SMS spam and Android Trojans in South Korea: A Doctor Web mobile security review for the first quarter of 2014
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
April 22, 2014
Overview
Statistics acquired by Doctor Web's security researchers in the first quarter of 2014 point to 430 incidents of unwanted SMS messages containing malware download links being distributed in South Korea. In contrast, the last quarter of 2013 saw 338 such incidents. Thus, the total number of attempts made to infect Android devices via SMS spam in South Korea has increased by 27.22% over the past three months. And, if at the beginning of this year, there was a decline in the intensity of these attacks, which reached their minimum in February, by March their volume had practically climbed back up to the maximum achieved last December. The pie chart below shows the number of SMS spam attacks registered during the specified period.
Incidents registered of malware download links being spread by unwanted SMS messages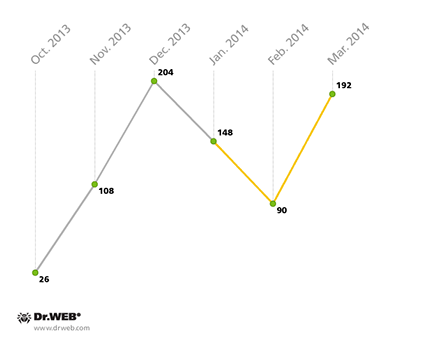
Spam messages under close scrutiny
The criminals behind SMS spam exploit a diverse variety of topics to attract the attention of potential targets and increase the probability of their malware being installed successfully. The most popular topics are those related to law enforcement (e.g., notifications about speeding, illegal downloads, court orders, police reports, prosecution requests) and fake postal delivery status notifications. These account for 36.05% and 31.86% of the volume of spam, respectively. They are followed by civil defence event notifications (11.63%), wedding-related information (10.23%), notifications of relatives being admitted to hospitals or having accidents (2.56%), as well as fake SMS messages from mobile phone carriers (2.32%) and credit institutions (1.17%).
Topics of unwanted SMS messages used to distribute malware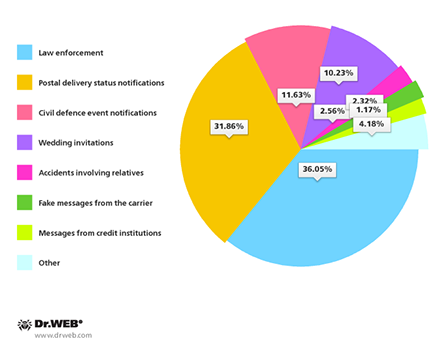
In 73.26% of incidents, URL shortening services were used to disguise the malicious download links found in the messages. This makes it possible to not only hide the address of the site that hosts the Trojan, but also make the messages more compact and easier for users to read. In total, the attackers used 42 such online services of which egoo.gl, me2.do, dwz.cn, ka.do and bye.im were the most popular.
The most popular URL shortening services used by criminals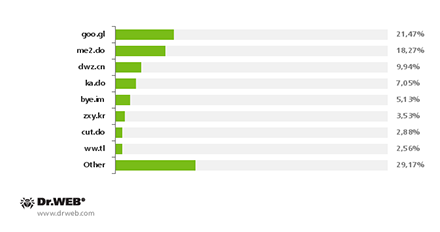
As for the sites hosting and distributing the malware, these included bogus sites crafted by criminals as well as legitimate ones such as file hosting services and blogs. At the same time, the past three months witnessed a marked reduction in the number of fraudulent web portals and a simultaneous increase in the use of legitimate online services.
Sites used by criminals to host malicious applications. The first quarter of 2014.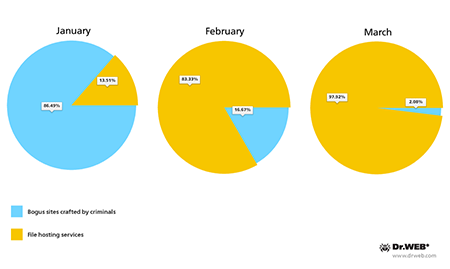
Among cybercriminals, the most popular hosting services included Dropbox, Google Drive, Clip2net and T cloud; Dropbox was used much more intensively than the others and accounted for 91.51% of all incidents, while its nearest competitor was only involved in 7.42% of the attacks.
Online file hosting services involved in spreading Android malware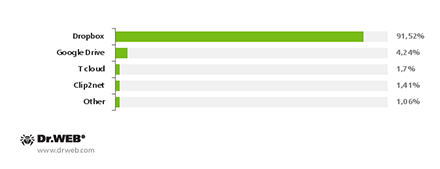
The malicious applications
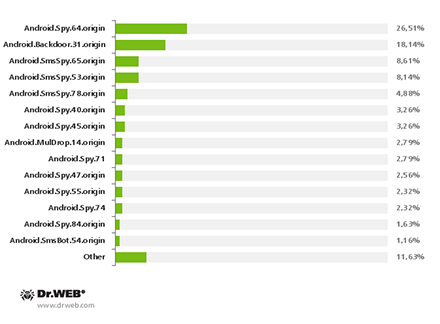
Nine malware families were identified as being involved in the spread of Android Trojans. These were Android.Backdoor, Android.MulDrop, Android.SmsBot, Android.BankBot, Android.SmsForward, Android.SmsSend, Android.SmsSpy, Android.Spy and Android.Tempur. The percentage of each family whose species were identified is presented in the pie chart below.
Identified Android Trojan families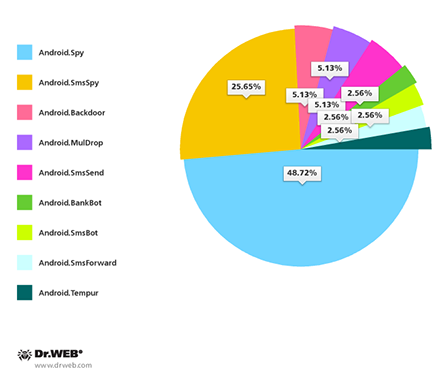
The pie chart indicates that Android.Spy (19 species or 48.72% of the total number of Trojans). They are followed by Android.SmsSpy (10 species or 25.65% of the total) which is commonly used to steal confidential information. One of its key features is that it intercepts inbound SMS that may contain online transaction information, mTAN codes and other data that can potentially be exploited by intruders. In addition, many versions of these Trojan horses also steal email addresses and phone book contact information; some are able to mimic legitimate banking applications to get hold of authentication data.
Other families are represented in much smaller numbers. Android.Backdoor, Android.MulDrop and Android.SmsSend each accounted for 2 malicious programs or 5.13% of the total, while Android.BankBot, Android.SmsBot, Android.SmsForward and Android.Tempur are represented in even smaller numbers—1 Trojan or 2.56% of the total.
All in all, it can be concluded that the vast majority of the attacks in South Korea (80%) were carried out to steal sensitive information, while few were driven by other motives such as gaining control over infected mobile devices (18.37%) or sending SMS messages without user consent (1.63%).
The main objectives pursued by attackers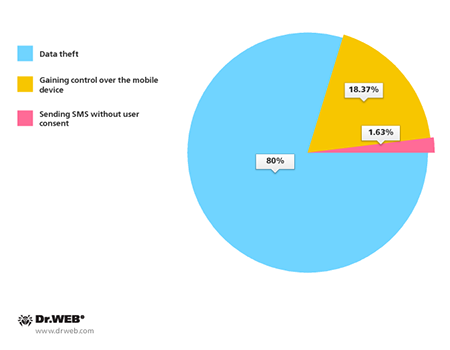
If we factor in the number of concrete Trojan modifications that have been identified, the distribution spread will appear as follows:
The most sophisticated threats
Android.Backdoor.53.origin. To distribute this malware, criminals modified Webkey (com.webkey v.209), an application that lets users control their devices remotely. Unlike the original version, the compromised application doesn't have a GUI and once it has been installed, it hides its presence in the system by removing its icon from the main screen. When launched, Android.Backdoor.53.origin sends the device's ID to a remote server, signalling that the infection was initiated successfully. Consequently, the intruders can get full control over the device and gain access to the personal data and hardware features.
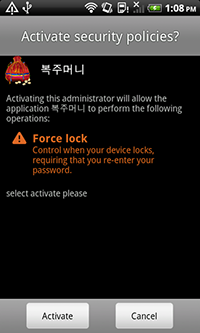
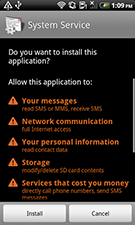
Android.Spy.47.origin (com.google.service v4.2). This Trojan-spy is designed to steal SMS messages from phone books, intercept calls, track GPS coordinates, and retrieve general information about the device. It repeatedly prompts users to add it onto the device administrator list and disables system settings to prevent its deletion. The Trojan is spread under the guise of an application called System Service, as well as the popular messaging service KakaoTalk.
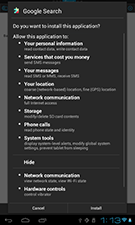
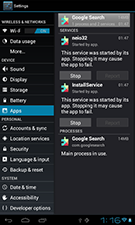
Android.BankBot.2.origin (com.googlesearch v1.0). This malicious program is designed to intercept SMS messages and steal banking information. Criminals disguised it as a legitimate application. When launched, the Trojan created two active services, named neio32 and InstallService, which performed malicious activities. The Trojan checked whether South Korean banking applications were installed on the device and could mimic their operation to steal confidential information. Furthermore, if it detected one of the most popular South Korean anti-viruses, Android.BankBot.2.origin would attempt to remove it.