May 18, 2012
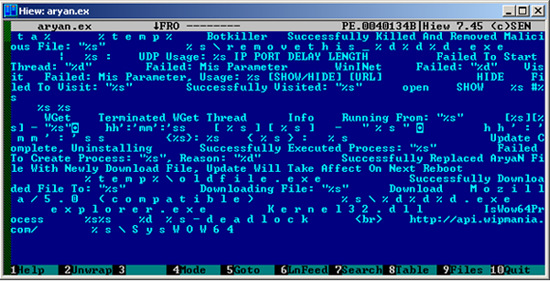
The malicious application BackDoor.IRC.Aryan.1 can be classified as an IRC bot. It spreads by copying itself to removable drives: the program creates its folder and the autorun.inf file in the infected drive's root directory. IRC.Aryan.1 also uses another method to infect removable data storage devices. It copies itself onto the disk, hides files found on the media into a folder, and replaces them with shortcuts linked to the hidden files as well as to the bot's copy. As a result, when the user double-clicks on such a shortcut, it doesn't merely opens the desired file but also runs BackDoor.IRC.Aryan.1. Once the disk is infected successfully, the bot notifies criminals via their IRC channel .
Then the malignant application copies itself as the svmhost.exe file into a folder and puts a link to this file into the registry branch responsible for launching applications automatically upon Windows startup. Also, the bot tries to inject its code into the process explorer.exe.
Among other features, BackDoor.IRC.Aryan.1 has a self-defense mechanism. It uses a separate thread to continuously check whether its file is present on the disk, and if the file is not found in the destination folder, it will save it again from memory to the disk. At the same time, it verifies whether its entry is found in the Windows Registry. In addition, BackDoor.IRC.Aryan.1 attempts to inject the code that would repeatedly restart the malicious program into the processes csrss.exe, alg.exe, and dwm.exe.
BackDoor.IRC.Aryan.1 can download various executable files from a remote server, run them on the infected computer, and carry out DDoS-attacks upon command. The program's signature has been added to the Dr.Web virus databases. Doctor Web also advises users to exercise caution when working with removable storage devices and, if possible, disable the AutoRun feature in the operating system’s settings.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments