May 2014 virus activity review from Doctor Web
Virus reviews | Hot news | All the news | Virus alerts
June 5, 2014
Viruses
According to statistics collected with Dr.Web CureIt!, Trojan.Packed.24524, which installs unwanted and potentially dangerous programs, was the most common threat of the past month. Trojan.BPlug.48, a browser plugin, ranked second, and the advertising malware Trojan.InstallMonster.51 ranked third. The top twenty most common malicious programs discovered on computers using Dr.Web CureIt! in May 2014 are listed in the table below:
| Name | Qty | % |
|---|---|---|
| Trojan.Packed.24524 | 79800 | 6.15 |
| Trojan.BPlug.48 | 40224 | 3.10 |
| Trojan.InstallMonster.51 | 36990 | 2.85 |
| Trojan.BPlug.28 | 34587 | 2.67 |
| Trojan.BPlug.47 | 29347 | 2.26 |
| Trojan.Runner.27 | 28104 | 2.17 |
| Trojan.BPlug.35 | 25494 | 1.97 |
| Trojan.BPlug.17 | 24256 | 1.87 |
| Trojan.Popupads.15 | 14596 | 1.13 |
| Trojan.DownLoader11.3101 | 13940 | 1.07 |
| Trojan.Packed.25266 | 12322 | 0.95 |
| Trojan.LoadMoney.1 | 11811 | 0.91 |
| Trojan.MulDrop5.10078 | 11561 | 0.89 |
| Trojan.Ormes.2 | 11280 | 0.87 |
| Trojan.Triosir.1 | 10980 | 0.85 |
| Trojan.BPlug.46 | 10671 | 0.82 |
| Trojan.LoadMoney.262 | 10412 | 0.80 |
| Trojan.InstallMonster.61 | 10026 | 0.77 |
| Trojan.LoadMoney.15 | 9720 | 0.75 |
| BackDoor.Maxplus.24 | 8502 | 0.66 |
Botnets
The botnet comprised of machines infected with the file infector Win32.Rmnet.12 is still operational. On average, around 165,000 bots connected daily to one of the two subnets controlled by Doctor Web, a number almost identical to last month’s. The subnet’s activity is illustrated in the following graph:
Win32.Rmnet.12 botnet activity in May 2014 (1st subnet)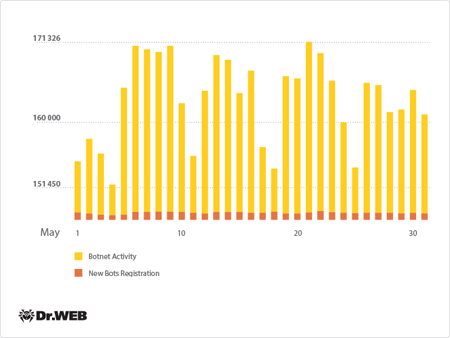
The second Win32.Rmnet.12 subnet also demonstrated stable operation, with an average of 250,000 infected PCs connecting to the network on a daily basis.
The botnet consisting of computers infected with Trojan.Rmnet.19 was active, too. Its operation is illustrated in the diagram below:
Average daily activity of the Trojan.Rmnet.19 botnet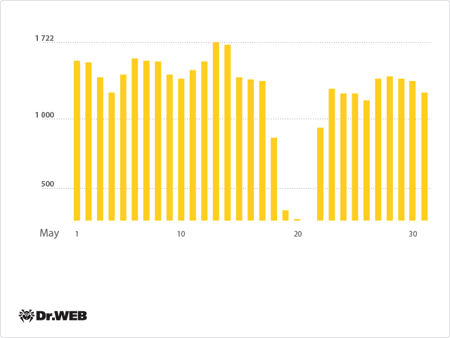
The number of computers running Mac OS X and infected with BackDoor.Flashback.39 has been declining gradually: at the end of May, the total number of infected Macs was 15,623—2,682 fewer than in the previous month. The diagram below represents the botnet’s current activity:
Average daily activity of the Backdoor.flashback.39 botnet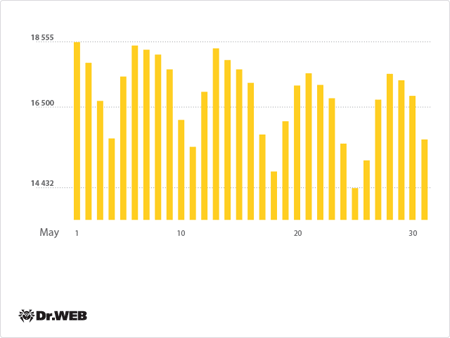
In May 2014, Doctor Web's security researchers examined the multi-component file infector Win32.Sector. Its main function is to download various executables via P2P networks and run them on infected machines. Because of the virus’s architecture, the botnet consisting of machines infected with Win32. Sector has no command and control servers. Instead the bots use IP lists to communicate with each other. Doctor Web's researchers employed the commands used by the malware to check whether the network, to which the infected host is connected, uses the NAT (if the NAT is unavailable, the bot receives a unique ID) to acquire the IP addresses of other infected PCs. In doing so, the researchers were able to assess the botnet’s size. On average, about 60,000 infected computers interacted over the botnet on a daily basis. A Win32.Sector botnet activity graph is presented below:
Average daily activity in the Win32.Sector botnet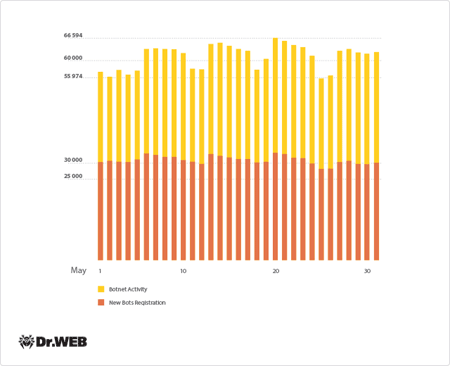
In terms of geographical distribution, the greatest number of hosts infected with Win32.Sector was found in Taiwan; the second highest number was registered in Egypt, and India ranked third.
Currently several malicious programs are being spread via the Win32.Sector botnet:
- Trojan.PWS.Stealer.1630which steals passwords and other confidential information;
- Trojan.Mssmsgs.4048 — a spam plugin;
- Trojan.DownLoader8.17844 which operates as an http and socks5 proxy;
- Trojan.DownLoader10.49375 which operates as an http and socks5 proxy;
- Trojan.Siggen6.11882 which establishes DNS tunnels (53 udp port) and TCP tunnels (port 80);
- Trojan.Rbrute which gains access to Wi-Fi routers;
- Trojan.Proxy.26841 which establishes a tunnel to transmit http traffic to specified nodes.
Also, at the end of May, Doctor Web security researchers discovered a new Win32.Sector module, designed to scan a specified IP address range for open RDP ports (3389). The module was dubbed Trojan.RDPCheck.
For more information about the architecture and distribution of this program, please refer to our earlier publication.
Linux in danger
In May Doctor Web reported a record-high (compared to previous months) number of malicious programs targeting different versions of Linux. A large portion of them was designed to conduct DDoS attacks. Linux.DDoS.3 can launch DDoS attacks on a specified server over the TCP/IP (TCP flood) and UDP (UDP flood) protocols. It can also send DNS requests to enhance the effectiveness of the attacks (DNS Amplification). Another modification of the threat, dubbed Linux.DDoS.22, targets Linux ARM distributions, while Linux.DDoS.24 can infect servers and desktops running 32-bit versions of Ubuntu and CentOS.
Another group of threats to Linux, researched by Doctor Web last month, was given the common name Linux.DnsAmp. Some malware of this family communicates with two control servers and can infect both 32- (Linux.DnsAmp.1, Linux.DnsAmp.3, and Linux.DnsAmp.5) and 64-bit ( Linux.DnsAmp.2 and Linux.DnsAmp.4 ) versions of Linux.
Finally, it’s worth mentioning the Linux.Mrblack program. One of its versions is meant for ARM editions of Linux distributions, while the other is intended for 32-bit x86 editions. This Trojan is also designed to perform DDoS attacks via TCP/IP and HTTP. It features a fairly primitive design, and, like other similar threats, acts on control server commands.
After theinformational material about the design and features of the threat was published on Doctor Web's site, the company’s virus analysts added definitions to the virus database for several malicious programs classified as a separate family, Linux.BackDoor.Gates These Trojans operate as DDoS bots and perform backdoor functions. More information about one of the members of this Linux Trojan family will be available in one of our upcoming reviews.
Encoders again
In May, 560 users whose machines had been affected by different encoders contacted Doctor Web's technical support service. More than 100 of the incidents involved Trojan.Encoder.293. Written in Delphi, the Trojan makes use of a two-stage file encoding system involving XOR and RSA encryption. The files, encrypted by Trojan.Encoder.293, have the extensions Support@casinomtgox.com, ONE@AUSI.COM, two@AUSI.COM and three@ausi.com.
Thanks to research carried out by Doctor Web, files compromised by Trojan.Encoder.293 and having the aforementioned extensions are now highly likely to be decoded successfully, even if the Trojan file has been removed from the disk.. If the encoder hasn't been deleted, all the files can be restored.
Threats to Android
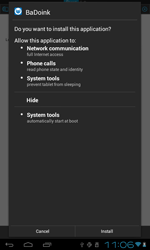
The last month of spring was rather intense in terms of the emergence of new threats to Android. In early May, the definition for Android.Locker.1.Origin was added to the virus database. It was designed to lock mobile devices and then extort money from the affected users. The criminals behind the program intended for it to limit access to an infected system by continuously displaying a message stating that a severe violation of the law had occurred and that the computer was being locked as a punitive measure, but in many cases Android.Locker.1.origin displayed a white screen or a harmless image. However, the locking itself was rather efficient because the malware periodically activated its main window which interfered with normal use of the device.
To neutralise such threats, users are recommended to enable the safe mode and remove the Trojan in question. In many cases, one can succeed in removing the program through repeated attempts to access the system settings, but this approach requires a certain skill and patience.
 |
 |
A similar Trojan extortionist (Android. Locker.2.origin (as classified by Doctor Web), which was discovered later, behaved much more aggressively. In addition to the above-mentioned locking, it performed a far more harmful task, namely searching for and performing AES encryption on a wide range of files, such as photos, videos and documents, and then demanding money for their decryption. The Trojan can compromise files with the extensions .jpeg, .jpg, .png, .bmp, .gif, .pdf, .doc, .docx, .txt, .avi, .mkv, and .3gp. In fact, this malware is the first Trojan encoder for Android which shows that cybercriminals engaged in extortion using notorious Windows Encoder malware have expanded their field of operation.
This Trojan can communicate with the attackers' control server and can relay a variety of information about an infected device (including, for example, its IMEI) to the server.
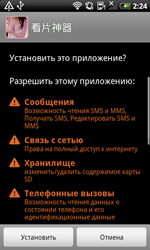
Mid-month, a definition for an Android.MMarketPay program, which pays automatically for digital content in various Chinese software market portals, was added to the Dr.Web virus database.
 |
 |
Unlike many other members of this family, which are designed to automatically purchase games and applications, the new malware Android.MMarketPay.8.origin is intended for the purchase of various game cards and can circumvent existing protection mechanisms such as CAPTCHA and SMS verifications. In particular, to recognise test images, the Trojan uploaded them onto the website of a recognition service, and then intercepted confirmation SMS messages and automatically responded to them.
In addition to this program, in May, devices in China were also threatened by the Oldbot program. Like the previous members of the family, the new version (named Android.Oldboot.4.origin) came pre-installed on a variety of mobile devices on the local market and was intended for the covert downloading and installation of various applications.
Alas, the past month didn't go without malware making an appearance on Google Play. In particular, at the end of May, Doctor Web's security researchers discovered a utility that incorporated undocumented features: it could send SMS messages to premium numbers at the command of a control server and download and install various applications. Because such dangerous actions cannot be controlled by the user, this utility was added to the virus database as Android. Backdoor. 81.origin. Read more about this event in the review on Doctor Web's site.
In addition, massive SMS spam mailings were dispatched in May to distribute Android Trojans in South Korea. Throughout the month, Doctor Web registered more than 180 such mass transmissions, and most of them were related to Android.SmsBot.75.origin (33.69%), Android.Spy.40.origin (16.58%), Android.MulDrop.18.origin (16.04%), Android.Spy.64.origin (7.49%), Android.SmsSpy.82. origin (5.88%) and Android.Spy.45.origin (4.28%).
Malicious files detected in mail traffic in May
| 01.05.2014 00:00 - 31.05.2014 23:00 | ||
| 1 | Trojan.DownLoad3.32784 | 0.84% |
| 2 | Trojan.Fraudster.778 | 0.64% |
| 3 | Trojan.PWS.Panda.5676 | 0.57% |
| 4 | Exploit.PDF.8011 | 0.56% |
| 5 | Trojan.PWS.Panda.7278 | 0.56% |
| 6 | Win32.HLLM.MyDoom.54464 | 0.50% |
| 7 | Trojan.DownLoader11.8676 | 0.47% |
| 8 | PDF.FakeLink.1 | 0.45% |
| 9 | Trojan.DownLoad3.33216 | 0.45% |
| 10 | Trojan.DownLoad3.28161 | 0.45% |
| 11 | Trojan.DownLoad3.33354 | 0.45% |
| 12 | Trojan.SkypeSpam.11 | 0.44% |
| 13 | Exploit.CVE-2010-0188.9 | 0.42% |
| 14 | Trojan.PWS.Panda.4795 | 0.42% |
| 15 | Trojan.DownLoad3.33498 | 0.40% |
| 16 | Trojan.Packed.26775 | 0.39% |
| 17 | Win32.HLLM.MyDoom.33808 | 0.36% |
| 18 | Trojan.Fraudster.517 | 0.36% |
| 19 | Trojan.PWS.Panda.2401 | 0.34% |
| 20 | BackDoor.Comet.884 | 0.30% |
Malicious files detected on user computers in May
| 01.05.2014 00:00 - 31.05.2014 23:00 | ||
| 1 | SCRIPT.Virus | 1.29% |
| 2 | Trojan.Packed.24524 | 0.59% |
| 3 | JS.Redirector.228 | 0.53% |
| 4 | Trojan.LoadMoney.262 | 0.46% |
| 5 | Tool.Unwanted.JS.SMSFraud.26 | 0.44% |
| 6 | Trojan.InstallMonster.51 | 0.43% |
| 7 | Trojan.MulDrop5.10078 | 0.40% |
| 8 | Adware.Downware.2095 | 0.37% |
| 9 | Adware.OpenCandy.4 | 0.37% |
| 10 | Adware.Downware.179 | 0.36% |
| 11 | JS.IFrame.566 | 0.34% |
| 12 | Adware.Toolbar.240 | 0.34% |
| 13 | Tool.Skymonk.14 | 0.33% |
| 14 | BackDoor.IRC.NgrBot.42 | 0.33% |
| 15 | Adware.OpenCandy.3 | 0.33% |
| 16 | Adware.NextLive.2 | 0.32% |
| 17 | Trojan.InstallMonster.209 | 0.31% |
| 18 | Adware.Conduit.33 | 0.30% |
| 19 | Trojan.InstallMonster.146 | 0.29% |
| 20 | Adware.Bandoo.13 | 0.29% |
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live