Downloader Trojans generate profit for "mobile" cybercriminals
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
April 10, 2014
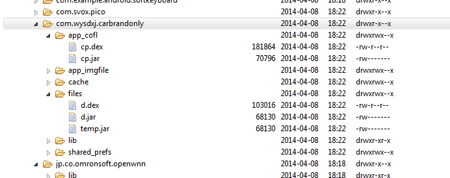
Doctor Web specialists have discovered new malicious applications spread with the aid of a dropper program that has entered the virus database as Android.MulDrop.18.origin.
 |  |
When launched, this Trojan uses a special library file to decrypt two of its apk packages and employs the routine DexClassLoader (without any user involvement) to load corresponding dex files into the device's memory. The executable files are detected by Dr.Web as Android.DownLoader.57.origin and Android.DownLoader.60.origin.If activated successfully, the malicious programs retrieve from remote servers the list of applications they need to download onto the device. In response to the malware’s request, the command and control servers can, at set intervals, provide the downloaders with various files. Among them, both known and new malware belonging to several families, such as Android.SmsSend and Android.Backdoor, were identified by virus analysts. Thus, criminals can implement various attack scenarios involving specific types of malicious applications, ranging from common SMS Trojans to complex spying programs. Malicious downloaders can also be adopted to spread legitimate applications (including games), so that the resourceful criminals involved will get paid for their installation.
It is worth noting that when the Trojans attempt to install the downloaded programs, the users will have to confirm this action. However, the chance exists that some of them just won't give the matter sufficient consideration and will go ahead and agree to the installation.
Currently Doctor Web's security researchers also know of a second dropper modification, Android.MulDrop.18.origin, which, unlike the first one, contains other Trojan downloaders in non-encrypted form. These programs were added to the virus database as Android.DownLoader.59.origin and Android.DownLoader.61.origin. Their mechanism for communicating with a remote server is somewhat different from that which was implemented in Android.DownLoader.57.origin and Android.DownLoader.60.origin, but their ultimate goal is the same: to download and install other applications.