New backdoor threatens Mac OS
Real-time threat news
October 3, 2011
BackDoor.Flashback is a fourth known backdoor program for Mac OS. However, unlike its predecessors such as BackDoor.Olyx it has complex architecture and incorporates a variety of features. Besides, it is the first malware of this kind for Mac OS that spreads on such a wide scale and implements a sophisticated scheme to spread and maintain bots.
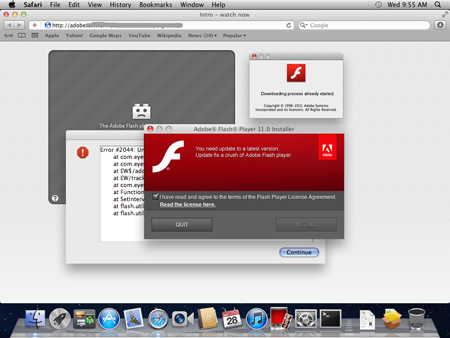
BackDoor.Flashback’s installer is disguised as an Adobe Flash Player installer. When a user visits a site distributing malicious software, a flash player error message appears on the screen and then the user is prompted to upgrade their Adobe Flash software.
If they agree to update, a chain of redirections brings up a prompt to download and install an archive containing the FlashPlayer-11-macos.pkg file (this file is downloaded only if the target operating system is Mac OS X Lion). Then the 'player' installation starts. When it is completed, the package is deleted and instead the main malicious component Preferences dylib is installed into /Library/Preferences/. It performs backdoor tasks in the system and executes commands received from numerous remote control centers.
It is also worth mentioning that the backdoor can receive additional commands from the mobile.twitter.com server.
The main malicious library Preferences.dylib won't be used to perform malicious tasks if one of the following files is found in the system:
/Library/Little Snitch/lsd
/Applications/VirusBarrier X6.app/Contents/MacOS/VirusBarrier X6
/Applications/iAntiVirus/iAntiVirus.app/Contents/MacOS/iAntiVirus
/Applications/avast!.app/Contents/MacOS/avast!
/Applications/ClamXav.app/Contents/MacOS/ClamXav
/Applications/HTTPScoop.app/Contents/MacOS/HTTPScoop
/Applications/Packet Peeper.app/Contents/MacOS/Packet Peeper.app
The main task performed by means of Preferences.dylib is implementation of various directives received from a remote command center or contained in the configuration file (for example, a command to embed JavaScript code into a web-page viewed by the user). In addition, the library also can be used to execute any standard shell command.
To prevent getting ifnected by BackDoor.Flashback Doctor Web recommends Mac OS X users to download Flash updates only from Adobe Software official web-site and disable auto-hiding downloaded files in the browser settings. The signature of this threat has been added into the virus databases of Dr.Web for Mac OS X.