In June 2014, Doctor Web issued a report about Linux.BackDoor.Gates.5–a program designed to mount DDoS attacks on web servers and capable of infecting 32-bit versions of Linux. This malware was rather active in November. Within just that one month, security researchers registered 3,713 unique IP addresses as having been attacked by this backdoor. Their geographic distribution is illustrated in the figure below:
Other events in November
Definitions for several programs targeting Mac OS X were added to the Dr.Web virus database. In particular, in early November Doctor Web's researchers examined the program Mac.BackDoor.Ventir.2—this backdoor can execute commands from a remote server, log key strokes and relay information to criminals. Another backdoor for Mac OS X— Mac.BackDoor.Tsunami—is a Mac OS X port of the Linux backdoor known as Linux.BackDoor.Tsunami. Criminals control this program via the IRC (Internet Relay Chat) protocol. Yet another backdoor for Mac OS X (also exposed in November) was named Mac.BackDoor.WireLurker.1—unlike many programs of its kind, this malware waits for the moment when an iOS device is connected to an infected Mac and uploads its files onto the device. There are two versions of these files: one of them is intended for jailbroken devices, while the other is intended for unaltered iOS devices. As soon as an iOS device connects to an infected Mac via USB, Mac.BackDoor.WireLurker.1 uses an Apple digital certificate to install a compromised application onto the target device. To accomplish this task, the backdoor takes advantage of the “enterprise provisioning” feature that enables companies to bypass the AppStore and install applications onto its employees’ devices.
Neither did attackers disregard Linux: in November Doctor Web warned users against the dangerous backdoor application Linux.BackDoor.Fgt.1, which was targeting all sorts of devices running various versions of this OS. There are versions of Linux.BackDoor.Fgt.1 that are tailored for particular Linux distributions. This backdoor was designed to mount DDoS attacks. To spread to other devices, Linux.BackDoor.Fgt.1 scans random IP addresses on the Internet and launches a brute force attack in an attempt to establish a Telnet connection with their nodes. If successful, it commands the attacked host to download a special script. The script is used to download and launch Linux.BackDoor.Fgt.1 on the compromised machine. It is noteworthy that the C&C server stores a large number of Linux.BackDoor.Fgt.1 executable files compiled for different Linux versions and distributions, including MIPS and SPARC server ports. Thus, the backdoor can infect not only Internet-connected servers and PCs running Linux, but also other devices, such as routers. More information about this malicious program can be found in a corresponding review published by Doctor Web on its site.
Windows machines were also in danger of getting infected with various malicious programs. In particular, many media outlets reported the discovery of a dangerous Trojan dubbed Trojan.Regin under the Dr.Web classification system. In the past month, security researchers discovered several modifications of this malware, and the corresponding entries were promptly added into the virus databases.
In November, Doctor Web researched another backdoor for Windows—Backdoor.OnionDuku.1. It is noteworthy that attackers are using this malware to infect executable files transferred over their TOR network node. Thus, if their traffic is transmitted via a malicious network node, users can get their systems infected simply by using the TOR-browser and downloading executable files from various sources with it.
However, there is good news for Windows users, too. In November, Doctor Web completed a research project that enabled its security researchers to decrypt files affected by the encryption ransomware Trojan.Encoder.398. This malicious program encrypts various types of files and usually offers the following email addresses for communicating with the intruders: mrcrtools@aol.com, back_files@aol.com, backyourfile@aol.com, vernut2014@qq.com, yourfiles2014@yahoo.com, restorefiles2014@yahoo.fr, and filescrypt2014@foxmail.com.
Malicious programs for Android
In November, Doctor Web registered a large number of various malicious programs for Android, a large portion of which was comprised of banking Trojans that stole money from accounts associated with the compromised devices.
Android.BankBot.33.origin was one such program. This malware can covertly steal money from Russian customers of financial institutions who use mobile banking. Android.BankBot.33.origin uses SMS commands to covertly transfer money to the intruders’ account and hide SMS replies from the bank, so that the user won't notice unauthorised transactions. It can also load a bogus web page in the browser to lure users into submitting their online banking credentials.
Android.BankBot.34.origin bears a similar payload. In addition to the ability to steal money from bank accounts, the malware can also acquire logins and passwords stored by a number of popular applications, and gather information about the phone number and credit card associated with a compromised device. You can find more information about Android.BankBot.34.origin in a corresponding publication on Doctor Web's site.
 |  |
Discovered in mid-November, Android.Wormle.1.origin turned out to be another malicious program that could steal money from bank accounts accessed from Android-powered devices. Android.Wormle.1.origin could not just steal money from its victims, but could also perform other unwanted actions as directed by the intruders. For example, it could steal confidential information, download various applications onto a compromised device and remove certain files from the SD card. More detailed information about this threat can be found in a review published by Doctor Web.
In November, handhelds in Brazil were attacked by banking malware. Android.Banker.127 and Android.Banker.128, which were spread via Google Play, were designed to steal login data from customers of Brazilian banks. To accomplish this, they displayed a fraudulent web page where victims were prompted to enter their bank account logins and passwords.
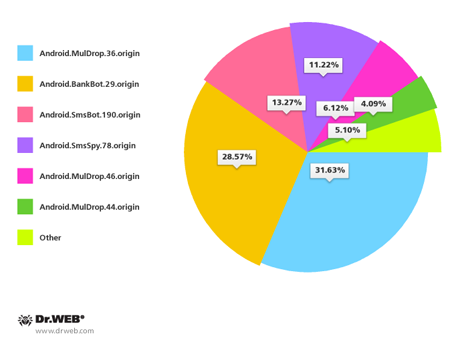
November didn't pass without incident in South Korea either. This past month, Doctor Web registered roughly 100 spam campaigns spreading malicious applications for Android. Most of the programs distributed were various versions of banking Trojans. Android.BankBot.29.origin, Android.MulDrop.36.origin, Android.SmsBot.190.origin and Android.SmsSpy.78.origin were the most common.
In addition to a large quantity of different banking Trojans, many other malicious applications for Android were discovered in November. One of them was the Trojan Android.Becu.1.origin. Discovered by Doctor Web's security researchers, this program is interesting in that it was incorporated into the Android firmware used on a large number of inexpensive Android handhelds. Android.Becu.1.origin can download, install, and remove programs without user consent and block inbound short messages from specified numbers. More information about this malicious program can be found in a related news publication.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live