New Trojan for Linux infects routers
Real-time threat news | Hot news | All the news | Virus alerts
August 4, 2015
The Trojan's distribution scheme makes it rather unique—Doctor Web analysts presume that initially Linux.PNScan.1 was installed on attacked routers by virus makers themselves. For that, they exploited the ShellShock vulnerability running a script with corresponding settings. Subsequently, the malware got uploaded and installed on devices by Trojans belonging to the Linux.BackDoor.Tsunami family, which, in turn, are distributed using Linux.PNScan.1. This malicious program serves the only purpose—to brute-force router access passwords. If the hacking attempt is successful, the Trojan uploads a malicious script that downloads and installs backdoors based on the router architecture (ARM, MIPS, or PowerPC). The script can also download a relevant backdoor if by exploiting the Shellshock vulnerability cybercriminals succeed to hack an Intel computer (x86).
Once launched, Linux.PNScan.1 receives operating parameters that determine the attack type and the range of IP addresses to scan. During attacks, the Trojan exploits RCE vulnerabilities to run a corresponding SH script; that is, to mount an attack on Linksys routers, the malicious program exploits a vulnerability in HNAP (Home Network Administration Protocol) and the CVE-2013-2678 vulnerability. The malware also tries to crack a login and password combination using a special dictionary. Moreover, ShellShock (CVE-2014-6271) and a vulnerability in the Fritz!Box routers' subsystem of remote command call can be exploited by Linux.PNScan.1 in the same way.
Malicious applications uploaded by Linux.PNScan.1 to the infected device are detected by Dr.Web as Linux.BackDoor.Tsunami.133 and Linux.BackDoor.Tsunami.144. Once these programs penetrate the compromised router, they register themselves in its autorun list. After that, they retrieve a command and control server address from the list and establish a connection to this server via IRC. These backdoors are multicomponent programs that can launch various DDoS attacks (including ACK Flood, SYN Flood , and UDP Flood) and execute intruder-issued commands. For example, upon a command from cybercriminals, the applications can download Tool.Linux.BrutePma.1. This tool is used to hack administrative control panel of PHPMyAdmin which is used to manage relational databases. Once launched, this script receives data on IP range and two files; one of these files has a dictionary with login:password pairs, while another file contains the path to the administrative panel of PMA.
A Trojan named Linux.BackDoor.Tsunami.150 and designed to mount DDoS attacks and perform other malicious actions is also distributed by means of commands issued by cybercriminals. This backdoor can be used to brute-force remote node access passwords via SSH. If such a hacking attempt is successful, depending on the attack type, Linux.BackDoor.Tsunami.150 can either execute a script to download Linux.BackDoor.Tsunami.133 or Linux.BackDoor.Tsunami.144 or gather information on the OS of the device. Actually, with the help of backdoors belonging to the Linux.BackDoor.Tsunami family, any Trojan can be uploaded to the compromised device.
Moreover, Doctor Web security researchers also detected another modification of Linux.PNScan.1 that was added to Dr.Web virus databases as Linux.PNScan.2. Unlike its predecessor, this particular version does not exploit vulnerabilities but use standard passwords to get unauthorized access to remote devices. The Trojan generates a list of IP addresses and tries to connect to them via SSH using one of the following combinations: root;root; admin;admin; or ubnt;ubnt. If the connection is established, the Trojan plants into the “/tmp/.xs/” folder of the compromised device a set of files (depending on the router model, different sets of files are used for ARM, MIPS, MIPSEL, and x86) and runs them. Periodically, Linux.PNScan.2 scans devices from the list to check whether they are still infected. If some device is cured, the Trojan infects it once again.
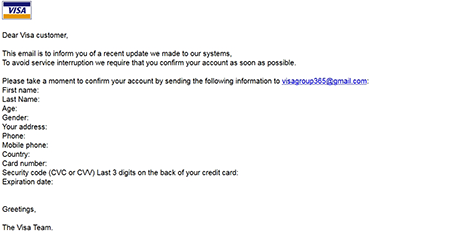
On the server used by cybercriminals, Doctor Web analysts detected other malicious programs, among which is a Trojan named Trojan.Mbot whose main purpose is to hack websites created on WordPress and Joomla platforms and also websites that use such online-store management system as osCommerce. Another detected Trojan was dubbed Perl.Ircbot.13. It serves the purpose of looking for vulnerabilities in websites created on WordPress, Joomla, e107, and WHMCS platforms and in websites which use such online-store management systems as Zen Cart and osCommerce. Hacked websites were used as proxy servers and to distribute tools employed by cybercriminals for attacks. Doctor Web security researchers also detected a malicious program named Tool.Linux.BruteSmtp.1 and designed to brute-force SMTP servers. Moreover, an application for conducting mass spam mailings fell under the scrutiny of Doctor Web analysts. The malware dubbed Perl.Spambot.2 was used for phishing messages that were allegedly sent from VISA.
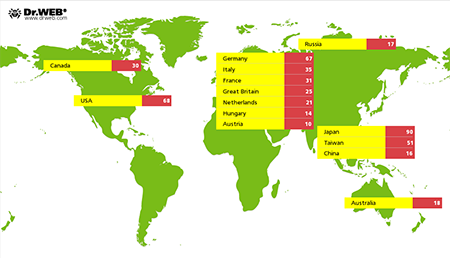
1,439 devices are known to be infected with the mentioned malicious programs; at that, in 649 cases, geographical location of infected devices was also determined—while the majority of incidents took place in Japan, considerable number of users in Germany, the USA, and Taiwan also suffered from such attacks. Detailed information on locations of hacked devices is presented in the following picture:
Signatures of these malicious programs have been added to Dr.Web virus databases for Linux.