Mobile threats in February 2014
Virus reviews | Hot news | Threats to mobile devices | All the news | Virus alerts
March 3, 2014
Overall, from February 1-27, 2014, Dr.Web for Android discovered 8,315,374 unwanted and malicious programs, with peak viral activity occurring on February 7. That day 374,194 malware samples were identified. The lowest level of virus activity was registered on February 19 when only 283,159 threats were found.
The most frequently detected programs include Adware.Revmob.1.origin, а также рекламные модули семейства Adware.Airpush.originad modules—these are normally incorporated in free applications and display in the system tray various notifications containing sponsored links. The most frequently detected malware programs are in the Android.SmsSend and Android.Spy families. Below you can find the top ten Trojans most frequently detected by Dr.Web for Android.
| № | Threat name | % |
|---|---|---|
| 1 | Android.SmsSend.1064.origin | 2,16 |
| 2 | Android.SmsSend.315.origin | 2,07 |
| 3 | Android.SmsSend.749.origin | 1,53 |
| 4 | Android.SmsSend.458 | 1,48 |
| 5 | Android.SmsSend.1070.origin | 1,42 |
| 6 | Android.SmsSend.859.origin | 1,32 |
| 7 | Android.SmsSend.309.origin | 1,30 |
| 8 | Android.SmsSend.758.origin | 1,24 |
| 9 | Android.Spy.78.origin | 1,13 |
| 10 | Android.SmsSend.1088.origin, Android.SmsSend.458 | 1,12 |
The bootkit Android.Oldboot.1.origin remains one of the most active threats to Android. It places one of its components in the protected memory area of infected devices, so that it can launch itself when the operating system is booting up. If core modules of the malware are removed, it will re-infect the system the next time the device is rebooted. The danger lies in the fact that Android.Oldboot.1.origin can execute commands coming from remote servers owned by criminals.
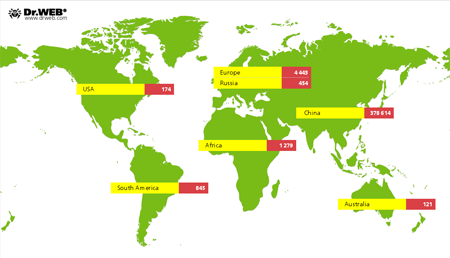
The prevalence of this threat has been clarified thanks to the fact that Doctor Web's security researchers managed to obtain statistics on the infection, including the IMEIs of the devices affected, during the period from February 1-27, 2014. Currently, the botnet consists of 396,709 infected devices (2,325,326 unique IP addresses were registered from February 22-27). The majority of them (378,614) are in China; about 4,500 infection incidents occurred in European countries.
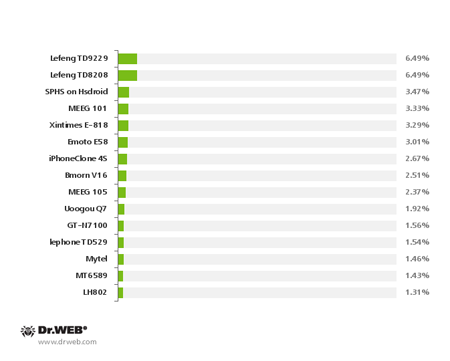
This malware mostly infects mobile phones manufactured in China. The handset models on which Android.Oldboot was most frequently detected are listed below.
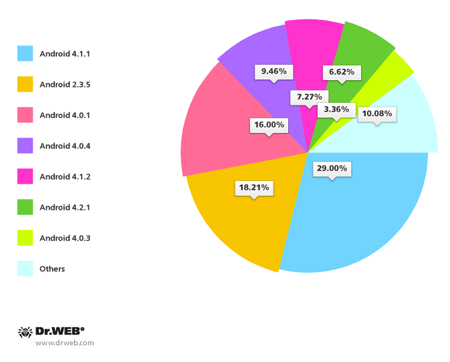
The distribution of the infected devices by Android OS version is shown in the following diagram.
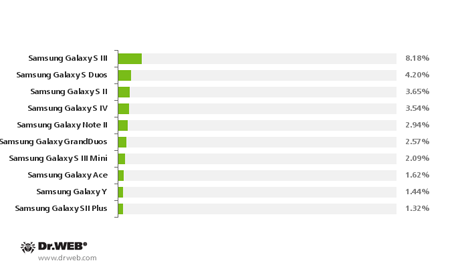
The majority of Dr.Web for Android users still prefer smart phones manufactured by Samsung. As far as devices of other manufacturers are concerned, LG Optimus models L5 and L7, and Sony Xperia J are the most popular. The list of the most popular handset models is presented in the diagram below.
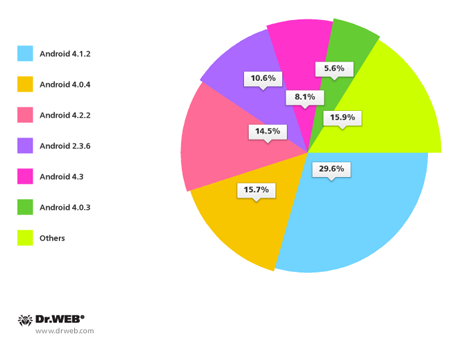
User preferences by Android OS version are illustrated below.
Doctor Web continues to monitor the mobile security situation.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live