SMS spam and Android Trojans in South Korea: Doctor Web mobile security review for the second quarter of 2014
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
July 23, 2014
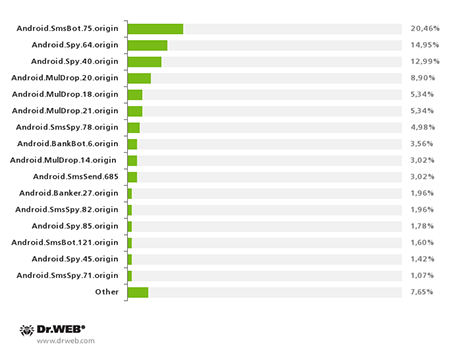
Android.SmsBot.75.origin, whose mass distribution got underway in April, is one of the most remarkable malware species currently targeting devices in South Korea. According to Doctor Web's statistics, within several days attackers dispatched around 40 mass SMS mailings to deliver this Trojan download link. The actual number of compromised devices could reach the tens of thousands. After three months Android.SmsBot.75.origin became the most widespread Trojan in South Korea, accounting for 20.46% of the incidents involving download links being distributed by SMS spam.
Once launched on a mobile device, this Trojan steals information from the phonebook and uploads its contents to a remote server, and then waits for commands containing the parameters needed to send SMS messages, e.g. the recipient's number and the text to be used. These features can particularly be used to steal money from user bank accounts that are accessed from mobile devices. To conceal its illegal activities, Android.SmsBot.75.origin blocks certain calls and short messages that can be sent by banks to confirm transactions. Thus, this malware can pose a substantial risk to the financial well-being of users. Read more about this Trojan in the review on Doctor Web's site.
Warranting no less attention is Android.Banker.28.origin, another banking Trojan that is equipped with a wider array of features. Like many similar malware programs, Android.Banker.28.origin spreads as a Google Play client application and requests administrator privileges with the goal of complicating its removal. To lull the user, the Trojan shows an error message and mimics its removal, after which it begins its covert activity.
In particular, Android.Banker.28.origin steals confidential information (including SMS messages, the user’s phone number, and bank security certificates stored on the memory card) and tries to gain access to any bank accounts involved in transactions via the device. To accomplish this task, it searches for applications from South Korean financial institutions, and when such applications are launched, the Trojan replaces their interface with a fake one and prompts the user to submit their authentication information which is subsequently forwarded to the criminals. This is a different method from the one used in similar banking Trojans that remove legitimate applications and replace them with fake copies.
To perform its malicious functions, the Trojan can run up to seven system services, some of which are activated by commands issued by the intruders. Another distinctive feature of Android.Banker.28.origin is its ability to send via SMS a download link leading to its copy to all the contacts in the phone book. Thus the number of handsets infected with this malware can increase manifold in a very short period of time. In addition, Android.Banker.28.origin tries to find the anti-virus applications that are popular in South Korea and remove them.
The most common Trojans for Android that were distributed with SMS spam in South Korea during the second quarter of 2014 are presented in the following diagram.
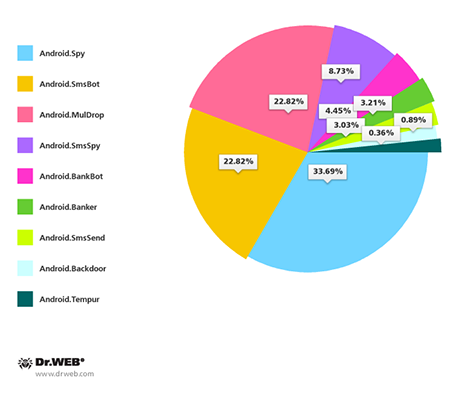
All in all, according to Doctor Web's security researchers, the Android malware spreading in South Korea belongs to the following families: Android.BankBot, Android.SmsBot, Android.Backdoor, Android.MulDrop, Android.Banker, Android.SmsSpy, Android.Spy, Android.SmsSend and Android.Tempur. Their percentage distribution, according to the number of representatives discovered, is shown in the pie chart below.
As the chart indicates, Android.Spy, Android.SmsBot and Android.MulDrop were found in the most abundance. They account for almost 80% of all the malicious applications detected. Other malware families account for a far smaller number of discovered malicious species: Android.SmsSpy —8.73%, Android.BankBot —4.45%, Android.Banker —3.21%, Android.SmsSend —3.03%, Android.Backdoor —0.89%, Android.Tempur —0.36%.
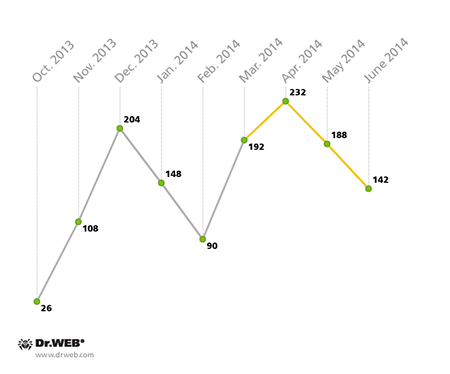
According to statistics, over the past three months, 562 SMS spam incidents involving Trojan download links were registered in South Korea. This is a 30.7% increase over the previous quarter. The largest number of such cases (232) was observed in April, after which there was a decline in their intensity: 188 and 142 incidents were registered in May and June, respectively. The chart below shows how the number of incidents fluctuated throughout the reported period.
In most unwanted messages, criminals resorted to their usual tricks. As before, they typically used fake postal delivery status notifications to try to mislead users. They also issued warnings to users about their alleged legal violations and the impending dire consequences awaiting them, as well as fake civil defence exercise alerts. The spam also included invitations and important messages made to appear as if they were from the user’s bank or mobile carrier.
Topics of fake short messages used to spread malware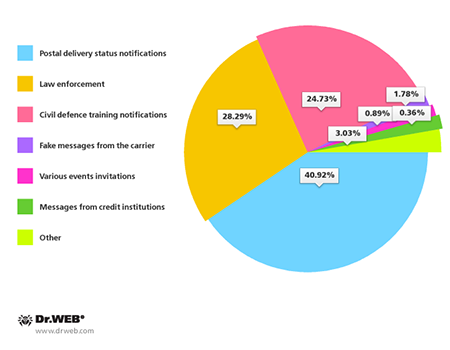
In 80.25% of the cases, URL shortening services were used to disguise the malicious download links found in the messages. Criminals used 49 such services, the most popular being goo.gl, asd.so, url.kr, grep.kr, me2.do and oze.kr.
The most popular URL shortening services used by criminals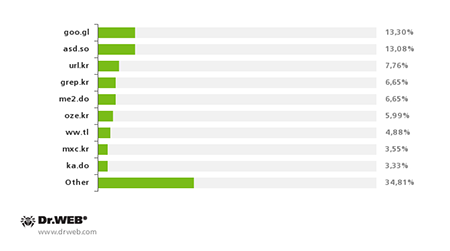
Cybercriminals targeting devices in South Korea still prefer to use file sharing services to host Trojan distributions: this method was used to spread 83.45% of the detected malware. Above all, criminals preferred the Dropbox and Box services (74.91% and 8.18%, respectively). At the same time, criminals are also hosting malicious applications on their own websites. At the beginning of the year, the number of these applications was in decline, but in the last three months, the trend has reversed.
Sites used by criminals to host malicious applications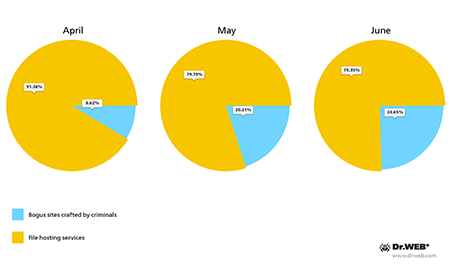
Online file hosting services involved in spreading Android malware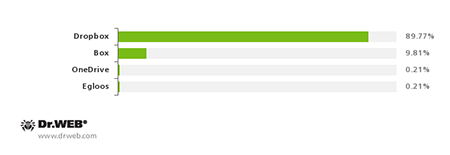
The growing number of attacks on Android handhelds in South Korea shows that criminals are showing great interest in the country's mobile market. The overwhelming majority of malicious applications spread by intruders—96% of the total—could be used to steal sensitive information including user names, passwords, and other data used to access bank accounts. At the same time, 31% of the Trojans for Android could be used to gain control over infected mobile devices and perform various actions on them, and 26% of these Trojans could send short messages without user consent.
The increasing interest in the South Korean mobile market on the part of cyber criminals reflects a global trend toward increased risks for transactions carried out via mobile devices. Therefore, to protect themselves against possible attacks, Android users should exercise caution and use up-to-date anti-virus software.