New backdoor found new way to use TeamViewer
Real-time threat news | Hot news | All the news | Virus alerts
May 25, 2016
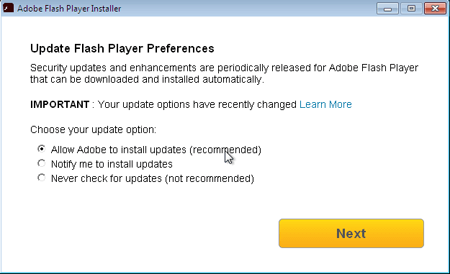
To spread BackDoor.TeamViewer.49, virus makers use another malicious application named Trojan.MulDrop6.39120, which is, in fact, a bogus update of Adobe Flash Player. The executable file of Trojan.MulDrop6.39120 installs the player on Windows. Meanwhile, it covertly saves TeamViewer, BackDoor.TeamViewer.49, and a necessary configuration file on the disc. During the installation, a legitimate installer window of Flash Player is displayed.
As a rule, Trojans use TeamViewer to get access to the user’s computer. Yet, in this case, TeamViewer plays another role: BackDoor.TeamViewer.49 uses different internal functions of the program’s process. In addition, once launched, TeamViewer usually automatically locates the avicap32.dll library to the memory, which appears to be very convenient for virus makers: they locate a malicious library with the same name in the folder to which Trojan.MulDrop6.39120 saves the application. Therefore, the library is automatically loaded to the memory at launch of TeamViewer.
Once TeamViewer is launched, BackDoor.TeamViewer.49 removes its icon from the Windows notification area and disables error reporting. The Trojan also implements a special mechanism intended to prevent it from being restarted on the infected computer. Parameters necessary for correct operation of BackDoor.TeamViewer.49 are stored in the configuration file.
BackDoor.TeamViewer.49 registers itself in autorun and then, operating in infinite loop but with specified time intervals, assigns the folder, which contains its executable file, the malicious library and the configuration file, with the “hidden” and “system” attributes. If it fails to assign these attributes, the Trojan starts removing all the TeamViewer keys from the system registry.
What is more, there is another encrypted library that is hard-coded in the Trojan's body and is responsible for performing malicious activity of BackDoor.TeamViewer.49. The library contains a specially generated array that represents names of the servers from which instructions can be delivered. All information sent and received is encrypted.
The malicious program can execute several commands. Yet, its main functions are to establish connection to the server (including authorization to it) and to redirect traffic from the server to the specified remote server via the infected computer. Thus, cybercriminals can remain anonymous on the Web while connecting to remote servers using the computer like via a proxy server.
Dr.Web Anti-virus detects and removes Trojan.MulDrop6.39120 and BackDoor.TeamViewer.49. Therefore, they do not pose any thereat to our users.
Doctor Web specialists would like to thank Yandex for providing the Trojan’s sample for research.